Data Breaches 101: How They Happen, What Gets Stolen, and Where It All Goes

Though people have reached a seeming point of desensitization to news citing a data breach, protecting user data has become increasingly important amid stricter regulation implementation. Companies are no longer just required to announce that their systems have been breached but also pay fines that can reach up to 4 percent of their annual turnover should they deal with the data belonging to European Union (EU) citizens in accordance with the General Data Protection Regulation (GDPR) requirements.
Just this year, big names such as Macy’s, Bloomingdale’s, and Reddit have joined the ever-growing list of breach victims. Compromised data is a subject that needs the public’s full attention. Data breaches can result in the loss of millions, even billions, of private records and sensitive data, affecting not just the breached organization, but also everyone whose personal information may have been stolen.
What is a data breach?
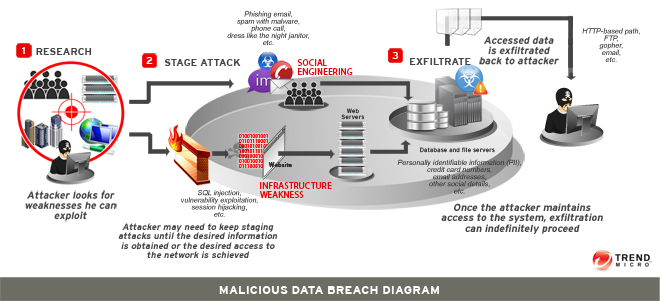
A data breach occurs when a cybercriminal successfully infiltrates a data source and extracts sensitive information. This can be done physically by accessing a computer or network to steal local files or by bypassing network security remotely. The latter is often the method used to target companies. The following are the steps usually involved in a typical a breach operation:
- Research: The cybercriminal looks for weaknesses in the company’s security (people, systems, or network).
- Attack: The cybercriminal makes initial contact using either a network or social attack.
- Network/Social attack: A network attack occurs when a cybercriminal uses infrastructure, system, and application weaknesses to infiltrate an organization’s network. Social attacks involve tricking or baiting employees into giving access to the company’s network. An employee can be duped into giving his/her login credentials or may be fooled into opening a malicious attachment.
- Exfiltration: Once the cybercriminal gets into one computer, he/she can then attack the network and tunnel his/her way to confidential company data. Once the hacker extracts the data, the attack is considered successful.
What are the biggest breaches to date?
The following table shows the 10 biggest breach incidents reported to date:
| Company/Organization | Number of Records Stolen | Date of Breach |
|---|---|---|
| Yahoo | 3 billion | August 2013 |
| Equifax | 145.5 million | July 2017 |
| eBay | 145 million | May 2014 |
| Heartland Payment Systems | 134 million | March 2008 |
| Target | 110 million | December 2013 |
| TJX Companies | 94 million | December 2006 |
| JP Morgan & Chase | 83 million (76 million households and 7 million small businesses) | July 2014 |
| Uber | 57 million | November 2017 |
| U.S. Office of Personnel Management (OPM) | 22 million | Between 2012 and 2014 |
| Timehop | 21 million | July 2018 |
What types of data are usually stolen?
The motive of a cybercriminal defines what company he/she will attack. Different sources yield different information. The following are examples of common targets with details on what kind of data was stolen:
Business
- Timehop (July 2018)
Mobile App Vendor
The data of the start-up’s 21 million users was exposed for around 2 hours due to a network intrusion on 4 July. - Reddit (June 2018)
Content Aggregator
Hackers gained access to an old database of users (the exact number of those affected has not been revealed) on 19 June. - Dixons Carphone (June 2018)
Retailer
An estimated 10 million customers could be affected by the hacking attack on its network sometime last year. The compromised data may include personal information like names, addresses, and email addresses. Some 5.9 million payment card records (nearly all of which are protected by the chip-and-PIN system though) may have been accessed as well. - Equifax (July 2017)
Information Solutions Provider
The major cybersecurity incident affected 143 million consumers in the U.S. Initially discovered on 29 July, the breach revealed the names, Social Security numbers, birth dates, and addresses of almost half of the total U.S. population. With investments in 23 other countries worldwide, around 400,000 U.K. customers were also reportedly affected. Final findings revealed a total of 145.5 million exposed records. - Ashley Madison (July 2015)
Social Media Website
Hacktivists stole and dumped 10GB worth of data on the Deep Web. This included the account details and personally identifiable information (PII) of some 32 million users, as well as credit card transactions. - Target (January 2014)
Retailer
Hackers penetrated the vendor’s network and infected all of its point-of-sale (PoS) machines. They were able to expose nearly 40 million debit and credit cards to fraud. The information stolen included PINs, names, and banking information.
