Why Leading Organizations Are Rethinking Their Cybersecurity Strategy
Imagine managing security for a modern organization: dozens of AWS accounts, applications running across multiple clouds, developers deploying several times a day, and your security team trying to keep up using tools that feel like they were designed for a different era. If this sounds familiar, you're not alone.
The truth is that the world has changed, but many solutions haven’t kept pace with the strategies. Today, we’ll explore how this transformation is unfolding and why it could be the competitive edge your organization needs.
The Problem Everyone Knows (But Few Admit)
Frustrations among technology leaders are universal and predictable.
“We have twenty different security tools, yet we still lack visibility in critical areas.”
Or the classic: “The development team complains that security slows everything down, while the security team says developers ignore policies.”
Behind these complaints lies a well-known challenge: tool sprawl that don’t work together.
Industry research consistently reveals organizations are overwhelmed by a multitude of security products — generating isolated alerts, requiring specialized expertise, and creating visibility gaps that skilled attackers know how to exploit.
It’s the security tooling that has evolved as a patchwork of best of breed tools. We implemented CWPPs (Cloud Workload Protection Platforms) when we realized cloud workloads needed specialized protection. We adopted CSPMs (Cloud Security Posture Management) when misconfigurations started causing incidents. The approach was always reactive: identify a gap, buy a solution. The result is a portfolio of siloed specialized tools that excel individually but fail to deliver unified visibility.
The Silent Revolution: When AI Meets Security
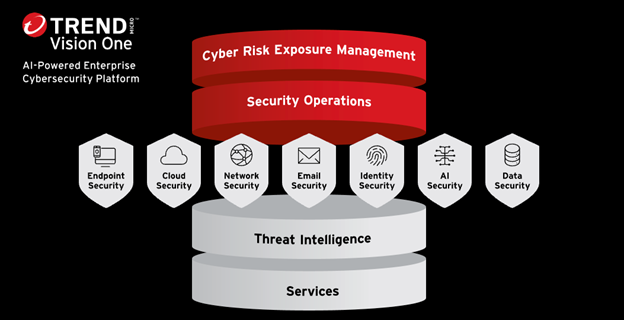
While many organizations are struggling with fragmented and complex environments, something transformative is emerging – The use of AI tools to protect your environment from threats. Trend Vision One™ is at the forefront of this evolution with a single platform of natively integrated security solutions and capabilities that others can only achieve through 3rd party APIs. This approach proves the next generation of security isn’t about managing more tools—but rather unlocking business potential through a truly unified view of risks powered by AI threat intelligence.
