While iOS devices generally see relatively fewer threats because of the platform's walled garden approach in terms of how apps are installed, it’s not entirely unbreachable. We saw a number of threats that successfully scaled the walls in 2016, from those that abused enterprise certificates to ones that exploited vulnerabilities to curtail Apple’s stringent control over its platforms.
This is further exemplified by iXintpwn/YJSNPI (detected by Trend Micro as TROJ_YJSNPI.A), a malicious profile that can render the iOS device unresponsive. It was part of the remnants of the work of a Japanese script kiddie who was arrested in early June this year.
While iXintpwn/YJSNPI seems currently concentrated in Japan, it won't surprise anyone if it spreads beyond the country given how it proliferated in social media.
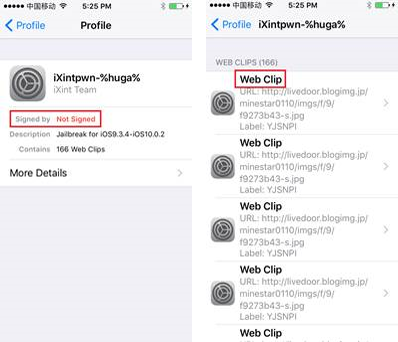
iXintpwn/YJSNPI first appeared in late November 2016 via Twitter—and subsequently over YouTube and social websites—posing as an iOS jailbreaker named “iXintpwn”. It’s also the name of the website the malicious profile is hosted in. The overflow of icons it places over the affected device’s screens appears as “YJSNPI”. It was also known as “Beast Senpai” (senpai means teacher or mentor in Japanese) as a reference to the image used as a meme in Japanese online forums.
Regardless if it was created as a prank or to gain notoriety, its attack chain is notable, as attackers can weaponize the iOS feature iXintpwn/YJSNPI misuses: unsigned iOS configuration profile.
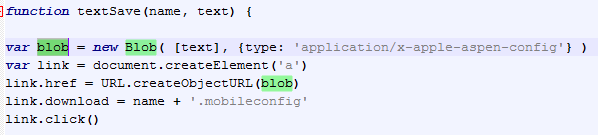
YJSNPI can proliferate by accessing the website hosting the malicious profile, especially via Safari. The malicious site contains a JavaScript, and responds with a blob object (the malicious profile) when the user accesses it. On iOS devices, the latest Safari accepts this server response and will automatically download the profile.
Figure 1. Code snippets showing YJSNPI as a blob object (top), and how it’s retrieved in Safari (bottom)
Abusing iOS Configuration Profile
An iOS configuration profile enables developers to streamline the settings of a huge number of devices, including email and exchange, network, and certificates. Enterprises employ these profiles to streamline the management of homegrown apps and corporate devices, for instance. A configuration profile can also customize the settings of a device’s restrictions, Wi-Fi, Virtual Private Network (VPN), Lightweight Directory Access Protocol (LDAP) directory, Calendaring Extensions to WebDAV (CalDAV), web clips, credentials, and keys.
Evidently, a malicious profile can be used to manipulate the settings, i.e., divert the device’s traffic. Examples of this include the information-stealing Wirelurker and adware-laden repackaged apps from Haima.
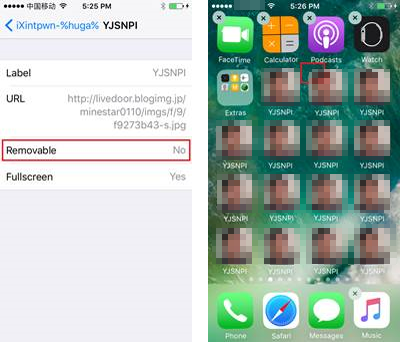
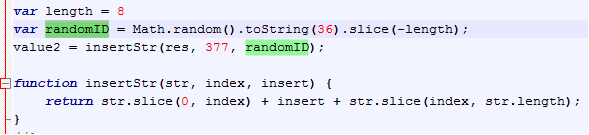
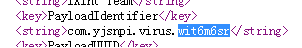
In iXintpwn/YJSNPI’s case, it uses an unsigned profile and sets it to “cannot be deleted” to make it more difficult to uninstall, as shown below. For persistence, the value for “PayloadIdentifier” string is randomly generated via JavaScript. Note that iOS has countermeasures in place for installing signed or unsigned profiles, which requires direct user interaction. The only difference is how these profiles are displayed—signed profiles are indicated as “verified”, for instance.
Figure 2. iXintpwn/YJSNPI using an unsigned profile
Figure 3. The malicious profile set as unremovable (left) and the icons overlaying the device screen (right)
Figure 4. Code snippets showing how the PayloadIdentifier’s value is generated (top and middle) that results into various iXintpwn configuration profiles (bottom)
iOS SpringBoard Icon Overflow
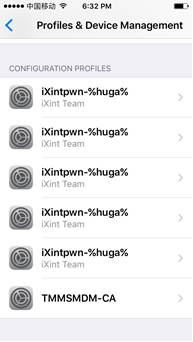
Upon iXintpwn/YJSNPI’s profile installation, an icon will be awkwardly superimposed on the home screen. Clicking it results in an overflow of YJSNPI icon-laden screens that crashes SpringBoard—the application that manages the home screen and controls how apps are displayed and launched. The YJSNPI icons are clickable but will only show a bigger resolution of the icon’s image. It is also during this overflow of icons that the device becomes unresponsive.
 Figure 5. iXintpwn/YJSNPI’s icon hovering in the home screen (left); screenshot of an iPad’s home screen populated with YJSNPI’s icons (right)
Figure 5. iXintpwn/YJSNPI’s icon hovering in the home screen (left); screenshot of an iPad’s home screen populated with YJSNPI’s icons (right)
Mitigation and Best Practices
Thankfully, YJSNPI can be removed from the device despite it being set as unremovable. Affected users can use Apple Configurator 2, Apple’s official iOS helper app for managing Apple devices via a Mac, to find and remove the malicious profile under the Actions function.
However, there are caveats. YJSNPI has to be fully installed or the icons won’t be removed—that is, the profile will not show up when Apple Configurator 2 is run. There is also no Windows version of Apple Configurator 2.
Follow best practices to improve mobile device security, especially if the iOS device you use runs in a BYOD environment. Regularly update and patch your iOS and apps and download only from the App Store or trusted sources. Beware of the risks of jailbreaking, and be aware of the permissions you grant to unknown or suspicious apps or profiles. App developers are likewise recommended to secure the apps they develop so that their apps can't be abused to spread malware.
Trend Micro Solutions
End users and businesses can also benefit from multilayered mobile security solutions such as Trend Micro™ Mobile Security for Apple devices (available on the App Store). Trend Micro™ Mobile Security for Enterprise also provides device, compliance and application management, data protection, and configuration provisioning, as well as protects devices from attacks that leverage vulnerabilities, preventing unauthorized access to apps, as well as detecting and blocking malware and fraudulent websites.