Ransomware Recap: January 30 - February 15, 2017
 What happens when ransomware manages to infiltrate and take over the control systems of important industrial plants? Researchers from the Georgia Institute of Technology tried to answer that question by developing a ransomware variant that could potentially infect industrial environments in a proof of concept demonstration at the 2017 RSA conference in San Francisco.
What happens when ransomware manages to infiltrate and take over the control systems of important industrial plants? Researchers from the Georgia Institute of Technology tried to answer that question by developing a ransomware variant that could potentially infect industrial environments in a proof of concept demonstration at the 2017 RSA conference in San Francisco.
[Related: Using Shodan to search for exposed cyber assets in the United States]
The research team simulated a hacker who has gained access to the control systems of an industrial plant. The primary targets were the programmable logic controllers (PLCs), small dedicated computers that monitor and control the devices that run the plant. In this case, the team built a model water plant complete with PLCs, which they infected with the custom ransomware. Under this setup, the research team managed to manipulate different aspects of the water plant, allowing them to shut down water valves, display false readings and even change chlorine levels.
Although there haven't been any reports of ransomware that targets industrial PLCs, according to David Formby, a Ph.D. student in the Georgia Tech School of Electrical and Computer Engineering and one of the researchers in charge of the demonstration, the team expects cybercriminals behind the current ransomware attacks to eventually move beyond customer data to targeting actual control systems. According to Formby’s faculty advisor, Motorola Foundation Professor Raheem Beyah, it is important for the operators of these industrial systems to strengthen their security and limit the connections to vital control systems.
UNIX-based ransomware on the rise
Trend Micro researchers gave a presentation at the RSA Conference which talked about the rise of ransomware targeting UNIX-based systems. The topic covered Linux.Encoder (detected by Trend Micro as ELF_CRYPTOR family), reportedly the first ransomware that goes after Linux systems, and KeRanger (OSX_KERANGER), which infects Mac OS X computers.
While these kinds of ransomware are still in the early stages of development, further analysis reveal that the cyber criminals behind these malware are starting to add more capabilities in an effort to expand their reach and maximize their profits. For instance, KeRanger was discovered to possess unused functions for deleting or encrypting backup tools in OS X, while Linux.Encoder was continuously refined in an effort to perfect its encryption routine.
A growing Crysis
Last September, the ransomware family known as Crysis (detected by Trend Micro as RANSOM_CRYSIS.A was found to have been targeting businesses through Remote Desktop Protocol (RDP) brute force attacks. Since then, Crysis’ attack volume has been growing at a rapid pace with an infection amount that doubled in 2017 from a comparable 2016 timeframe. The cyber criminals behind Crysis have also managed to extend its reach ; while the initial attacks focused on businesses in Australia and New Zealand, recent attacks were discovered to have primarily affected US-based healthcare services.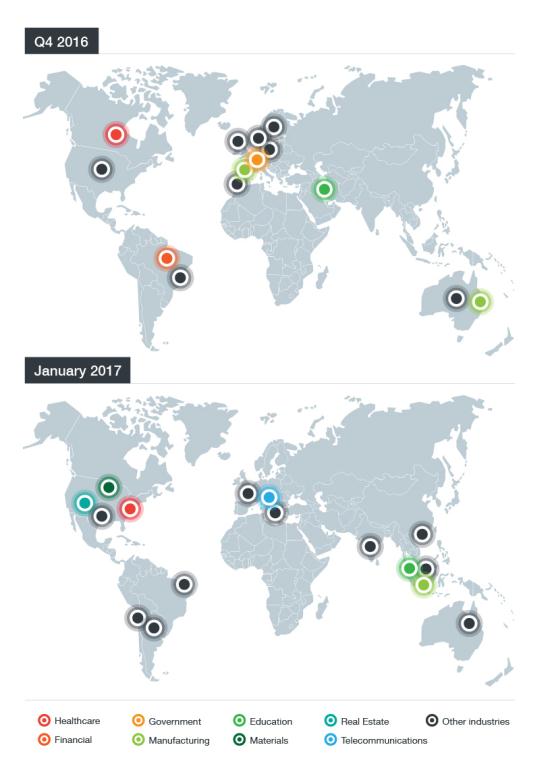
In these incidents, the perpetrator of the ransomware attack use shared folders or the clipboard to gain access to the victim’s machine. This method allows them to force their way into the system using crude but effective tactics such as entering common usernames and passwords. Multiple attempts to infect the endpoint may also happen in a short span of time.