Protecting the Frontier of Artificial Intelligence
As companies rush to implement AI in their processes, a new category of risks has emerged that few are prepared to face. AI Application Security represents one of these critical new challenges, requiring specialized approaches that go far beyond traditional security measures. Consider this scenario: your company deploys an AI-powered chatbot for customer service. Without proper protection, an attacker could manipulate the model to leak confidential customer information through carefully crafted prompts. Or worse, poison the training data so the model makes decisions that harm the business.
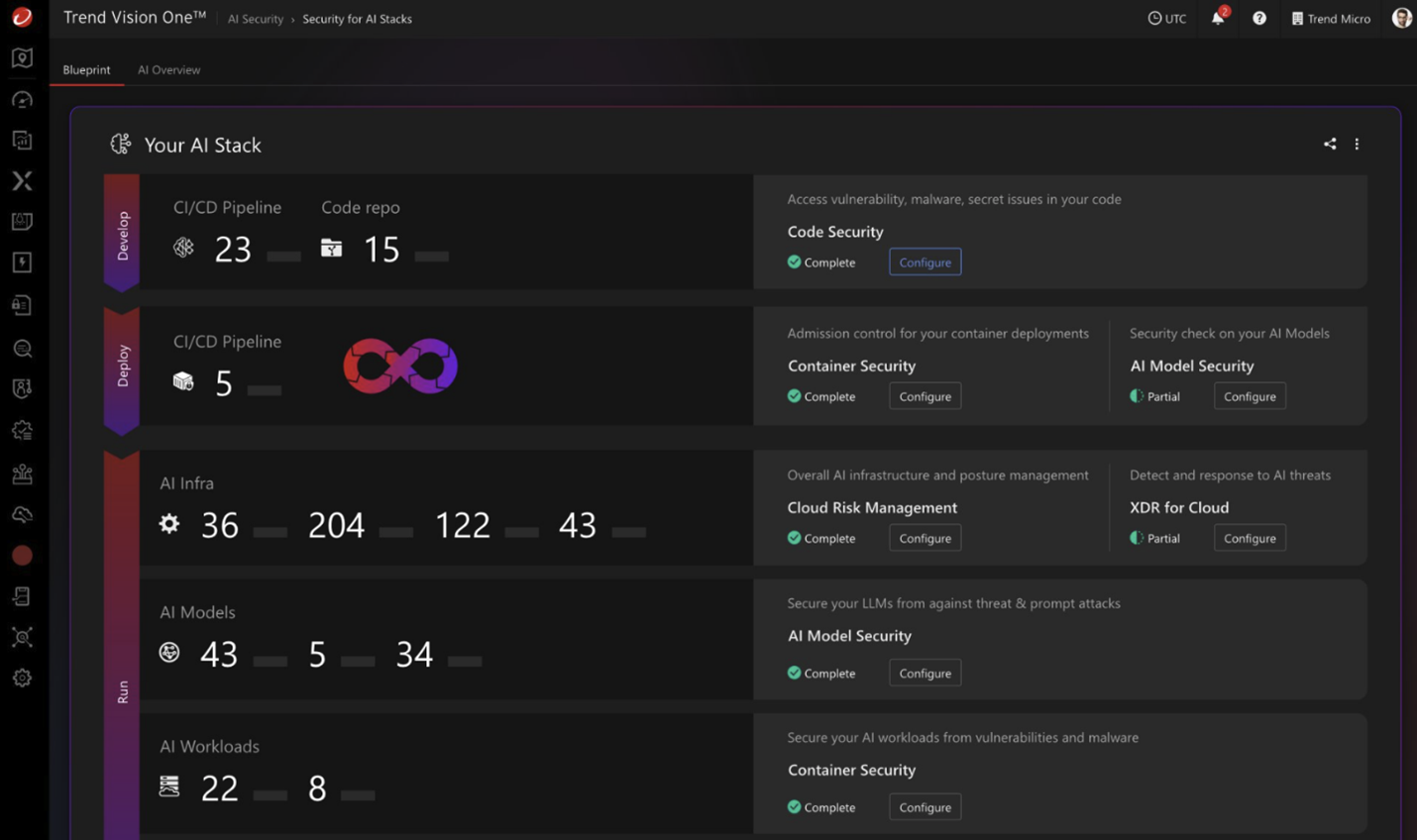
Modern “Security of AI Stack” solutions offer full visibility through specialized dashboards along with AI risk insights that reveal not only what’s happening, but the real impact on the business. Trend Vision One native integrations consolidate all of these capabilities into a single interface that eliminates the need to consult multiple systems to understand the full AI risk landscape—transforming what traditionally required expertise in multiple tools into a simplified, easy to use intuitive experience.
Breaking Down Silos Between Development and Security
Here’s where the real magic happens. The project view dashboard within Trend Vision One™ Cloud Risk Management is revolutionizing how teams collaborate. When it comes to visibility, this view focuses on providing contextual information about cloud risks by grouping resources into projects that reflect the business context. This allows teams to prioritize risks based on project criticality and ownership. For example, a high risk in a non-critical project (such as a static marketing website) may be less urgent than a medium risk in a business-critical project (such as a banking application that processes credit card data). In this scenario, the medium risk in the critical project should be prioritized, as it represents the greatest potential impact.
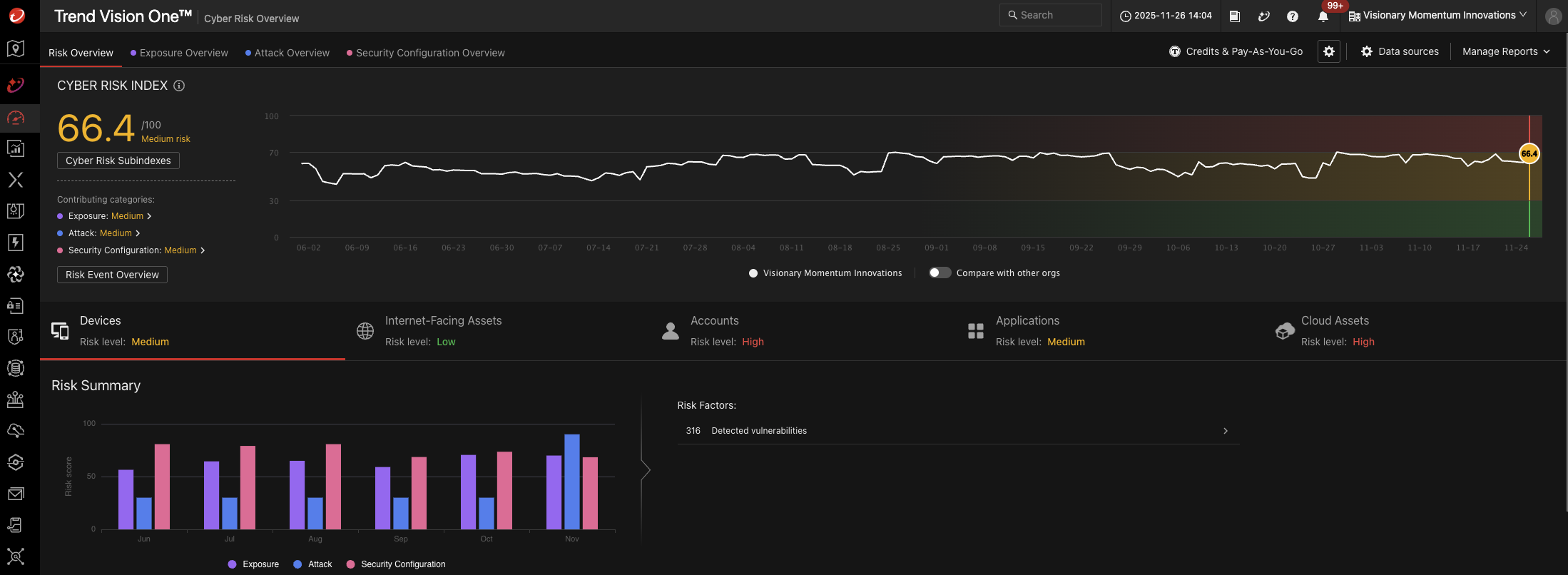
Security That Scales With Your Business
When Code Becomes the First Line of Defense
Modern code security goes far beyond simply scanning code for vulnerabilities. It's about creating an environment where security and development go hand in hand from the very first line of code.
Imagine a developer working on a new feature. As they write code, they receive intelligent suggestions not only about performance and quality, but also about security implications. When a third-party library they're using is flagged with a new vulnerability, they're automatically notified with suggestions for secure alternatives .
But perhaps even more critical today is continuous monitoring of supply chain exposure. With recent incidents like the Shai-Hulud case demonstrating how supply chain attacks can compromise entire organizations , the ability to track and validate every software component has become essential. Modern solutions automatically map all dependencies, monitor suspicious changes in upstream repositories, and alert about compromised components before they reach the production environment., the ability to track and validate every software component has become essential. Modern solutions automatically map all dependencies, monitor suspicious changes in upstream repositories, and alert about compromised components before they reach the production environment.
Trend Vision One™Code Security offers comprehensive supply chain protection, automatically correlating code vulnerabilities with dependency exposures and providing complete visibility of the software bill of materials (SBOM) in real-time. This level of integration transforms security from a blocker into an accelerator. Issues are fixed when they cost pennies to fix—not thousands of dollars in production, or worse, when they compromise the organization's entire value chain.
