Cybercriminals kick-off 2021 with sweepstakes, credit card, delivery scams
We predicted that this year, cybercriminals will continue to take advantage of Covid-19-related effects and incidents — such as people’s reliance on online purchases and e-services and the increased need for financial assistance — in order to bait victims and steal critical information. Even though new ways of stealing information regularly arise, tried-and-tested ones are still being actively utilized. We discuss the behaviors and external indicators of some phishing campaigns that we observed from the latter part of December 2020 to the first weeks of January 2021. These campaigns highlight the inclusion of fake online payment forms with the goal of stealing financial information more efficiently.
Sweepstakes scams
In one campaign, we saw how malicious actors lured victims with a fake sweepstakes giveaway (winneragent[.]com/usr/register). On the top part of the page, a countdown timer can be seen alongside a message claiming that because of “great media attention,” the sweepstakes queue will end after a certain number of hours. This aims to create a fake sense of urgency in potential victims.
The fake sweepstakes landing page also states that no purchase is necessary. However, it instructs victims to encode their personal information and card information on a fake form to get “unlimited downloadable access to 100,000 e-books.” Interestingly, the initial amount of US$19.99 is different from the supposed monthly renewal fee of US$39.99.
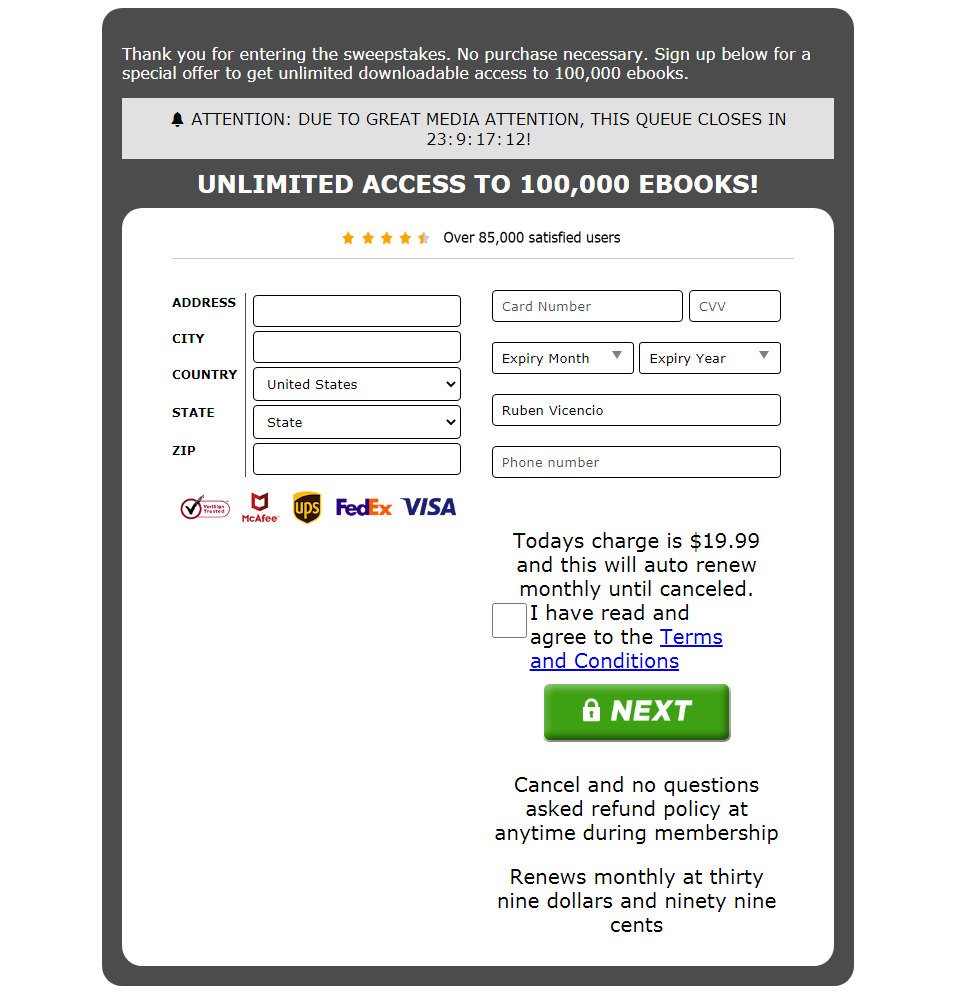
Figure 1. A fake sweepstakes scam landing page
The site also claims to be supported and verified by multiple brands despite having no external links that are affiliated with the website.
