Exploits & Vulnerabilities
Mitigating an Intel Management Engine Vulnerability
Intel released a security advisory detailing several flaws in its Management Engine (ME). There is also one notable vulnerability that can pose a big risk, especially to corporate computers and networks:CVE-2017-5689, a privilege escalation flaw.
Intel recently released a security advisory detailing several security flaws in its Management Engine (ME). The advisory provides critical ME, Trusted Execution Technology (TXE), and Server Platform Services (SPS) firmware updates for versions 8.X-11.X covering multiple CVE IDs, with CVSS scores between 6.7 and 8.2.
But there is also another notable vulnerability that can pose a bigger risk especially to corporate computers and networks: CVE-2017-5689, a privilege escalation flaw. While there are certain factors and/or triggers for this vulnerability, it can provide attackers administration access and enable them to remotely reset or power off the vulnerable system if exploited successfully. This security issue was divulged in the research, "Silent Bob is Silent." Compared to the recently identified ME vulnerabilities, CVE-2017-5689 was assigned a CVSSv3 score of 9.8.
Given CVE-2017-5698’s impact, which can be compounded by the other flaws identified in Intel’s latest security advisory, users and system administrators are urged to update and patch their MEs. Blocking or disabling the use of ports 16992-16995, which the vulnerability leverages, is also recommended.
Intel ME Platform: An OverviewThis piece of HW and SW is located in Intel chipsets, which started in 82573E known as 945 (ICH7) in 2008, integrated into high-end desktop, notebook, and server chipset families. Computers with the “vPro” (even older ones) have the ME.
In a nutshell, Intel ME is a small computer inside the motherboard chipset running independently of the operating system (OS). It runs when the computer is in sleep or standby modes, and even when switched off. It’s enough to have the computer’s power supply plugged into the power outlet, or have the battery inside the notebook for this small, silent computer to run in the background. In Pre-Skylake (ME 11.X) chipsets, it was built on ARC architecture with RT-OS ThreadX, web server, and JavaVM engine running applets in J Executable File Format (JEFF).
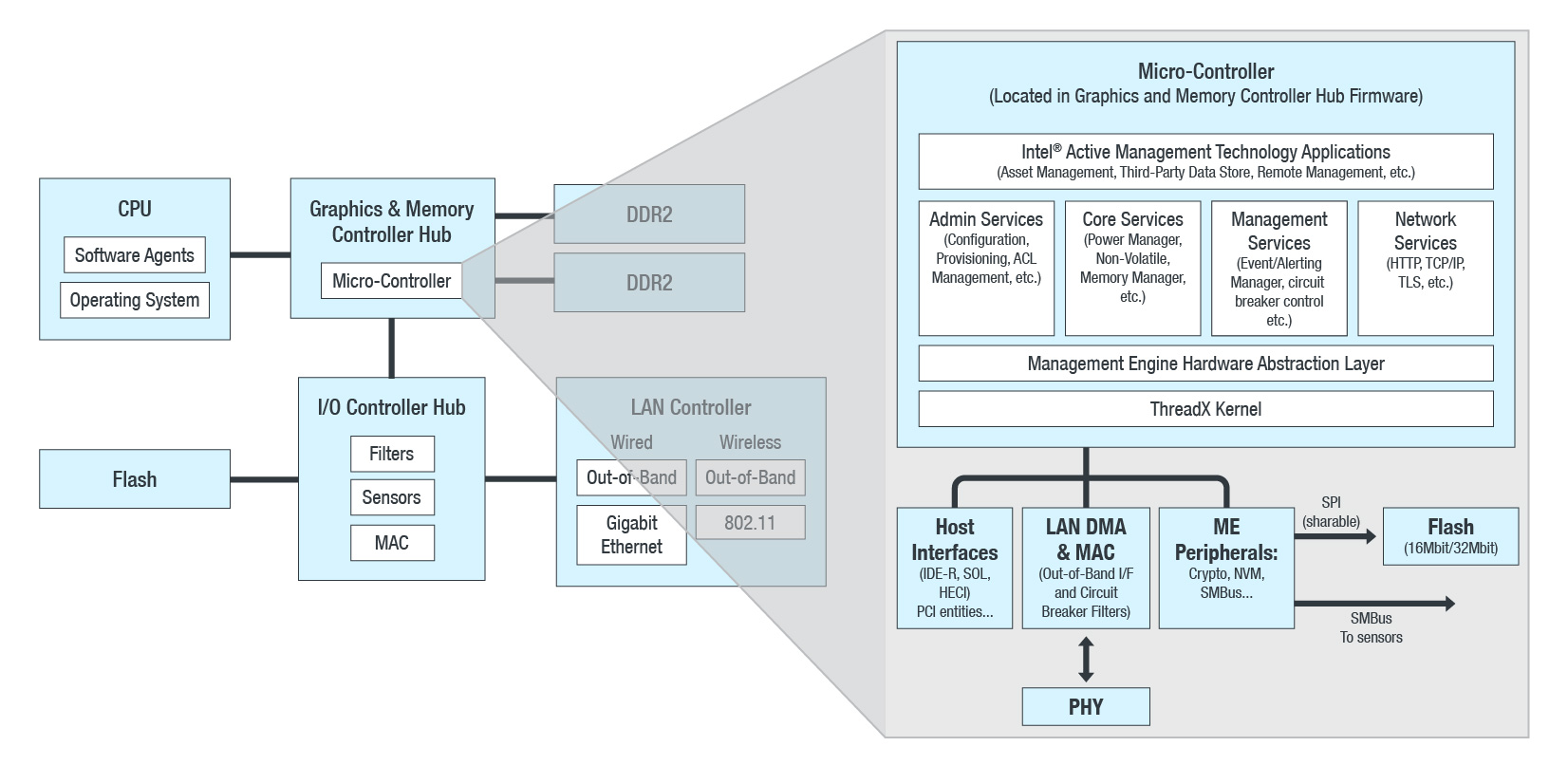 Figure 1: Architecture of Intel’s Management Engine (recreated; original image source: Intel)
Figure 1: Architecture of Intel’s Management Engine (recreated; original image source: Intel)
ME Code Reverse EngineeredSince Skylake, Intel has used the MINIX3 kernel-based OS running on an x86-core Intel Quark microcontroller. The ME computer is crucial for the main CPU and chipset initialization procedures, so it cannot be switched off or disabled. There is a me_cleaner project aiming to reduce unnecessary management modules and keep only those that are critical and needed for platform initialization. For pre-11.X, it was partially a success, as it reduced firmware image sizes (from 1.5—5 MB to 90kB). The changes in version 11.X allowed further size reduction to 300 kB. When ME recognizes that the firmware has been modified, the whole computer either won't boot or will shut itself down within 30 minutes. It should be noted that ME code modification is not easy, given ME's self-checking feature.
Since the change of the ME platform to x86, it became easier to reverse engineer the ME code not only for researchers but also for attackers. While the ME code was supposed to be hidden, it was only a matter of time until it was uncovered and exploited by bad guys.
Security researchers who reverse engineered the code reported that there is a hidden option to disable ME after HW is initialized. Using this option is risky and involves ME firmware modification.
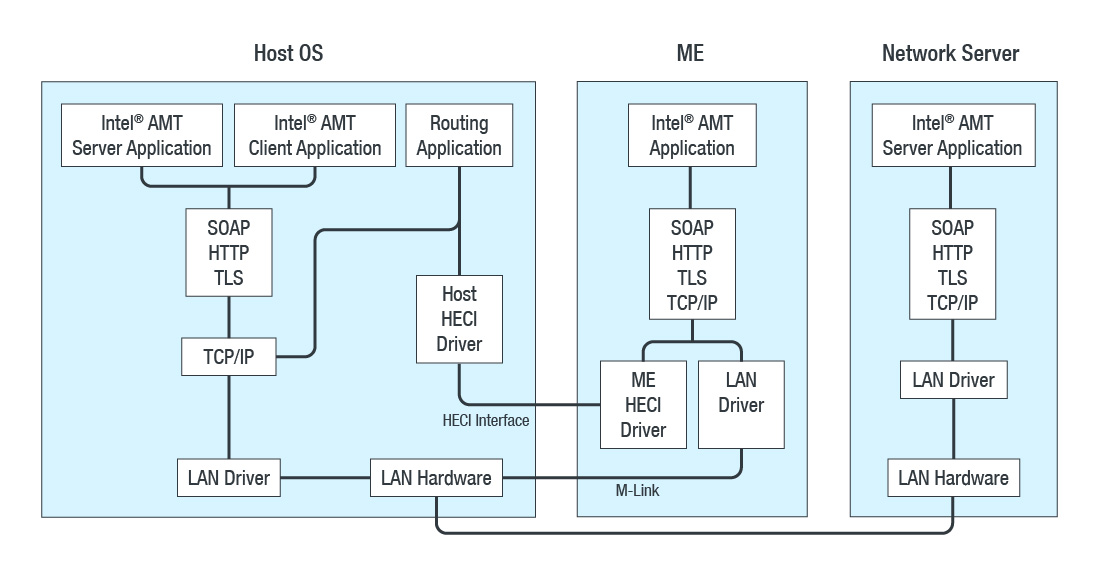 Figure 2: ME’s connection architecture showing communication between network and host OS (recreated; original image source: Intel)
Figure 2: ME’s connection architecture showing communication between network and host OS (recreated; original image source: Intel)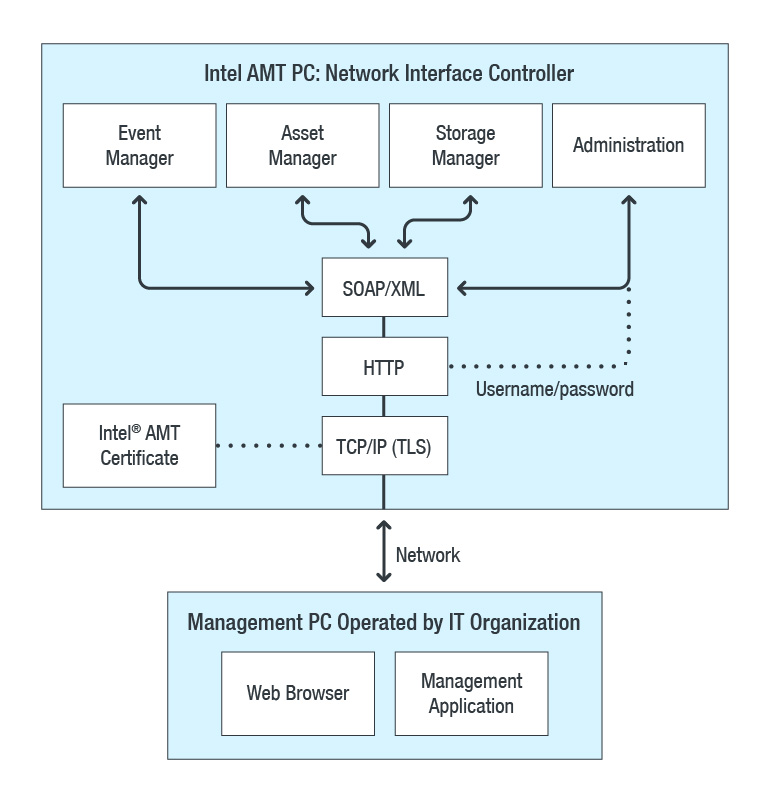 Figure 3: How ME is connected to corporate networks/computers; network protocol is based on Simple Object Access Protocol (SOAP), which can be HTTP or HTTPS (recreated; original image source: Intel)
Figure 3: How ME is connected to corporate networks/computers; network protocol is based on Simple Object Access Protocol (SOAP), which can be HTTP or HTTPS (recreated; original image source: Intel)
Impact and MitigationME is connected to the computer’s Ethernet port as an out-of-band (OOB) interface, communicating over ports 16992-16995. As I have checked today via Shodan, there are still over 5,000 computers with 16992 (AMT web server over HTTP) still exposed publicly to the internet. Some of them could be Intel ME honeypots, and some may have been patched, but there are still a lot of systems vulnerable to a CVE-2017-5698 exploit. Anyone using a simple proxy rule can log into these systems as an administrator. The least they can do is to reboot or switch off the entire system with a mouse click. To further exemplify: if serial-over-LAN (SOL) is activated in ME, an attacker can gain administrator access to the OS or hypervisor running on that system.
I also found that login events are not recorded in a management log. There will even be more internally accessible and vulnerable ME computers on corporate networks (including some Intel-based firewalls and routers). The traffic to the aforementioned ports should be blocked and network traffic carefully monitored.
Here are some preventive best practices that can help mitigate attacks exploiting CVE-2017-5689:
- Update the ME firmware immediately
- Update the Intel ME host OS components, such as Intel Management Engine Interface Driver, Intel(R) Management & Security Status software, LMS service, as soon as possible
- Review ME configuration and ME OS components; switch off/disable unnecessary modules and functions
- Trend Micro released TippingPoint signatures for blocking exploitation packets to prevent attacks over the network. Note that ME can still be accessed from the hosted OS locally, so practice defense in depth
- Block ports 16992-16995 both on the endpoints and firewalls
Trend Micro™ TippingPoint™ customers are protected from threats leveraging CVE-2017-5689 via these MainlineDV filters:
- 28214: HTTP: Null response digest
- 28456: HTTP: Intel Active Management Technology Authentication Bypass Vulnerability