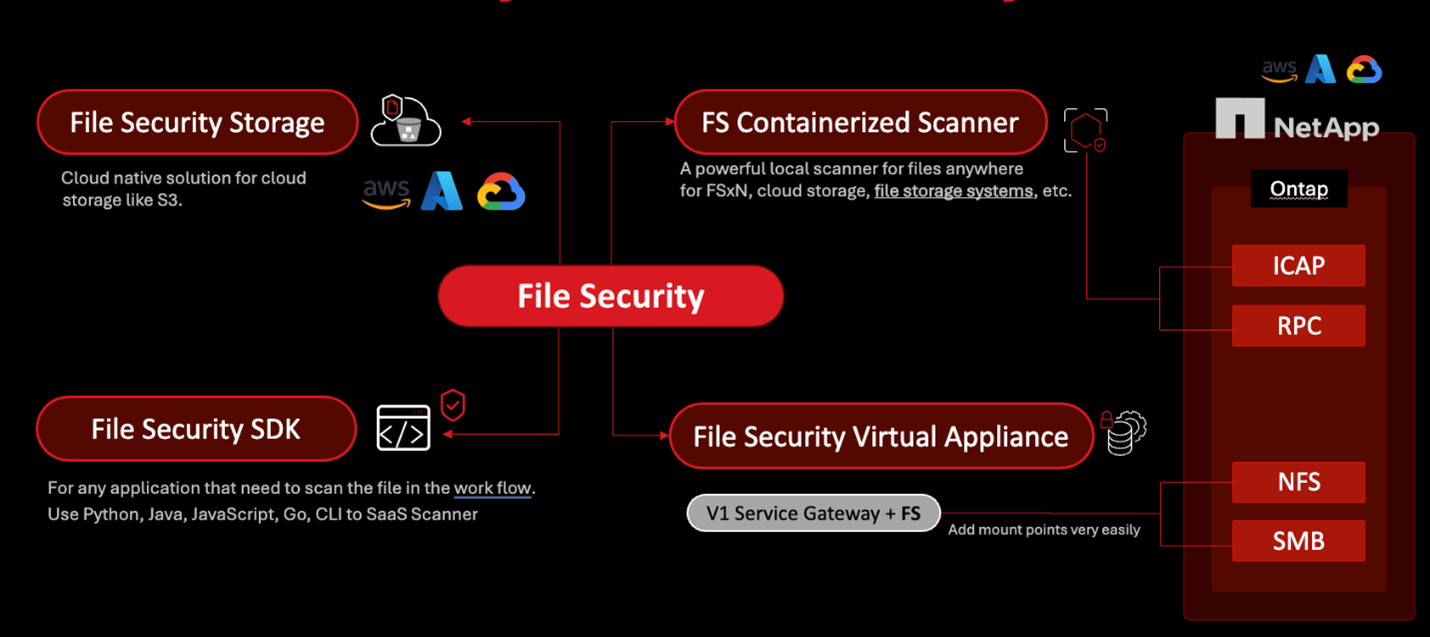
Automatically Scaling Data Protection from Malware
Support for NetApp Storage with Trend Vision One™ File Security – FSx for NetApp marks a leap forward in enterprise data protection. In hybrid environments, where critical data resides both on-premises and in the cloud, unified protection is not a luxury—it’s a necessity. Trend Vision One extends this protection through consistent policies that work regardless of data location. Customers can deploy malware scanning across both on-premises and cloud-based NetApp ONTAP file systems, eliminating protection gaps and simplifying compliance. This ensures that critical data remains secure—no matter where it resides.
With this integrated approach, organizations can confidently adopt modern storage technologies like ONTAP, knowing that data protection scales automatically alongside their infrastructure. This empowers business growth and innovation without compromising security.
File Security centralizes threat detection across all file systems, including ONTAP and cloud storage platforms such as Amazon S3, providing unified visibility and control.
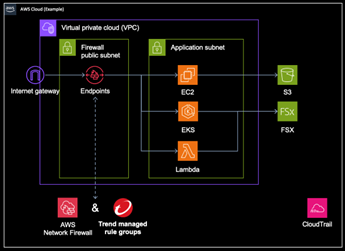
The integration of Trend Vision One™ Cloud IPS with AWS Firewall goes beyond technical protection. It empowers organizations to participate in the rollout of new AWS services, ensuring they stay at the forefront of security while maintaining the agility to adopt emerging technologies.
AWS users can natively enable Trend-managed rule groups within their AWS Network Firewall—no additional deployment required. With just one click, they can instantly apply Trend Micro industry-leading IPS filters to their network firewall, streamlining advanced protection across their cloud infrastructure.
Container Security: Protecting the Invisible
Containers have completely changed how applications are developed and deployed—but they’ve also introduced new security blind spots. How do you monitor the integrity of something that exists for only a few minutes?
File Integrity Monitoring for Trend Vision One™ Container Security runtime capabilities solve this puzzle through continuous monitoring that works independently of the container’s lifecycle. It’s like having a smoke detector that still works even when you move houses.