Upon taking a closer look, we saw that the domain is relatively new — less than a year old, in fact. This is a strong indicator that the domain is inherently used for scamming purposes.
The terms and conditions page of this fake sweepstakes website points to a company called “Red Gem Media,” which reportedly hosts fraudulent activity and runs multiple fake giveaways.
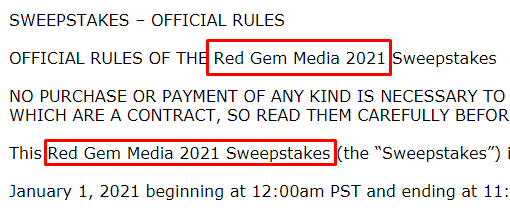
Figure 2. The fake sweepstakes is run by a company called Red Gem Media.
After a user submits their information, the page redirects to a message indicating an unsuccessful submission.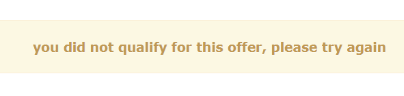 Figure 3. A message indicating that the submission has not been successful
Figure 3. A message indicating that the submission has not been successful
Fake money transfer scheme
Another recent phishing scheme attempts to dupe victims into providing their card information in exchange for a large sum of money that will be deposited to a victim’s account after they pay a transfer fee. Cybercriminals send phishing emails to victims, stating that an amount of 127,280 Russian rubles (roughly equivalent to US$1,700 as of writing) has been approved but needs to be confirmed by the user in order for the transfer to go through.

Figure 4. The phishing email used in this money transfer scheme
Aside from the glaring grammatical and layout errors, the email also contains a fake transaction number and a fake sender account number. What is markedly missing from the email, however, is the name of the money transfer service. Upon clicking the “Go to your personal account” button, the email will redirect to a page that poses as the user’s personal account on a money transfer website (ckconsulting[.]host/landing4.html). 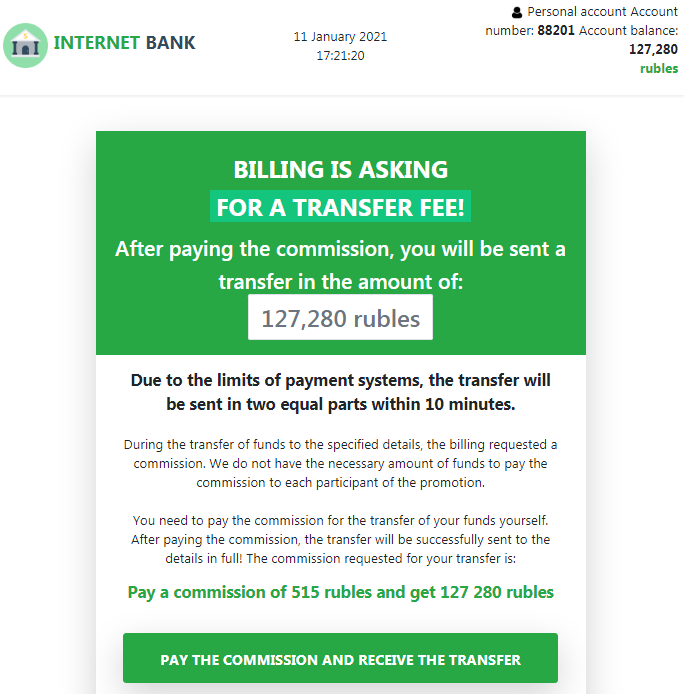
Figure 5. A fake personal account page on the fake money transfer website
The fake personal account page, which features a generic bank name called “Internet Bank,” is on a relatively new domain.
