By Feike Hacquebord, Philippe Lin, Fyodor Yarochkin, Vladimir Kropotov
Key takeaways:
- Residential proxy providers and bulletproof hosting companies stand side by side as key enablers of cybercrime today. Residential proxy providers offer millions of IP addresses with precise location data that can allow cybercriminals to execute targeted attacks and bypass antifraud and IT security systems of enterprises, governments and ecommerce websites.
- The effectiveness of IP address blocklists has diminished over time, due to the abundant availability of residential proxy providers; this creates a growing need for connection-based and session-based access control.
- We anticipate that residential proxy providers will seek to bypass connection and session-based access controls, such as uploading separate software modules to residential endpoints, enabling them to perform specific tasks.
- This modular model is already employed by certain residential proxy providers in the far east who obtain close to millions of residential proxies by exploiting vulnerabilities in the software and hardware supply chains of inexpensive IoT devices and by selling pre-infected Android Open Source Project-supported devices (AOSP).
This research explores the growing market for residential proxies and their role in cybercrime that was traditionally served by bulletproof and proxy network service providers.
A residential proxy is a proxy on an internet-connected device, such as a computer, smartphone, smart TV, or home router, that is configured to provide connectivity for third parties. This third-party access could be with or without the owner’s awareness but is often the latter. This setup can be exploited to make it appear as if the connection is coming from the home user behind the device. As such, residential proxies can enable cybercriminals to bypass anti-fraud systems and target enterprises and governments more precisely – significantly altering the underground bulletproof hosting and proxy market by replacing and complementing parts of the existing ecosystem.
Key drivers to this trend are the changes in cybercrime business models triggered by the explosion of data leaks from thousands of ransomware attacks and intrusions in the past years. Cybercriminals aim to monetize the terabytes of compromised sensitive and Personally Identifiable Information (PII) data using residential proxies to enable internet connections and sessions that appear to come from legitimate users.
The growth of remote work set-ups since the COVID-19 pandemic fanned the flame by creating wider attack surfaces and therefore more opportunities for cybercriminals. The third, driver is the improvement of security and defense mechanisms that made cyber-attacks originating from traditional bulletproof hosting providers less effective.
We hash out these factors that contributed to the rise of the use of residential proxies in cybercrime in the following sections. We’ll also explore future changes in the residential proxy provider market that we envision and what this means for Cyber Risk Exposure Management (CREM). This includes how residential proxies service providers might move away from simple proxies on endpoints, and how the proxy software might be replaced by software that can load different modules and execute tasks like credential brute forcing or internet data scraping directly from an endpoint.
We anticipate that this methodology will be used by cybercriminals to circumvent blocking based on network packet fingerprints; a model already being put in place by some residential proxy providers in the far east with millions of exit nodes. This model mimics some functionality seen in cybercrime botnets in the past but is now used in a business that claims to have legitimate use cases. This underlines the importance of shifting to a proactive security with tools that help security operation centers keep track of evolving tactics and formulate ways to mitigate risk ahead of attacks.
Evolution of cybercriminal business processes
Business processes naturally evolve over time, and so do the operations of cybercriminals. Several factors drive this evolution in cybercrime, including the need for criminals to outmaneuver improved defense strategies and cybersecurity products used by their targets, the emergence of innovative technologies like Generative Artificial Intelligence (GenAI), shifts in online user behavior, and even geopolitical circumstances.
Changing business models in cybercrime also leads to changes in underground services and the way cybercriminals use legitimate services. A clear example is the rise of residential proxy service providers in the last decade. These services have not only partially replaced existing proxy services and bulletproof hosting but have also significantly complemented them. Today, residential proxy providers and bulletproof hosting companies stand side by side as key enablers of cybercrime.
Is traditional bulletproof hosting out?
Traditional bulletproof hosting and proxy providers are known to facilitate multiple unauthorized activities and cybercrime related activities like data scraping, network scanning, delivering spam emails, and hosting of malware and Control and Command (C&C) servers. Other use cases include routing internet traffic through multiple hops, and making tracing the origin of cyberattacks more difficult. Proxy services also made it possible to bypass geographical restrictions and antifraud systems based on geolocation of IP addresses.
Bulletproof IP addresses and proxies at datacenters are hard for foreign law enforcement agencies to take down, but they are relatively easy for defenders to block; this makes them a less attractive option for cybercriminals as defense systems become more effective in blocking them. Instead of working harder with traditional bulletproof hosting and proxies, they turn to residential proxies to overcome these defenses.
Residential proxy providers allow cybercriminals to circumvent anti-fraud systems better because they have vast pools of internet IP addresses. This pool allows attackers to use IP addresses from home users within a vicinity that is plausible for benign traffic. This is one of the reasons that residential proxy providers have become a full-fledged business ecosystem that partially replaced but mostly complemented the already existing bulletproof hosting and proxy market.
