Delving into the World of Business Email Compromise (BEC)
Business Email Compromise (BEC) attacks have expanded tremendously over the past few years, with a projected growth of over $9 billion in 2018. The combination of simplicity and effectiveness have ensured that BEC will continue to be one of the most popular attacks, especially for those who lack special tools and knowledge to pull off more complicated schemes.
We looked at BEC-related incidents over a period of nine months (from January to September 2017) to see emerging and present trends from BEC incidents, examine the tools and techniques cybercriminals use, and analyze the data to give us an overall picture of what BEC looks like today.
The Internet Crime Complaint Center (IC3) separates BEC attacks into five main categories, but during our tracking efforts, we managed to narrow these even further to two main techniques:
- Credential-grabbing – Involves the use of keyloggers and phishing kits to steal credentials and access the webmail of target organizations.
- Email-only – Involves an email sent to someone in the finance department (usually the CFO) of the target company. The attackers design the email to make it look as if a company executive sent it, typically instructing the target to transfer money. The transfer request is usually for payment to a supplier or contractor, or as a personal favor.
Credential grabbing-techniques can further be categorized into those that use malware and those that use phishing.
By examining malicious attachment samples that had filenames that could be clearly categorized, we were able to determine the most prominent ones: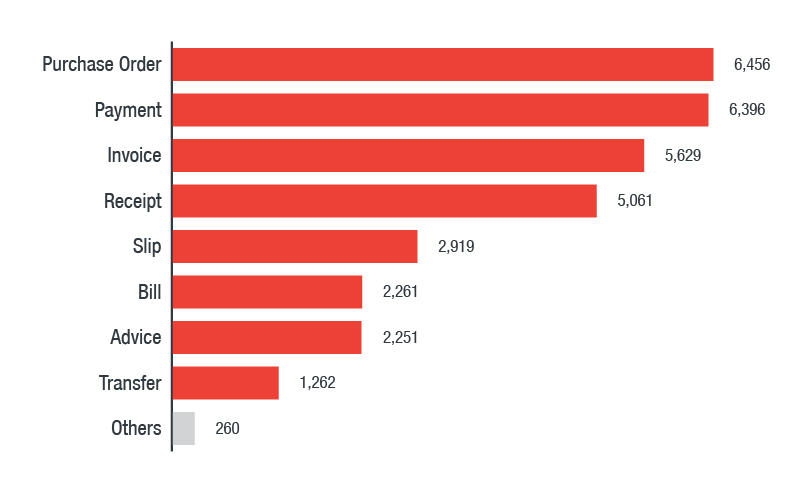
Most popular filename categories used in malicious attachments
(based on VirusTotal samples)
We also examined the malicious attachments for phishing-related BEC attacks, of which the following were the most common filename categories:
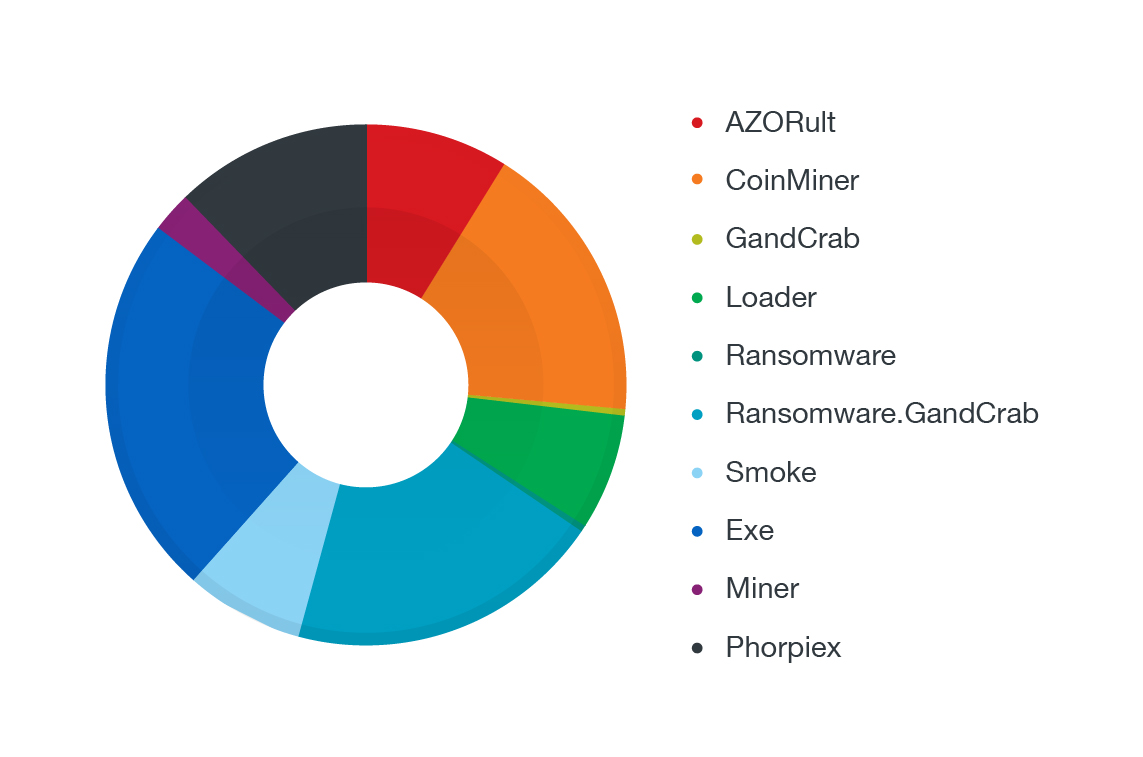
Most popular filename categories used in the attachments of phishing-related BEC attacks
(based on Trend Micro Smart Protection Network™ feedback)
BEC actors will also create legitimate-looking email addresses designed to impersonate company executives, either by using dodgy free webmail providers or by registering a copycat domain that resembles or references the target company.
