Ransomware Recap: Old Dogs Locky, SAMSAM, HiddenTear Learn New Tricks
On August 16, LG Electronics’ service centers were reportedly hit by WannaCry ransomware. The company shut down the affected self-service kiosks to mitigate the malware’s spread and shared threat intelligence to South Korea’s Internet and Security Agency. In late June, WannaCry also made its way down to Victoria, Australia, affecting traffic lights and speed cameras.
The previous weeks showed that old dogs Locky, SAMSAM/Samas, Cerber, HDDCryptor, and HiddenTear learned new tricks to attack businesses and end users.
Locky gets new variants, its large-scale spam campaign in progress
Security researchers uncovered several iterations of the notorious Locky ransomware (detected by Trend Micro as RANSOM_LOCKY family), with one variant, rebranded as IKARUSdilapidated, actively pushed by a widespread spam campaign. First spotted on August 9, the campaigns are powered by over 11,600 unique IP addresses from 133 countries, with more than 62,000 spammed messages sent in one day alone.
The spam emails contain a malicious Visual Basic script masquerading as either a Word document (.doc), archive (.zip), Portable Document Format (.pdf), or image file (.jpg, .tiff). When executed, it downloads and runs IKARUSdilapidated on the system. It uses typical social engineering lures: urging users to enable macros and obfuscating file attachments to evade detection. The ransom note demands a payment ranging between 0.5 and 1 bitcoin (US$2,145 to $4,290, as of August 18, 2017).
Several other Locky variants appeared in the previous weeks. A version that appends a .lukitus extension (which translates to “locking” in Finnish) to the files it encrypts employs a malicious JavaScript file, and demands a payment of 0.49 bitcoin ($2,102). Another Locky variety also surfaced last week, this time appending the encrypted files with .diablo6. Both iterations employ spam emails as infection vectors.
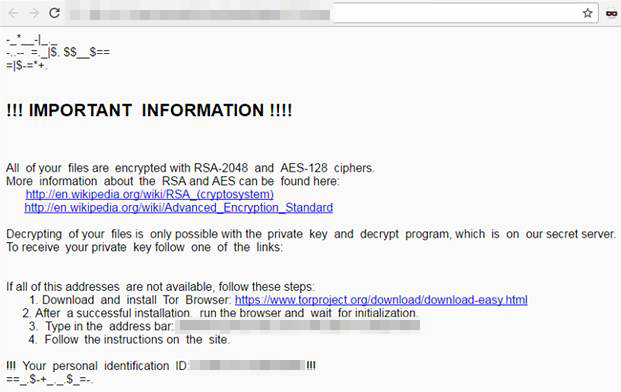
Ransom note of a Locky version that appends .diablo6 to encrypted files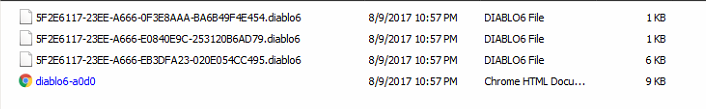
Sample encrypted files appended with .diablo6 extension
SAMSAM ransomware demands a ransom of up to $51,000
SAMSAM/SAMAS (RANSOM_SAMAS) made headlines in April 2016 when it hit healthcare and education sectors in the US. SAMSAM used a hacking tool to exploit vulnerabilities in servers running JBoss, an open-source application server that runs Java, and used worldwide by K-12 schools. The compromised server is then used as an entry point from which attackers can spread the ransomware to the machines.
Security researchers noted the recent spikes of SamSam distribution, but this time its operators seem to be more fastidious and can now check the scope of infection. If a single machine was infected, SAMSAM demands 1.7 BTC ($7,267). If more systems were taken hostage, the ransom goes up to 6 BTC ($25,650) to decrypt half of them. The ransom for getting all infected systems back online is 12 BTC, or $51,000. Last May, SamSam infected the computer systems of Erie County Medical Center in New York and demanded a $44,000 ransom, which the hospital refused to pay.
