Massive LOCKY Campaign Targets Millions of Users
After a recent spam campaign that saw LOCKY being dropped along with FAKEGLOBE, a potentially larger campaign is underway, using spam emails to infect users with a LOCKY ransomware variant (Detected by Trend Micro as RANSOM_LOCKY.TH918). As of the time of this publication, the number of spam emails that were sent already number in the millions.
The campaign uses different types of spam emails. The first one is a fake email, allegedly sent by the Multi-Level Marketing (MLM) Company Herbalife International, in which a tax invoice for a supposed order placement is sent to the user in the form of a file archive: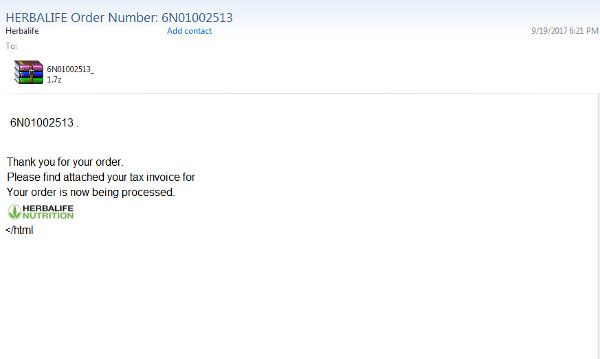
Figure 1: “Herbalife” spam email sample
The second spam email also uses a malicious archive to deliver the malware. However, it comes with a generic “copier” sender without any other indication as to what the spam email is about: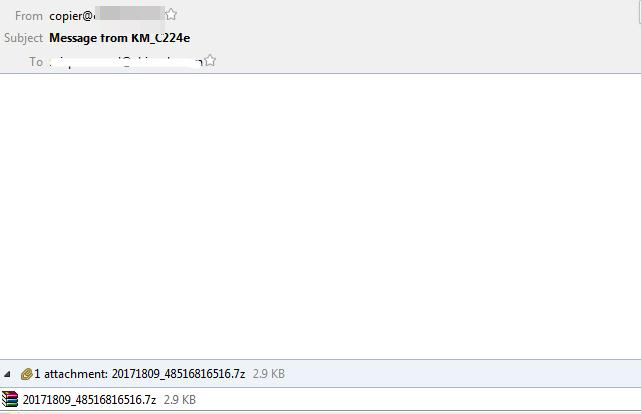
Figure 2: “copier” spam email sample
A third spam email involving LOCKY was also used in the campaign, this time allegedly sent by a “voicemail” service:
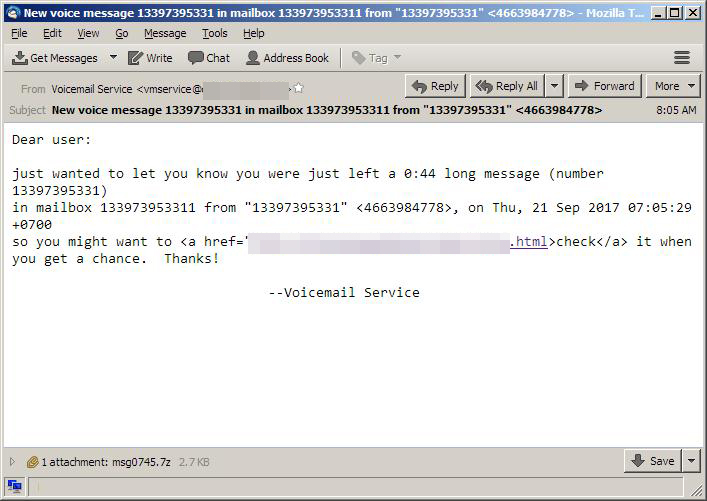
Figure 3: “vmservice” spam email sample
These spam emails all come with an archive file that uses a .7z extension. Contained within these files is a malicious VBS (Detected by Trend Micro as MAL_VBSCRDLX) that, when executed by the user, downloads the LOCKY ransomware.
Trend Micro Smart Protection Network (SPN) data revealed that Chile was the main target of the “Herbalife” spam attacks, hitting Chile (41%) and Japan (21%). The “copier” spam attacks hit India (18%), followed by the US (17%) and Japan (14%). The “vmservice” attacks followed the same patterns, with India at the top (24%), followed by the US (13%) and Japan (12%).
The full coverage for the attacks can be seen in the Heat Maps below: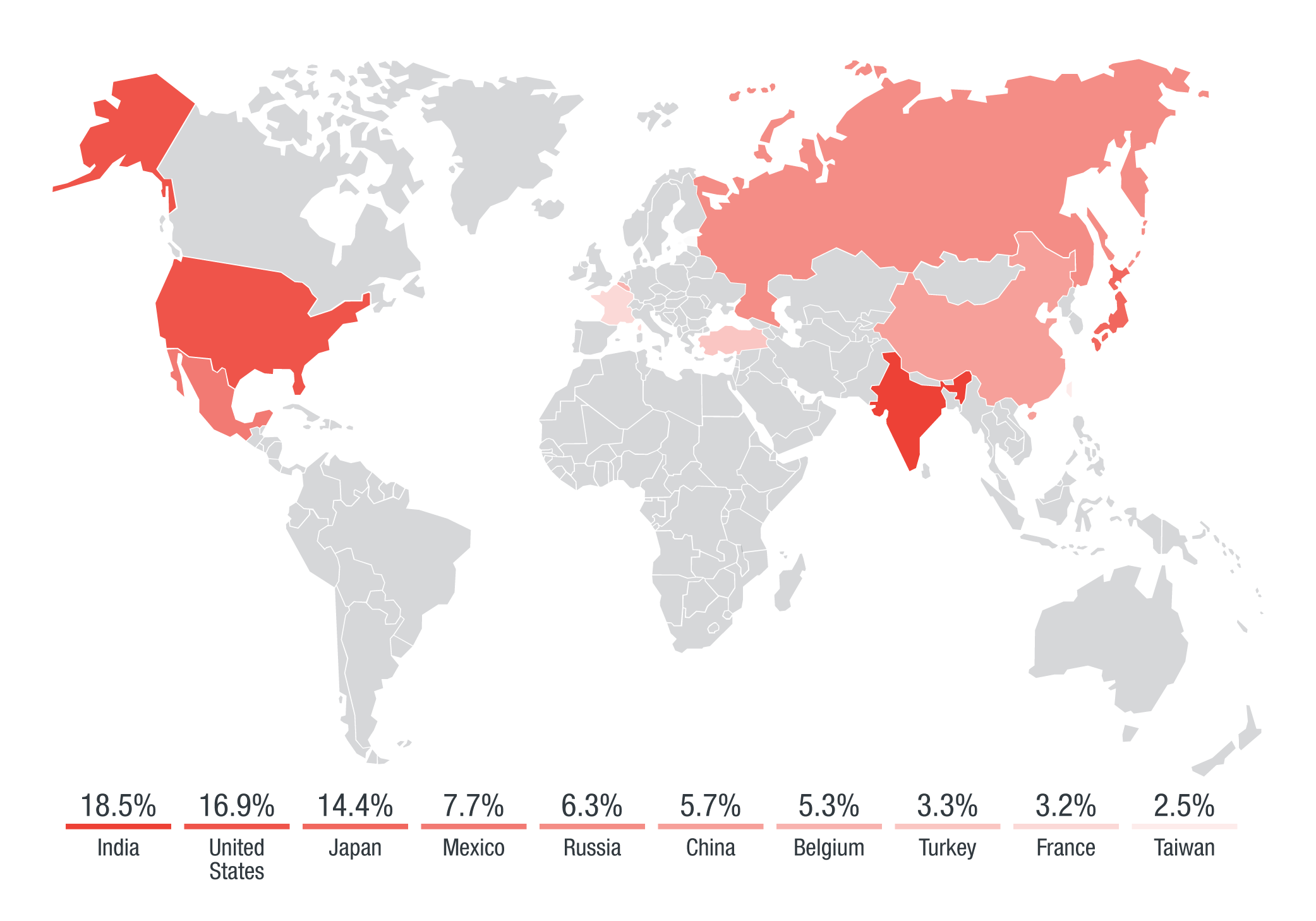
Figure 4: Top 10 countries affected by the “copier” attacks. Apart from India, US, and Japan, "copier" spam attacks were also seen in Mexico, Russia, and China.
