PE_SALITY
Windows 2000, Windows XP, Windows Server 2003


Threat Type: File infector
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
A family of file infectors known to spread by infecting .EXE and .SCR files, SALITY malware also spreads via removable drives and network shares.
When infecting target files, SALITY follows certain rules such as avoiding files located in certain folders or avoiding files with certain strings in file names. It also avoids infecting files that have file names with more than 250 characters.
SALITY malware modifies the affected computer's HOSTS files to prevent access to certain websites. SALITY variants are also found to terminate antivirus-related processes.
SALITY connects to particular URLs and IPs to download its components.
TECHNICAL DETAILS
Installation
This file infector drops the following files:
- %System%\vcmgcd32.dll
- %System%\vcmgcd32.dl_
- {drive letter}:\ autorun.inf
- %System%\drivers\{random file name}.sys
(Note: %System% is the Windows system folder, which is usually C:\Windows\System32.)
It drops the following copies of itself into the affected system:
- {drive letter}:\{random}.exe/cmd/pif
- {drive letter}:\{malware file name}.exe
Other System Modifications
This file infector adds the following registry keys:
HKEY_CURRENT_USER\Software\{random}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Tracing\FWCFG
It adds the following registry entries:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Internet Settings
GlobalUserOffline = "0"
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
system
DisableRegistryTools = "1"
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
system
DisableTaskMgr = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
AntiVirusDisableNotify = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
AntiVirusOverride = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
FirewallDisableNotify = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
FirewallOverride = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
UacDisableNotify = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
UpdatesDisableNotify = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\policies\
system
EnableLUA = "0"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSetServices\
SharedAccess\ParametersFirewallPolicy\StandardProfile
DisableNotifications = "1"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSetServices\
SharedAccess\ParametersFirewallPolicy\StandardProfile
DoNotAllowExceptions = "0"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSetServices\
SharedAccess\ParametersFirewallPolicy\StandardProfile
EnableFirewall = "0"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\SharedAccess\Parameters\
FirewallPolicy\DomainProfile\AuthorizedApplications\
List
{malware path and name} = "{malware path and name}:*:Enabled:{infected file name}"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\SharedAccess\Parameters\
FirewallPolicy\StandardProfile
DisableNotifications = "1"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\SharedAccess\Parameters\
FirewallPolicy\StandardProfile
DoNotAllowExceptions = "0"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\SharedAccess\Parameters\
FirewallPolicy\StandardProfile
EnableFirewall = "0"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\SharedAccess\Parameters\
FirewallPolicy\StandardProfile\AuthorizedApplications\
List
{malware path and name} = "{malware path and name}:*:Enabled:ipsec"
HKEY_LOCAL_MACHINE\System\CurrentControlSet\
Services\{random}
DisplayName = "{random}"
HKEY_LOCAL_MACHINE\System\CurrentControlSet\
Services\{random}
ErrorControl = "1"
HKEY_LOCAL_MACHINE\System\CurrentControlSet\
Services\{random}
ImagePath = "\??\%System%\drivers\{random file name}.sys"
HKEY_LOCAL_MACHINE\System\CurrentControlSet\
Services\{random}
Start = "3"
HKEY_LOCAL_MACHINE\System\CurrentControlSet\
Services\{random}
Type = "1"
It modifies the following registry key(s)/entry(ies) as part of its installation routine:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
Advanced
Hidden = "2"
(Note: The default value data of the said registry entry is 1.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\SharedAccess
Start = "4"
(Note: The default value data of the said registry entry is 2.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
UpdatesDisableNotify = "1"
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
AntiVirusOverride = "1"
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
AntiVirusDisableNotify = "1"
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
FirewallDisableNotify = "1"
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
FirewallOverride = "1"
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
UacDisableNotify = "1"
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\wscsvc
Start = "4"
(Note: The default value data of the said registry entry is 2.)
