Securing the Industrial Internet of Things: Addressing IIoT Risks in Healthcare
 The constant quest for prolonging and preserving human life has continually driven technologies to develop groundbreaking innovations in the delivery of healthcare services and state-of-the-art treatments. Like in many other enterprises, the industrial internet of things (IIoT) has rapidly transformed the network and data infrastructure in health and medicine. With the IIoT, medical data and information have become more accessible and portable, making remote monitoring of patients seamless and sharing of critical treatment trends up-to-date.
The constant quest for prolonging and preserving human life has continually driven technologies to develop groundbreaking innovations in the delivery of healthcare services and state-of-the-art treatments. Like in many other enterprises, the industrial internet of things (IIoT) has rapidly transformed the network and data infrastructure in health and medicine. With the IIoT, medical data and information have become more accessible and portable, making remote monitoring of patients seamless and sharing of critical treatment trends up-to-date.
However, rapid adoption of the IIoT is not without risks. Healthcare stakeholders must first understand the dangers it brings to the field when haphazardly implemented. In utilities, IIoT-related threats could cause cascading problems to a larger community.
In healthcare, these consequences might be more contained but no less life-threatening.
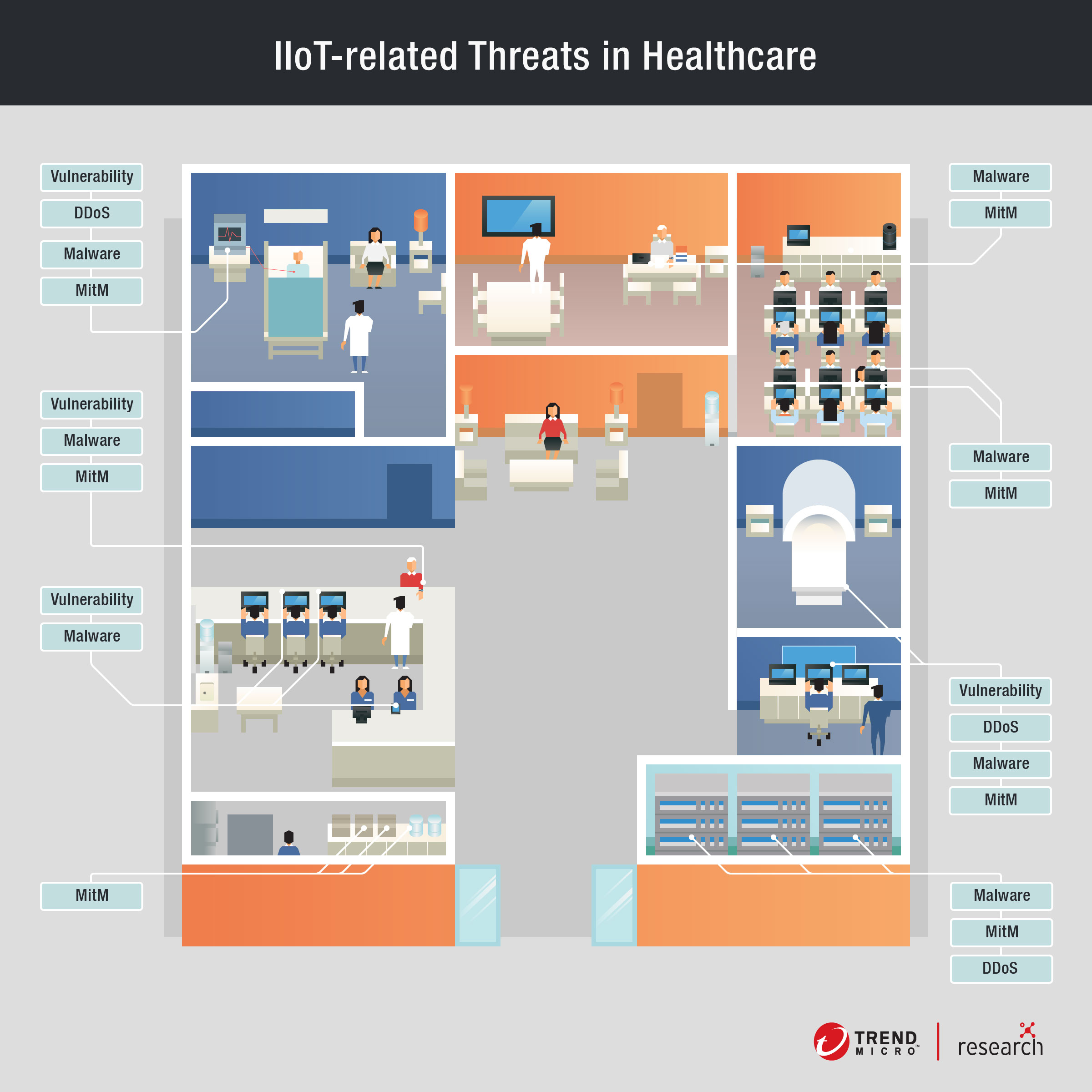
IIoT in healthcare
In the healthcare sector, the industrial internet of things has ushered in an era of expanded possibilities where, when connected to the internet, ordinary medical equipment are now able to gather and share important data, which give healthcare providers and medical practitioners added insight into symptoms and treatment trends. Furthermore, the IIoT has drastically lessened the workloads of healthcare professionals, allowing them more time and energy to better attend to patient needs.