Upon clicking on the “Pay the commission and receive the transfer” button, the user will be redirected to fjpay[.]icu, which displays a fake credit or debit card form. The transfer fee indicated on the form amounts to 515 Russian rubles (equivalent to US$6.95 as of writing).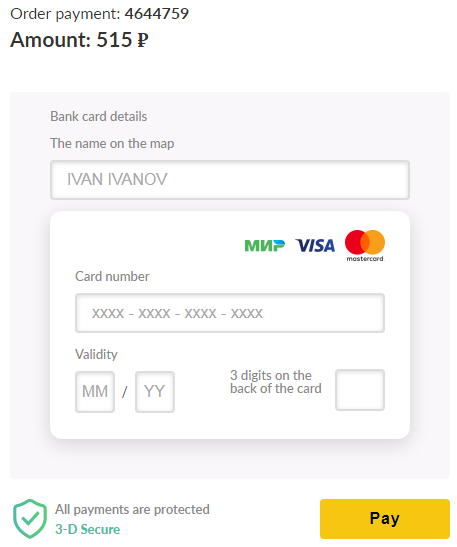
Figure 6. A fake credit or debit card form
Once the victim’s credentials are encoded on the form, the page will redirect to a legitimate transaction verification service (cap.attempts.securecode.com). This process is used to check if the card details that have been provided are valid. Once the card details are verified, an error message stating that the payment was declined by the bank will appear.
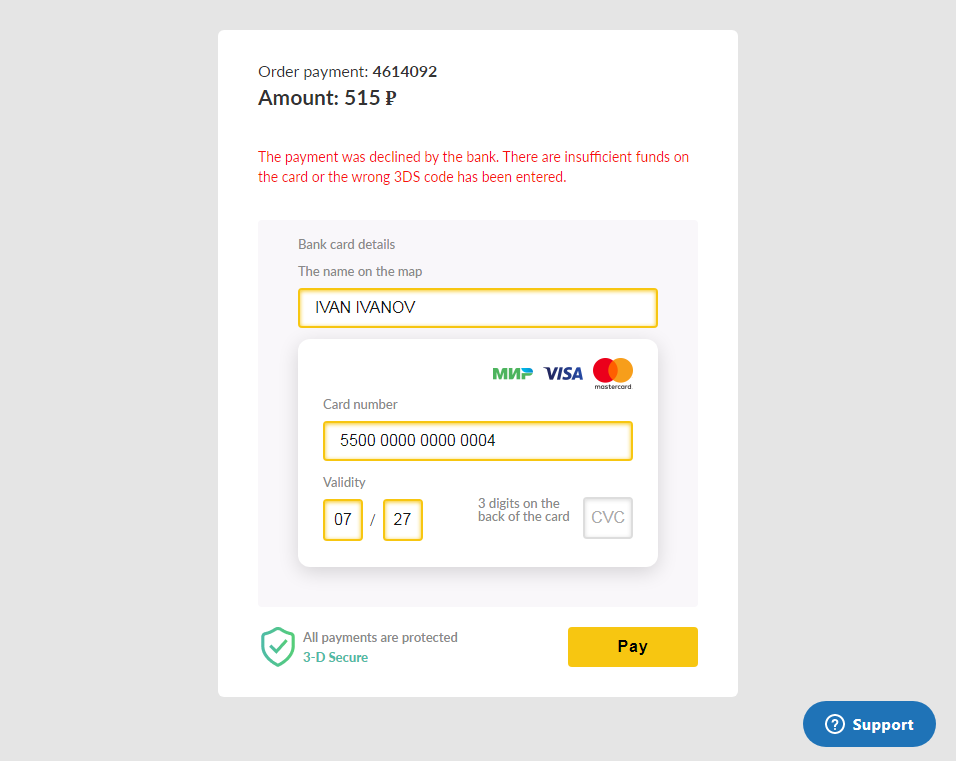
Figure 7. An error message stating that the bank transfer fee payment did not go through
Fake online payment service sites
We also recently saw five fake online payment service websites that aim to siphon off credit card information from victims. Victims are sent emails that contain links to these fake websites.