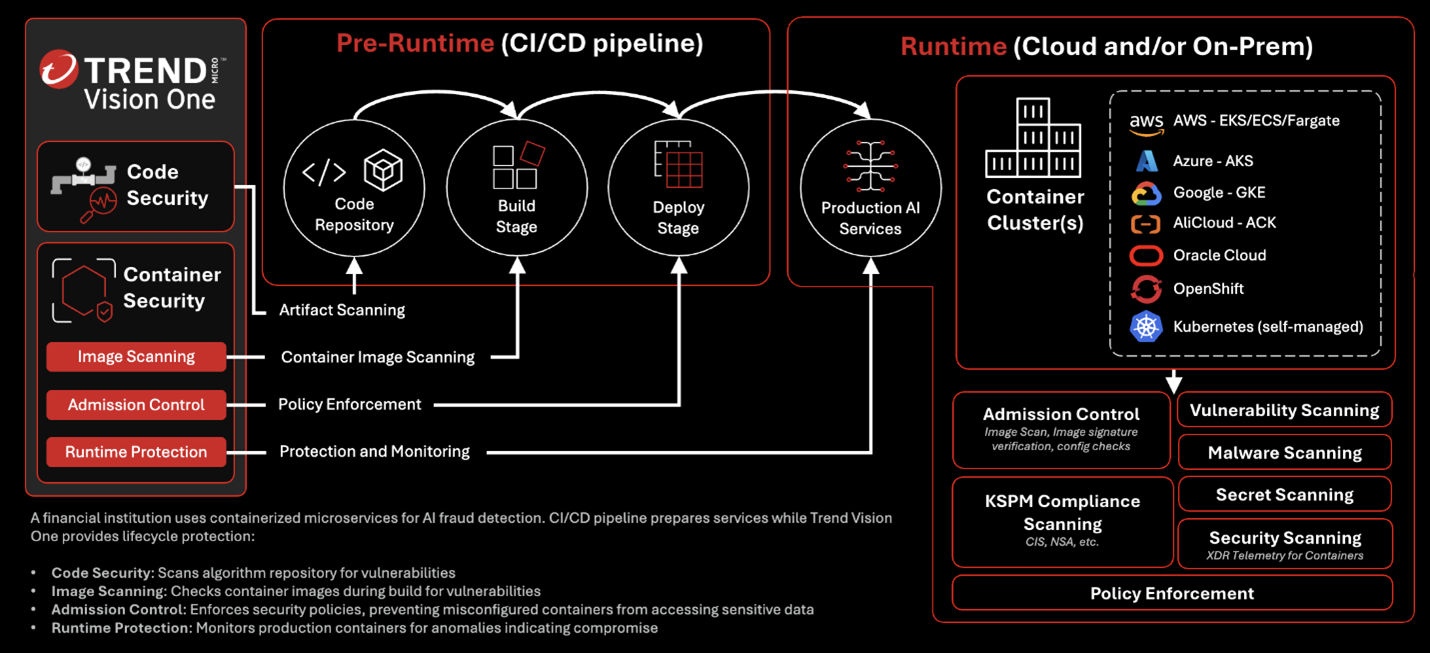
Threat intelligence sweeping for container telemetry goes a step further, correlating local events with global threat intelligence. When a new indicator of compromise is identified anywhere in the world, your containers are automatically scanned and protected. Trend Vision One centralizes this intelligence, ensuring that insights gained in any part of the infrastructure benefit the entire organization.
