Unveiling the Hidden Risks of Industrial Automation Programming
 Download Rogue Automation: Vulnerable and Malicious Code in Industrial Programming
Download Rogue Automation: Vulnerable and Malicious Code in Industrial Programming
Robots and other programmable industrial machines are the backbone of the manufacturing industry. Without them, the large-scale and fast-paced production that our modern economy depends on would simply be impossible. Critical sectors — from automotive and avionics to pharmaceuticals and food production — are reliant on these machines for the precise and efficient actions that they are capable of.
However, as much as modern manufacturing is dependent on them, these machines themselves rely on legacy technology designed decades ago. Although created in the relatively distant past, the technology that drives them is still very much in use today. Their various makers also built custom, proprietary programming languages and unique ecosystems for their respective machines. As we discuss in our research paper “Rogue Automation: Vulnerable and Malicious Code in Industrial Programming,” these conditions mean that these machines could harbor vulnerabilities that knowledgeable attackers could exploit to perform malicious actions and stay persistent within a smart factory.
Legacy technology
vs. smart factory
Programmable industrial machines are used for sophisticated automation routines in smart factories across the globe. They are programmed for specific repetitive tasks, such as picking and placing items, moving loads, soldering, and cutting.
The technology that drives these machines is very different from, say, the better-known technology used to create websites or mobile applications. Control process engineers and system integrators develop automation task programs that define the machines’ actions using vendor-specific programming languages.
We examined eight leading industrial robot vendors and found security-sensitive features in their programming environments. We describe how these features could lead to vulnerabilities or be abused by malicious actors to create new strains of self-propagating malware that traditional scanners wouldn’t be able to detect.
These issues are difficult to resolve because they are inherent to the design of the machines and legacy programming environments cannot be easily replaced.
Unfortunately, failure to address these security flaws could have costly and damaging consequences. An attacker could exploit them for surveillance and reconnaissance, remaining silently persistent within a smart factory. Or the attacker could act more aggressively, altering the quality of the products, halting the manufacturing line, or even exfiltrating valuable intellectual property.
But the attacker would need to possess significant resources and intimate knowledge of the working environment of the target. Only advanced, state-level attackers could attempt hacks of this nature.
Attacks
and consequences
We look at several cases to illustrate attacks that could arise from the exploitation of the vulnerabilities we discovered in our research, and their corresponding consequences.

From a Robot
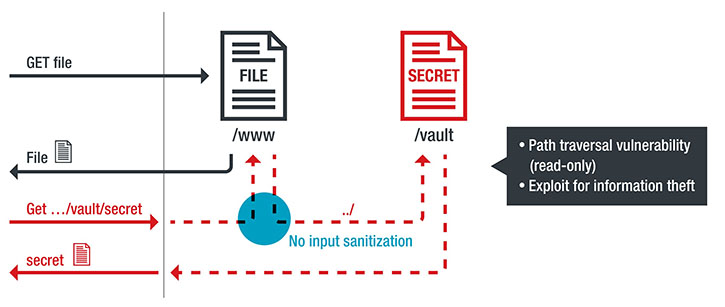
A path traversal vulnerability or a task program with an unsanitized network data flow could allow an attacker to exfiltrate the log file that records the target robot’s movements, which likely contains sensitive information such as intellectual property (for example, how a product is built). The attacker could then access other files in other directories (including files containing authentication secrets) and use them to finally access the machine’s console. We found one such vulnerability in 2019. We reported it to the vendor, and the issue was resolved.
An example of vulnerable automation logic: from unsanitized (e.g., file, network, serial) data to read/write file access