Magnitude exploit kit delivers Cerber
Cerber (RANSOM_CERBER) is one of the most prolific ransomware families. And given that it’s peddled as a service in the cybercriminal underground, it has no shortage in variety. A more recent version is now capable of further monetizing their operations by stealing from bitcoin wallets, for instance, along with credentials saved in Internet Explorer, Google Chrome, and Firefox.
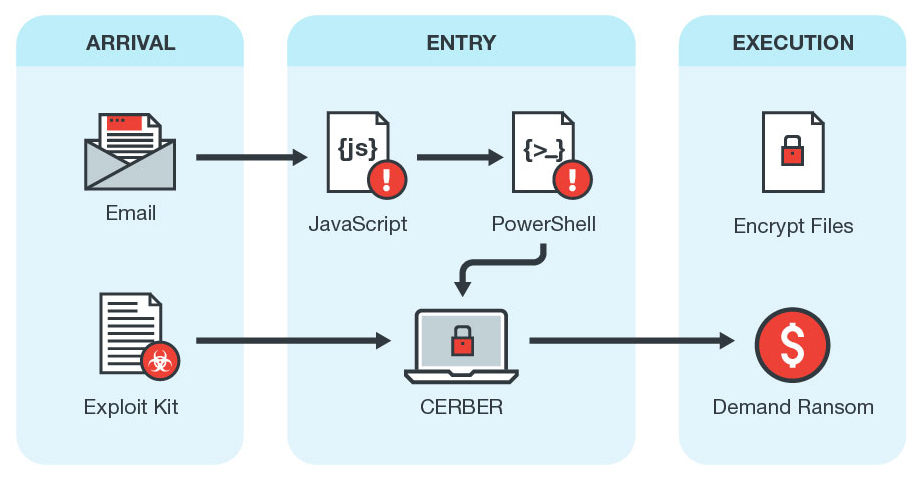
Attack chain of Cerber version 6
More recently, security researchers found that Cerber was actively delivered by the Magnitude exploit kit. Magnitude came to prominence last 2014 when its malvertisements made their way into Yahoo!’s advertising network, redirecting site visitors to a malicious domain hosting a cryptocurrency-mining malware. Magnitude is one of Cerber’s long-time partners in crime, leveraging security flaws in Adobe Flash Player as doorways into the system. Since the demise of Angler and the arrest of its operators, Magnitude—like other exploit kits—kept a low profile to avoid law enforcement. It has since become a private exploit kit used by a select group of cybercriminals. Magnitude was noted for its latest evasion and payload delivery technique: binary padding. This entails adding data to the payload to increase the file size beyond what detection technologies (i.e., static AV signatures) can handle and analyze.
Disk-encrypting HDDCryptor comes back
HDDCryptor (RANSOM_HDDCRYPTOR.AUSE), also known as Mamba, also reemerged in Brazil and Saudi Arabia. This time it misuses PsExec, a legitimate system administration utility, to hack into the targeted network shares and encrypt the files and hard disk.
It employs free and commercially available tools, particularly DiskCryptor, to lock the hard drive by overwriting the system’s Master Boot Record. When the machine reboots, it displays the ransom note instead of the login screen.
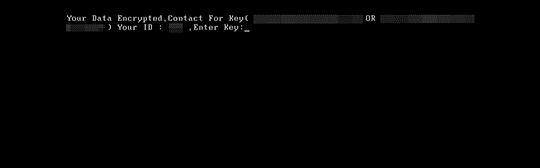
HDDCryptor’s ransom note
HDDCryptor drops various components needed to encrypt the local hard drive and file shares
This is a variant of the same ransomware family that scrambled the workstations of San Francisco Municipal Transportation Agency (SFMTA) and demanded a ransom of $73,000 in bitcoins. The agency had to open their turnstiles, offer train rides for free, and resort to handwriting bus routes—all to avoid disrupting San Francisco’s transportation system.
