QuickTime Player Allows Movie Files to Trigger Malware Download
Publish Date: 2010年8月1日
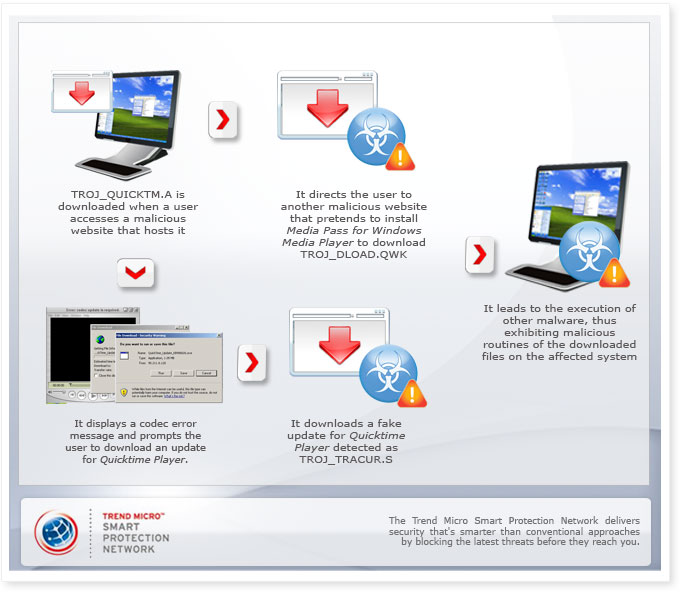
How does this threat get into users' systems?
This threat is distributed through malicious websites, most commonly on torrent sites that serves pirated/cracked movies and application softwares. It may be downloaded into a system by unknowing users who access the said websites. It can also be found in most peer to peer application such as limewire.
What happens once the threat gets inside computers?
This is the Trend Micro detection for movie (.MOV) files that have been created to download other malware files on an affected system. Once the malicious movie file is run, it performs any of the following activities:
1. It directs the user to another malicious website that pretends to install Media Pass for Windows Media Player, which is allegedly required to watch the movie file. This deceives the user into downloading and executing another malicious file, detected as TROJ_DLOAD.QWK.
2. It displays a codec error message and prompts the user to download an update for Quicktime Player. The update is actually a malicious file detected as TROJ_TRACUR.SMDI.
How are users affected by this threat?
This threat is distributed through malicious websites, most commonly on torrent sites that serves pirated/cracked movies and application softwares. It may be downloaded into a system by unknowing users who access the said websites. It can also be found in most peer to peer application such as limewire.
What happens once the threat gets inside computers?
This is the Trend Micro detection for movie (.MOV) files that have been created to download other malware files on an affected system. Once the malicious movie file is run, it performs any of the following activities:
1. It directs the user to another malicious website that pretends to install Media Pass for Windows Media Player, which is allegedly required to watch the movie file. This deceives the user into downloading and executing another malicious file, detected as TROJ_DLOAD.QWK.
2. It displays a codec error message and prompts the user to download an update for Quicktime Player. The update is actually a malicious file detected as TROJ_TRACUR.SMDI.
This Trojan leads to the download and execution of other malware, thus exhibiting malicious routines of the downloaded files on the affected system. Malicious files may vary from simple downloaders to more dangerous information-stealing malware, depending on what the malware author chooses to host on the malicious websites.
What is noteworthy about this attack?
This attack makes use of specially-crafted movie files (.MOV files in particular), which contain codes that enable the download of other malicious files on the system using QuickTime Player version 7.6.6 and lower. In this attack, the malware author takes advantage of a feature in the QuickTime specification known as wired actions, which allows QuickTime files to take certain actions – in this case, go to a URL where the malicious content is located.
Are Trend Micro users protected from this threat?
Yes. Solutions supported by the Trend Micro™ Smart Protection Network™ block the access to the malicious URLs used by this threat to download other malicious files via Web Reputation Services. It can detect and prevent the execution of the malicious files TROJ_QUICKTM.A, TROJ_DLOAD.QWK, and TROJ_TRACUR.SMDI via File Reputation Technology.
What can users do to prevent this threat from entering computers?
Users may avoid this threat by being wary of downloading movie files on the Internet, especially if the movie is just newly released in the theaters. Most of these files are illegally distributed and should not be available or downloaded in the first place. Users should download movie files from reputable and legitimate online media sites, which may require a certain fee before downloading the movie.