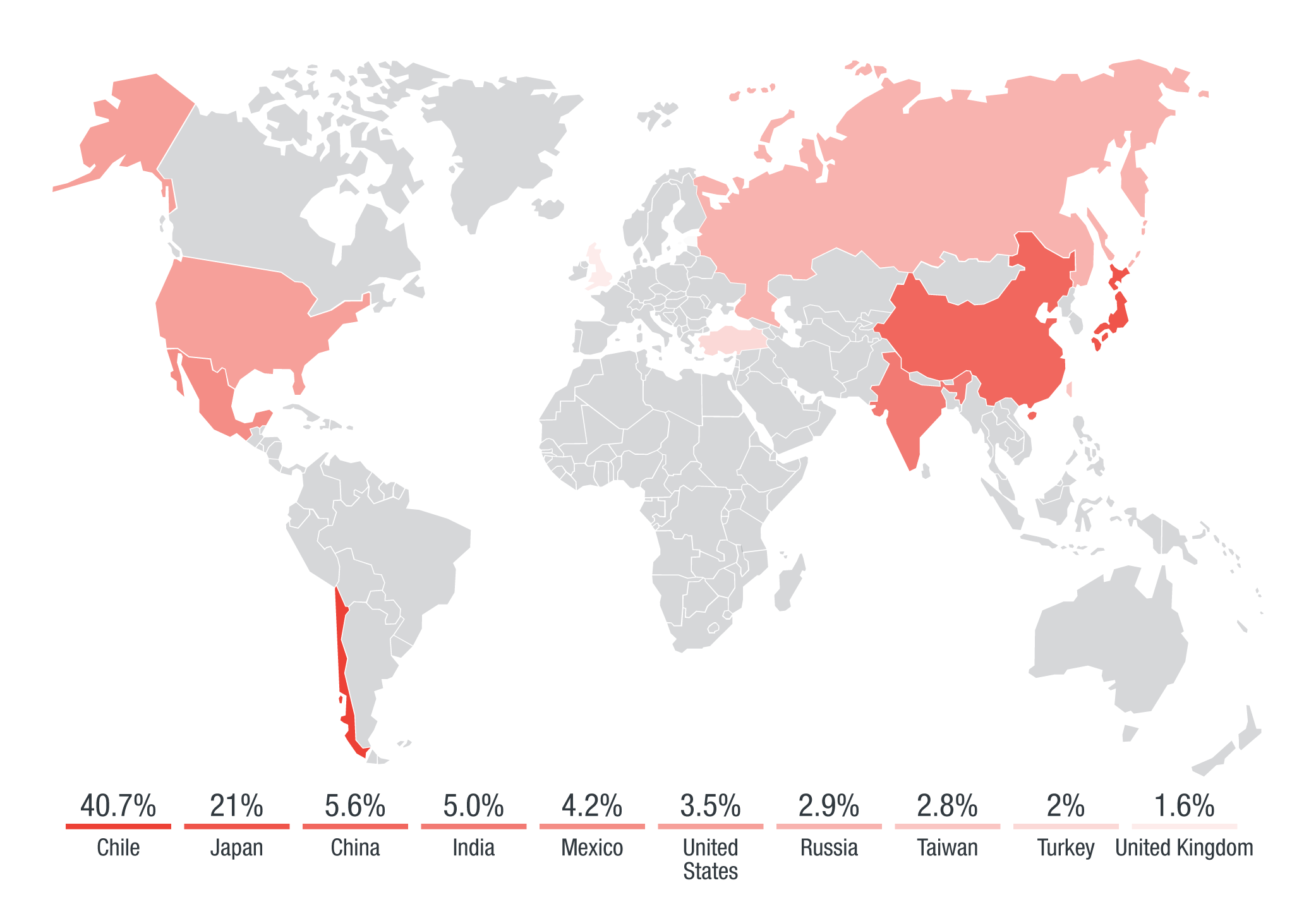
Figure 5: Top 10 countries affected by the “Herbalife” attacks. Chile and Japan, were the main countries involved, followed by China, India and Mexico.
