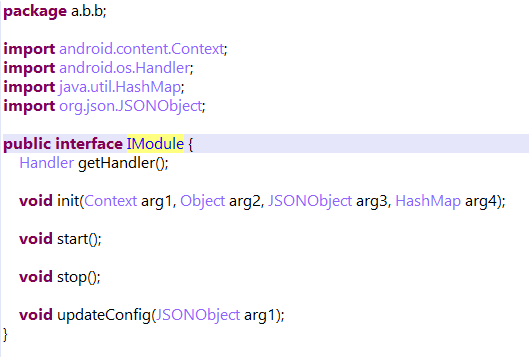
Malware
Fake Voice Apps on Google Play, Botnet Development
Several apps on Google Play posing as legitimate voice messenger platforms have automated functions such as fake survey pop-ups and fraudulent ad clicks. Variants were observed to have included evasive techniques and multi-stage infection behavior.
We noticed several uploaded apps on Google Play posing as legitimate voice messenger platforms, with suspicious automated functions such as automatic pop-ups of fake surveys and fraudulent ad clicks. Observed variants of these malicious apps and malware have been deployed one by one since October, with its evolution including evasive techniques and its infection behavior divided into several stages. The modular capabilities of the analyzed samples have been tagged versions 1.0, and the cybercriminals may be in the process of adding more features and updates for future malicious activities such as botnet attacks. Infection numbers are not yet critical, but the increase in uploads and user downloads for the remaining live apps call for continued observation due to its rapid development and distribution in the mobile ecosystem.
While the majority of the fake apps have been taken down, we took one of the apps as an example to show their common behaviors. All the analyzed samples from the seven identified app IDs have similar coding and behavior, which make us suspect that the cybercriminals are working on additional modules and will deploy more malicious apps.
Figure 1. One of the apps posing as a legitimate voice messenger uploaded on Google Play
Figure 2. Malicious voice messenger app with thousands of installs recorded
Behavior
Uploaded on Google Play, the app (detected by Trend Micro as AndroidOS_FraudBot.OPS ) tries to be subtle by using lightweight modular downloaders to compromise unknowing users’ gadgets. While the published uploaders of these apps are different, we suspect that the apps came from the same authors since the codes are similar to each other. Once downloaded, the first component connects with the C&C server, then decrypts and executes the payload.
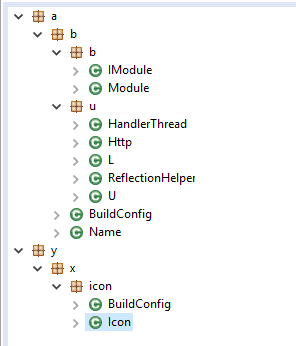
Figure 3. Order of payload execution.
The payload executes as follows:
- The module named “Icon” hides the app’s icon to prevent the user from uninstalling it.
Figure 4. Hiding the icon
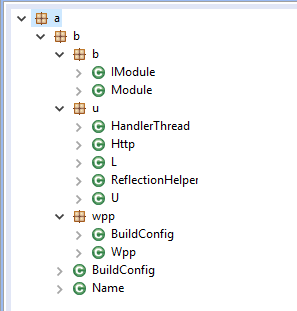
- Module “Wpp” can open the browser to access arbitrary URLs.
Figure 5. The module collects specific URLs found in the browser
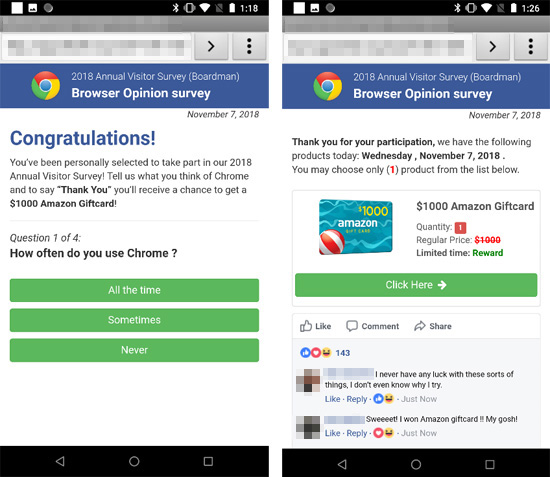
While analyzing the sample, the app displays fake survey forms to collect users’ personally identifiable information (PII) such as names, phone numbers, and home addresses, in exchange for gift cards. The fake survey form will load using the device’s default browser. If the default browser cannot be identified, the survey is loaded from the any of the following browsers, which we have observed based on the C&C response: Boat Browser, Brave, Chrome, Cheetah, Dolphin, DU, Firefox, Jiubang Digital Portal, Link Bubble, Opera, Opera Mini, Puffin and UC.
