Blockchain: The Missing Link Between Security and the IoT?
 The internet of things (IoT) has been associated with major
The internet of things (IoT) has been associated with major
Two key enablers merged into one: When the IoT meets blockchain
Within several decades, the IoT has significantly expanded its reach and connected numerous devices and networks in homes, workplaces, transportation systems, and even entire cities. The decade-old blockchain, on the other hand, is set to revolutionize business models through its encrypted and distributed ledger designed to create tamper-proof and real-time records. With the IoT and blockchain working together, the latter is expected to provide a verifiable and secure recording method for devices and processes associated with the former.
Blockchain works as a distributed ledger, where every deletion or modification of data is recorded, and as more entries, aka blocks, are put into it, a
In the context of recent noteworthy IoT security incidents, blockchain can reduce the risk of distributed denial-of-service (DDoS) attacks that affect multiple devices at once: An outage in one device shouldn’t impact the others. We have noted that in securing smart cities, such an expediency is crucial to maintaining connectivity and functionality in services, especially for critical systems.
With blockchain, each device will have strong cryptography, further ensuring secure communication with other devices and affording anonymity in IoT use cases where privacy is of utmost concern. Adopters will have the ability to better track devices and distribute security updates, helping to fortify potentially vulnerable devices.
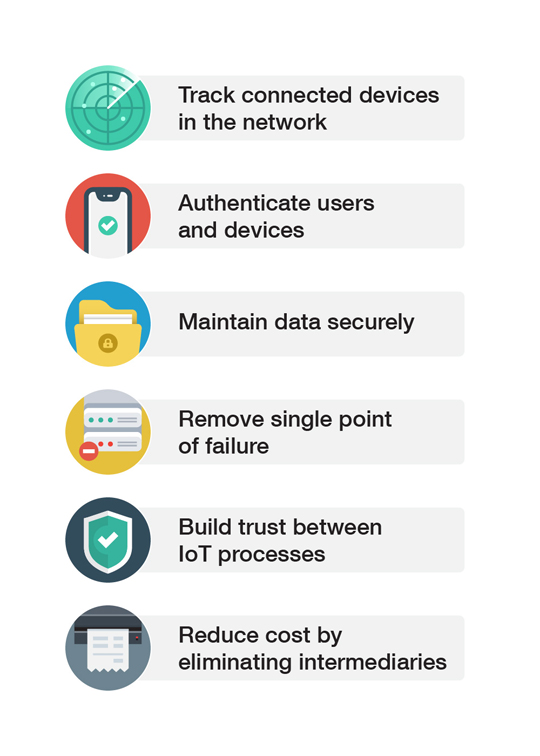 Figure 1. Blockchain in the IoT: Potential benefits
Figure 1. Blockchain in the IoT: Potential benefits
The merging of blockchain and the IoT is also expected to address the issue of oversight. In businesses, for instance, transactions made by multiple sources can be administered through an immutable and transparent record, where data and physical goods are tracked throughout the supply chain. In the event of an erroneous decision or system overload, the blockchain record should be able to identify the point — say, a device or a sensor — where something went wrong, and the business could take immediate action. Blockchain could also help reduce operational costs since it eliminates intermediaries or middlemen.
Blockchain implementations and use cases in the IoT
In the IoT sphere, blockchain has been gaining traction as well. A blockchain-protected security platform for the industrial internet of things (IIoT) is already being offered by one company. Touted as the first and only one of its kind, the solution aims to address the IoT’s broad attack surface by having more participants in control of the consensus and increasing the redundancy in systems. A blockchain-focused research center has also been formed to promote the development and commercialization of the technology and its capabilities to revolutionize the IoT ecosystem.
Challenges in integrating blockchain into the IoT
Blockchain in the IoT is indeed gaining momentum, but not without a few roadblocks. For one thing, the key concept to blockchain is the series of transactions that have been made and how they form a chain. The chain is created by keeping a reference
This setup seems to be ideal for securing the IoT. However, the caveat is that IoT devices are relatively underpowered and underlying blockchain protocols create overhead traffic, with the generation of a block introducing potential latency. This situation doesn’t bode well especially for resource-constrained and bandwidth-limited devices and operations that need real-time updates or speedy responses.
In terms of security risks, researchers have classified threats related to accessibility, anonymity, and authentication and access control. Malicious actors may threaten accessibility by preventing users from accessing data or services through such means as denial-of-service (DoS) attacks and cloud storage compromise. Furthermore, they can attempt to identify a particular user by finding links between the user’s anonymous transactions and other publicly available information. They can also try to pass themselves off as legitimate users to gain access to data, although threats against authentication and access control can be detected since all transactions are recorded and verified by users in the chain.
Additionally, in our security predictions for this year, we forecast that blockchain will be exploited by threat actors to expand their evasion techniques. It is also not far-fetched to conjecture that IoT sensors and devices can be compromised to transmit wrong information to a blockchain. By virtue of the technology, if an entry is authenticated, it will be recorded in the chain. Adopters
Security recommendations
When run properly, blockchain can greatly benefit IoT systems by decreasing costs and pushing efficiency. Even so, the technology’s penetration into IoT-enabled environments is far from optimal. For example, up to only 10 percent of production blockchain ledgers are expected to incorporate IoT sensors by 2020. Moreover, there still is a long way to go before most IoT systems become computationally competent enough to handle bulky blockchain implementations.
While the elimination of the single point of failure has yet to be realized, securing the IoT still lies in the continuous deployment of security for all connected devices. Aside from timely software updates to prevent downtime, what IoT adopters, individuals
- Changing default credentials. Factory default credentials have notoriously enabled IoT botnets in compromising connected devices. Users are therefore advised to enable password protection and to use unique and complex passwords to reduce the risk of device hacking.
- Strengthening router security. A vulnerable router makes a vulnerable network. Securing routers through comprehensive security solutions allows users to take stock of all connected devices while maintaining privacy and productivity.
- Setting up devices for security. Devices’ default settings should be checked and modified according to users’ needs. Customizing features and disabling unnecessary ones are recommended for increasing security.
- Monitoring traffic in the network. Actively scanning for anomalous behaviors in the network can help users deter any malicious attempts. Automatic and efficient malware detection can be also employed through real-time scanning provided by security solutions.
- Implementing added security measures. Users are advised to enable firewalls and use the Wi-Fi Protected Access II (WPA2) security protocol for added protection. Solutions that employ web reputation and application control also allow for better visibility across the network.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One