More HiddenTear spawns crop up
Two more ransomware variants were spotted in the wild, both of which were derived from the publicly disclosed source code of Hidden Tear: InfiniteTear (RANSOM_INFINITETEAR.A) and 3301 (RANSOM_HIDDENTEARTHREE.A).
InfiniteTear is capable of encrypting 444 file types, including databases, document files, and multimedia, and appends the infected files with a .JezRoz extension. It demands $320 in bitcoin, and gives an ultimatum of seven days before the decrypt key is deleted from their server.
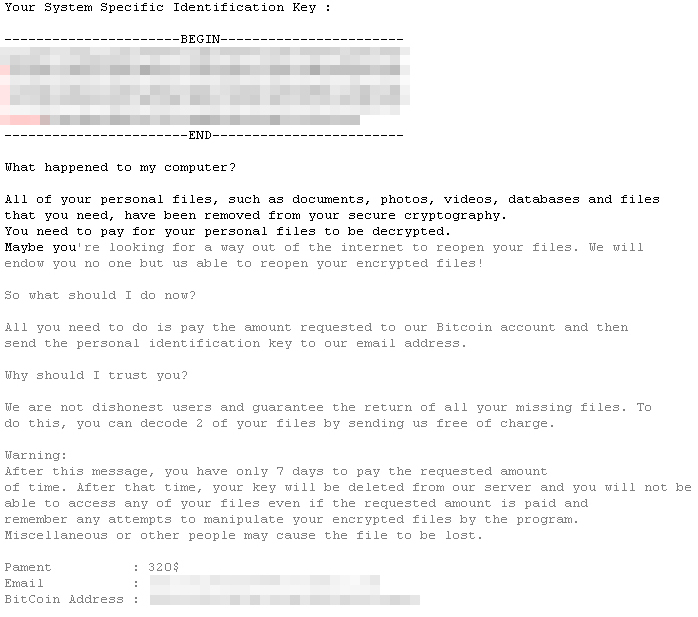
InfiniteTear's ransom note
3301 appends the encrypted file with the same extension name, and is capable of encrypting 2,783 file types. Its payment site is hosted in Tor’s hidden service. However, unlike other ransomware, victims had to first input their location and the 3301-generated victim ID to know the amount they had to pay. Victims are also given a week before the decryption key is deleted. The ransom note also sports seven other languages, which indicates that 3301 is distributed at least in countries that use those languages.
