Think Before You Click: Truth Behind Clickjacking on Facebook
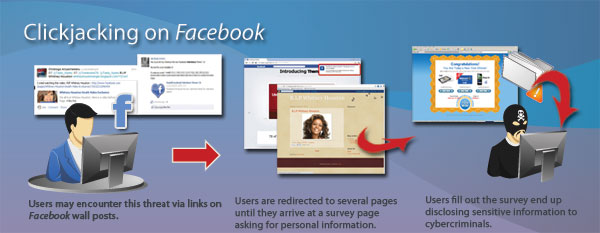
What is clickjacking on Facebook?
Clickjacking is a security threat similar to cross-site scripting. It happens when cybercriminals use several transparent layers to trick users into clicking a button or a link. Clickjacking may use different types of links, ranging from image links to text links.
The term “clickjacking” was coined because the attack aims to "hijack" the number of clicks meant for a particular page. It then routes to the clicks to another page. Cybercriminals hide malicious content under the veil of legitimate pages and may use iframes and malicious JavaScript to load this content from a third-party site.
Facebook, on the other hand, has their own definition of clickjacking. On their website, they describe clickjacking as "certain malicious websites that contain code to make your browser take action without your knowledge or consent". Through the use of social engineering techniques, clickjacking prompt users to click Facebook wall posts with links that lead them to survey scams. The spammed post spreads to their contacts' Facebook walls.
How do users encounter this threat?
Users typically encounter this in social media sites. The threat may appear as an enticing Facebook wall post. These wall posts are crafted to appear enticing to users.
How is social engineering used in clickjacking?
Cybercriminals use social engineering disguise threats as material that don't look blatantly malicious. Some of the most commonly used social engineering techniques that have been used in recent clickjacking attacks include the following:
- Exclusive Clips. These are threats that declare to have photos or videos of exclusive content. Users who may want to read about this "exclusive content" end up being tricked into clicking the malicious link.
- Latest Updates on World News. Clickjacking attacks also take advantage of the latest news to disguise itself. Updates on significant events may attract users who want to be updated in real time.
- Breaking Entertainment News, Gossip. Entertainment news and anything related to showbiz controversies and intrigue (including hoaxes) can be used to trick users.
- Promos, Contests. Users are enticed by any good contest or promo. However, in their desire to win, they may end up becoming victims of a clickjacking attack.
What happens once users click on these posts?
Once users click these wall posts, they are lead to a page that gives further instructions to click another link. However, this only leads the frustrated user to another Web page. There are also instances where users only need to click once to trigger the threat.
Here are two common forms of clickjacking that we have noted on Facebook.
Wall Posts Redirects to Several Pages
Users may encounter a post on their Facebook feed about a supposed video of a celebrity, browser extension, or a contests. Instead of seeing the content promised in the description, they are redirected to several other pages until they land on a Web page that asks for personal information such as mobile numbers and email addresses.
Cybercriminals may then use these information to spam more users and for other malicious activities. We've seen this form of clickjacking in the following instances:
- Cybercriminals Leverage Whitney Houston's Death
- Facebook Valentine's Theme Leads to Malware
- Facebook Free Breaking Dawn Part 2 Tickets Scam Spreads in Facebook
Clickjacking That Asks Users to Copy Code
An earlier version of the clickjacking attack became widespread on Facebook in early 2011. It's usually disguised as a wall post promoting a promo, contest, or an interesting app. Before joining the said contest or using the app, users are asked to follow several instructions. This includes copying a snippet of code onto their browser address bar. In doing so, users inadvertently "like," share, and create a Facebook event and spreads post to their contacts.
The following are examples of this clickjacking attack:
What is the driving force for this threat?
Since Facebook, Twitter and other social media sites are now considered hubs for the latest updates and news, users are likely to spend lots of time on these sites. Hence, cybercriminals saw this as an opportunity to lure users into their malicious schemes.
