Securing Smart Homes
Welcome to the Smart Home: IoT Adoption and Security Accountability
One day, everything will be buttonless. Nobody will ever need to grab the remote to turn on the television or hit a switch to kill the lights. These devices will just do what they’re supposed to, all by themselves, without any physical prompts from the user. They won’t be set off by claps, or voice commands, or hand gestures in the air. They will gain a certain level of independence that will diminish the need for human interaction. This is the very inevitable, very near, and very real future. Smart technology is here, and it’s only getting smarter.
Often, people talk about these technologies and the internet of things (IoT) as if automation were the only criteria for gadgets and infrastructure to be called smart. But it’s more than just that.
Firstly, for any device to fall under IoT, it needs to go beyond its original basic functions. It has to be able to receive, process, and transmit digital information the way a personal computer normally does. In order to do this, it should meet a second requirement—connectivity. The device should have the ability to connect to the internet or even communicate with other smart machines around it.
Think of it this way: A smart home fitted with automated blinds can have them immediately open once the sun rises. This triggers the smart lightbulbs inside the house to turn off. This relay of actions allows natural sunlight to come in, illuminating the house while saving on energy. Another example of devices communicating with each other is when a smart TV’s volume goes down every time a phone call comes in. This makes it easier for the user to notice the call.
Both automation and connectivity have helped push IoT forward, but, in the same way, they have also held it back.
The Inevitable Rise of Home IoT Adoption
For a number of years, the mass adoption of IoT has stalled. Users found smart devices impractical. The production of these one-off gadgets was very costly, thus driving up their prices. A few years ago, they were more of a luxury than a necessity. On top of this, not every country in the world has the kind of infrastructure needed to make internet access available to everyone. The early adopters were limited to enthusiasts who had the money to afford IoT devices and were based in regions that allowed them to optimally use their devices.
But the market has since shifted. People are clamoring for smarter things to either ease their daily lives or be a source of personal pleasure. And the industry is taking notice.
Multi-billion dollar companies out of Silicon Valley are trying to one-up each other in terms of innovation, offering a very diverse collection of IoT devices to the public. Companies, regardless of size, that are not willing to acknowledge this shift will eventually get left behind. Some things that come to mind are those cellphone giants that did not respond to the shifting consumer demand for smarter phones. They eventually disappeared.
Research and advisory firm Gartner even predicted that there will be over one billion connected devices in use by 2018, and that figure alone is just for smart homes. Another billion devices are projected to be used in smart commercial buildings. The remaining billion devices are divided accordingly to industries such as healthcare, transportation, and other organizations that make up fully functional smart cities.
Japan and Germany are two of the many countries whose urban areas are already embracing smart homes. In these places, IoT has become ingrained in people’s lives to the point of necessity.
In metropolitan Japan, where commuting takes a big toll, workers are able to save time and energy during their long rides from their office to their house through home automation. Apartments with smart cookers, for example, can churn out meals which should be ready by the time their owners step through the front door.
In Germany, where the elderly make up a significant portion of the population, a number of people have opted to use smart health-monitoring devices. In the event of an emergency, like a heart attack, the device can trigger a call for emergency assistance. These monitors can save people’s lives.
Holding Accountability for Home IoT Security
The rise of the home IoT adoption rate will ultimately increase the competition between several players in the market. But with no unified regulating body to instill functional and security standards on these devices’ manufacturers, this can lead to several security issues in the long run.
This then begs the question: Who should be responsible for IoT security?
Should it be the IoT users? At the moment, it seems to be the case. Users have the freedom to decide which IoT devices to introduce to their homes. They can opt to install a smart home entertainment system in their house knowing what kind of information they could be sending back to the device manufacturer every time they use it. It’s an ongoing tradeoff, with users weighing their personal privacy and safety against their personal comfort and satisfaction.
But the IoT landscape is continuously evolving. As IoT branches out from user homes and into the city, users become significantly more powerless.
A good illustration would be new smart condominium units already being fitted with IoT devices like security cameras or emergency sensors. People who will be moving into these spaces will have no other choice but to opt in to that level of surveillance. Just imagine if all future building developments, both private and public, were required to have these IoT devices in place.
Once smart technologies get broadly used for public utility buildings or vehicles, users will have no reign over their privacy and personal security. The brunt of that responsibility ultimately shifts from the users to the IoT manufacturers. What risks should manufacturers foresee to protect both their users and their organizations from potential disaster?
We shall explore more of this in part two of this blog series.
