osCommerce Mass Compromise Leads to Data-Stealing Malware Infections
Data de publicação: quarta-feira, 10 de agosto de 2011
Using open source software (OSS) has, like all things, advantages and disadvantages. While these boast of convenience, ease of installation, and affordability, these can also expose your business and your customers to certain risks. This is exactly what happened in the recent osCommerce attack wherein more than 5.9 million Web pages in various e-commerce sites were compromised to steal financial information.
Unlike the first two attacks, however, this specifically targeted users who recently shopped online, making them more vulnerable, as they just used their credentials.
—Karl Dominguez, Trend Micro threat response engineer
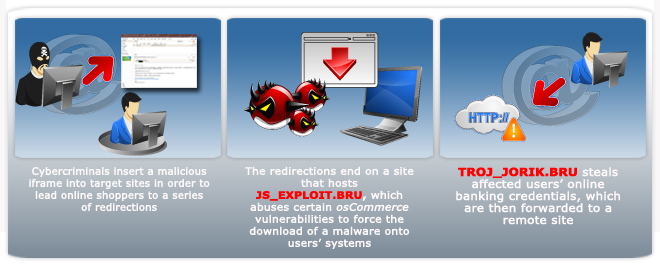
Based on our analysis, the attack begins with the use of osCommerce, an open source e-commerce solution that allows users to easily manage their online shops. The attackers began their assault by inserting an iframe that led to certain URLs in each e-commerce site, which triggering several redirections. These redirections sent affected users to a malicious page wherein an exploit kit abuses certain vulnerabilities in the software in order to force the download of a malware, aka TROJ_JORIK.BRU, onto the users’ systems. This Trojan steals affected users’ login credentials and other data for specific online banks and other financial institutions’ sites. The stolen information is then forwarded to specific Web pages and into cybercriminals’ eagerly waiting hands.
How do Web pages get infected?
Cybercriminals begin their attack by abusing a vulnerability in osCommerce via the insertion of a malicious iframe into certain pages of legitimate sites. This iframe redirects affected users to various sites and finally led to a page that hosts an exploit kit we detect as JS_EXPLOIT.BRU. This malicious JavaScript then abuses other software vulnerabilities to force the download of a malicious file onto the users’ systems.
What happens when TROJ_JORIK.BRU infects Web pages or systems?
Visiting any compromised site triggers the execution of the embedded malicious script that leads to a series of redirections before they end up on a malicious site that hosts JS_EXPLOIT.BRU. The malicious process is subtle, as the page the user is on stays the same. An ordinary user may not even notice that the malicious script has started running, as it carefully hides its routines.
System infiltration involves the exploitation of certain vulnerabilities, which then forces the download of TROJ_JORIK.BRU onto infected systems.
How does TROJ_JORIK.BRU affect users?
Affected users can become potential information (e.g., online banking and other financial institution related data) theft victims. This can result in significant financial losses as well as loss of trust and reputation for the sites that were responsible for the infections.
What is the driving force behind the osCommerce attack?
The attackers were driven by the lure of profiting from their victims’ login and other personal credentials.
What makes this attack similar to previously reported mass compromises? What makes it different?
Similar to the LizaMoon and WordPress mass compromises, this attack made use of redirections as well in order to lure users to a malicious page so the cybercriminals can steal their online credentials.
How can Web page owners determine if their sites have been infected? What can they do to mitigate or even prevent infection?
Web page owners who used osCommerce can check for unfamiliar iframes or scripts in their HTML versions. Remove suspicious-looking iframes if found. To prevent infection, improving their site’s security and seeking an alternative to osCommerce is advisable. If this isn’t possible due to cost or other constraints, updating to the software’s most recent version can also help.
How can affected users remove JS_EXPLOIT.BRU and TROJ_JORIK.BRU from their systems?
Non-Trend Micro customers can use Trend Micro Browser Guard to prevent JS_EXPLOIT.BRU from executing on their systems. Trend Micro Browser Guard has the ability to remove malicious JavaScripts from Web pages, rendering similar threats harmless.
Are Trend Micro customers protected from JS_EXPLOIT.BRU and TROJ_JORIK.BRU?
Yes. Solutions supported by the Trend Micro™ Smart Protection Network™ block access to related URLs and prevent the download of the related malicious files onto our customers’ systems.
What can users do to prevent similar attacks from affecting them?
Users can prevent similar attacks from affecting them by installing a reliable security software that prevents the download and execution of malicious scripts and files. They can also make it a habit to only shop from reputable sites.
EXPERTS’ INSIGHTS
“This attack is quite efficient. It specifically targets users who visit e-commerce sites since they are the ones who are most likely to have gone shopping online before and are more likely to have their credit card information stored in their systems.”