Clickjacking can be used as an alternative way to mine information from users aside from the usual phishing attack and spam. The survey pages asking for contact details doesn't appear menacing in light of a promo, so users are easily tricked.
According to threat engineer Christopher Talampas, clickjacking can also be considered a form of spamming. A potential clickjacking scammer would only need to create a Web page and link it to Facebook. This principle is akin to what spammers do. Talampas also mentioned that there are free clickjacking tools available online, which makes it easier for a potential attacker to create their own scheme.
How widespread are clickjacking attacks?
As of November 2011, more than 500 domains related to clickjacking attacks were found based on Trend Micro Web Reputation Technology data. This is probably due to the numerous Facebook scams related to Steve Jobs’ death as attackers might have taken advantage of this event to peddle their malicious pages.
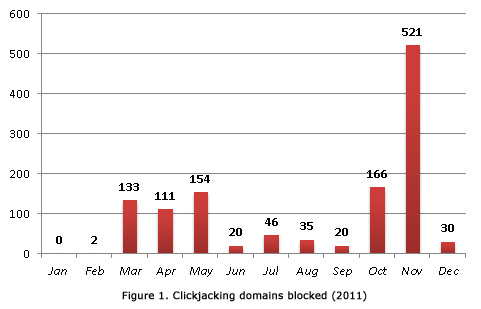
Trend Micro was able to block 1,238 domains related to clickjacking attacks.
For the first quarter of 2012, Trend Micro uncovered and blocked 624 malicious domains. The graph below shows a gradual increase in the number of domains related to clickjacking. This proves that clickjacking attacks are here to stay and may even increase, given the right social engineering lure.
In 2011 to the first quarter of 2012, the same data also reveals that most of clickjacking-related domains are registered in the United States with 757 registered domains.
|
Country |
Number of Registered Domains |
|
United States |
757 |
|
Canada |
550 |
|
South Korea |
192 |
|
Singapore |
107 |
|
China |
42 |
|
United Kingdom |
25 |
|
Netherlands |
10 |
|
Russian Federation |
5 |
|
Spain |
4 |
|
Bahamas |
2 |
Why does this threat persist?
Clickjacking attacks on Facebook persist because it is the most popular social networking site in the world. With 901 million active users as of March 2012, Facebook has become a natural target for cybercriminal activities.
Aside from its popularity, Facebook has an average of 502 million active users who share or “like” videos and links. Cybercriminals have taken advantage of such robust activities on the site to spam users and spread threats such as survey scams and malware.
This threat is persistent due to its clever use of social engineering techniques. Cybercriminals know how to use significant news events, celebrity gossips and events, and promos that appeal to users.
Cybercriminals have also found a way to update these attacks. According to Talampas, added capabilities make the threat more persistent. For example, one of the more recent attacks downloaded a malicious file with the extension .CRX. This is not the first attack that requires users to download a file. However, this shows that the next wave of payloads may include files with web browser extensions.
Also, the success of the clickjacking scheme may be attributed to users' lack of awareness regarding such threats. The growing number of teenagers and children using social media may also contribute its persistence, as they are the likely victims to this ruse.
How could users avoid this threat?
There are many ways for users to this threat. Here are some simple steps that'll do the trick:
- Be wary of clicking links posted on your Facebook feeds.
- Restrict your social media contacts to people you know personally.
- Study the privacy settings of your social networking site of choice. Make sure that your connection to these sites are secured (https://) as this may help in blocking malicious posts or sites.
- If possible, make your profile on Facebook private. Other than guarding your privacy, it also lessens the chances of encountering malicious users online.
- To know the latest news and updates about world events, promos, etc. consider bookmarking credible news sites instead of solely relying on social media.
- Proactively report or tag suspicious posts seen on social networking sites.
FROM THE FIELD: EXPERT INSIGHTS
"Clickjacking is the best way to spam. Why? Because cybercriminals only need to create a website containing malicious script and link it to Facebook. Scammer just need to publicly post the page and let other users to click them". - Christopher Talampas, Web Reputation Services Engineer