From Comfort to Chaos: The Risks of Owning a Smart Home
What do you do when the thing that’s supposed to make your life easier starts working against you?
It was April 2015 when a couple from Washington discovered something unsettling. Their three-year-old son had been complaining about an invisible man talking to him at night. They were initially apprehensive about the story until they themselves heard a stranger’s voice come out of the baby monitor they installed in their son’s room.
“Wake up, little boy. Daddy’s looking for you,” it said.
Their fears were further confirmed when they noticed the device’s camera tracking their movements. The disembodied voice continued taunting them: “Look, someone’s coming into view.”
Theirs is just one of many horror stories involving hacked home IoT devices.
Risks versus benefits
People should be able to use smart devices without worry, but the current reality makes this a challenge. The way today's home IoT devices are designed and built puts functionality to the fore and often relegates security as an afterthought. When these flashy smart machines hit the market, they come with a bevy of risks that excited buyers may not be fully aware of. Are they able to weigh all the pros and cons and prepare themselves before welcoming potential hazards into their homes?
First, there’s the issue of privacy. A number of IoT devices have the function to record or transmit audiovisual information to the cloud. If an attacker is able to intercept this communication, it gives him the proverbial eyes and ears into people’s homes. Going back to the case of baby monitors, attackers were able to spot and take advantage of software flaws. By doing so, they turned these devices—originally intended to help out parents to check on their children—into makeshift spy cameras.
Some IoT gadgets like automated voice assistants are able to listen in for voice prompts, process them via the cloud, and answer back in a matter of seconds. There have been contentions in the past regarding how much of people's conversations are being recorded by the said devices. Normally, voice assistants only get activated when they are triggered by certain "wake words." For Amazon Echo, it activates whenever someone says "Alexa." Amazon guarantees their customers that their device merely streams recorded audio to their cloud if it’s found in between the wake word and the end of the request. The company provides users with the option to turn off device listening—something that home users should avail of.
Wearables such as fitness trackers can record a user’s exact whereabouts. This kind of data, in the hands of malicious individuals, could lead to actual physical risks. Attackers would be able to see whether a house owner is away or maybe know if a person they’re targeting is heading to a specific location. Of course, these kinds of scenarios are extreme, but they are not farfetched.
Then there is end-of-life, which is one consideration that’s often forgotten. The functionality of many IoT devices is reliant on cloud-based components supplied by the companies that built them. In case these said companies abruptly close up shop or get absorbed by other organizations, the support for these devices goes into limbo. One example of this scenario is the case of the 246 Padlock in Japan. The padlock let users lock and unlock the device using a key accessed via a smartphone app. Since the service shut down this June 30, users of the said lock no longer have a way of unlocking the device unless its battery runs out—which, according to the manufacturer, could stay powered for around 180 days. Only those users who could physically return the padlocks were eligible for refunds.
Another case is that of Revolv, a smart home hub which ceased its operations a few years after being acquired by Nest. The hub acted as a home command center that allowed users to access other smart appliances via central app. But since Nest decided to shut down the service this May 15, many of the device’s users were left with nothing but a fancy accessory that no longer serves its purpose.
Internal and external factors
The factors that contribute to these risks can be categorized into two categories—internal and external. Internal factors are things that can be controlled by either the IoT manufacturers or home users themselves; external ones are those outside of their sphere of influence.
Examples of external factor are weather disturbances or power outages. In case the power goes out in a storm, how would that affect the status of home devices? Do smart locks remain locked? If so, would home owners get locked out of their own homes? If the power goes back, do the devices reset?
Other external factors include attackers who, as stated previously, can spy on unsuspecting home users. Attackers can take advantage of device flaws to gather data and profile their targets better. They can use this said data for sabotage or blackmail. Bad guys can also perform man-in-the-middle attacks to send malicious commands to devices. They can shut off fire alarms, manipulate smart lightbulbs, and potentially tamper with other smart home devices to the point of breaking them. When malicious attackers enter the picture, a home designed for comfort can spiral into chaos.
But there is a caveat. These kinds of attacks—at least for now—take a lot of time and effort to set in motion. Unlike PCs that more or less run widely used operating systems, IoT devices have a much more fragmented landscape. Attacks on a set of IoT devices cannot be easily replicated on a different set from a different manufacturer. Some IoT hacks also require attackers to physically buy and tamper with samples of their target devices before they can actually proceed to attacking their intended targets. Knowing this, people should not be afraid of using their smart gadgets; they just have to learn to use them wisely.
Many risks stem from how home users have set up their IoT systems. Poorly configured wireless home networks are still the best attack vector for bad guys seeking to get a foothold into a smart home. If a user, for example, does not change the default password on their device, it makes it easier for an attacker to hack into.
IoT manufacturers can also be at fault for putting their users at risk when they don’t update their firmware. By not doing so, they create a network of homes with vulnerable devices. And although sharing source code isn’t technically bad (researchers can use this to test device security), attackers might also find ways to use these codes to their advantage.
We shall be discussing how both manufacturers and home users can prevent these risks and protect themselves from attacks in the final part of our home IoT security series.
The Usual Suspects: IoT Attackers and Motivations
Who would attack a smart home and why? What would an attacker gain by doing so? Unlike PCs and smartphones, IoT devices—at least those available in the market right now—don't all run on a single operating system. This difference makes it more challenging for interested people to launch attacks on a wide scale. Compromising the security of such devices would also require a bit of knowhow and the right tools.
Over the last few years, there have been reports published by security researchers that have proven that smart devices can indeed be abused. These researchers set out to break these gadgets with the sole intention of informing manufacturers of the areas they need to improve in terms of their devices’ functionality and security.
Just last year, our very own Trend Micro researchers, for example, proved that it’s possible for an attacker to remotely snoop on smart car data or even alter the status of automated gas tank gauges. These experiments were done in controlled settings, decreasing the chances of doing any real-world damage. Bad guys, unfortunately, are not that considerate.
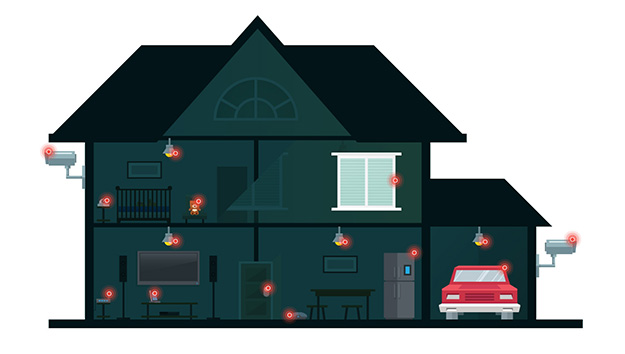
Knowing fully well that IoT devices can be hacked, what more can bad guys do to much simpler smart devices found at home? Here, we list down the usual suspects, their probable motivations, and consider how likely or unlikely they’d go for smart homes.
Taking note of possible personas that can attack smart homes will give home users a better understanding of what kinds of attacks they can expect and what they should safeguard. As for the actual steps they and home IoT manufacturers can take to protect themselves, we give recommendations in the final part of this series.
Securing the Smart Home: Tips for Home Users and Manufacturers
Home users and home IoT device manufacturers can minimize the potential risks that come with a smart home. They just have to know where to start. Below are some practical security measures they can apply.
As a home user, what can you do to secure your smart home?
The reality for home users is that not all smart devices have basic built-in security measures. This gives you, as a user, the de facto responsibility to secure the way you set up and use the devices. When you start prioritizing the security of your smart home, it will give you and your family some peace of mind and put you in a better position to continue introducing smart devices into your home.



Set up your smart devices for security
How much of the smart appliances in your home are accounted for? Have you taken the necessary precaution of learning how they work and what they’re fully capable of? If, for example, your home IoT devices have encryption capabilities make sure they’re on by default. Enabling encryption can deter attempts at compromising sensitive data in the devices.
Previously, we also talked about how devices like the Amazon Echo can listen in for voice prompts. If you are not comfortable with this capability being on 100% of the time, then perhaps you can temporarily disable that function until you find the need for it again.
Some devices come with cloud-based solutions, which is a convenient way to access data from your devices. But as much as possible, try to avoid them. Devices like that should be approached with caution, especially if the manufacturer is not known for expertise in handling data in the cloud.
Checking all your devices’ default settings and knowing how to modify them will enable you to customize the features that best suit your needs–while keeping your privacy and personal security intact.
Also be sure to check if all your gadgets are up to date. Regularly update their firmware to the latest versions every time you are notified to do so. Many devices even have an auto-update feature which does this for you. Updating your devices at least once a month should reduce your risk of getting hacked through unpatched vulnerabilities. Backing up or saving copies of your devices’ original configuration files should also provide you the option to restore your device settings to their previous state in case of an unforeseen failure.
