Ransomware
Massive WannaCry/Wcry Ransomware Attack Hits Countries
Previously WannaCry was downloaded from Dropbox URLs, but new variants are now spreading via this previously found SMB vulnerability. This has resulted in one of the most serious ransomware attacks to hit users across the globe.
Updated on May 13, 2017, 8:11 AM PDT to add information regarding services.
Updated on May 14, 2017, 10:15 PM PDT to add information regarding propagation.
Updated on May 20, 2017, 09:15 PM PDT: Limited decryption support for the WannaCry (WCRY) Ransomware has been added to this tool (primarily for Windows XP). Please read the guide here.
Earlier this year, two separate security risks were brought to light: CVE-2017-0144, a vulnerability in the SMB Server that could allow remote code execution that was fixed in March, and WannaCry/Wcry, a relatively new ransomware family that was found in late April. Previously WannaCry was downloaded from Dropbox URLs, but new variants are now spreading via this previously found SMB vulnerability. This has resulted in one of the most serious ransomware attacks to hit users across the globe.
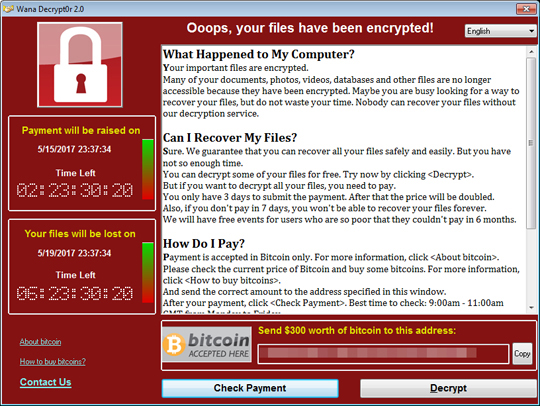
The ransom note demanded a payment of US$ 300 be made in Bitcoin; note that this ransom demand is already lower than the amount asked for in the earlier attacks. Aside from the initial attacks in the United Kingdom, other countries were also affected in large numbers.
Trend Micro detects the variants used in this attack as RANSOM_WANA.A and RANSOM_WCRY.I. Customers are already protected against this threat through Predictive Machine Learning and other relevant ransomware protection features found in Trend Micro XGen™ security.
[RELATED: Identify the gaps in your existing endpoint protection solution using the free Trend Micro Machine Learning Assessment tool.]
Infection Vector
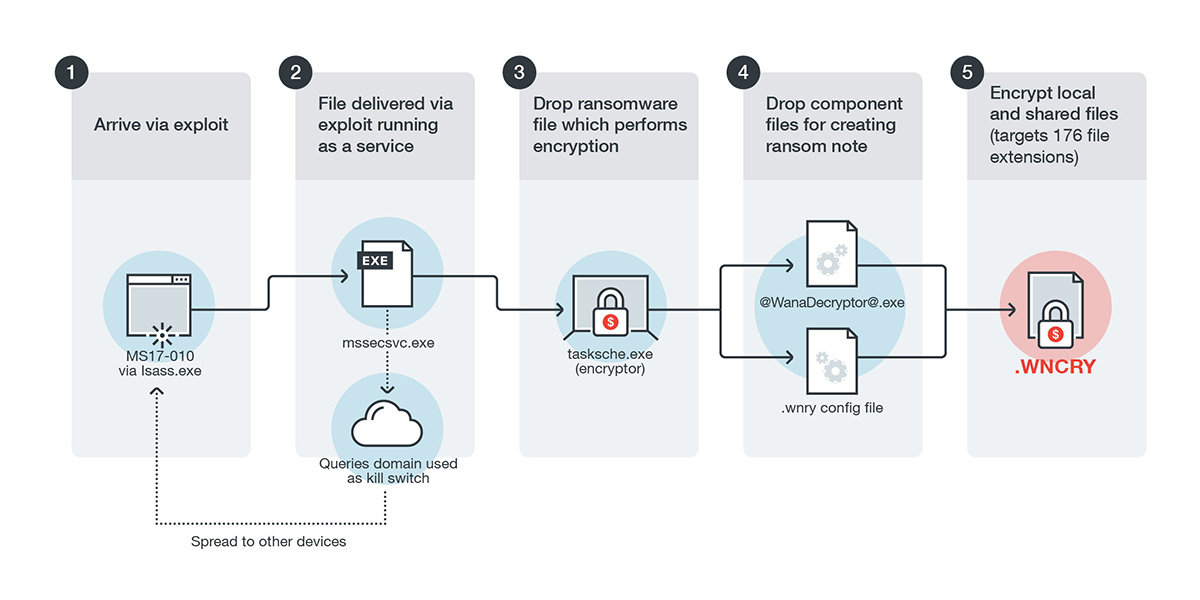