The distribution of email-only BEC attacks according to the techniques used can be seen in the chart below: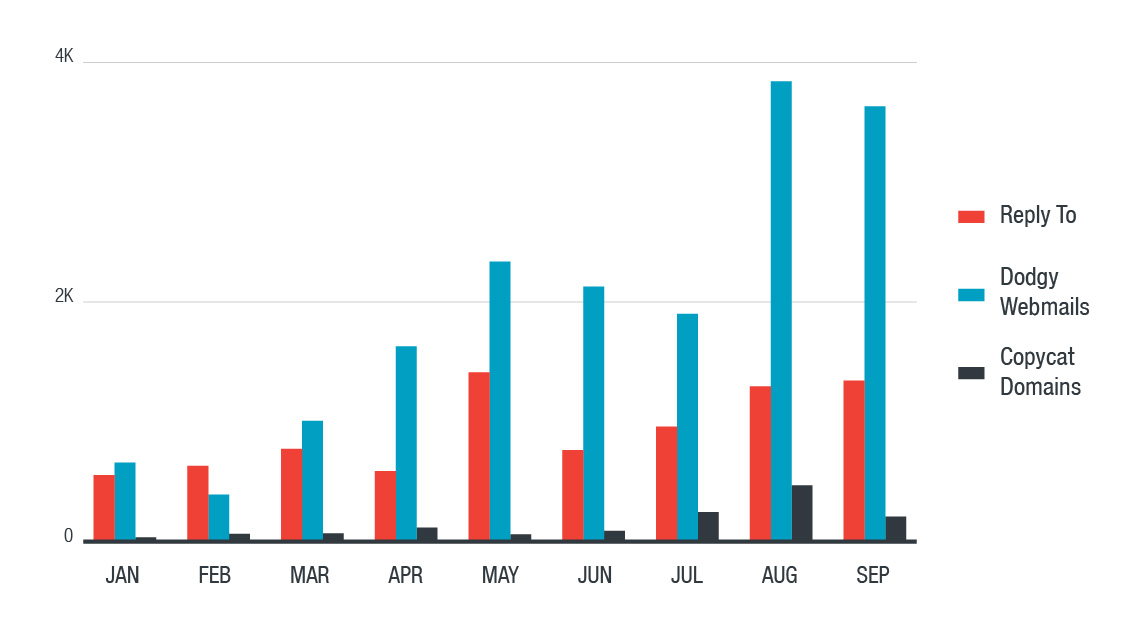
Distribution of methods used for email-only attacks based on the techniques used
In addition, we also looked at how BEC actors acquire their tools, particularly the phishing websites they used in their attacks. One of the most common methods used by BEC actors involve the use of phishing kits—scampages—as the main source of attacks. Examining these websites allowed us to identify a BEC actor and learn how this individual sourced and utilized his tools.
We found traces of this individual in multiple phishing sites, providing us with clues on how many BEC actors use multiple sites to perform their attacks. They will also typically interact with and have access to underground markets that can provide them the tools they need to pull off effective BEC attacks. Resources are even available to inexperienced BEC actors, as spamming tutorials exist that can help them start their operation. This means that for BEC actors, tools and techniques are easily accessible without having to jump through hoops. This research effort aims to paint a clearer picture of the emerging trends in BEC, the tools and techniques they use, and how individuals and organizations can protect themselves from these types of attacks.
Read the full report: Tracking Trends in Business Email Compromise (BEC) Schemes
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Deepfake It ‘til You Make It: A Comprehensive View of the New AI Criminal Toolset
- Proactive Security: The Role of Exposure Management and Detection-Response Capability
- The Trend Micro Underground Series
- The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity
- Stay Ahead of AI Threats: Secure LLM Applications with Trend Vision One
 Unveiling AI Agent Vulnerabilities Part III: Data Exfiltration
Unveiling AI Agent Vulnerabilities Part III: Data Exfiltration AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity
The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity