Analysis by Julie Cabuhat
Late last year, in several high-profile and potent DDoS attacks, Linux-targeting Mirai (identified by Trend Micro as ELF_MIRAI family) revealed just how broken the Internet of Things ecosystem is. The malware is now making headlines again, thanks to a new Windows Trojan that drastically increases its distribution capabilities.
We predicted last year that the propagation of Mirai-like malware for DDoS attacks is set to increase—but this new Trojan focuses on spreading Mirai itself and not any mimic. In 2015 and 2016, Mirai relied on a type of brute-force attack, with bots constantly pinging IP addresses to pinpoint more potential victims. This newly-identified Windows Trojan (detected by Trend Micro as BKDR_MIRAI.A) helps find potential Mirai victims, and amplifies the Mirai bots distribution.
The Windows Trojan connects to the C&C server to find the IPs to be scanned. If it successfully logs into its targeted system, it checks the OS running on the targeted machine. If it is running Linux, it drops the Mirai malware to create a new bot. If the machine is running Windows, then the Trojan copies itself into the machine and continues to look for Linux targets. The Trojan can drop two different payloads, one for Linux machines and another for Windows.
The original Mirai was discovered in August 2016 and targets IoT devices running Linux-based firmware: routers, digital video recorders, printers, CCTV cameras and others. To infect these devices the malware chooses random IPs and attempts to use default administrative credentials to take over the device via ports 7547 and 5555 (TCP/UDP), 22 (SSH) and 23 (Telnet). After the source code was exposed to the public in October 2016, attacks increased. Variants were used in attacks that affected major sites like Netflix, Reddit, Twitter and AirBnB, as well as 900,000 home routers from Deutsche Telekom.
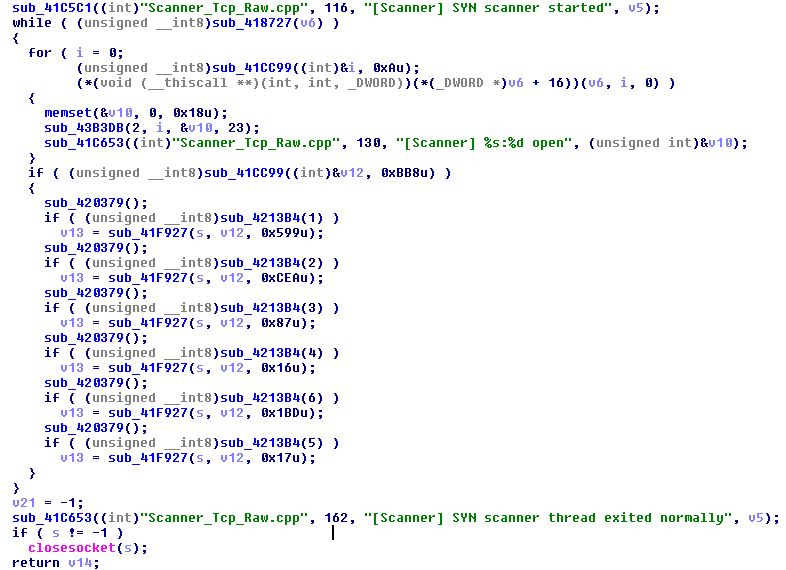
Figure 1. Windows Trojan port scanning code
The Windows Trojan targets more ports than the original Linux Mirai, hunting for every possible avenue of infection. It checks if the following ports are open: 22 (SSH), 23 (Telnet), 135 (DCE/RPC), 445 (Active Directory), 1433 (MSSQL), 3306 (MySQL) and 3389 (RDP). These ports are typically kept open for a variety of reasons: aiding the writing of distributed software, file sharing, and remote device administration
Based on the ports targeted, we can see that the Trojan also works to identify host software like MySQL and Microsoft SQL Server databases. If one of these is identified, it will try to create a new user with administrative privileges. Specifically, when it encounters the Microsoft SQL Server it will create a database user “Mssqla” with sysadmin privileges. With that level of access, a malicious user could change server-wide configuration options and shut down the server, change logins and their properties, end running processes, run the BULK INSERT statement, and also create, alter, drop or restore any database.
This Windows Trojan is designed simply to distribute Mirai, but it also has potential to evolve. It could easily expand to distribute other malware, and since it targets Windows devices it allows Mirai to broaden its activities as well.
This malware could also be used to compromise IoT devices within the same network as its infected victim. The IP addressing of home networks is usually very predictable—most home routers use the 192.168.x.x IP space. Since the Windows Trojan gets the IP addresses it hits from the central C&C server, the server could instruct the Trojanized device to scan the local IP space. This would result in the compromise of all connected IoT devices using default passwords.
Trend Micro™ Security and Trend Micro Internet Security offer effective protection for this threat, with security features that can detect malware at the endpoint level. To protect IoT devices like home routers, security solutions like Trend MicroTM Home Network Security can check internet traffic between the router and all connected devices. Enterprises can use Trend Micro™ Deep Discovery™ Inspector which is a network appliance that monitors all ports and over 105 different network protocols to discover advanced threats and targeted attacks.
Our BKDR_MIRAI.A samples had the following SHA1 hashes:
- 42c9686dade9a7f346efa8fdbe5dbf6fa1a7028e
- F97E8145E1E818F17779A8B136370C24DA67A6A5
- 9575D5EDB955E8E57D5886E1CF93F54F52912238
- 938715263e1e24f3e3d82d72b4e1d2b60ab187b8
TippingPoint customers are protected from this vulnerability with the following MainlineDV filter:
- 27134: HTTP: BKDR_MIRAI.A Checkin