A Shift in the ATM Malware Landscape: From Physical to Network-based Attacks
 View Cashing in on ATM Malware: A Comprehensive Look at Various Attack Types
View Cashing in on ATM Malware: A Comprehensive Look at Various Attack Types
There is no way around it: Compromising automated teller machines (ATMs) could be seen by criminals as hitting the mother lode. Oftentimes there would be reports of unauthorized cash-outs, and upon investigation, skimmers and other attacks by physical means would be the usual suspects.
Over the years, ATM thefts have been undertaken in a variety of ways: from blowing up safes to gluing on skimmers and attaching fake keypads to installing malware executables. In particular, the use of malware in attacking ATMs has seen considerable adoption among cybercriminals, and one of the primary factors contributing to its sustained use is the fact that many of the targeted machines still use outdated operating systems. Such systems no longer receive critical security updates, so in the most basic sense, system vulnerabilities are not addressed, let alone resolved.
Among cybercriminals who use malware to attack and steal cash from ATMs, gaining physical access has become perhaps the most common approach. However, these criminals have found an even more nefarious infection vector, where no removable drives are inserted and no incriminating footages or fingerprints are found. There is no indication that the ATMs have been physically tampered with, but still, the machines are found to have been emptied of cash. The machines do not even have to be stationed on shady streets, remote locations, or other unsecured spots to be thus compromised.
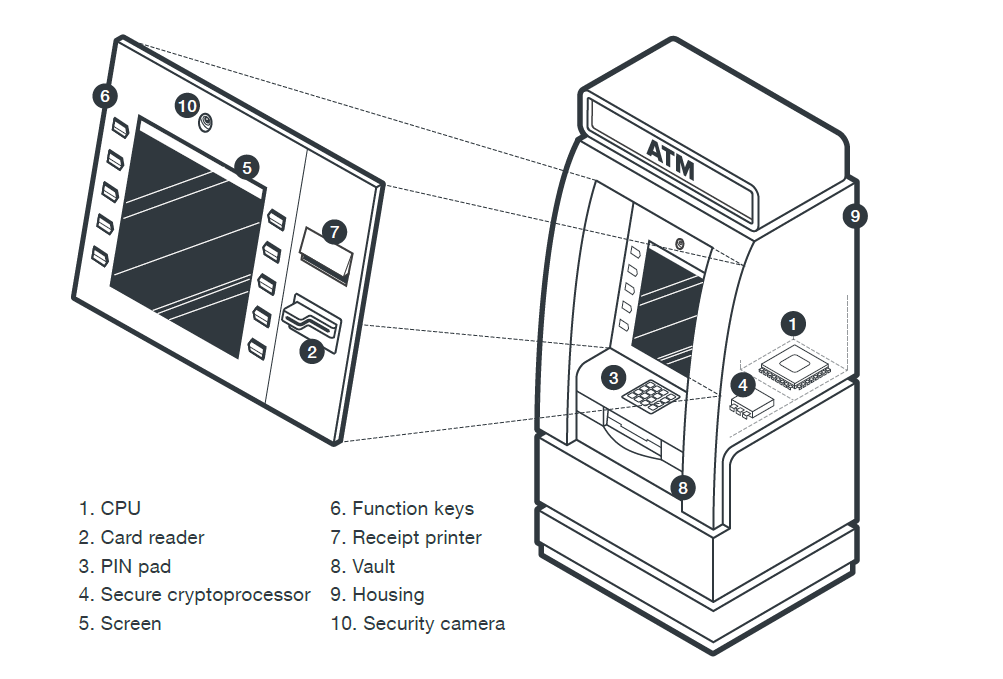
Figure 1. Components of an ATM
Cybercriminals, in their ceaseless attempt to rake in profits, have found another way to target ATMs: via the bank’s network. It is worth noting that the first entry into the network is usually by social engineering, making bank employees the weakest link in this infection chain. Network-based ATM heists are far more elaborate than physical attacks, but they have proved to be a more profitable money-making scheme.
Trend Micro and Europol’s European Cybercrime Center (EC3) have collaborated to examine how ATM malware, as a formidable threat, has evolved over the years and continued to gain stealthier features that target a multitude of ATMs.
[READ: The contributing factors to the rise of ATM malware attacks]
ATM Malware: Targeting Safes Since 2009
We have known
Since then, different types of ATM malware have entered the scene with their respective capabilities, including dispensing cash or “jackpotting” in its most stripped-down design and often exhibiting the cybercriminals’ penetrating technical know-how on ATMs. In 2016, Trend Micro worked with Europol’s EC3 and uncovered a new malware family called Alice. The malware, launched via an executable file, is capable of emptying safes for attackers to net heaps of cash.