Residential Proxy Services
The first residential proxy (RESP) providers appeared around 2014, and this business has grown significantly in recent years. Nowadays there are various brands and several types of providers. Some companies claim to have millions of residential IP addresses to their disposal, while others have a much smaller pool.
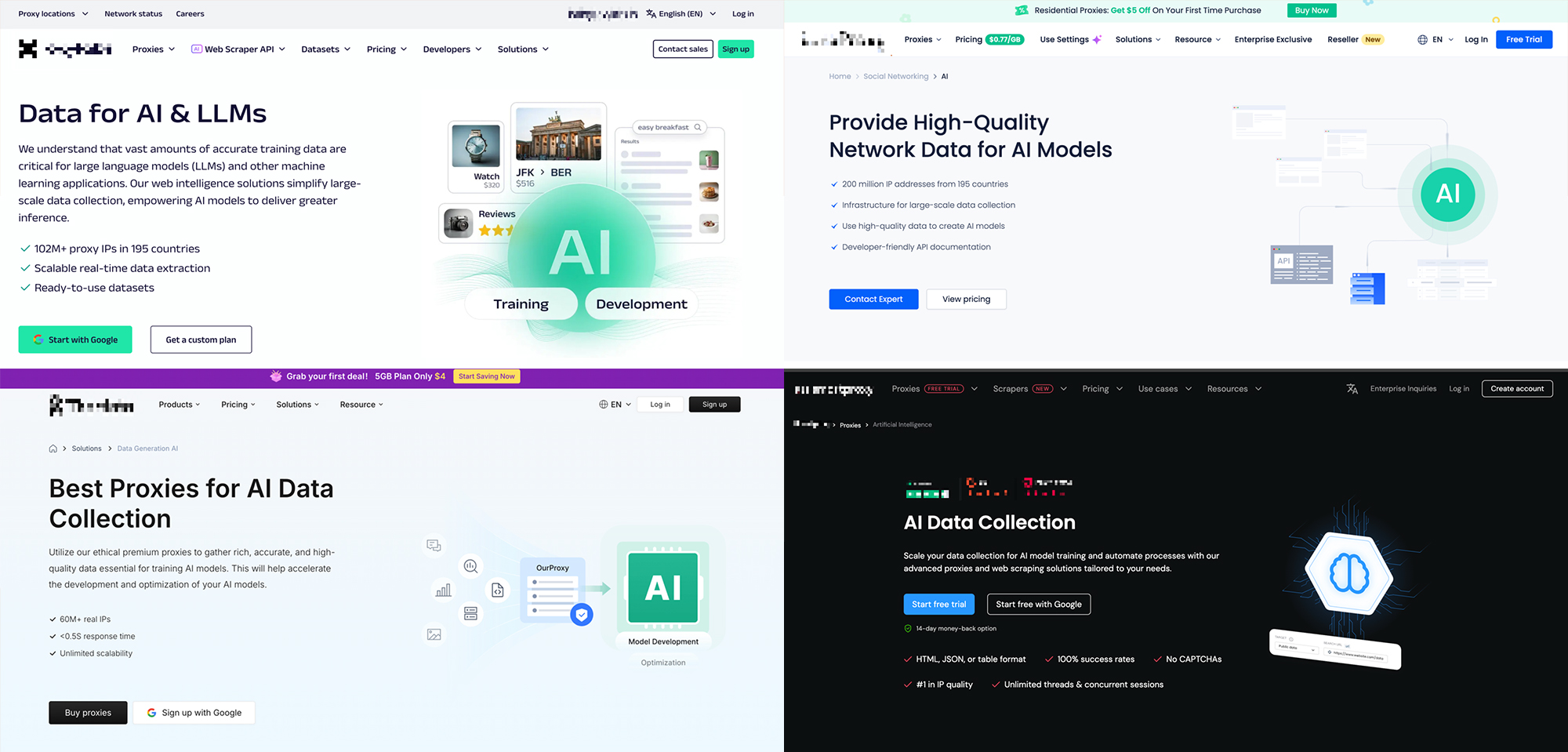 Figure 1. Examples of service providers of residential proxies for scraping data for Large Language Models.
Figure 1. Examples of service providers of residential proxies for scraping data for Large Language Models.
Despite the growth in residential proxy providers, the market lacks transparency in that oftentimes companies do not disclose how exit points are sourced. A substantial overlap of proxies offered by several providers has also been reported, which would make sense as residential proxy providers often operate under different business names that share the same infrastructure. They also offer affiliate programs for partners and utilize the proxy pools of other providers.