CERBER gains additional capabilities
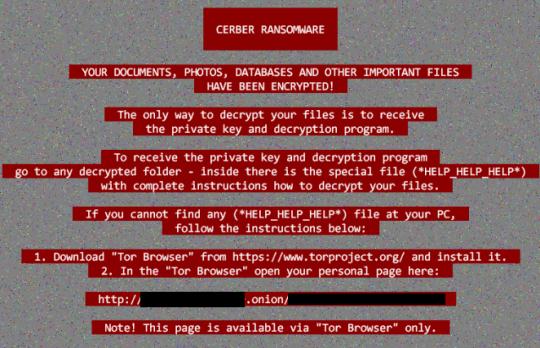
CERBER is a name that often comes up whenever the topic of notable ransomware is discussed – and with good reason. From its initial coverage, CERBER has evolved as it identified new targets and gained new distribution channels, including malicious advertisements, exploit kits and script files. Recently, Trend Micro detected a variant of the notorious ransomware that has the ability to detect and avoid encrypting security software.
The new CERBER variant (detected as RANSOM_CERBER.F117AK) does this by checking three Windows Management Interface (WMI) classes FirewallProduct, AntiVirusProduct, and AntiSpywareProduct. Once queried, CERBER extracts the path for these specific items and adds them to the list of folders that it will avoid encrypting.
Although the motivation for developing this current CERBER variant is unclear, it might be a case of the perpetrators being extra cautious with their mode of attacks.
Here are the other notable ransomware stories from the past two weeks:
A potential new Erebus variant
First discovered in September of 2016, Erebus (detected by Trend Micro as Ransom_EREBUS.A) was distributed primarily through malicious advertisements designed to lure users to an exploit kit server that dropped the ransomware as its payload. In early February, a new ransomware carrying the Erebus name (detected by Trend Micro as Ransom_EREBUS.TOR) was detectedby researchers who noted that the new variant is significantly different from the earlier version.
Once the new Erebus variant infects the target system, it will encrypt files and place a ransom note on the desktop titled README.HTML. The note threatens to delete the encrypted files unless the user purchases a decryption key within 96 hours.