The following systems and devices are common components of a connected hospital or healthcare facility.
Hospital Information System (HIS)
Patient care is a complicated task that involves not only the medical, but also administrative, financial – and in some cases, legal – aspects, where the information for each are integrated into a single platform, the Hospital Information System or HIS.
A patient is usually attended to by a team of healthcare professionals that includes doctors and nurses. The specialized care they provide is supported by a comprehensive base of information, which includes the patients’ medical history that should be accessible to them when needed. Easy and immediate access to these information – by the right people – ensures that a patient gets the correct treatment and care. Also, safeguarding the integrity of such information is vital.
Aside from medical and hospital-related activities (e.g., diagnostic, admission/discharge, etc.), an HIS may include legal, administrative, financial records and other such information needed in a hospital’s daily operations.
Risks. HIS presents a desirable target for any potential cybercriminal because of the critical information it holds, such as the personally identifiable information (PII) of patients, which can be used for extortion, especially when the patient’s medical condition requires confidentiality. Additionally, individuals or parties with malicious intent can go after the medical institution by using HIPAA (Health Insurance Portability and Accountability Act) breach penalties for blackmail. If compromised, it would not only jeopardize the privacy of its patients, but also their security.
In a connected hospital, an HIS is susceptible to threats that include, but not limited to, distributed denial of service (DDoS), ransomware, and phishing attacks. Several other devices connected to hospital networks could serve as the entry point for malicious actors, who could perform lateral movement to gain access to more critical information. Once an HIS is accessed, malicious actors could manipulate data, steal information, or disrupt the hospital’s daily operations.
Recommendations. Securing an HIS is largely dependent on network security. Network segmentation could help prevent or lower the impact of a compromise. This involves splitting a network into subnetworks that could reduce the risk of lateral movement. Encryption software could also be useful in mitigating the consequences of data theft and loss.
Medical devices
There are innumerable medical devices that serve highly-specialized and critical functions inside healthcare facilities – primarily used to monitor patient’s vital signs or administer medication – such as infusion pumps, anesthesia machines, dialysis machines, and respiratory ventilators. Modern versions of these devices can be wirelessly connected to a network, which would allow these devices to be controlled remotely and transfer collected information, such as the amount of medication a patient has taken to an HIS.
Risks. As with any equipment or device, previously unknown vulnerabilities are prevalent dangers that consistently threaten connected machines. Stolen patient information, as well as attacks on these medical devices could lead to inaccurate readings, which can harm patients under care. A case in point was a recent vulnerability that researchers have uncovered in a brand of anesthesia machines, which could allow an attacker to remotely modify equipment parameters, i.e., change the composition of aspirated gases, placing patients at risk. Connected devices can also fall victim to DDoS, malware, and other network attacks.
Then, there is also the possibility, albeit remote, of hacktivists using stolen medical histories of certain individuals to target a specific ethnic or political group to draw attention to their cause.
Recommendations. Manufacturers, distributors, and healthcare facilities all share the responsibility of ensuring that these medical devices remain safe for use. Stakeholders should be wary of vulnerabilities and exploit disclosures, so that they could be agile in mitigating possible threats. They can also refer to government agencies, such as the US Food and Drug Administration (FDA) and Department of Homeland Security (DHS) for guidance in addressing discovered threats. The FDA for example, continues to develop a medical device safety action plan, to help mitigate the risks brought about by oversights in device safety and bring stakeholders together in addressing these oversights and performing recalls should vulnerabilities be discovered. Healthcare facilities can also use virtual patching that would help greatly in managing vulnerabilities.
Wearables and home medical equipment
Wearables provide basic, real-time information like heart rate, steps taken, and sleep duration, which are information users can refer to for making healthier decisions. Patients who have been released from the hospital can also be monitored through IoT remote devices. Glucose monitors, for example, periodically take blood samples to alert diabetic patients when they need to take insulin shots, while heart monitors could also signal the onset of a heart attack or stroke.