Secure your home router
Consider your router as the gateway to all the internet-connected devices in your smart home. It’s where all the internet traffic passes through so you have to guard it well. Some attackers are able to compromise home routers since many models come with default credentials that regular home users often forget to change. This is why it’s always important to create a strong router password right after you’ve set it up. How to do that is typically indicated in the router’s user manual. You can also refer to the manufacturer's website just in case your manual goes missing.
When connecting to the home network, instead of the widely used and easily compromised Wired Equality Privacy (WEP), you can opt for the Wi-Fi Protected Access II (WPA2) protocol. By also setting up the firewall to only allow traffic on specific ports, you can significantly cut down on potential network-probing attempts. Another measure you can take is setting up a guest network for your devices. This limits the devices’ ability to talk to each other and potentially pass on malicious commands or content.
Smart home network solutions can help secure potential network intrusions through virtual patching, default or weak password detection, Web Threat Protection (WTP) for all connected devices, and parental controls to protect kids online.
Change your passwords frequently
It’s not enough that you place a password on your router or on your smart devices. Passwords can fall into the wrong hands– especially when you have people visiting your home, asking if they can connect to your Wi-Fi or sync their own gadgets. Frequently changing your passwords can ban outsiders from accessing your router and devices. Also make sure to use unique passwords for each of your home IoT devices. Soin case an attacker figures out one of your passwords, the possibility of your other devices getting hacked will be lower.
Also make sure to keep your passwords long and complex. If the devices allow you to, it’s best to use a combination of upper and lowercase letters, numbers, and special characters. As much as possible, don't include any names, birthdays, or addresses– since those information can be used to guess your passwords in brute-force attempts.
Review your devices’ log history
Some smart devices will allow you to check the activity logs whenever they connect to the internet. Again, you will need to know your devices inside out for this. Read up on your particular device’s model if it has this capability. You, or somebody in your family who is tech-savvy, can be designated to regularly monitor and review device logs for any suspicious activity. For instance, many home security cameras allow users to view the history of IP addresses that have accessed its feed. By going through the logs, you can find out if strangers have been keeping an eye on you.
Protect your smartphone
Since a number of IoT devices can be controlled through mobile devices via an app, your smartphone also needs protecting. Here, standard mobile security guidelines apply. Much like smart devices, make sure your phone is updated with the latest firmware version. Next, download only legitimate apps from your smart device providers and review the app permissions before installing them on your smartphone. Installing a mobile security app can also prevent malicious apps or codes from running on your phone.
How can manufacturers develop devices safe for everyday use?
The home IoT industry allows a lot of creativity for manufacturers who want to pack their devices with cool functionalities that may interest potential customers. But without focus on security, they risk coming out with faulty products that can compromise the safety of their users and could lead to monetary losses and possible legal concerns. Having a clear security mindset from day one to product roll-out will allow home IoT manufacturers to meet their obligation of protecting users who seek better security and privacy.
Implement a security-by-design approach
Manufacturers need to have the mindset that any device, once connected to the internet, becomes open to abuse. In the early stages of product development, testing and implementing appropriate security measures should have the same weight as enhancing device attributes. Enforcing data encryption, for example, can be one option. Manufacturers can place limitations on communication protocols as these can be used as main attack vectors. In case of any suspicious traffic, the devices should be able to alert the users. Home IoT devices should also be designed to have a streamlined and intuitive security interface that allows users to easily resolve security issues if ever they arise.
Perform penetration testing and regular security audits
Vulnerability testing—where developers can simulate or perform attacks—is a practice that can help in assessing whether the device’s security can be circumvented or weakened. This is not only crucial for evaluating the security infrastructure but it also benefits device performance and maintenance in the long run. Are communications protected against disclosure, modification, and denial of service? Can users opt out of the data collection? Is the user’s data correctly processed according to privacy regulations?
Manufacturers should be able to keep compliance on track and save the company from future business headaches by conducting risk assessments and security audits. This can be done by integrating security in the devices’ endpoint SDK. Security solutions for SDKs should allow manufacturers to block attack attempts, perform risk assessments, and secure their IoT platforms before a new firmware or patch is released.
Consider third-party collaboration
Security specialists reviewing the system security of a device is crucial in aiding device makers with limited experience in security. Through this, manufacturers can avoid design inconsistencies and flaws. Third-party researchers who share device vulnerabilities can also be accommodated by providing an incentive through bug bounty programs.
For extra defense against evolving cyberthreats home owners can take advantage of Trend Micro Home Network solutions that defend against threats for all connected devices inside their homes.
Protect Your Home Network: Secure Your Router
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines








 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One