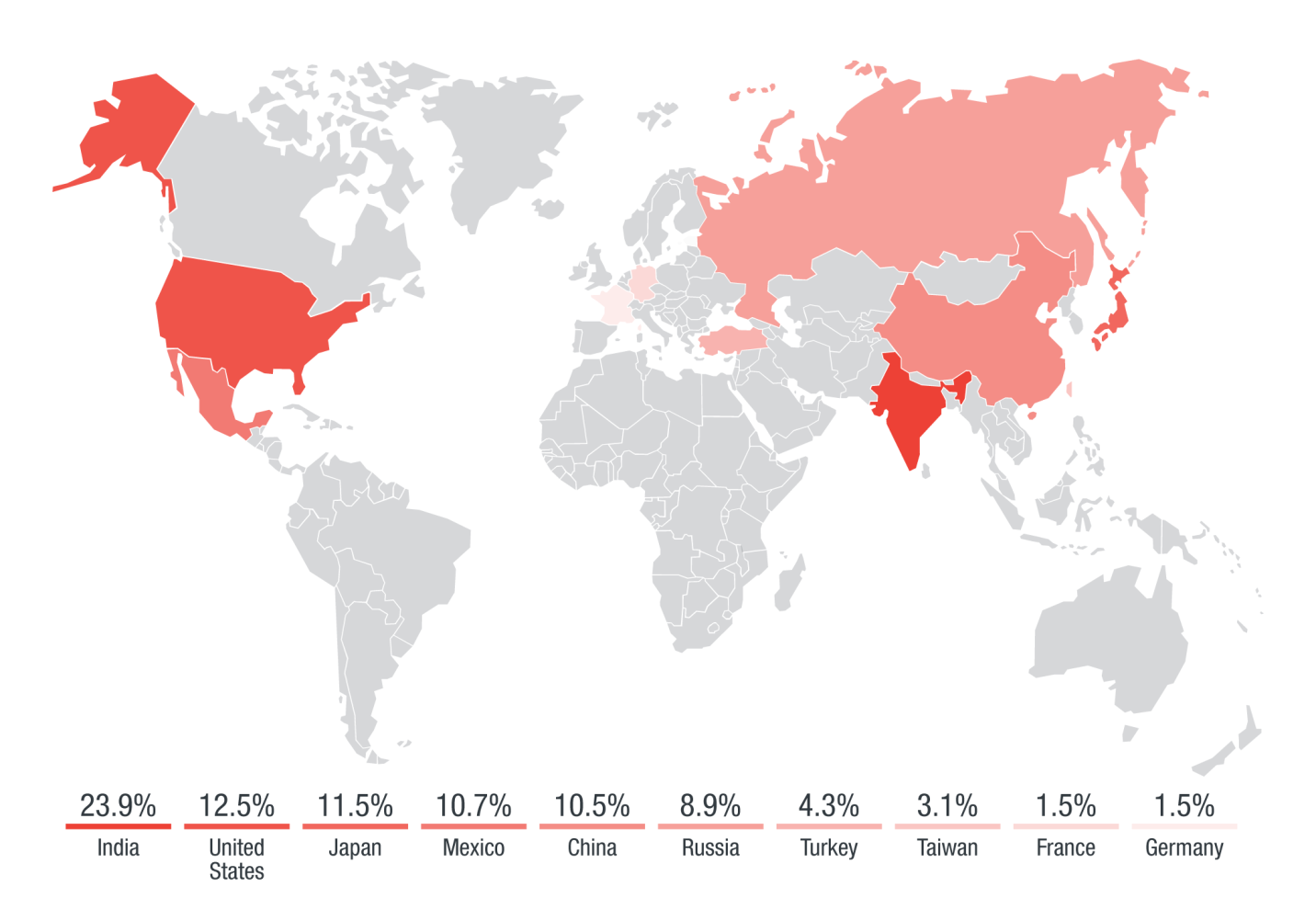
Figure 6: Top 10 countries affected by the “vmservice” attack. India, US and Japan make up the three top countries affected, followed by Mexico, China and Russia.