Risks. Evolving vulnerabilities are a constant risk for these portable devices. FDA for example had issued a warning against a certain brand of insulin pumps (device that mimics the function of the pancreas by issuing insulin and keeping blood sugar levels in a safe range), which could allow an attacker to send radio frequency (RF) and change the nearby pumps’ setting. Compromised insulin pumps could not be updated and patients were urged to replace them. Since these devices work remotely, attacks could lead to life-threatening situations, wherein patients might find themselves far from medical institutions to receive quick emergency response. These devices would also be susceptible to threats from a poorly configured home network, depending on the security stance of users.
Recommendations. Medical devices that patients can bring home or wear illustrate how users and patients also share the responsibility of securing these connected devices. Patients who bring such devices home should be careful in sharing information about their devices, like serial numbers. These devices should also be physically secured and be kept close to the user as much as possible.
Healthcare systems software
Medical institutions need software to help control several systems they use to run and transfer information within their facility. The interface of such systems can contain the controls for critical functions or critical information like patients’ PII.
Risks. Mere exposure of the interface of such systems is an alarming risk. These exposed systems can be found using the industrial search engine Shodan. A Trend Micro research that looked into the topic of connected hospitals revealed that among the exposed systems were software for pharmacy management, patient scheduling, and record maintenance. The research showed a small number of exposed medical systems, although the small number contained medical records, history, and financial information. Potential attackers can also infect the exposed device with ransomware or issue incorrect commands. An attacker could also have their sights on other devices on the network, using the compromised software simply as an entry point.
Recommendations. Medical institutions should ensure that their devices, equipment, and software systems are not inadvertently exposed online. This can be prevented through the careful configuration of these devices and systems, especially those that contain PII of both patients and hospital staff.
Legacy systems
Many medical institutions still use legacy systems despite the integration of more and more IoT devices in their facilities. This is because replacing legacy systems would translate to extensive downtime, which healthcare facilities could ill-afford. However, this comes with certain risks and consequence that these institutions must account for.
Risks. Legacy systems could be ill-equipped to provide the cyber defenses IoT devices need to operate securely. In addition, there is a possibility that manufacturers have stopped developing patches and updates, moving on to newer iterations of a similar system instead. This leaves the legacy system vulnerable to new threats and have inadequate security measures that could make it as the perfect entry point to compromise other devices and steal more information.
Recommendations. If medical institutions do not foresee the possibility of replacing their legacy systems in the near future, they should opt instead to strengthen their defenses through an applicable security architecture. Using solutions like virtual patching could mitigate some of the vulnerabilities unpatched legacy systems face.
Other IoT applications
Aside from the considerations and IoT applications mentioned above, other applications seen in connected medical facilities simply provide added convenience to their staff. RFID technology, a component of the IoT, can for example, be used to help hospital staff quickly locate and identify equipment they would need to treat a patient. Although such applications do not have an obvious medical value, they do ease the burden of the staff and allow them to concentrate on treating their patients.
Risks. IoT applications that are seemingly innocuous in nature could be overlooked and under-protected against malicious actors fishing for a chance to get into their defenses. Although the consequences of a compromise are less impactful than that in a critical medical device, a compromise could still allow an even bigger attack with far less recoverable consequences.
[Read: Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations]
Recommendations. Integrators should map and manage their connected devices, including those that have simpler functions, as they could be used as entry points for bigger targets. System integrators should also consider devices with virtual fencing features that will disable the devices once they are out of range.
Conclusion
IoT in healthcare has not reached full maturity yet and is still brimming with possibilities. Developing technologies like 5G will push the boundaries of what IoT can do, and consequently what IoT can do for healthcare. Only recently, the first remote surgery in 5G was done in China where a doctor operated on a patient 30 miles away. It is easy to be swept by similar developments, but it is imperative to develop security parallel to these changes.
Stakeholders—manufacturers, distributors, healthcare facilities and professionals, and users—share the responsibility of protecting the value IoT brings to healthcare by taking measures to secure it. Manufacturers should abide by the guidelines of institutions like FDA to produce standardized and quality healthcare devices. Security must also exist from the design phase, and not merely as an afterthought. Healthcare facilities meanwhile should plan a security architecture that best fits their needs, and the devices they plan to connect to their network. They can also apply a multilayered protection system that would provide better visibility and protection against known and unknown vulnerabilities. Finally, users or patients also need to take responsibility over their respective devices, and be wary of signs of a possible attack or compromise of these devices.
All these measures are necessary because a single threat can negate the advantages of IoT and introduce new risks to an already delicate industry like healthcare. Like health, security should not be neglected only until it is too late.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One