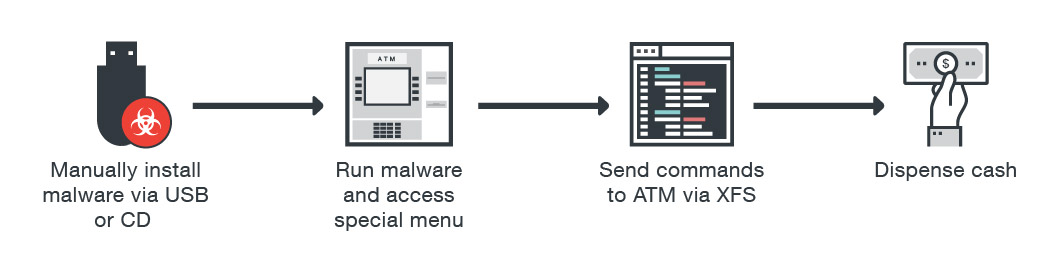
The installation of ATM malware, as represented below, often requires physical access to the targeted machine. Once the malware is installed, the cyber crooks send commands to the machine through the eXtensions for Financial Services (XFS) middleware in order to dispense cash.
Figure 2. How a typical ATM malware physical attack is carried out
The New Path to ATM Malware Infection: Attacking Through the Network
Now, banking institutions should be vigilant not only of malware infection due to poor physical ATM security, but also about the very real possibility of attackers infiltrating their networks.
Recently, a seeming spate of remotely orchestrated attacks had swept a number of ATMs in different countries. In these attacks, cybercriminals compromised the internal networks of banks in order to infiltrate the ATM infrastructure. Interestingly enough, though, a sophisticated technique like this has not been reported yet in bigger regions such as the United States and Canada.
A notorious example is the malware Ripper that hit ATMs nationwide in Thailand and reportedly stole around 12 million baht. The attack was coordinated in such a way that the criminals first hacked into the bank’s network and then proceeded to distribute the malware to the ATMs. What is particularly noteworthy here is that Ripper was the first of its kind to infect ATMs without the perpetrators’ having to physically open the machines.
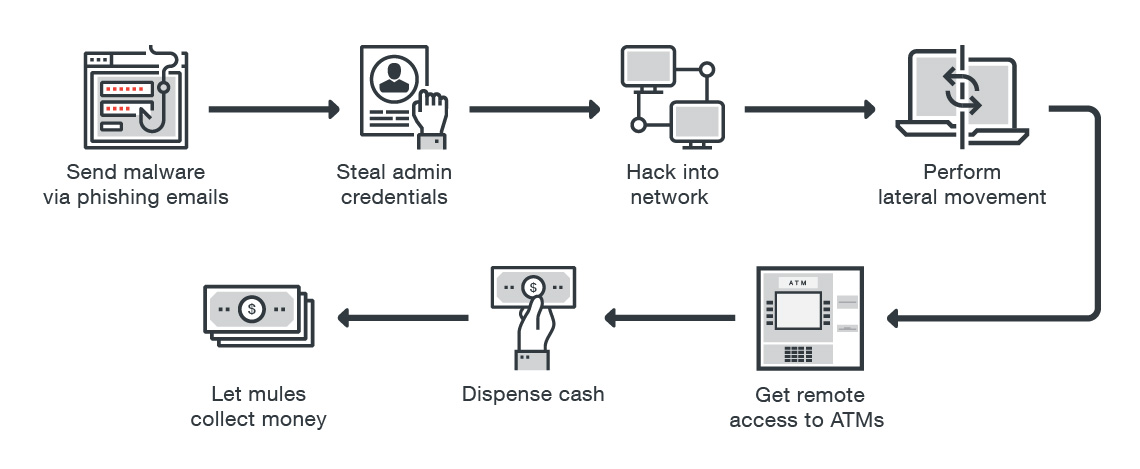
Figure 3. How a typical ATM malware network-based attack is carried out
While network-based attacks require more work than do physical attacks, their appeal lies in allowing cybercriminals to extract cash on command without having to seek out the targeted ATMs. They involve phishing emails, containing malicious executables, to bank employees. Once the malware gets executed, banks’ internal networks are penetrated. Criminals use this network access to move laterally within the banks’ network and control ATMs — even simultaneously infecting multiple machines in a single attack. Some malware families even have self-deleting capabilities, effectively dissolving most traces of the criminal activity.
To dive deeper into the latest malware developments, the perpetrators of the attacks, and how the digital ATM threat is being leveraged by criminals, see our comprehensive joint report with Europol’s EC3, Cashing in on ATM Malware: A Comprehensive Look at Various Attack Types.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One