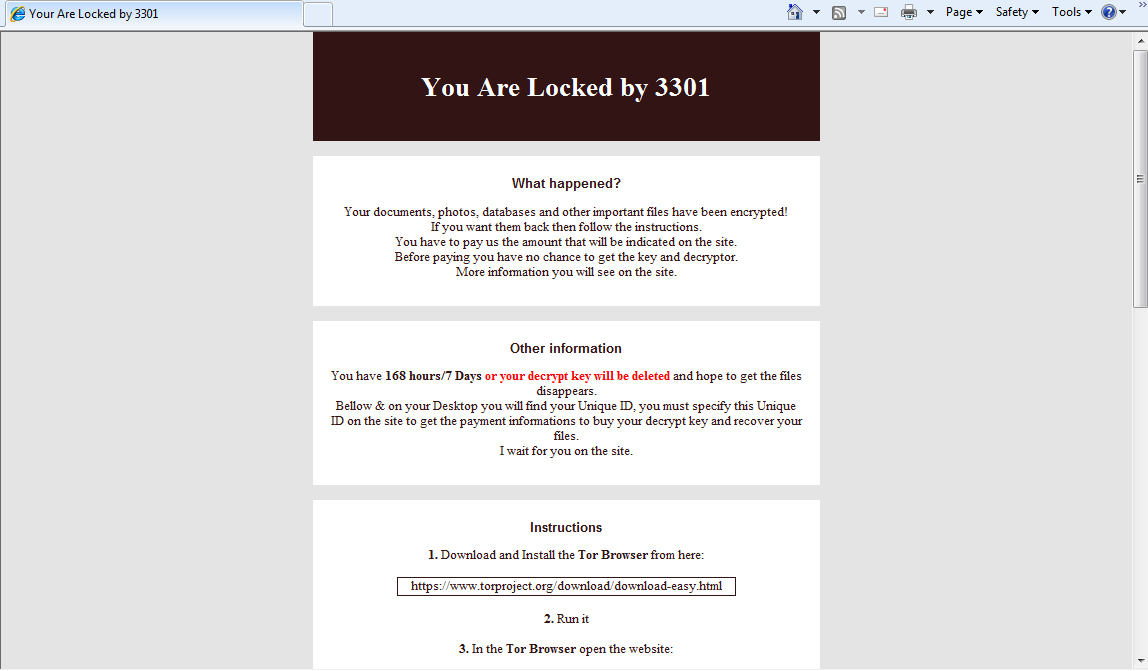
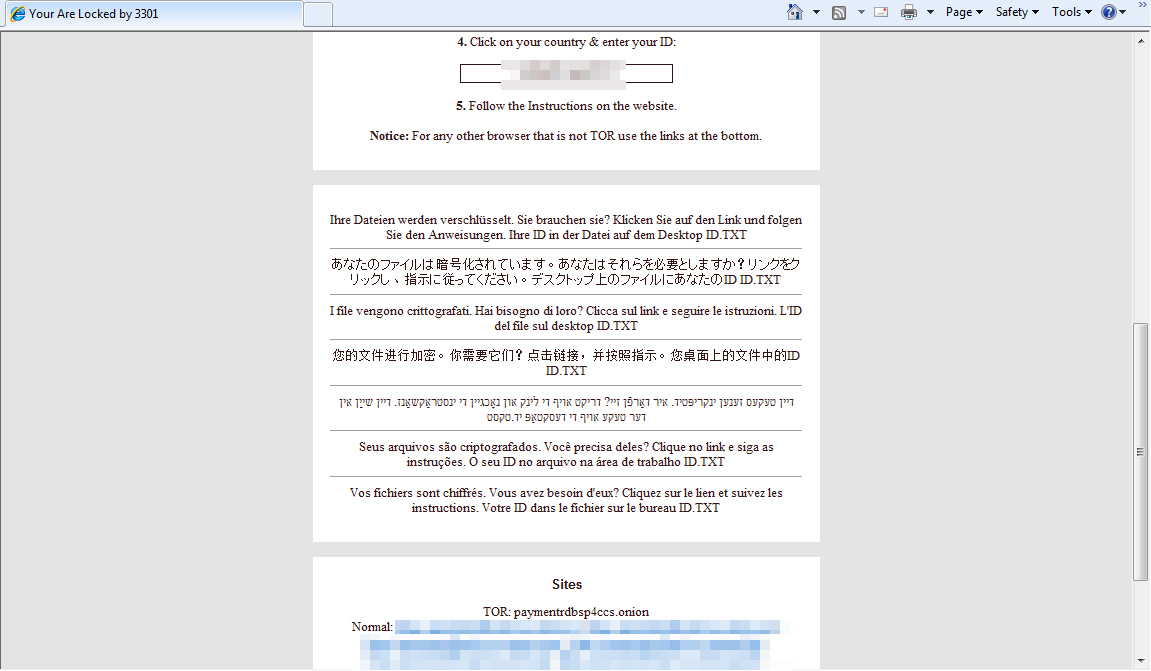
3301 ransomware's payment pages
The previous weeks’ ransomware made use of multifarious attack vectors, which makes a multilayered approach all the more significant. Follow best practices for defending against ransomware, and implement defense in depth in your cybersecurity—from the gateways, endpoints, networks, and servers.
Trend Micro Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by ransomware. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. At the endpoint level, Trend Micro™ Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimize the impact of this threat. Trend Micro™ Deep Discovery Inspector™ detects and blocks ransomware on networks, while Trend Micro™ Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro™ Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware. For home users, Trend Micro™ Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro™ Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One