The vulnerability used in this attack (code named EternalBlue)was among those leaked by the Shadow Brokers group that was allegedly stolen from the National Security Agency (NSA). The vulnerability was exploited to drop a file on the vulnerable system, which would then be executed as a service. This would then drop the actual ransomware file onto the affected system, encrypting files with the .WNCRY extension. (A separate component file for displaying the ransom note would also be dropped.) Files with a total of 176 extensions, including those commonly used by Microsoft Office, databases, file archives, multimedia files, and various programming languages.
Figure 1. Infection diagram
Figure 2. Ransom note
Feedback from the Smart Protection Network indicates that aside from the United Kingdom, Taiwan, Chile and Japan were all significantly affected by this threat. India and the United States are also affected.
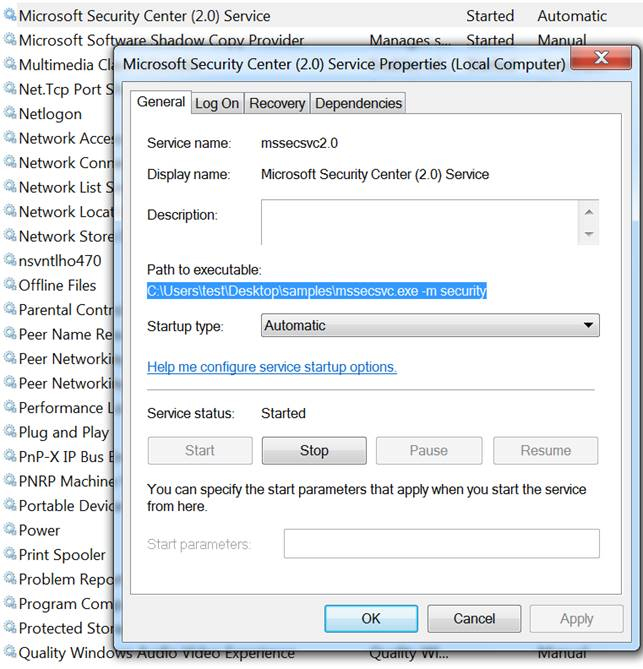
To spread to other systems, it uses the file that was dropped and run as a service. The service uses the name "Microsoft Security Center (2.0)". This service scans for other SMB shares on the network, and uses the EternalBlue vulnerability to spread to other systems.
Figure 3. Added service
As we noted earlier, the SMBv1 vulnerability used in this attack was already patched in March by Microsoft. Even before that, in September 2016 Microsoft had strongly urged users to migrate away from SMBv1, which dates back to the early 1990s. US-CERT had issued similarly strong recommendations as well. Organizations that had followed best practices—both in patching and in proper configuration of SMB services—would not be affected by this attack.
Propagation and the Kill switch
This particular threat grew very quickly, but the initial wave quickly tapered off. Why was this the case?
For one, this ransomware had a very unusual component: it contained a worm component. It would scan for and attempt to compromise using the same EternalBlue vulnerability machines on both its LAN and on the internet. This was done by the service before the ransomware is dropped and run. It scans the following IP addresses as follows:
- On the LAN, it scans for all enumerated addresses within its LAN with an open port 445 (i.e., the SMB port)
- On the internet, it scans for random IP addresses to see if it has an open port 445. If it finds one with an open port, it scans all devices in the same /24 IP range (i.e., IP addresses that share the first three octets) as the found address.