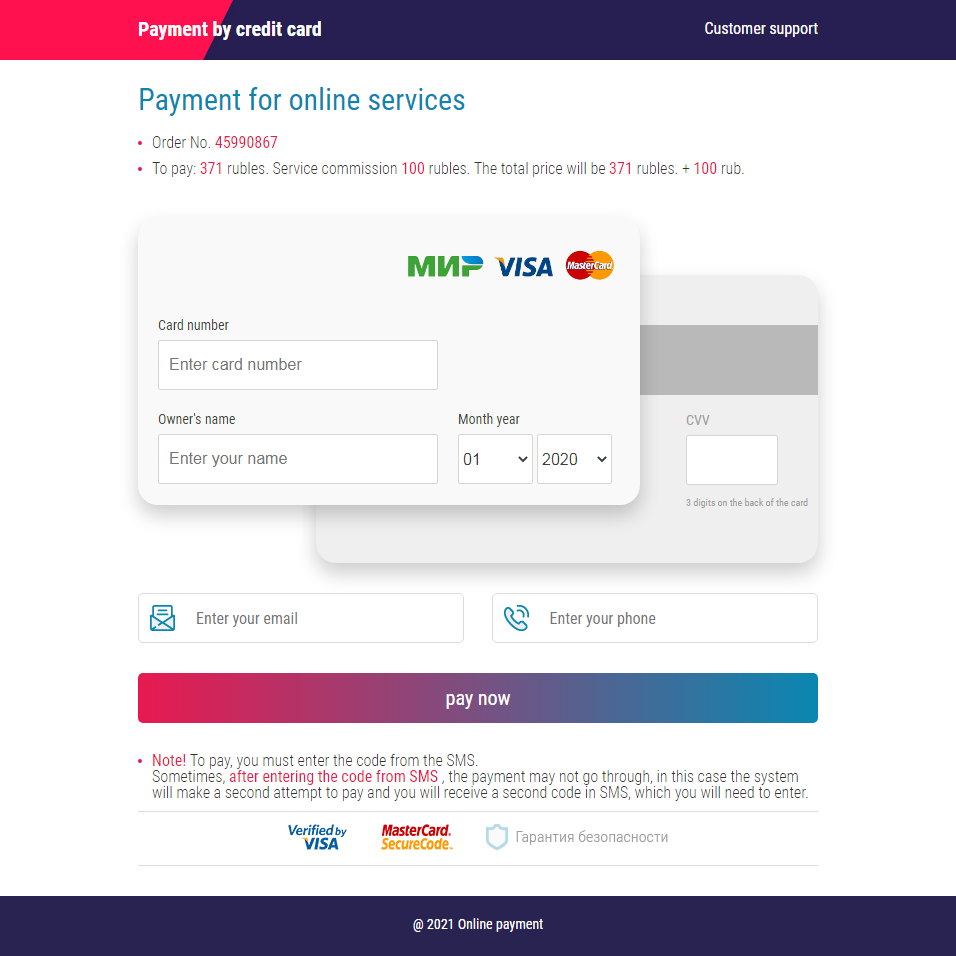
Figure 8. A fake online payment service site
Two of these sites, gosinpay[.]com and onepay[.]shop, are relatively new domains.
After a user agrees to pay a certain amount, the page redirects them to a legitimate transaction verification service (cap.attempts.securecode.com) to check the validity of the card information. After that, the page will be redirected back to the form with no indication of whether the payment was successful.
The other three fake online payment service websites, pay-ping[.]top, payink[.]top, and aalbn[.]xyz, are all less than a month old.
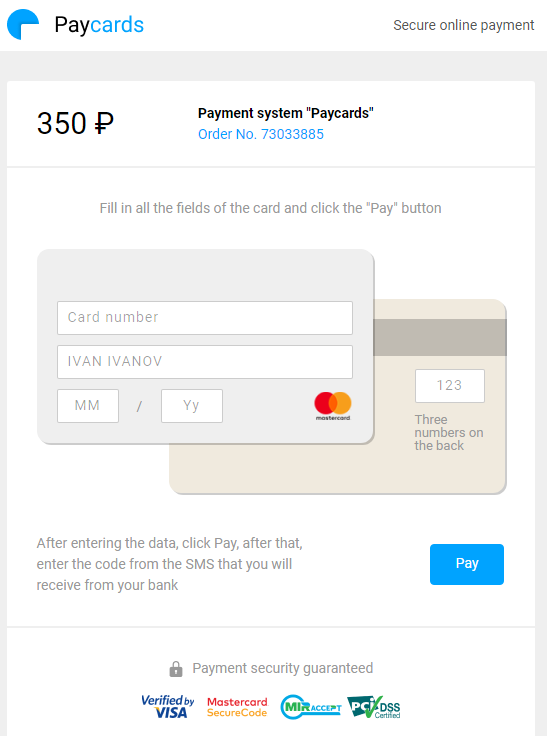
Figure 9. A fake online payment service site
After the card information is filled out and the victim clicks on the “pay” button, the site displays an error message.