It deletes the following registry keys:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\
Control\SafeBoot\Minimal
HKEY_LOCAL_MACHINE\System\CurrentControlSet\
Control\SafeBoot\Network
Other Details
This file infector connects to the following possibly malicious URL:
- http://{BLOCKED}.{BLOCKED}.19.14/logo.gif
- http://{BLOCKED}.{BLOCKED}.222.206/logos.gif
- http://{BLOCKED}metgrup.com/images/logosa.gif
- http://{BLOCKED}.{BLOCKED}.213.217/images/?{random}
- http://{BLOCKED}overseas.net/images/xs2.jpg
- http://{BLOCKED}o.cz/logo.gif
- http://{BLOCKED}in.com.tr/images/logos.gif
- http://{BLOCKED}ye.net/xs.jpg
- http://{BLOCKED}hotel.com/images/logof.gif
- http://{BLOCKED}ry.org/images/xs.jpg
- http://{BLOCKED}lim.com.tr/images/xs2.jpg
- http://{BLOCKED}x.com/xs.jpg
- http://{BLOCKED}pie.in/images/xs.jpg
- http://{BLOCKED}l.net/images/xs.jpg
- http://{BLOCKED}mediaproduction.com/images/xs.jpg
- http://{BLOCKED}e.co.uk/images/xs.jpg
- http://{BLOCKED}t.com.tr/main.gif
- http://cdn.{BLOCKED}a.com/images/image_redirect/shopwiki.com.gif
- http://cdn.{BLOCKED}a.com/images/image_redirect/shopwiki.com.jpg
- http://{BLOCKED}asa.com/images/logos.gif
- http://{BLOCKED}tara.com/logof.gif
- http://{BLOCKED}tingdestinations.com/?f
- http://{BLOCKED}tingdestinations.com/images/logos.gif
- http://{BLOCKED}so.com.br/s.jpg
- http://{BLOCKED}scapeuk.com/xs.jpg
- http://{BLOCKED}nt-eg.com/images/logosa.gif
- http://{BLOCKED}ix.us/images/mainf.gif
- http://{BLOCKED}ny.com/logos.gif
- http://{BLOCKED}oletarianparty.org/logof.gif
- http://g2.{BLOCKED}itech.com/xs.jpg
- http://{BLOCKED}rtltd.com/img/xs.jpg
- http://{BLOCKED}wing-tomorrow.org/images/s.jpg
- http://{BLOCKED}nia.my1.ru/mainh.gif
- http://{BLOCKED}rnajd.com/images/logo.gif
- http://{BLOCKED}n-ferienhaus.com/logos.gif
- http://{BLOCKED}hnes-server.de/cms/images/main.gif
- http://{BLOCKED}m.de/images/main.gif
- http://{BLOCKED}wel.fm.interia.pl/logos.gif
- http://{BLOCKED}sh.com/images/mainf.gif
- http://radio.{BLOCKED}b.ir/farhang/images/logos.gif
- http://{BLOCKED}ie.com/images/logos.gif
- http://{BLOCKED}tu.funpic.de/img/logos.gif
- http://v11.{BLOCKED}abschirmkiste.de/foo?ip=120.89.55.2&port=3846&req=/logos.gif
- http://www.{BLOCKED}becreatives.com/logos.gif
- http://www.{BLOCKED}desk.org/images/xs.jpg
- http://www.{BLOCKED}ogullari.com/logof.gif
- http://www.{BLOCKED}zanbil.com/Images/logos.gif
- http://www.{BLOCKED}ccorini.com/images/logos.gif
- http://www.{BLOCKED}kkk4d.info/mrow_china/?id{random characters}
- http://www.{BLOCKED}vns3sdsal.info/mrow_china/?id{random characters}
- http://www.{BLOCKED}k.info/mrow_china/?id{random characters}
- http://www.{BLOCKED}ine.com/s.jpg
- http://www.{BLOCKED}-adv.com/gallery/Fusion/images/logos.gif
- http://www.{BLOCKED}yservices.be/images/logos.gif
- http://{BLOCKED}uncil.ya.funpic.de/images/logos.gif
- http://{BLOCKED}tt.yo.funpic.de/logos.gif
- http://{BLOCKED}avdar.blogspot.com/logos_s.gif
- http://{BLOCKED}avdar.com/logos_s.gif
- http://{BLOCKED}kalpilkogretim72.meb.k12.tr/images/logos.gif
NOTES:
This malware has the capability to damage files.
SOLUTION
NOTES:
Trend Micro OfficeScan 10 users are also urged to use the following features to protect from PE_SALITY malware:
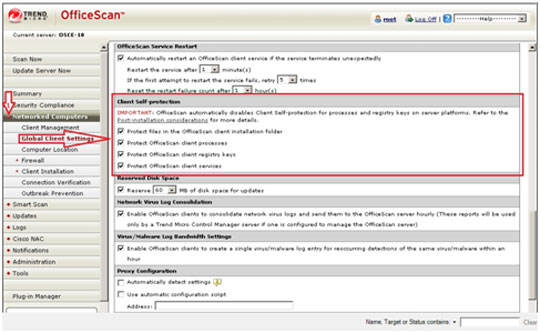
Enabling the Self-protection Feature
- Open the OfficeScan 10 Web console.
- In the left panel, click Networked Computers to expand its list of contents.
- Click Global Client Settings to open the user interface found in the right panel.
- In the right panel, locate Client Self-Protection and tick your preferred options in the list to ensure and enable self-protection against malware that can disable the software.