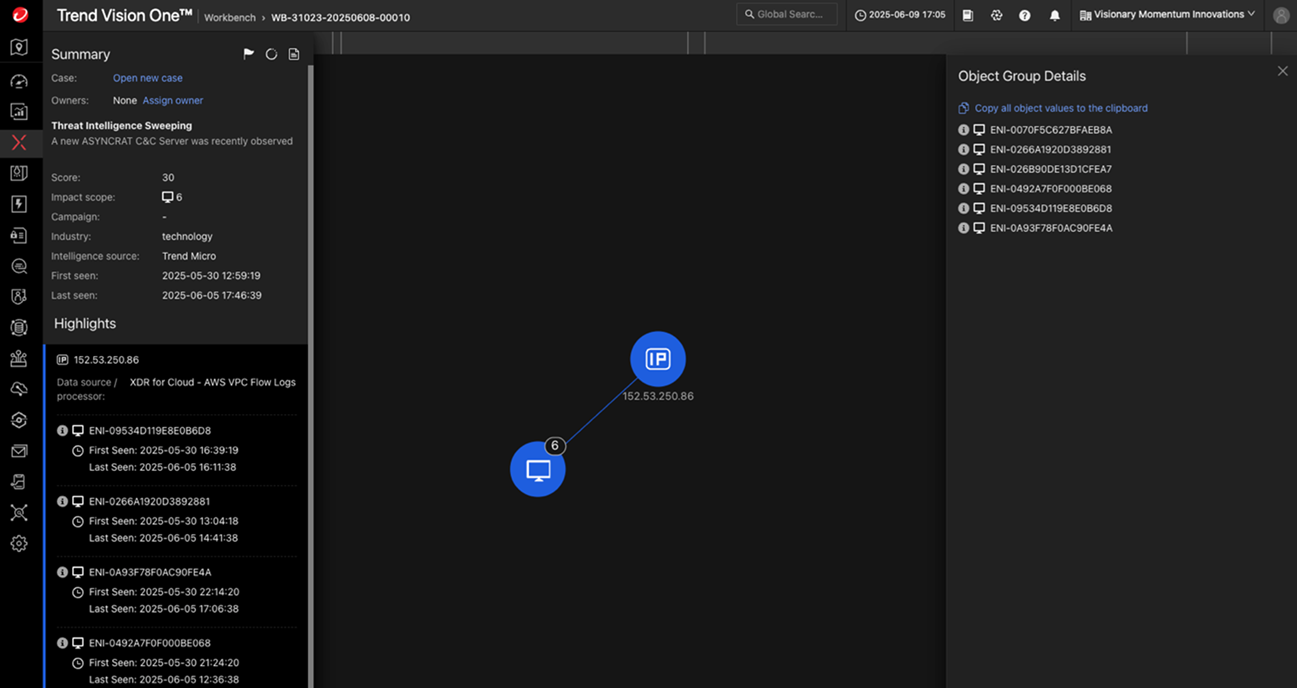
Leading with AI-Powered Rule Development
One of Vision One’s standout features is its best practice rules. Detect misconfigurations risks across 5 cloud providers with our comprehensive out of the box security checks in customers’ cloud environments, risks that can leave them exposed to cyberattacks like ransomware.
By integrating Amazon Bedrock’s generative AI, we’ve accelerated rule development by over 50%, transforming how we deliver security and compliance capabilities.
Bedrock enables intelligent automation throughout the rule-writing process, significantly reducing manual effort. This allows us to quickly implement customer-requested rules and expand coverage across AWS, Azure, Alibaba Cloud, OCI, and GCP.
Previously, creating a new rule required 3–4 days of work from developers and QA teams. Now, with Bedrock, the development cycle is down to just 1 day.
Each phase of this initiative is designed to minimize time spent on building, deploying, and testing rules. Our ultimate goal is to shift developer and QA involvement to oversight only, focusing on final code review.
Customer Impact
One of the largest insurance companies in APAC, running on GCP, can now safely scale and increase their use of AI and ML services to drive innovation, thanks to Trend’s consistent and comprehensive out-of-the-box rules coverage.
The Future of Detection: A SIEM That Thinks
Artificial Intelligence That Truly Understands Context
Threat detection models using Amazon Bedrock represent a fundamental evolution in threat detection. Instead of relying on static rules that quickly become outdated, these models use natural language to understand the full context of security events.
It’s the difference between a system that alerts you “there were 100 failed login attempts” and one that says “we’ve detected a coordinated attack pattern targeting administrative accounts, similar to the APT29 campaign identified last week, with an 87% probability of being a real attack based on timing and origin of attempts.”
Agentic SIEM with AWS: AI-native cloud detection and response combining real-time observability, IOC sweeping with threat intelligence, and automated security playbooks. Delivers rapid onboarding of new cloud application logs, meaning they are parsed, mapped, and correlated within hours, to accelerate investigation and response across your AWS environment.