Residential proxies have become pivotal in facilitating various illicit activities in today's underground cybercrime ecosystem. These proxies are now essential tools in modern cybercrime business processes due to their ability to mask identities and bypass restrictions. Key use cases for residential proxies include:
- Data scraping for market monitoring and competitor analysis
- Data scraping for building large language models in artificial intelligence
- Copyright infringement
- Ad fraud and click fraud
- Bypassing antifraud systems of ecommerce systems and financial institutions
- Password and credential spraying techniques
- Social media account management, spreading misinformation on social media
- Bypassing geo-fencing restrictions
- Anonymization layers, including Operational Relay Boxes (ORB) used by APT groups
As a multipurpose tool, residential proxies can be detrimental to key business processes across a variety of verticals. For instance, they undermine the effectiveness of promotional and advertising campaigns through click fraud and business process compromise attacks. Improved abilities to bypass anti-fraud systems affect financial institutions, e-commerce platforms, and telecom companies. Additionally, the ability to scale account creation and simulate user posts and engagements on social media platforms can lead to the manipulation of public opinion, the promotion of fraudulent schemes, and even stock manipulations, all of which impact governments, financial sectors, and the general public.
BPH versus Residential Proxies
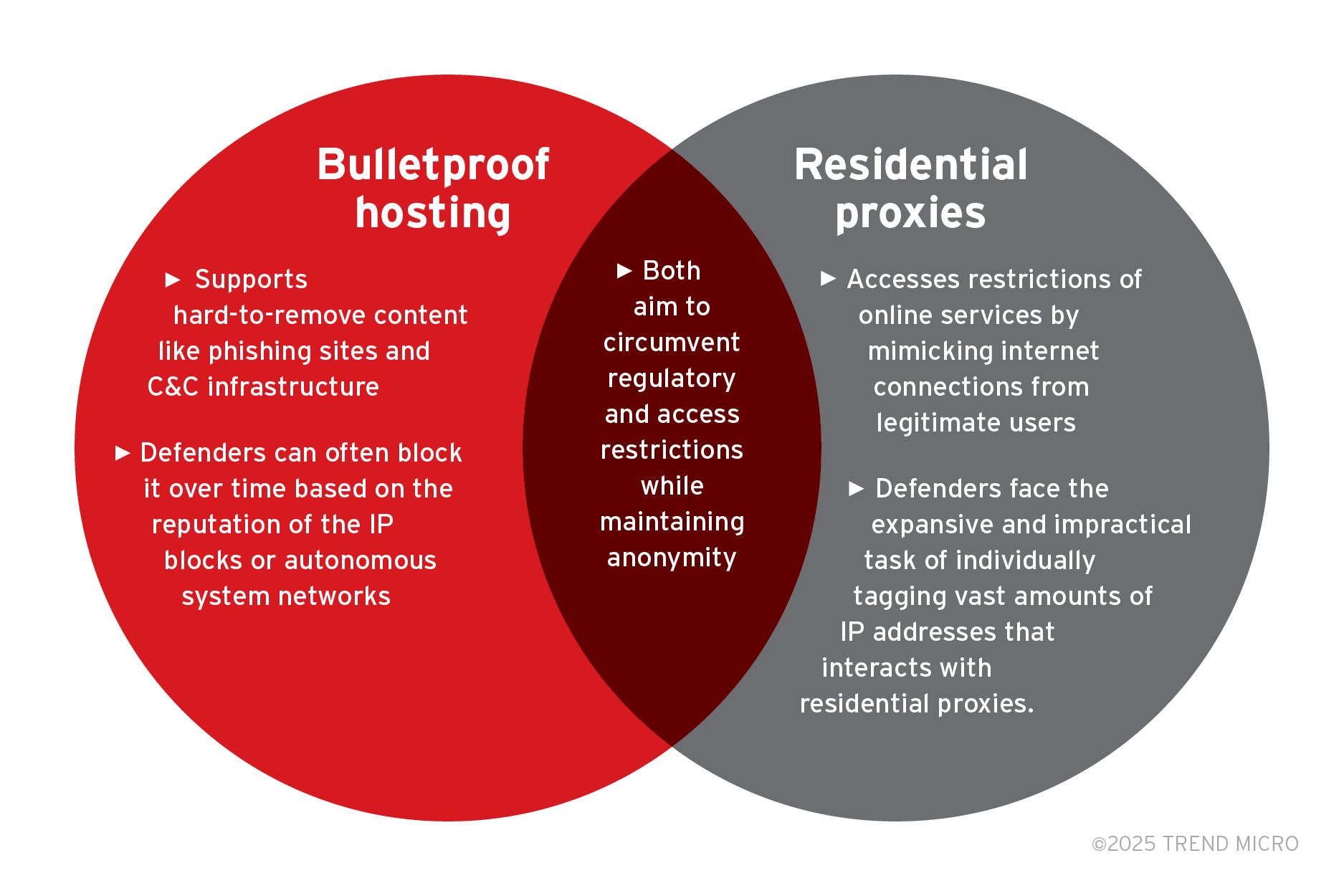
Residential proxies are often installed on equipment owned by legitimate users like laptops, tablets, phones, routers, smart TVs and set-top boxes so the number of IP addresses can be in hundreds of thousands or more. Internet traffic originating from these IP addresses is a mix of legitimate traffic from the device owners and proxy traffic from actors leveraging the devices, the vast amount of which is not practical to individually tag as malicious or not.
