Ransomware: What It Is and How You Can Protect Yourself

An office employee checks his email, sees a message that looks important, and clicks on the link. Later, a message flashes on his computer screen that says his system—and all the files in it—has been locked. He has 72 hours to pay a ransom to unlock it, or lose the files forever.
While the message and methods vary, a typical ransomware attack scenario shares the same common elements: malware that prevents the user access to the infected system, and a demand for payment. Unfortunately, it's a scenario that plays out more and more frequently these days.
Ransomware is arguably one of the most dangerous types of computer malware because of how it works and how it affects its victims, but despite all the warnings, many users still fall victim to this type of threat. But what is ransomware really? When most people think of computer security or privacy, the usual suspects come to mind—malware such as Trojans, worms, and keystroke loggers that steal credentials to gain access to online accounts and corporate networks.
Ransomware is a type of malware that locks your computer screen and prevents you from accessing your files until you pay a certain fee or “ransom”, which involves handing your password or your money to the anonymous attacker. In the past, ransomware was designed to shut your systems down by locking computer screens with a warning message that demands payment. They've been around for a long time, and have taken a number of different forms, but just like any other successful endeavor, ransomware has also evolved into a number of newer, more dangerous variants.
In 2013, a new type of ransomware called crypto-ransomware emerged. An example of this is CryptoLocker, a variant that doesn't just lock its victim's system—it also encrypts the files. This is to ensure that the victim will still pay up even if the malware itself was deleted. Over the years, more common variants such as Curve-Tor-Bitcoin (CTB) Locker were discovered, that, like other newer ransomware variants, will encrypt the victims' files. However, instead of dropping instructions on how to decrypt the files, it displays a large dialog box that prompts the user to enter a transaction ID.
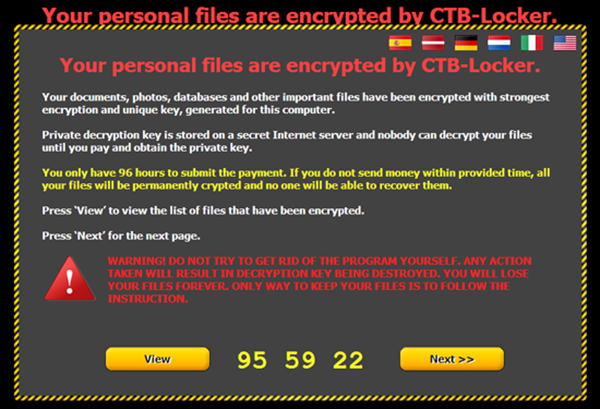
Recently, we’ve seen new "features" being added to CTB Locker, such as a “free decryption” service (designed to prove that it's worth it to pay up), an extended deadline to decrypt the files (after all, the attacker won't gain anything if no one pays the ransom after the deadline), and an option to change the language of the ransom message and instructions. The new lures arrive through spammed emails feigning important updates and notifications from popular services such as Google Chrome and Facebook.
[More: No easy solutions for crypto-ransomware]
How does ransomware work?
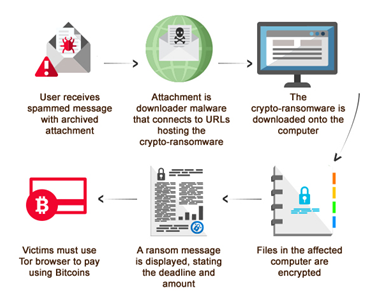
Ransomware sometimes come in the form of a fake antivirus installer, and have been relying on social engineering tricks to lure or scare users into clicking on links or giving their account credentials. A person may unwittingly download and install ransomware by opening an infected file from a malicious email or website. The nature of a ransomware attack largely depends on the motives of the attacker. Essentially, the attacker creates a code designed to take over a computer and hijack files. Once executed in the system, the ransomware can either lock the computer screen or encrypt predetermined files.
In the first context, the infected system will display a full-screen image or notification that prevents victims from using their computers unless the ransom is paid. The message also includes instructions on how users can pay. In the second scenario, the attacker gives the victim a time limit to pay for locked files, documents, spreadsheets, and other important files. However, paying does not guarantee access to the infected system. Moreover, infected systems run the risk of being rendered unusable because once files are encrypted, anti-malware tools are only able to remove the malware variant from the system, but still leaves the encrypted files unusable.
The ransom amount varies, ranging from a minimal amount to hundreds of dollars, and is paid via online payment methods. The attacker still profits no matter how meager the amount, as they can make their money from the overall numbers of computers they infect. If the user fails to pay, the attacker could create additional malware to further destroy the files until the ransom is paid.
[More: From infection to payment procedures, see how ransomware works in this infographic]
What can you do to avoid being a ransomware victim?
As dangerous as ransomware is, simply being aware and staying updated with the latest ransomware trends can go a long way in securing your data and systems. Here are helpful tips on how you can defend yourself from a likely attack.
Scrutinize emails before opening them
Be wary of emails from unverified sources. You can check by communicating directly with the purported sender to confirm if they sent the messages.
Avoid clicking embedded links found in unverified emails
Such social engineering tricks can lead to the download of ransomware. Additionally, be wary of sites that prompt you to enter a CAPTCHA code as this could be linked to a ransomware attack. To check its validity, you can use free services like Trend Micro Site Safety Center to verify the reputation of the site.
Back up your important files
While prevention is always better than the cure, having a backup of important files can at least lessen the potential damage done by a ransomware attack. While being locked out of your own system is always a bad thing, at least it's not a total disaster since you can always retrieve your important files. The 3-2-1 backup rule applies here—three backup copies of your data on two different media, and one of those copies in a separate location.
[More: What, When, Where and Why You Need to Back up and How to do it]
Regularly update software, programs, applications
Updating them to the latest versions can provide an added layer of protection against online threats as some ransomware arrive via vulnerability exploits.
Use a layered protection suite
Doing so can detect threats before they enter your system. Security solutions like Trend Micro Security can block dangerous websites, including harmful links found in websites, social networks, emails and instant messages, and safeguards against viruses, phishing, and other online threats.
For those dealing with locked screens because of a ransomware infection, the Trend Micro AntiRansomware Tool 3.0 can be run from a USB drive.
[More: View the latest articles and updates on our Ransomware page]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One