 Download Toll Fraud, International Revenue Share Fraud and More: How Criminals Monetise Hacked Cell Phones and IoT Devices for Telecom Fraud
Download Toll Fraud, International Revenue Share Fraud and More: How Criminals Monetise Hacked Cell Phones and IoT Devices for Telecom Fraud
by Craig Gibson (Principal Threat Defense Architect, Forward-Looking Threat Research Team), and Europol
Telecommunications fraud is by no means a new crime. It encompasses a wide range of modi operandi, each of which takes multiple forms and many of which have existed for over a decade. Until recently, many of these crimes had not featured significantly on the radar of law enforcement. However, developments in technology, the industry, and criminal capabilities have turned telecommunications fraud into a multi-billion euro criminal industry.
Two major types of telecommunications fraud can be identified: subscription fraud and toll fraud. Subscription fraud is the use of carrier business process compromise (BPC) by an attacker to pose as a legitimate customer and gain access to one or more customer accounts that can be abused. Toll fraud, which is the more damaging, involves exploiting how money moves within the global telecom network. Typically, the amount of money stolen in each event is much higher, often going beyond €1 million. Prosecuting this kind of event is usually more difficult given the cross-border nature of the crime.
These crimes have a significant impact on customers, including the loss of all connectivity due to being blocked at the carrier (or telecom infrastructure provider) level. Customers can also receive enormous bills, be mistakenly blocked by their own carriers or be blocked globally by all carriers. During these crimes, the criminals pose as real customers and carriers. The customers may, in some cases, experience prolonged outages as they are unable to persuade the carriers involved that they are actually the victims and not the perpetrators.
Inter-carrier trust and how it gives rise to fraud
International revenue share fraud (IRSF) is a type of crime relying on the “gentlemen’s agreement” between telecom carriers, in which they have an unspoken pact not to hack or attack one another. This global agreement is called inter-carrier trust, similar to the relationship banks have with one another. When a miscreant entity exploits that trust, it can manipulate the flow of traffic — money in the case of banks, expensive calls in the case of telecom carriers — to perform activities such as fraud and money laundering. As for miscreant carriers who have joined the inter-carrier trust community, they can commit traffic redirection abuses, including wiretapping (to record conversations and search for credit card numbers and passwords, for example) and injection of malware. These often include IRSF methods.
IRSF is attractive to criminals because of the inherently low risk of the attack: It can be performed at a distance and the received money comes from redirecting the inter-carrier billing for expensive telecom traffic. This redirected money moves from the victim’s carrier to the attacker’s carrier in such a way that it can be “withdrawn” quickly in the form of payment from a complicit carrier.
Since these frauds can be executed against the internet of things (IoT), the sheer number of devices that can be possibly involved has to be considered. Many fraud cases may be more profitable and more difficult to detect when performed against, say, refrigerators or traffic lights. If fraud originates from IoT-critical infrastructures, such as in smart cities, and is consequently blocked as fraud, the IoT-enabled deployments would go silent. Therefore, cities and organizations that are using telecoms in operations should improve their security and fraud prevention posture to ensure the continuity of services.
The popularity of IRSF in particular and telecom fraud
While fraud primarily poses financial damage, the secondary impact, such as the use of the crime’s proceeds to pay for activities like terrorism, cannot be ignored.
Inter-carrier trust involves multiple methods that can be abused to bring about toll fraud. One of these is the use of international premium rate numbers (
If, for instance, a telecom carrier colludes with criminals to make a profit, cell towers (and all mobile phones nearby them) will have very little in the way of anti-fraud controls. Some criminals even go out of their way to set up their own cell towers (also called rogue femtocells) that can affect devices, including wireless IoT devices, within a 100-meter radius or more.
These risks can originate from a wide range of technologies, including 5G, traditional trunking, long-distance networks, and satellite. They may be aimed at phones (hacking, for example), networks, carriers, or the IoT.
While the fraudulent activity of toll traffic compromise is very profitable, it can be detected although often only after the fraud has occurred. If the victim carrier detects the fraud, it can report the source carrier to the global telecom authorities, which effectively “block” the perceived source of the crime. However, the perceived source of crime is not always the actual source of the crime. Criminals can originate their attack from another source and have it appear as the most profitable victim. It is then the victim, not the attacker, who is consequently blocked or subjected to a denial-of-service (DoS) attack, which may have been the intent in the first place. In some cases, such as in island nations, on cruise ships, and at other similar locations, they are even blocked entirely.
How the fraud can be carried out
When a miscreant adds itself to the circle of inter-carrier trust as a supplier to a carrier, a vendor of carrier equipment, a “gray” carrier covertly partnering with criminals, or a “black” carrier reselling hacked carrier services, the technical sophistication of an attack is moderate. However, when a miscreant creates its own “war rig” carrier infrastructure (as represented in Figure 1 below), which could be both financially cheap and physically small, the attack becomes more sophisticated. From the perspective of an attacker with a functional war rig, the attack becomes more flexible, more profitable, and less risky
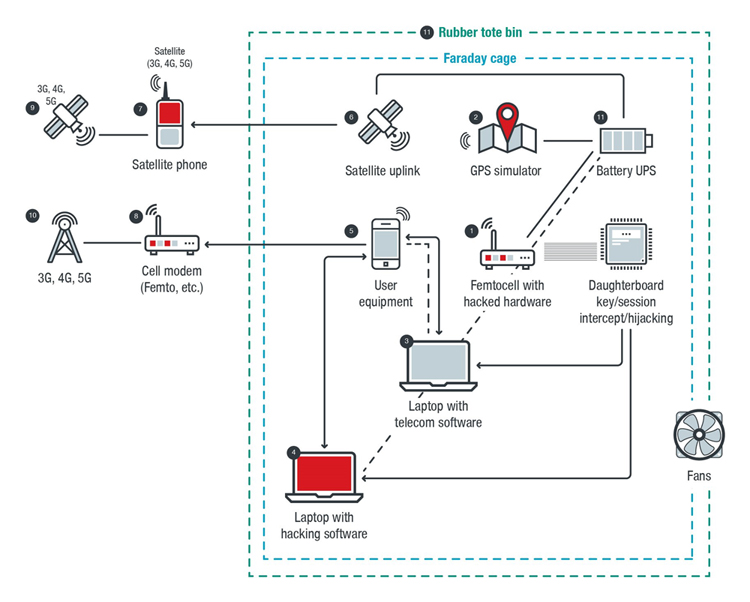
1. Radio war box – Femtocell with hacked hardware, which allows arbitrary information to be fed to and from the user equipment (UE).
2. GPS war box – GPS simulator, which allows arbitrary information to be fed to the UE and provokes a change of state such as roaming and falsification of the apparent location that the attack is originating from (hiding the location of the attacker).
3. Telecom war box – Laptop with telecom software, which provides a sense of “reality” and technical consistency to the changed state of the mobile device.
4. Traditional information technology (IT) war box – Laptop with hacking software, which collects, sorts, and manages data generated by the attack.
5. Victim (“user equipment”) – One or more mobile devices such as those connected to the IoT (note that the victim UE can be outside the shield represented by the dotted line to perform bulk attacks against people or devices within range).
6. Satellite war box – Satellite uplink, which routes the attack across satellite infrastructure to provoke a telecom billing response from the telecom network on the other side of the satellite.
7. Satellite phone – A point to launder data as it goes back to the telecom network.
8. Cell modem,
9. Typical telecom satellite with common attributes.
10. Cell tower or other base stations (5G, 4G, 3G, LPWAN, etc.) – These allow arbitrary information to be fed to the telecom network.
11.
It is also important to note that telecom fraud grows substantially in impact each year. However, the necessary cost and sophistication to execute it decreases. Attacks have also recently gained attention in the cybercriminal underground in anticipation of the widespread use of 5G technology. The nature of 5G amplifies the financial impact of frauds such as IRSF due to the dynamic scalability and openness of billing of the technology.
Defending against telecom fraud
The fight against fraud should not be something that either private industry or law enforcement should shoulder alone. Forming public-private partnerships based on trust and information sharing is a fundamental strategy for success. Europol has already demonstrated how such initiatives can work effectively, with hugely successful industry-spanning actions targeting a number of areas of fraud, including e-commerce, airline ticket fraud, and money mules. To this end, in 2017 Europol established the Cyber Telecoms (Cytel) Fraud Working Group, with its initial focus being on the largest class of cyber telecom fraud: IRSF. The group consists of law enforcement officers from 18 countries from around the world, the GSM Association (GSMA), the Pacific Island Telecommunication Association (PITA), the International Telecommunication Union (ITU), Trend Micro, and more than 35 global telecom companies.
In April 2018, during a two-week action by the Working Group, 250,000 fraudulent transactions were reported and over 100 cases were reported to law enforcement, resulting in 25 new investigations. Additionally, over €13.13 million in fraudulent payments was blocked. While the focus of the action was IRSF, the activity also captured a wide variety of other telecom frauds, with
As discussed, toll fraud is a financial crime executed in the telecom domain. As such, it can be tracked at a financial level through the correlation of financial and telecom evidence. As a multijurisdictional technology crime, it can be predicted through intelligence fusion, where more intelligence means faster detection and more credible prediction.
As a financial telecom cybercrime, it can be detected well in advance through predictive analytics such as those employed by new technologies. One example is the virtual security architecture called security orchestration, a rules-based network management strategy that can easily adopt financial and anti-fraud rules as part of its native network management approach. Through the correlation of telecom events (such as calls, radio communications, and messages) and available threat information (such as IP addresses and reputation data), security orchestrators will be able to combat increasing telecom fraud incidents.
The prevalence of old and new frauds that use emerging technologies such as the IoT and 5G warrants the integration of 5G machine learning and artificial intelligence to create new models capable of being orchestrated. This way, enterprises’ security posture will evolve in pace with attackers’ techniques. Moreover, this will help organizations prepare against the different types of fraud that can put them in a bad light and negatively affect legitimate customers. This approach is also especially critical in regard to organized crimes and their use of criminal artificial intelligence (CAI).
Conclusion
Telecommunications fraud represents a serious threat to the telecommunication industry, resulting in loss of revenue, which is undoubtedly passed onto customers. It also represents a significant source of criminal revenue, which could potentially be reinvested in other serious criminal activities.
Experience in other areas of fraud has shown us that collaborative public-private partnerships are a prerequisite for effectively tackling this threat. Unfortunately, relationships between law enforcement and the telecommunication industry have in most cases not reached the level of trust and cooperation as those seen in, for example, the financial sector. The Cyber Telecoms (Cytel) Fraud Working Group is the first step toward addressing this.
More work is needed to determine how criminals can obtain the telecommunication equipment needed to carry out such attacks and how they can become part of the circle of inter-carrier trust. Solutions to these problems, and other aspects related to cytel
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One