By using residential IP addresses, attackers can easily scale user impersonation, leverage the pools of auto-rotating IP addresses, and cost-effectively bypass many filters, including antifraud systems. This facilitates the emergence and scalability of modern criminal processes where residential proxy providers and bulletproof hosting companies stand side by side as enablers of cybercrime. Figure 2 shows an example of an underground residential proxy provider on xss.is, a forum where cybercriminals meet for business.
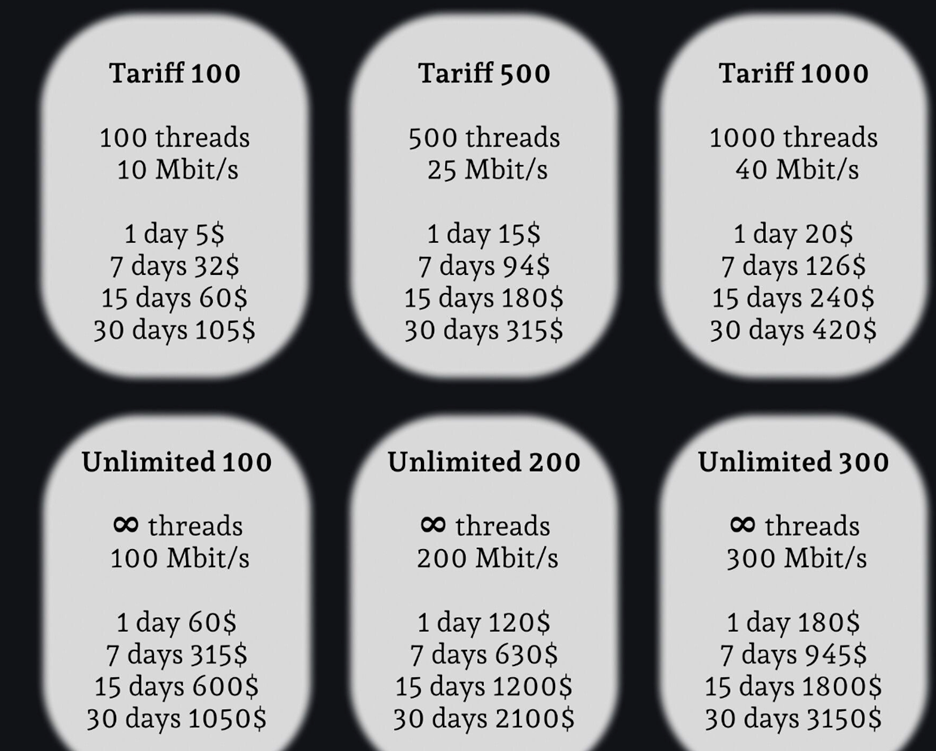 Figure 2. A pricing example of residential proxy provider services from xss.is
Figure 2. A pricing example of residential proxy provider services from xss.is
Detecting residential proxies
Having established why residential proxies are the more attractive tool for cybercriminals, detecting and mitigating attacks that leverage them pose significant challenges. Unlike ordinary proxies and VPN services, residential proxies utilize expansive pools of IP addresses. Organizations must adopt risk-based strategies to efficiently combat the misuse of residential proxies that encompasses an immense attack surface.
There are countermeasures that website and e-commerce owners can take to detect and flag access from residential proxies. One option is based on popular open-source network fingerprinting techniques called JA4+, first described by FoxIO. These fingerprinting methods are both human and machine readable and can help facilitate more effective threat-hunting and analysis. The following list includes some of the features that JA4+ fingerprinting uses to identify unique network packets:
- Packet length. This refers to the Maximum Segment Size (MSS), which is the largest amount of data that a source can send in a single TCP segment.
- TCP length. This specifies the size in bytes, of the TCP header in the TCP SYN packet
- Packet window size. This specifies the amount of data a receiver is willing to accept from the sender before acknowledging it.
- Window scale. This specifies how much of an increase can be made in the window size, which determines the amount of data a sender can transmit before needing an acknowledgment.
