Red Flags: How to Spot a Business Email Compromise Scam
Simplicity and high returns—these sum up why Business Email Compromise schemes are attractive to cybercriminals. True enough, this attack vector has been greatly exploited, as evidenced by the amount of money that victims lost to it in 2016. According to a report by the FBI released in May 2016, victims lost $3 billion to BEC scams. In 2017, we predict that BEC will remain a prominent threat and will be used in more targeted scams.
One of the types of BEC scams is CEO fraud, wherein the perpetrators spoof or hack into the e-mail of an organization's executive in order to initiate a fund transfer to their own accounts. While, it’s not technically sophisticated, organizations should step up their defenses against this type of scheme, and one of the ways is being able to identify the signs that an e-mail message is being used in CEO fraud. Here’s what you should watch out for to keep the threat at bay:
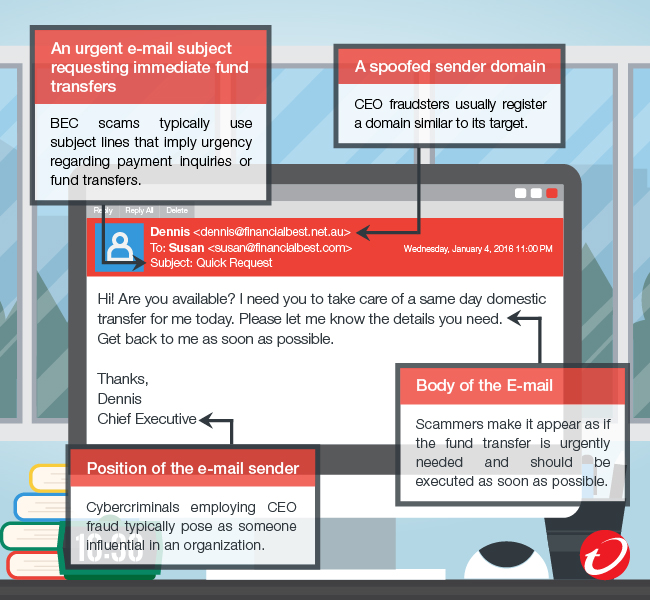
A spoofed sender domain
CEO fraudsters usually register a domain similar to its target. If the target e-mail is name@company.com, a scammer may use a variation such as name@company.au.net or slightly change the spelling into name@cmpny.com.
An urgent e-mail subject requesting immediate fund transfers
Based on our detections, BEC scams typically use subject lines that imply urgency regarding payment inquiries or fund transfers such as:
- Payment - Important
- Payment Notice
- Process Payment
- Quick Request
- Fund Payment Reminder
- Wire Transfer Request
- Bank Transfer Enquiry
Position of the e-mail sender
Cybercriminals employing CEO fraud typically pose as someone influential in an organization. Based on our data, e-mails used in BEC usually appear as if they came from the Founder and President, COO, CEO, and Chief Executive.
Body of the E-mail
In CEO fraud, scammers make it appear as if the fund transfer is urgently needed and should be executed as soon as possible. In addition, pay attention to e-mails asking for fund or wire transfers to an account that's different from ones normally used for that specific transaction.
A message may appear out of place or it may be timely as BEC scammers use social engineering tactics in order to create believable messages, hoping to persuade victims to just act on the supposed request without verifying it. That’s why it’s always important to err on the side of caution, especially when corresponding over e-mail regarding matters involving funds, payments, transfers, and other crucial information.
BEC Safety Tips
While these red flags seem obvious, in most cases, they are harder to identify. BEC perpetrators design emails to be as realistic as possible. For instance, email domains may be spoofed to mimic the ones used by the target organization or those used by legitimate companies. Scammers also use social engineering and other information gathering methods to be more familiar with the ins and outs of an organization.
Aside from being on the lookout for these signs, here are tips on how you can further protect your organization from BEC:
- Always verify. It always pays to confirm details with the parties involved, especially when it comes to messages that involve fund transfers. It’s also important to note that some BEC schemes are employed using a hacked account, which further stresses the need for protocols that include verification other than email. Non-email methods may include communicating via phone, text messaging, and chat programs or applications.
- Instead of clicking on Reply, use the Forward feature and type in or select from your contacts list the e-mail address of the person you’re replying to. This is to ensure that you are not replying to a spoofed address.
- Have mail security solutions in place. The tricky part with e-mails used in BEC scams is they don’t necessarily carry a malicious payload. With that being said, it’s advisable to go for solutions that not only detect dangerous attachments but also have social engineering correlations and a context-aware approach to email detections.
The naked eye can only do so much in trying to spot a BEC e-mail, and having email security solutions can help greatly in thwarting BEC schemes.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One