Figure 4. Propagation routine
This means that if WannaCry/Wcry entered an organization's network, it could spread within it very rapidly. Any machine or network that has exposed port 445 to the internet is at risk as well.
However, the initial infections tapered off very quickly because this ransomware also integrated a built-in kill switch. It would access a nonsense domain and if it was active, it would stop running then and there. This took place before any propagation or encryption. It's unclear why this particular kill switch was added to the software.
[RELATED: Learn how to defend against this threat, as well as what system administrators can do to minimize the associated risk.]
Trend Micro Solutions
Trend Micro OfficeScan™ with XGen endpoint security infuses high-fidelity machine learning with other detection technologies and global threat intelligence for comprehensive protection against ransomware and advanced malware. As mentioned earlier, we detect these as RANSOM_WANA.A and RANSOM_WCRY.I. Products with Predictive Machine Learning and all relevant ransomware protection features enabled are already protected against this threat.
Trend Micro Deep Security™ and Vulnerability Protection, Deep Discovery™ Inspector, TippingPoint and Trend Micro Home Network Security protects against this threat. For a complete list of associated rules and filters for Trend Micro and TippingPoint products, please refer to this Trend Micro support page. Below are the SHA256 hashes related to this ransomware:
- 043e0d0d8b8cda56851f5b853f244f677bd1fd50f869075ef7ba1110771f70c2
- 09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa
- 11d0f63c06263f50b972287b4bbd1abe0089bc993f73d75768b6b41e3d6f6d49
- 16493ecc4c4bc5746acbe96bd8af001f733114070d694db76ea7b5a0de7ad0ab
- 190d9c3e071a38cb26211bfffeb6c4bb88bd74c6bf99db9bb1f084c6a7e1df4e
- 201f42080e1c989774d05d5b127a8cd4b4781f1956b78df7c01112436c89b2c9
- 2584e1521065e45ec3c17767c065429038fc6291c091097ea8b22c8a502c41d
- 3f3a9dde96ec4107f67b0559b4e95f5f1bca1ec6cb204bfe5fea0230845e8301
- 4186675cb6706f9d51167fb0f14cd3f8fcfb0065093f62b10a15f7d9a6c8d982
- 4b76e54de0243274f97430b26624c44694fbde3289ed81a160e0754ab9f56f32
- 57c12d8573d2f3883a8a0ba14e3eec02ac1c61dee6b675b6c0d16e221c3777f4
- 78e3f87f31688355c0f398317b2d87d803bd87ee3656c5a7c80f0561ec8606df
- 940dec2039c7fca4a08d08601971836916c6ad5193be07a88506ba58e06d4b4d
- 9fb39f162c1e1eb55fbf38e670d5e329d84542d3dfcdc341a99f5d07c4b50977
- a3900daf137c81ca37a4bf10e9857526d3978be085be265393f98cb075795740
- b47e281bfbeeb0758f8c625bed5c5a0d27ee8e0065ceeadd76b0010d226206f0
- b66db13d17ae8bcaf586180e3dcd1e2e0a084b6bc987ac829bbff18c3be7f8b4
- b9c5d4339809e0ad9a00d4d3dd26fdf44a32819a54abf846bb9b560d81391c25
- c365ddaa345cfcaff3d629505572a484cff5221933d68e4a52130b8bb7badaf9
- dff26a9a44baa3ce109b8df41ae0a301d9e4a28ad7bd7721bbb7ccd137bfd696
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa
- eeb9cd6a1c4b3949b2ff3134a77d6736b35977f951b9c7c911483b5caeb1c1fb
- f8812f1deb8001f3b7672b6fc85640ecb123bc2304b563728e6235ccbe782d85
- fc626fe1e0f4d77b34851a8c60cdd11172472da3b9325bfe288ac8342f6c710a