- Maximum segment size. This is the largest data payload size that the source will accept per packet and is dependent on the overhead in the network connection.
- Order of TCP options. Another factor that creates a unique fingerprint that creates an exact order that depends on the client and server implementations. Common options and their typical ordering include NOP (No-Operation), WScale (Window Scale), MSS (Maximum Segment Size), and SACK (Selective Acknowledgement).
These features create a specific fingerprint that can only change when the networking configuration in the operating system changes. The fingerprints might also differ based on intermediate hops that an attacker might be using in a proxy chain, thus making it a promising tool to detect the usage of residential proxies.
During our research we have done two tests: a small test using one target system (over Socks5), and a bigger test with about 1,500 target endpoints spread over 80 countries. In our first test we added packet length and TCP data length to the set of networking fingerprinting techniques. Table 1 shows the results of the first test where we recorded the network traffic from different tunnels to a website that we hosted (using port 443 and TLS/1.3 in the experiments).
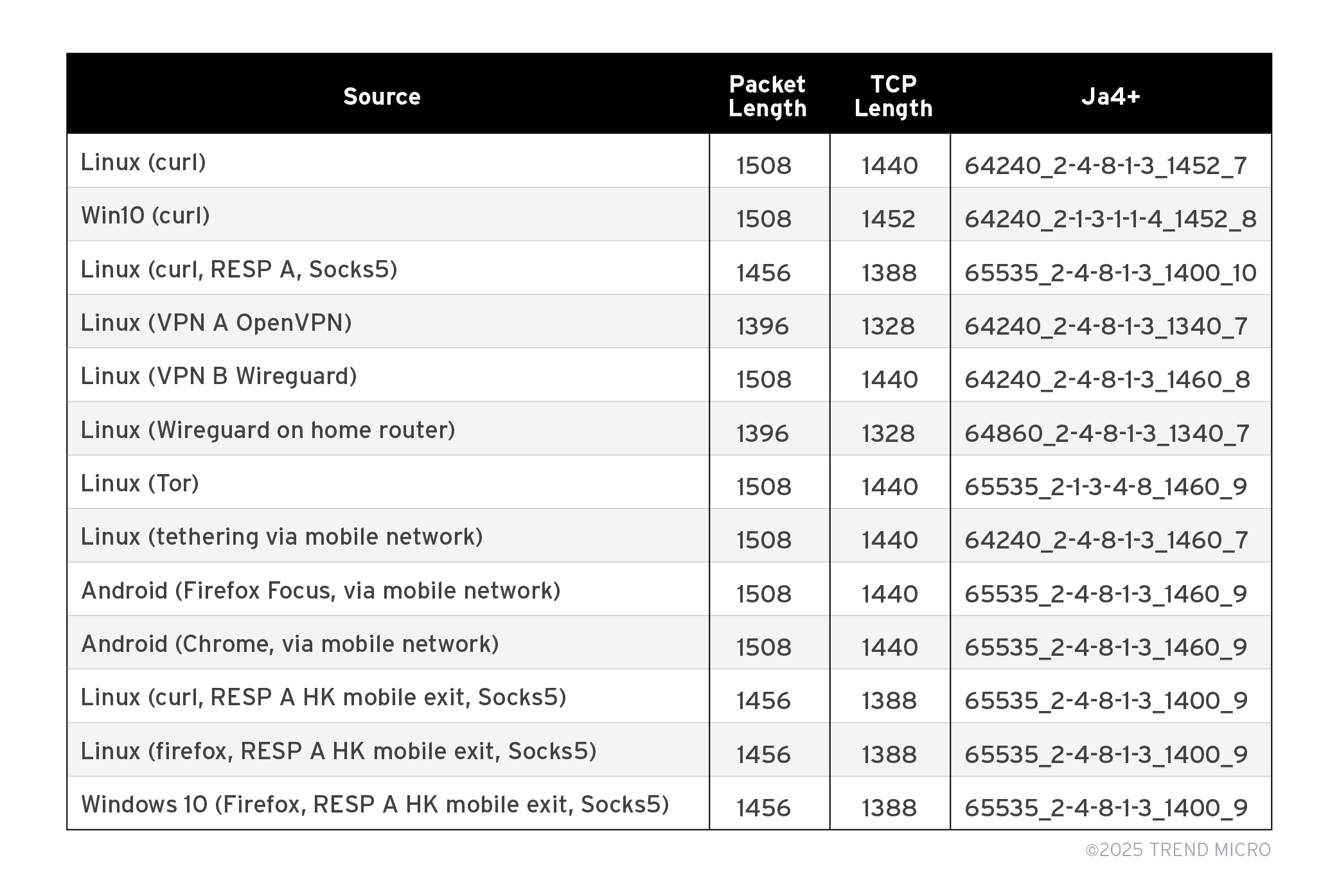 Table 1. The results of the first and smaller test where we recorded the network traffic from different tunnels to a website that we hosted
Table 1. The results of the first and smaller test where we recorded the network traffic from different tunnels to a website that we hosted
As we can see from the results, different operating systems can be classified by packet length, TCP length, and Ja4T fingerprint. The same operating system also shows different features when the networking configuration differs.
The TCP window size from the residential proxy that we have tested is 65,535, and only the connection from Tor has the same value. Moreover, its packet length is not frequently observed (1508 for most connections, 1396 for many commercial and private VPNs). The window scale size is also notably outstanding.
In the second and bigger test with 1,500 endpoints, we collected 1.5 billion SYN packets in 5 days. We used Ja4T fingerprints to detect whether the SYN packets were routed through several well-known residential proxy networks. We validated this labeling with a third-party IP reputation system and found a true positive rate of about 60%, as shown in Table 2. We assess that logging packet length and Ja4T fingerprints on internet-facing devices of enterprises and governments is a key tool to help identify suspicious incoming connections. While we do not recommend simply blocking incoming connections with these fingerprints, they can be used as an indicator along with the detection of other anomalies like a series of failed logins on a mail server or corporate VPN server.
It should be noted that network performance optimizations in commercial VPNs might also change Ja4T fingerprints according to the destination port of a connection; it is therefore recommended to refer to this blog and design your blocking policy accordingly.
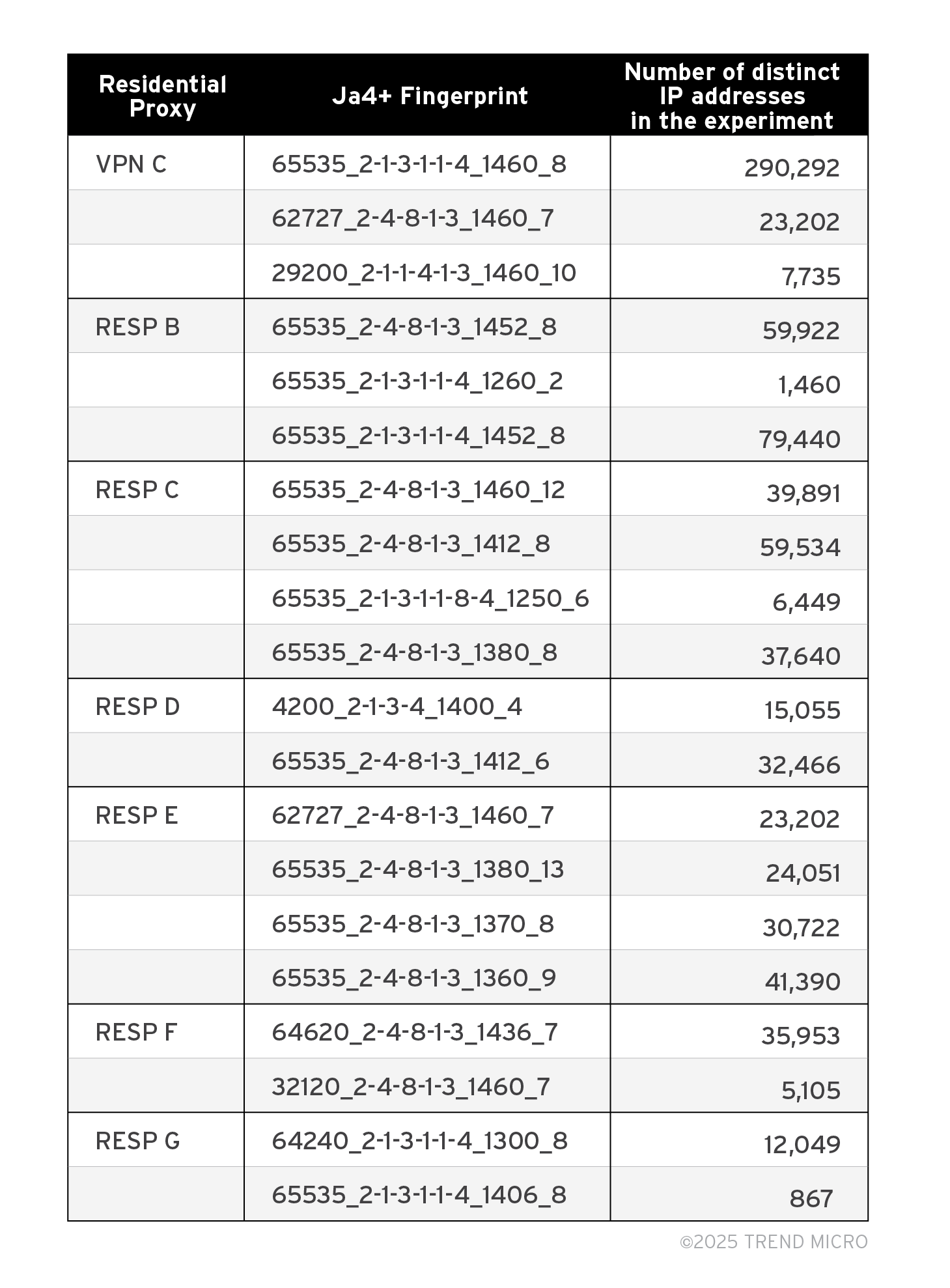 Table 2. A breakdown of the number of distinct IP addresses detected per Ja4+ fingerprint in our experiment.