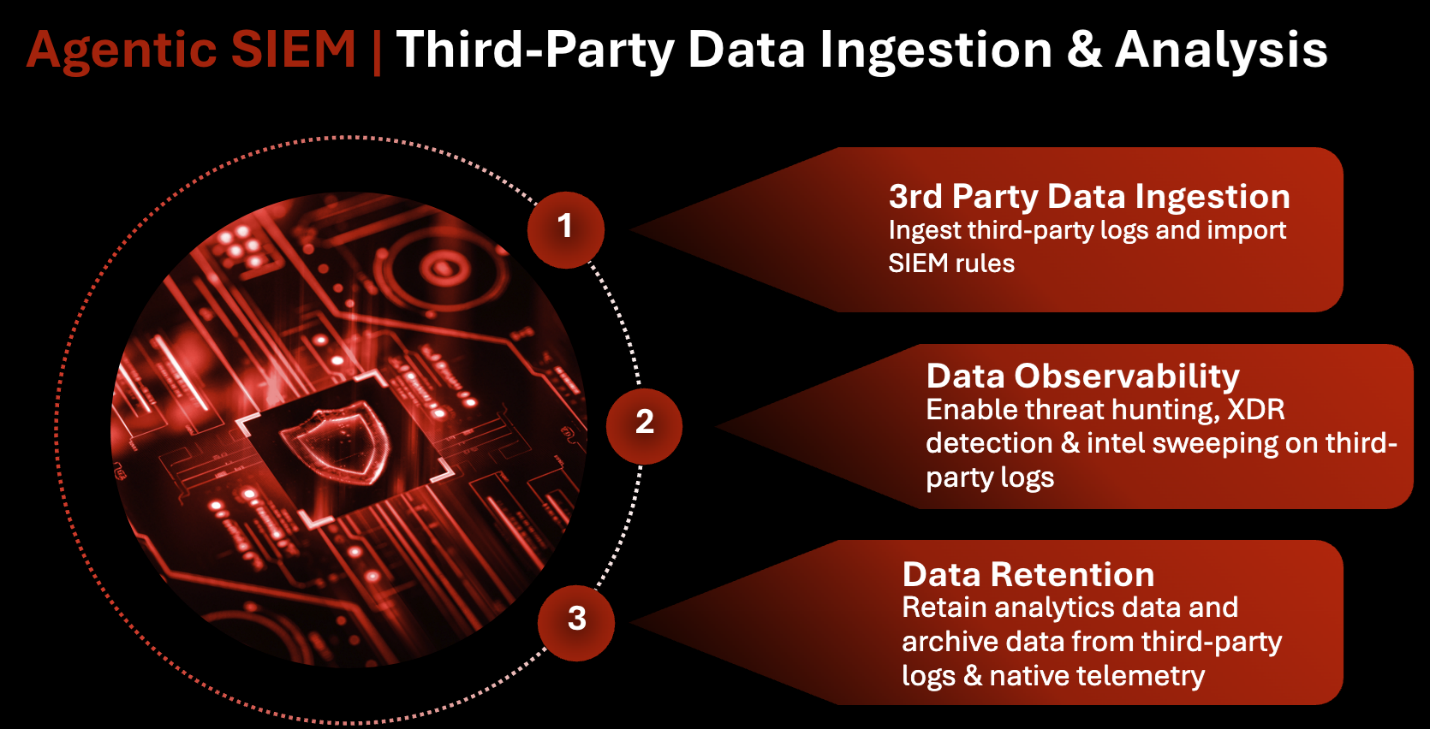
Real Business Impact
All these technologies are impressive, but what truly matters is their impact on organizational outcomes:
- Reduced Operational Costs: Smart automation transforms incident response economics. By automating initial evidence collection, event correlation, and context analysis, organizations allow senior analysts to focus on strategic decisions instead of repetitive manual work.
- Accelerated Projects: When security is integrated into development through a single platform, approval bottlenecks disappear. Projects are delivered faster because security controls are applied automatically.
- Competitive Advantage: Organizations with advanced security can take calculated risks that competitors cannot. They can innovate faster, enter new markets with confidence, and build products their customers trust.
Where to Start?
Security transformation doesn’t happen overnight—but it doesn’t require a full overhaul either. The most successful organizations start with a specific area—perhaps code security to improve collaboration between development and security, or AI application security to protect their AI initiatives.
What matters most is starting with a different mindset: security isn’t a hurdle to overcome, but a capability to develop. It’s the difference between seeing security as a cost center and seeing it as a competitive differentiator. Trend Vision One acts as the catalyst for this transformation, providing a solid foundation for future growth without adding new complexity—allowing organizations to evolve their security posture without compromising operational agility.
The question isn’t whether your organization will need to evolve its security strategy—it’s whether it will lead that transformation or be forced to follow it.
The future of enterprise security is being written now. And for the first time in a long time, that future looks brighter and more promising than the present.

