PUA.Win32.Mindspark.AA
Win32/Toolbar.MyWebSearch.BA potentially unwanted (ESET-NOD32); Generic PUA DN (PUA) (Sophos AV)
Windows


Threat Type: Potentially Unwanted Application
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Potentially Unwanted Application arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It connects to certain websites to send and receive information.
TECHNICAL DETAILS
Arrival Details
This Potentially Unwanted Application arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Potentially Unwanted Application drops the following files:
- %User Temp%\ns{random characters}.tmp\nsDialogs.dll
- %User Temp%\ns{random characters}.tmp\System.dll
- %User Temp%\ns{random characters}.tmp\TransitSimplified_msi_bg-copy_1501785279667.bmp
- %User Temp%\ns{random characters}.tmp\reporting
- %User Temp%\ns{random characters}.tmp\cancel_blue_1473358017200.bmp
- %User Temp%\ns{random characters}.tmp\Install_ENG_1435680405923.bmp
- %User Temp%\ns{random characters}.tmp\reporting
- %User Temp%\ns{random characters}.tmp\installerParams
- %User Temp%\ns{random characters}.tmp\reporting
- %User Temp%\ns{random characters}.tmp\TransitSimplified_msi_bg-copy_1501785292781.bmp
- %User Temp%\ns{random characters}.tmp\reporting
- %AppDataLocal%\TransitSimplifiedTooltab\TooltabExtension.dll
- %User Temp%\ns{random characters}.tmp\reporting
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %AppDataLocal% is the Local Application Data folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Application Data on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
Other System Modifications
This Potentially Unwanted Application adds the following registry entries:
HKEY_CURRENT_URSER\Software\TransitSimplified
Start Page = "http://hp.{BLOCKED}y.com/transitsimplified/ttab02/index.html?n=78497636&p2=^BYP^mni000^TTAB02&ptb=2DA31C30-F19F-4223-A7D9-0AE5A043F453&coid=6357f541372247b29de80313cf5c2932"
HKEY_CURRENT_URSER\Software\TransitSimplified
UnInstallSurveyUrl = "http://@{downloadDomain}.dl.{BLOCKED}y.com/uninstall.jhtml?surveyUrl=http%3A%2F%2Fwww.research.net%2Fr%2FHYSCVNM%3Fc%3D2DA31C30-F19F-4223-A7D9-0AE5A043F453%26ptb%3D^BYP^mni000^TTAB02"
Other Details
This Potentially Unwanted Application connects to the following website to send and receive information:
- http://dp.tb.{BLOCKED}k.com:443
- http://apps.{BLOCKED}ust.com/roots/dstrootcax3.p7c
- http://anx.{BLOCKED}ark.com/anx.gif?anxa=CAPDownloadProcess&anxe=Error&errorCode=-16&errorType=nsisError&errorDetails=&platform=vicinio&anxv=2.7.1.3000&anxd=2018-05-18&coid=&refPartner=^BYP^mni000^TTAB02&refSub=&anxl=en-US&anxr=-2006788705&refCobrand=BYP&refCampaign=mni000&refTrack=TTAB02&refCountry=
- http://anx.{BLOCKED}ark.com/anx.gif?anxa=CAPDownloadProcess&anxe=Error&errorCode=-8&errorType=nsisError&errorDetails=3d49db2ecb4855112017327f46b76b184cb4a3d6%2Eexe&platform=vicinio&anxv=2.7.1.3000&anxd=2018-05-18&coid=6357f541372247b29de80313cf5c2932&refPartner=^BYP^mni000^TTAB02&refSub=&anxl=en-US&anxr=2104981669&refCobrand=BYP&refCampaign=mni000&refTrack=TTAB02&refCountry=
It does the following:
- It displays the following during installation:
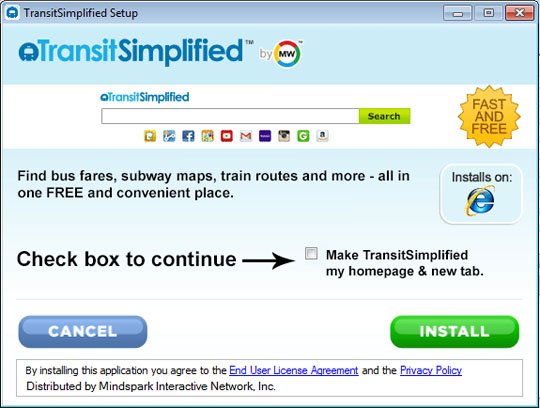
SOLUTION
Step 1
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 2
Remove PUA.Win32.Mindspark.AA by using its own Uninstall option
Step 3
Scan your computer with your Trend Micro product to delete files detected as PUA.Win32.Mindspark.AA. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Did this description help? Tell us how we did.