- At the bottom of the right panel, click Save
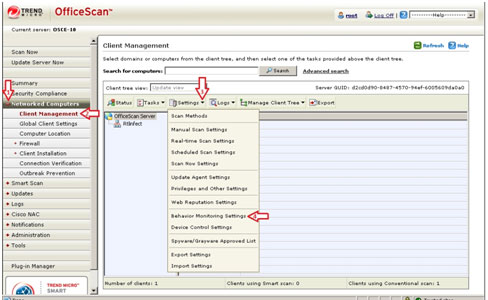
Enabling the Behavioral Monitoring Module
- Still in the OfficeScan 10 web console, in the left panel, click Networked Computers to expand its list of contents.
- Click Client Management to open the user interface on the right panel.
- In the right panel, click Settings. Choose Behavioral Monitoring Settings from the dropdown list.
- In the new window, configure the program's behavioral monitoring settings.
- Click Enable Malware Behavior Blocking.
- Click Enable Event Monitoring and set your policies and desired actions.
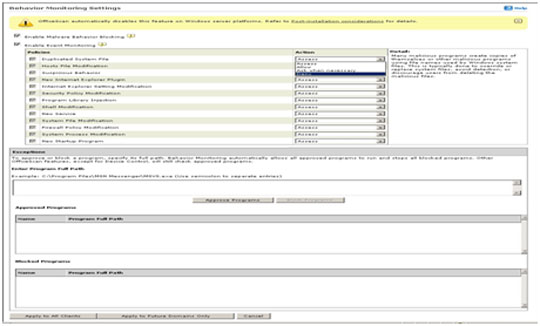
- At the bottom of the window, click Apply to All Clients.
Enabling the Device Access Control (DAC) Feature
- Still in the OfficeScan 10 Web console, in the left panel, click Networked Computers to expand its list of contents.
- Click Client Management to open user interface on the right panel.
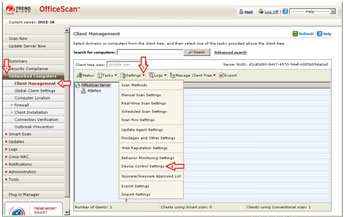
- In the right panel, click Settings and choose Device Control Settings from the dropdown list. This opens a new window where you can configure the program's behavioral monitoring settings.
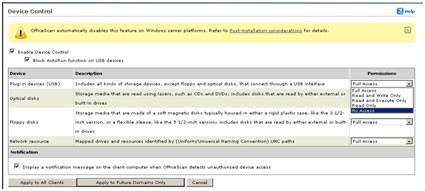
- Click Enable Device Control then Block Autorun function on USB devices after setting your desired permissions.
- At the bottom of the window, click Apply to All Clients.
Enabling Scan Network Drive
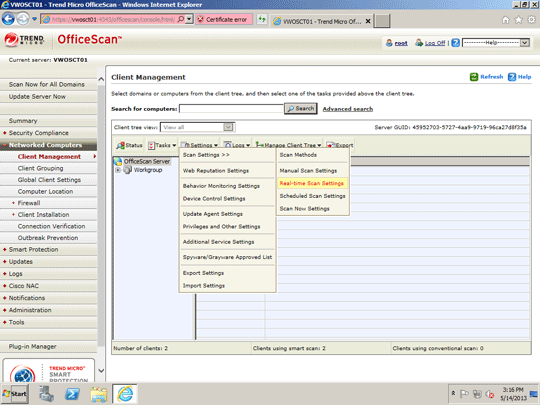
- Still in the OfficeScan 10 Web console, in the left panel, click Networked Computers to expand its list of contents.
- Click Client Management to open user interface on the right panel.
- In the right panel, click Settings and select Scan Settings>Real-Time Scan Settings.
- Click All scannable files and Scan network drive.
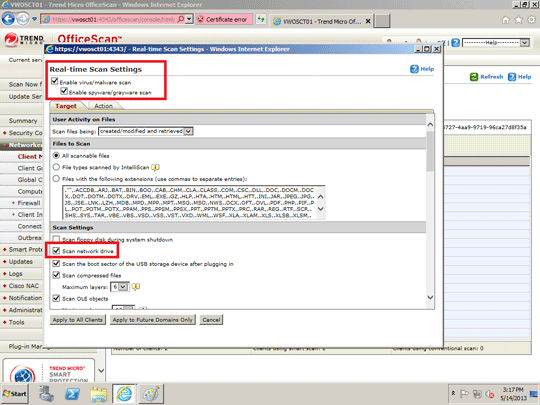
- At the bottom of the window, click Save.
Did this description help? Tell us how we did.