 Figure 10. The error message after a victim encodes information on the fake online payment service form
Figure 10. The error message after a victim encodes information on the fake online payment service form
Delivery scams
We saw three package delivery scams that falsify legitimate postal and delivery companies to siphon off financial information from victims. The malicious actors behind these campaigns deliver links to these malicious sites via phishing emails. In all three campaigns, the cybercriminals copied content from authentic companies in order to fool victims into providing their financial information without hesitation.
Fake UPS Taiwan online payment site
A phishing email displays a fake parcel delivery payment page that is purportedly from UPS Taiwan. The page asks for a victim’s credit or debit information before a supposed parcel is delivered.
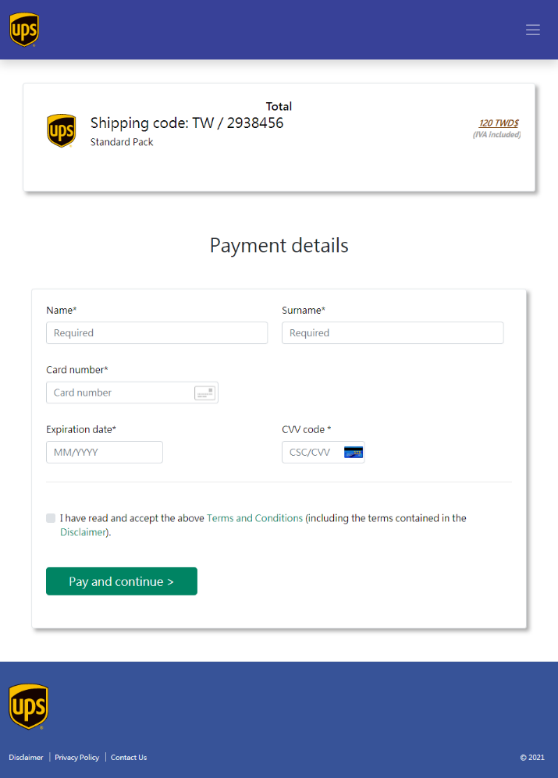
Figure 11. A fake UPS Taiwan parcel payment form
The fake payment form has a URL that is unrelated to UPS (rupeezen[.]com/wp-content/ups.taiwan.delivery/5ff9a9f49fffc26/payment.php). Upon clicking “Pay and continue,” the user will be redirected to a fake SMS verification page.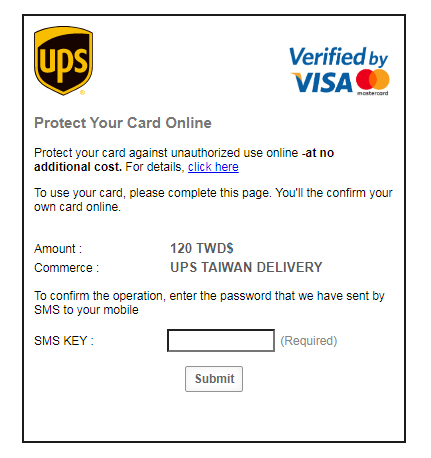
Figure 12. A fake SMS verification page
Aside from the obvious grammatical lapses on the verification page, another indicator that this is a fake page is that when a user types in any number on the “SMS key” portion, it will automatically lead to an infinitely loading page.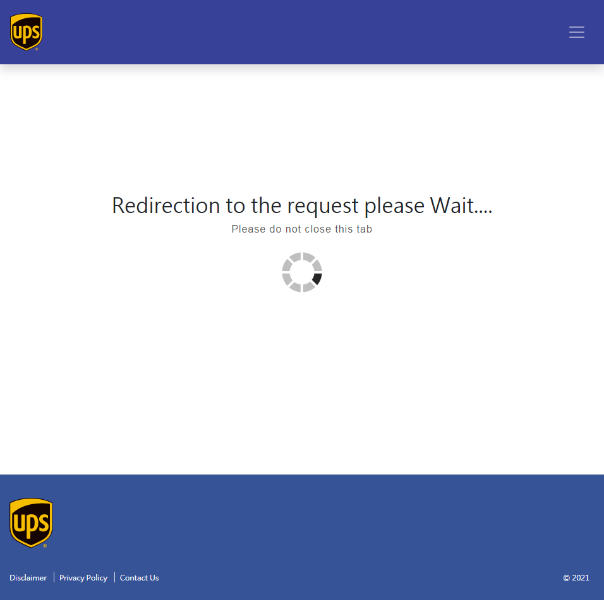

Figure 13. A fake UPS Taiwan page redirects to an infinitely loading page.