Table 2. A breakdown of the number of distinct IP addresses detected per Ja4+ fingerprint in our experiment.
We can also notice how the infrastructure of a residential proxy shapes the packet size and TCP length as seen in Table 3. Regardless of whether it’s a DSL or cellular connection, the fingerprints of network traffic through our residential proxy under test always have 1456 packet length and 1388 TCP length with TCP window size of 65535.
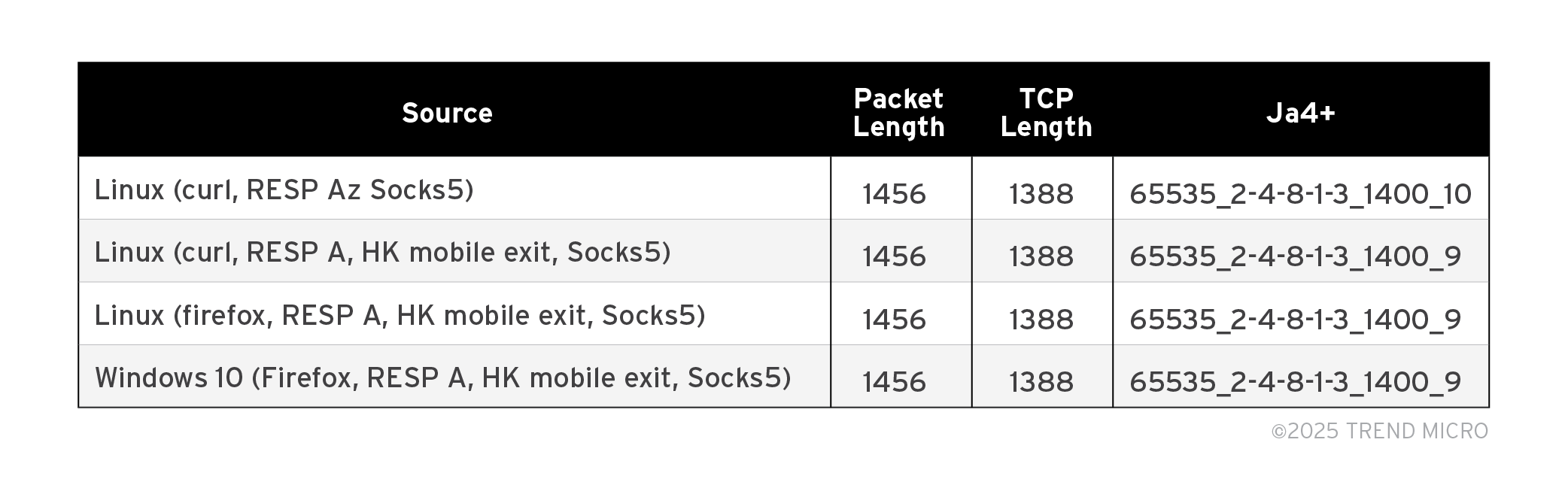 Table 3. The infrastructure of a residential proxy affects the packet and TCP length of the fingerprint.
Table 3. The infrastructure of a residential proxy affects the packet and TCP length of the fingerprint.
FoxIO has also proposed a way to calculate the estimated distance from a client to the server and spot possible tunneling. However, we didn’t find the results significantly stable. For a supportive example, “Wireguard on Home Router” has a Ja4L of 3,040 µs. 3040 (µs) * 0.206 (km/µs) / 1.5 (delay factor < 15 hops) = 417.5 (km). With a geo-IP database, such as MaxMind GeoIP, we know that the distance of the client IP to the server is less than 100 kilometers. It therefore suggests that there must be a tunnel in between. However, cellular data and access from a virtual machine might also be a factor in the increase in latency; creating room for error in wrongly flagging a normal connection as residential proxy.
Residential proxy providers could also adopt a modular approach capable of loading various software modules for tasks like proxy services, website scraping, and fraud activities. This has already been seen in Lemon Group’s business and monetization strategies built on pre-infected devices. This approach can be done on devices that support Android Open Source Project (AOSP), but other residential proxy providers can use other modular distribution techniques that don’t rely on pre-infected AOSP-supported devices. This modular method allows residential nodes to operate independently, potentially bypassing advanced network fingerprinting techniques and complicating defenses against residential proxies. We further discuss different kinds of residential proxies in the appendix.
Conclusion and security recommendations
Residential proxies are among the latest in evolving business models driven by the need for cybercriminals to adapt to improved defense strategies. By capitalizing on emerging technologies and changes in user behavior, residential proxies transform the traditional bulletproof hosting and proxy markets. Cybercriminals leverage vast pools of residential IP addresses to effectively bypass antifraud systems and impersonate legitimate users, posing yet a new set of challenges for cybersecurity defenders. Residential proxies can also be used for password brute force or other malicious activity without a proper solution in place.
The rise of the criminal use of residential proxies makes blocklists and allow-lists of IP addresses much less effective, especially because their use leads to a mix of malicious and benign traffic from residential IP addresses of millions of home internet users. Therefore, there is a need for more granular filtering, separating benign and malicious traffic based on network connection fingerprints and session characteristics, instead of being based on IP address reputation alone. Security measures like DDI (domain name system [DNS], dynamic host configuration protocol [DHCP], and IP address management [IPAM]) can be used to block malicious activities based on the specific patterns of attacks.
Large Content Delivery Networks (CDN) can train Artificial Intelligence (AI) models to separate between benign internet user traffic and bot traffic. For several years, session classification has already been done by large content service providers by looking at mouse movements or using challenge–response tests.
A similar approach that leverages more data sources by integrating deeper correlations between network flows and the data used in key business processes and financial processes can also improve detections. This approach can be beneficial to defenders of e-commerce, financial, media platforms, and other enterprises with significant web presence. Additionally, advanced classification by session and network connection fingerprinting is also possible, as discussed in the previous sections. Network packets that are sent through multiple proxies by an attacker from a residential internet connection have a different technical fingerprint than network packets that are sent by the owner of the residential internet connection themselves.
While Ja4T fingerprints are well suited to detect incoming connections from VPN services and residential proxies, older fingerprinting techniques like JA3 and JA3S are also a useful tool for defenders. JA3 and JA3S can be used to cluster IP addresses that are being used in the same kind of campaign against internet facing servers. To detect the usage of proxies, VPN services, and residential proxies, we recommend defenders to use Ja4T instead. Ja4T fingerprinting can address the problems SOC teams face when they must differentiate between traffic coming from legitimate users of residential IP addresses and traffic coming from the exact same IP addresses but then generated by a third-party user of a residential proxy service provider.
We foresee that some residential proxy providers will turn to a modular approach capable of loading various software modules for tasks like proxy services, website scraping, and fraud activities. This model has been in use by the Lemon Group actors and other groups in the far east using pre-infected devices. Other residential proxy providers may follow using the modular approach while keeping their traditional distribution techniques like SDKs. In this modular approach the residential nodes can perform tasks on their own and therefore it will be possible to defeat more advanced fingerprinting techniques based on network packet characteristics that are typical for proxied connections over multiple hops. This will make the defense against residential proxies even harder.
To combat the misuse of residential proxies, organizations must adapt to risk-based strategies that include moving away from reliance on IP reputation services alone and adopting more granular filtering techniques based on network connection fingerprints and session characteristics. Advanced detection mechanisms, such as JA4+ network fingerprinting and AI-powered security platforms and solutions like Trend Micro’s CREM offer promising techniques for identifying connections that originate from residential proxies. These techniques can help defenders differentiate between legitimate use of residential IP addresses by the owners and abuse of these same IP addresses by criminal users of residential proxy providers.
Trend Vision One™ – Endpoint Security can be an enterprise’s additional layer of defense in the case of successful malicious use of residential proxies. This all-in-one endpoint protection with native threat detection and response, proactive risk mitigation, and centralized visibility streamlines operations and enhances an organization’s IT security posture. This solution extends protection to other security layers and integrates with third party solutions, meeting the security teams at whatever stage of the security journey they are on, giving them full visibility and critical insights into their IT and OT infrastructure.
To mitigate the risks of residential proxy providers, we recommend that end users should not install software that is offered for free or at a reduced price, in return for making their internet bandwidth available to a residential proxy provider. The risks of engaging with residential proxy providers far outweigh the promised benefits.
Additionally, law enforcement can address the most problematic and abusive residential proxies by starting active investigations into the abuse of these services.
This appendix further discusses bulletproof hosting and how it enables cybercrime. It also discusses residential proxies and the different ways they are provisioned. Download the appendix here.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One