Medical/Healthcare
- SingHealth (July 2018)
Medical/Healthcare Service Provider
The nonmedical personal data of 1.5 million patients was reportedly accessed and copied, including their national identification number, address, and date of birth as part of the attack. The stolen data also included the outpatient medical data of 160,000 patients. - Hong Kong Department of Health (July 2018)
Federal Agency
The government agency was hit by a ransomware attack that rendered its systems inaccessible for two weeks starting 15 July. - Anthem (May 2015)
Medical/Healthcare Service Provider
An attack that started in April 2014 resulted in the theft of more than 80 million records of current and former customers. The data stolen included names, birthdays, social IDs, email addresses, and employment information
Government/Military
- U.K. military contractor (May 2017)
Military Contractor
Sensitive data from a military contractor was extracted by a targeted attack group from the military contractor’s network using a backdoor identified as RoyalDNS. - U.S. OPM (April 2015)
Federal Agency
Hackers gained access to more than 18 million federal employee records, including Social Security numbers, job assignments, and training details.
Banking/Credit/Financial
- Deloitte (October/November 2016)
Accountancy Firm
The firm was targeted by a sophisticated hack that compromised the confidential emails and plans of some of its blue-chip clients. The attack was discovered in March 2017 though findings revealed though the hack may have been launched as early as October or November 2016. - JP Morgan Chase & Co. (October 2014)
Credit Service Provider
The data of an estimated 76 million households and 7 million small businesses was compromised. The information included names, addresses, phone numbers, email addresses, and others.
Educational
- University of Maryland (March 2014)
Educational Institution
More than 300,000 student, faculty, and staff records going as far back as 1998 were compromised though no financial, medical, or academic information was included. The stolen data included names, birth dates, university ID numbers, and Social Security numbers. - University of Greenwich (2004)
Educational Institution
The university was fined ₤120,000 for exposing the personal data of students, including names, addresses, dates of birth, signatures, and in some cases even medical information, on a microsite that was left unsecured since 2004.
Based on the data stolen, here are specific types of information that are of value to cybercriminals. Hackers search for these data because they can be used to make money by duplicating credit cards, and using personal information for fraud, identity theft, and even blackmail. They can also be sold in bulk in Deep Web marketplaces.
[Read: Where do all the stolen information go?]
- Member name
- Date of birth
- Social Security number
- Member identification number
- Email address
- Mailing and/or physical address
- Telephone number
- Banking account number
- Clinical information
- Claims information
End users are almost never the target of cybercriminals who are out to steal sensitive information in bulk, unless an individual is connected to an industry (see Spear Phishing). However, end users can be affected when their records were part of the information stolen from big companies. In such cases, it is best to take note of the following practices.
- Notify your bank. Verify your account details and change PIN codes.
- Double-check email addresses from incoming emails. Cybercriminals can pose as bank representatives and ask for credentials.
- Do not click suspicious-looking links or download files from unknown sources.
- If credentials or financials have been tampered with, contact the breached company and ask if they can assist in enrolling you to a fraud victim assistance program.
[More: Data breach news, incidents, and resources]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Proactive Security: The Role of Exposure Management and Detection-Response Capability
- The Trend Micro Underground Series
- The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity
- Stay Ahead of AI Threats: Secure LLM Applications with Trend Vision One
- Slopsquatting: When AI Agents Hallucinate Malicious Packages
 Unveiling AI Agent Vulnerabilities Part III: Data Exfiltration
Unveiling AI Agent Vulnerabilities Part III: Data Exfiltration AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity
The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity