Anatomy of a Data Breach
A data breach refers to the exfiltration—the release of data from a system without the knowledge or consent of its owner. This data resides in the targeted organization’s systems or networks and is proprietary or sensitive in nature. Propriety data may be confidential in nature for or valuable to a company. Acquisition by external parties may cause harm. This data can comprise personally identifiable information (PII), customer data, trade secrets, and the like.
Data breaches can be instigated by malicious attackers or can accidentally occur.
How does a data breach take place?
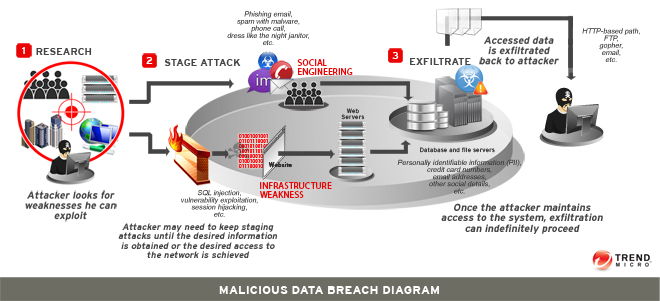
Before an attack can take place, the attacker must first identify a target. Once the cybercriminal has selected a target with the motive of either causing annoyance, harm, or damage or of extracting profit from the breach, he proceeds as follows:
- Research: The cybercriminal looks for a weakness in the target's people, systems, or networks. This may include conducting research on the company’s employees and infrastructure.
- Attack: The cybercriminal makes initial contact with the target through either a network or through a social attack.
- In a network attack, the attacker uses infrastructure, system, and application weaknesses as well as techniques like SQL injection, vulnerability exploitation, session hijacking, and the like in order to penetrate the targeted organization's network.�A social attack, on the other hand, uses tactics that have an element of social engineering. Typical social attacks begin with a phishing email message, a spam that carries malware, or even obtaining physical access to the company's premises by dressing up as office housekeeping staff, among others.
- Exfiltration: The cybercriminal extracts and transmits data back to him. This data can be proprietary or sensitive in nature or can comprise credentials that he may need for another attack or to get higher privileges inside his target’s network.
The cybercriminal may have to stage more than one attack to get enough information and to gain a foothold in targeted systems in order to keep transmitting data.
What do data breaches tell us about the current state of the threat landscape?
According to reports published by Dataloss.db, three of the 20 largest data breaches of all time occurred in 2011. Considering that we’re only a little over halfway through the year, it’s easy to say that this data breach issue is escalating. In line with this, Trend Micro researchers stated their observations on what the escalation suggests and what organizations as well as individuals can do to mitigate and prevent such breaches:
A broader attack surface increases the number of opportunities for cybercriminals to launch attacks. The adoption of new and varied software platforms, devices and technologies and network segments, the interaction of all these with each other in the conduct of business inevitably broadens the attack surface available for cybercriminals. Remember that cybercriminals only need to find a single weakness that they can exploit, and having many points of vulnerability to choose from makes it easier for them to conduct a successful attack.
Furthermore, consumerization—the trend wherein new IT devices and tools first emerge in the consumer space then make their way into the enterprise space—is forcing enterprises to embrace, adapt, or follow suit, thus contributing to the inherent difficulty of keeping total control over data access.
The mobile workforce culture also presents additional challenges to enterprises that want to protect their data.
The human element is key. All it takes is a single employee, innocently but unknowingly acting against the company’s best interests to defeat its security perimeter.
We must keep in mind that social engineering—the manipulation of human weaknesses such as trust or curiosity—is an ever-present bane to any sufficiently secure infrastructure.
Protection via perimeter defense no longer works; data access control and data access intelligence is key.
A paradigm shift in security mindset is necessary. Merely understanding and defending the many layers of your network from outsiders, granted this is already being properly done, is not enough. Any network-connected data should be able to defend itself from attacks. This holistic approach, in addition to strong employee education, should strengthen your company's overall security.
What are other possible causes of data breaches?
The possible causes of internally triggered data breaches—intentional or otherwise—include the following:
- Disgruntled employees: Employees that mean to do harm to their employers by willingly taking information from the company for malicious purposes.
- Lost or stolen devices: Company laptops and other devices that contain data may be lost or stolen.
- Malware-infected personal or network devices: Company laptops, other devices, or removable drives may be infected by information-stealing malware.
- Unintentional sharing: Employees may unwittingly reveal information in conversations or leave personal details in publicly accessible locations. These locations may be actual places or online pages such as those found on social networks.
What are real-world data breach examples?
Recent examples of data breaches include those that affected RSA and Sony Pictures. Both incidents are good examples of the types of data breach attack.
RSA
The attackers behind the RSA breach used a social attack to get the information they wanted, as explained in the report "Anatomy of an Attack" by Uri Rivner. They sent two different phishing email messages with the subject, "2011 Recruitment Plan," to two small groups of RSA employees over a two-day period.
One of the said employees retrieved the message from his Junk Mail folder and opened the attachment with the same file name as the subject, unaware that the message contained a zero-day exploit for CVE-2011-0609. The exploit installed a backdoor we detect as TROJ_ADOBFP.SM, which allowed the attacker to gain deeper access to the network until he gets hold of the information he is looking for.
The steps RSA had to undergo to undo the damage the breach cost reportedly amounted to US$66 million. According to RSA executive vice-president David Goluden, these steps included hardening their systems as well as working with their customers to implement remediation programs.
Sony Pictures
Sony Pictures, on the other hand, was attacked by a group that calls itself LulzSec, which used a network attack to steal and to expose confidential information. According to the group, despite the supposed improvements Sony Pictures made to its systems, they were able to gain access to SonyPictures.com using a "very simple SQL injection." A documentation of the said attack was published by ComputerWorld in the article, "Sony Pictures Falls Victim to Major Data Breach."
LulzSec added that "Sony stored over 1,000,000 customer passwords in plaintext, which means it’s just a matter of taking it." The stolen data included personal information such as passwords, email addresses, home addresses, dates of birth, and all Sony opt-in data associated with accounts. The group also claimed to have gotten hold of Sony Pictures’s administrative network information, including passwords, music codes, and music coupons.
LulzSec, however, was unable to copy all the available information on Sony Pictures's servers. Instead, they only took samples that they then posted on file-sharing websites.
The said attack was just one of the many hacking attacks targeting Sony. According to reports, Sony spent US$171 million, which is still likely to increase, in order to fix the damage the breaches cost.
What should enterprises do to stay protected from data breaches? Based on the attack techniques cybercriminals typically use to stage data breaches, enterprises can do a lot of things to protect themselves starting with the implementation of safe computing practices. There is no silver bullet for this but strict observance of these practices will increase their networks' defense: What should the customers of breached companies do? Enterprises are not the only ones that should be concerned about data breaches. Consumers are also at risk of being affected by data breaches, especially if they use a certain service that the breached organization offers. Enterprises are made up of people who are consumers themselves so it is important for them to know how they can help prevent a data breach as individuals. Here are some steps they can do to protect themselves: Experts' Insights "Most of the targeted attacks that work are indeed persistent yet still build upon the usual weak link—the social engineering ploy where a human gets duped." — Paul Ferguson in "Highly Targeted Attacks and the Weakest Links" "… the level of targeting and sophistication (of these attacks) are results of prior knowledge gained by the attackers and are not necessarily caused by some technical brilliance with regard to the tools and methods used." — Nart Villeneuve in "How Sophisticated Are Targeted Malware Attacks?" "All of these instances prove that our standard thinking of protecting with a perimeter defense doesn’t work anymore. We really have to look at data access control and data access intelligence." — Raimund Genes in "What We Can Learn From Recent Hacks"