The Security Features of Blackberry 10
 View infographic: The Security Features of Blackberry 10
View infographic: The Security Features of Blackberry 10
Nearly two decades ago, before smartphones were all the rage, payphones and beepers made up the very few communication devices we relied on when a landline wasn’t available. By the late 90s, we started using cellular phones to make calls from wherever we were, and personal digital assistants (PDAs) to organize our personal information on the fly.
In 1999, we were introduced to the BlackBerry®, one of the pioneers of the trend. At first, we were overwhelmed by its Qwerty keypad and Bluetooth capabilities, but to date, BlackBerry has come a long way to improve its overall functionality and design. Though it’s facing stiff competition against other more stylish smartphones, the latest Blackberry® 10, much like its predecessors, sticks to its strength. It offers a strong approach to security, making it an ideal enterprise-grade device.
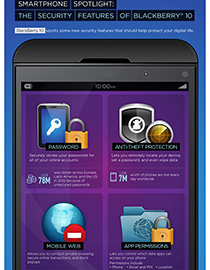
Large-scale businesses who rely on mobile devices to hold mission-critical data, and even individuals who just want to protect their personal information, can actually benefit from Blackberry 10’s improved security features. They cover most, if not all, the gaps threats can use to infiltrate a device.
It has a strong password option that prohibits any unauthorized physical use. It has anti-theft protection which lets you wipe all your data in case of device loss. It has a private browsing option as well as pup-up blocking capabilities. The smartphone even lets you control the permissions you grant each app you install.
As an add-on, Trend Micro partnered with BlackBerry for its special app screening feature. This measure ensures that BlackBerry apps are screened for malware. All these built-in security features allow users to make the most of their smartphone experience by worrying less about data loss or mobile threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization
- Agentic Edge AI: Development Tools and Workflows

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One