Erebus will also clear the Windows Volume Shadow Copies so that they cannot be used to recover files.
SerbRansom 2017
Developed by an ultranationalist Serbian developer, the ransomware known as SerbRansom 2017 (detected by Trend Micro as RANSOM_SERBRAN.A) threatens its victim by claiming that it will delete a random file every five minutes the $500 ransom is not paid.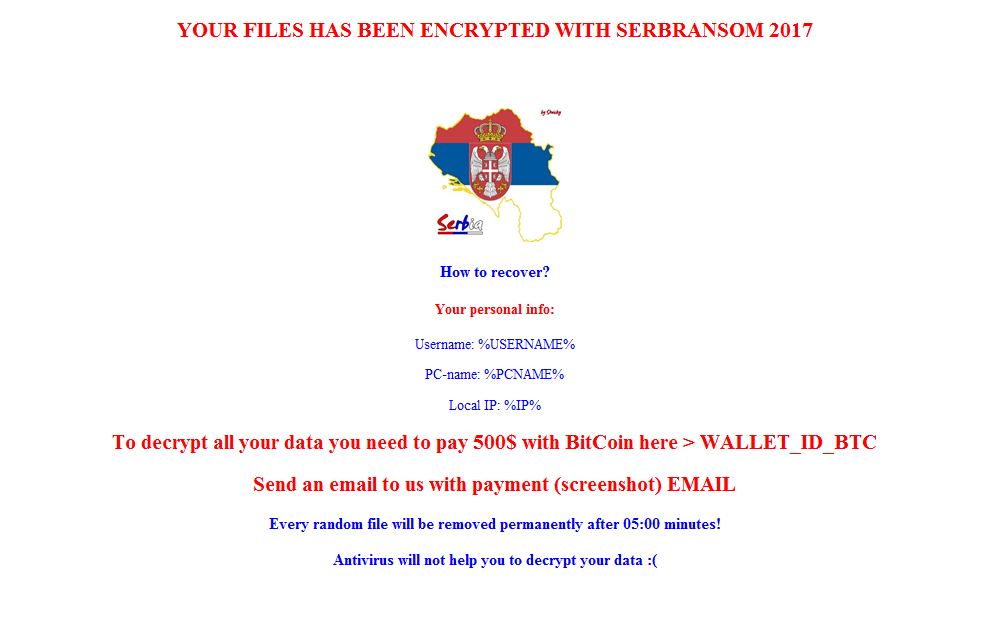
However, further analysis reveals that SerbRansom 2017 does not actually have this capability, and in fact uses simple encryption methods. In addition to the actual malware’s discovery, researchers from Malware Hunter also managed to find its builder, which allows the developer behind the ransomware to generate customer versions of the malware—an indication that it could be monetized soon.
SerbRansom 2017 uses the extension .velikasrbija, which is Serbian for “Great Serbia” and targets the following files: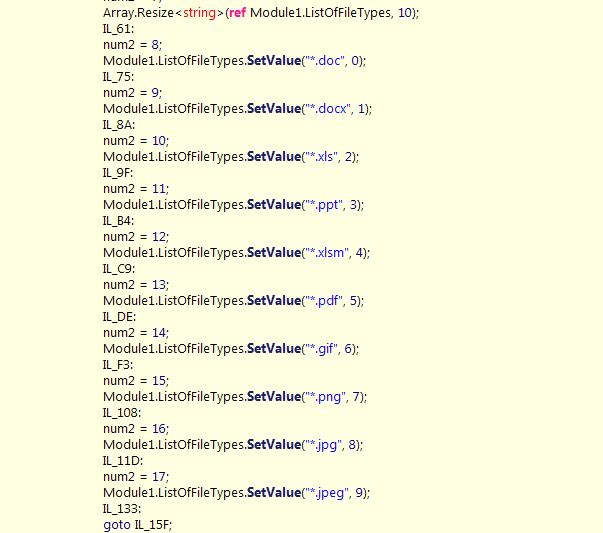
LataRebo Locker
Instead of encrypting files, LataRebo Locker (detected by Trend Micro as RANSOM_REBOLOCK.A) prevents its victims from using their computers via a large image containing the ransom note, which can be seen below.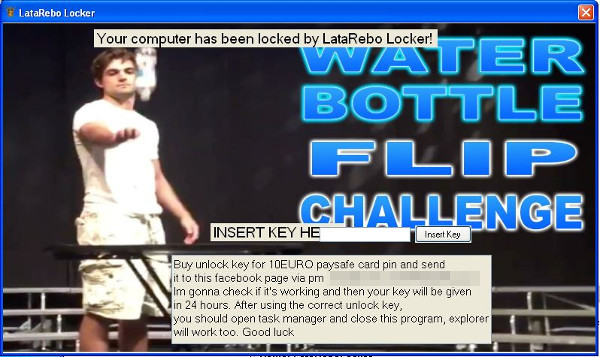
It adds entries to the Windows Registry in order to enable activation whenever the user’s operating system starts up. It will also add additional registry entries that disables the task manager, preventing users from terminating its process.
Once the correct key (“Rebatsa”) is entered, victims will be able to access their computer’s functions. In addition, Windows Task Manager will be re-enabled and the auto-start function will be removed from the registry. However the program itself will not be terminated.
Ransomware Solutions:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One