“Motion server” automation programs drive connected robots. An attacker could exploit a vulnerability in one of these programs and move a robot by spoofing network packets. In the example we found in ROS-Industrial, a leading open-source project written for all major industrial robots, this type of manipulation could happen if the safety system is not properly configured. With safety systems correctly configured and deployed, the attacker would have a hard time causing damaging movements, although the attacker could still cause small unintended movements and interrupt the production process.
The impact of the vulnerability when the safety system is not correctly configured: the “hand” of a robot, aka the end effector, in place (left) and the end effector after it fell off (right)
Trend Micro Research and Politecnico di Milano have been coordinating with ROS-Industrial to mitigate the security issue we found affecting ROS-Industrial drivers that control industrial robots. As a result, the ROS-Industrial Consortium released an instructional report to help users improve their security. The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) of the US Cybersecurity and Infrastructure Security Agency (CISA) has also released a report confirming the severity of our findings and acknowledging the suggested mitigation strategy.

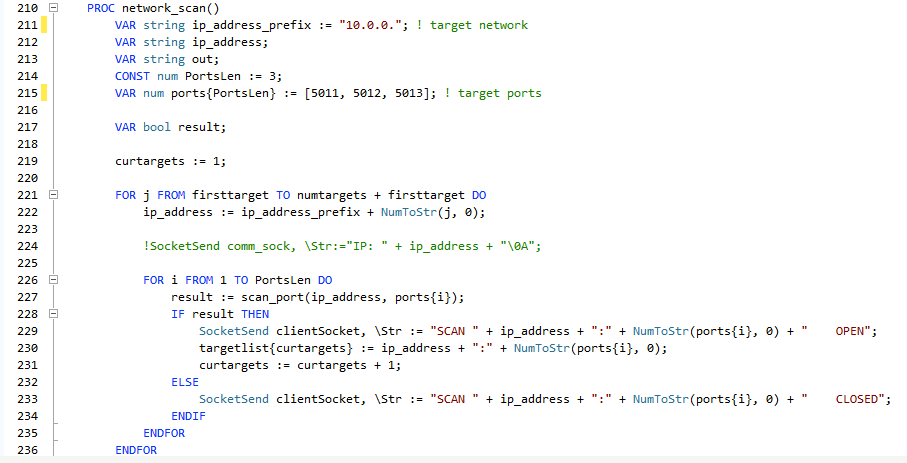
We found that legacy programming is so powerful that it enables the creation of targeted malware with wormlike behavior, capable of self-propagation at the logic level of automation platforms. Upon infecting a new robot, the worm would start scanning the network for other potential targets and exploit a network vulnerability to propagate. A more comprehensive piece of malware would also include a file-harvesting routine to exfiltrate any relevant data found on each infected target. We found most of the preconditions required for such self-propagating malware to spread in a demonstrator task program, partially vulnerable to remote code execution (that is, an attacker could invoke arbitrary functions already declared in the code).
The network-scanning routine of the proof-of-concept wormlike malware that we wrote
A Trend Micro researcher shows how an attacker could alter the automation script of a vulnerable robot and thus be able to control its movements.
Mitigation strategies
The issues raised in our research can be fully addressed only by long-term solutions, but there are also short- and medium-term mitigation strategies that control process engineers, system integrators, and original equipment manufacturers (OEMs) can adopt to enhance the security of industrial programming environments.
measures
-
Use network segmentation to isolate machines that need to process data coming from other networks.
-
Adopt network and endpoint protection to minimize the risk of vulnerability exploitation or malicious code infection.

-
Implement proper source code management processes, including automatic or periodic manual source code reviews.


measures
-
Develop security libraries (for example, cryptographic primitives) that will allow developers to easily implement input validation and authentication.

-
Provide a reference implementation of motion servers to allow machines to receive sanitized motion data in a high-level way.
-
Implement proactive patching of vulnerable task programs as a remedy for flaws found in periodic source code reviews.


measures
-
Ensure that future generations of programmable industrial machines will be secure by design, mainly by integrating security features into programming languages.

-
Implement fine-grained privilege separation with a permission system in the runtime on machines’ controllers.

-
Implement code signing to make certain that the code running on an industrial machine hasn’t been tampered with.

Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering



 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One