Figure 6. Fake app for users’ information collection
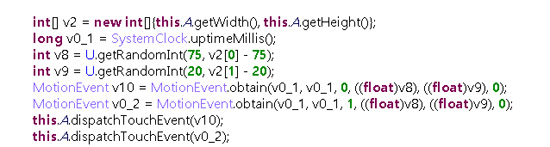
Wpp also generates fraudulent ad clicks via random app touch events.
Figure 7. Random app touch events for fraudulent ad clicks
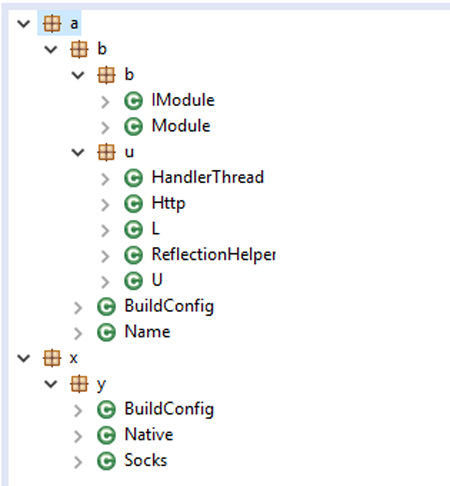
- The module named “Socks” functions as a dynamic library that integrates with C-Ares (the C library for asynchronous DNS requests) as well as name resolves. Though we have not observed communication with the server, we believe that this feature is still in development.
Figure 8. Socks integrates with C-Ares
Defending against this threat: Trend Micro solutions
Google confirmed removal of the malicious voice apps from the store at the time of writing. However, we can expect more of these threats with evolving capabilities, especially for evading detection. Malware like these demonstrate how cybercriminals can easily manipulate the features of these digital threats to attack mobile devices through apps. Devices should also be equipped with comprehensive mobile security that can defend against mobile malware.
Trend Micro Mobile Security detects this threat, and Trend Micro Mobile Security Personal Edition and Mobile Security Solutions defends devices from all related threats. Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies to protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability. Indicators of Compromise
App URL |
SHA256 |
com.bitv.freeaudiomessages |
3f7b367488e761f89b4adeb5dc1b961766c238d41ebb9fbd726da8499d1fce26 |
| com.wififree.messenger | 7a4813f68936a37fce366154a608ad307084336abc205b55f80b0a6788d067ac 811f12ea658f9325eede5afcc9898aaf37d1e0eafab84e94b9d3b13adcc6131f |
| com.onlinevoice.playerapp | 92ea01d0198506d5a43e3cfccf7b2661c131c57e8d260fbf34760f01a897b0cb |
| com.bestvoice.messenger | 9742148afe109e8ab25ec81f58aee8befed6be20affa7b2a71702a65d4bc377c |
| com.netaudio.vam | cabe057cf19ddd54a1489e0db74d0c8833cea501c4b4a22b7953a6e7d1fd9391 |
| com.voicedata.justvoicemessenger | dddb84da1b4f8914f31781a1a8a46c028dbb776a891d198b5d4b78c3c9a62c8d |
Detection Name |
|
Google Play App URLs |
https://play.google.com/store/apps/details?id=com.bitv.freeaudiomessages https://play.google.com/store/apps/details?id=com.wififree.messenger https://play.google.com/store/apps/details?id=com.onlinevoice.playerapp https://play.google.com/store/apps/details?id=com.bestvoice.messenger https://play.google.com/store/apps/details?id=com.netaudio.vam https://play.google.com/store/apps/details?id=com.voicedata.justvoicemessenger |
Command and Control |
hxxp://vilayierie.live:443 hxxp://aspiet.club:443 hxxp://213.239.222.7:8081 |