The different spam emails also peaked at different times, with the “copier” spam sending out the most spam mail from the afternoon of September 18 to early morning September 19. It started to intensify at 4pm UTC time, or 9:30pm in India, which was the country most affected by the attacks.. This was followed by the “Herbalife” spam, which was most prominent from the morning of September 19 and continued through the night. The third spam email, involving “vmservice”, started on the afternoon of September 20 and lasted until September 21. Interestingly, this attack also started peaking at 4PM UTC—similar to the “copier” attacks.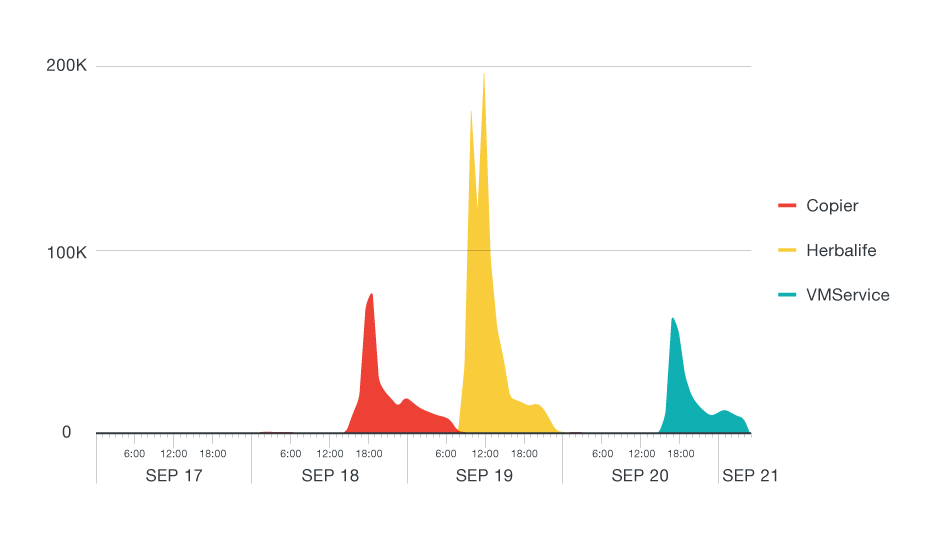
Figure 6: Hourly timeline for the different LOCKY spam attacks. All times are in UTC+0
Spam is still an effective attack vector
While the behavior of LOCKY itself remains unchanged, the scope of the attack and the rapidness with which it managed to spread points to effectiveness of spam for propagating ransomware. LOCKY itself has had a history of being delivered via spam, as seen in previous campaigns such as the one involving the Brazilian underground market, as well as the campaign using encrypted DLLs.
To protect their systems from spam and phishing attacks, users are recommended to use the following best practices:
- Users should always double-check the legitimacy of an email by checking identifiers such as sender domains as well proper spelling and grammar.
- For organizations, proper implementation of antispam filters will help filter threats coming from malicious sources
- Users should always take the context of an email or message into account. If they receive an email from an unfamiliar company or individual, or if they receive invoices for purchases they did not make, then this should be a red flag.
- As a general rule, users should avoid clicking on links or download files even if they come from seemingly “trustworthy” sources without verifying first.
Trend Micro Solutions
Enterprises can benefit from a multi-layered, step-by-step approach to best mitigate the risks brought by spam mail. Trend Micro™ Hosted Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop spam, malware, spear phishing, ransomware, and advanced targeted attacks before they reach the network. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. Also at the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat.
Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud. For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware. For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Updates and technical information on this ransomware can be found in this article.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization
- Agentic Edge AI: Development Tools and Workflows

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One