Fake Chunghwa Post site
We also saw a campaign that dupes an online payment page for Chunghwa Post, Taiwan’s official postal service. Like the campaign mentioned earlier, this fake payment page has copied content from Chunghwa Post to fool victims into encoding their financial information before a supposed package is delivered. It’s interesting to note that the URLs related to this fake payment site are similar to the domain construction of Chunghwa Post’s website (track-post-gov-tw[.]info/post/internet/Group/fe98e/SSLAuthUI.html which redirects from track-post-tw[.]com/dpc/sd5cds48sd8.html).
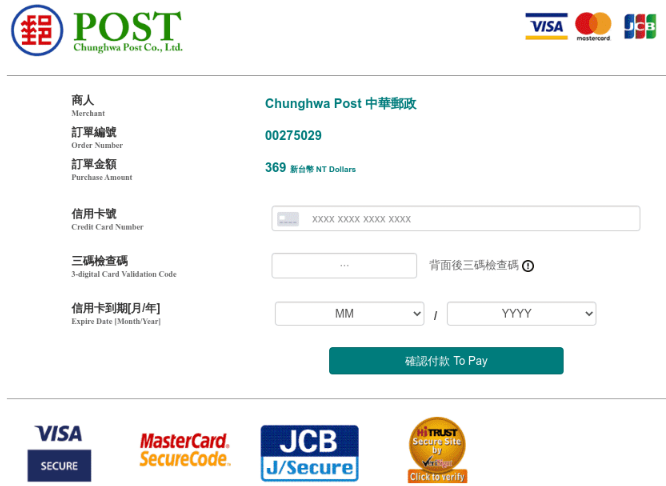
Figure 14. A fake Chunghwa Post online payment page
Although both domains do not provide information for their registration and creation dates, there is evidence that they are relatively new. It’s important to note that as of writing, the contents for these domains are inaccessible.
![The domain information for the URLs that are related to the fake Chunghwa Post payment page, track-post-tw[.]com and track-post-tw[.]info](https://documents.trendmicro.com/images/Fig 15 a.png)
![The domain information for the URLs that are related to the fake Chunghwa Post payment page, track-post-tw[.]com and track-post-tw[.]info](https://documents.trendmicro.com/images/Fig 15 b.png)
Figure 15. The domain information for the URLs that are related to the fake Chunghwa Post payment page, track-post-tw[.]com and track-post-tw[.]info
Fake Singapore Post site
The third campaign features a fake Singapore Post site. Here, a phishing email informs a user of a supposed pending delivery that will be made only after the user pays a small fee of SGD1.99 (equivalent to US$1.49 as of writing). However, Figure 16 shows that the email address of the malicious actor is unrelated to Singapore Post (club[.]vpcuk[.]org). Significantly, the email is also signed at the end as “The Australia Post team.”

Figure 16. A Singapore Post phishing email
Similar to the previously mentioned campaigns, the phishing email redirects to a fake website (vs29[.]com/sgspost/manage/) that mimics content from Singapore Post. It also displays some fake order information and asks for a victim’s card information.
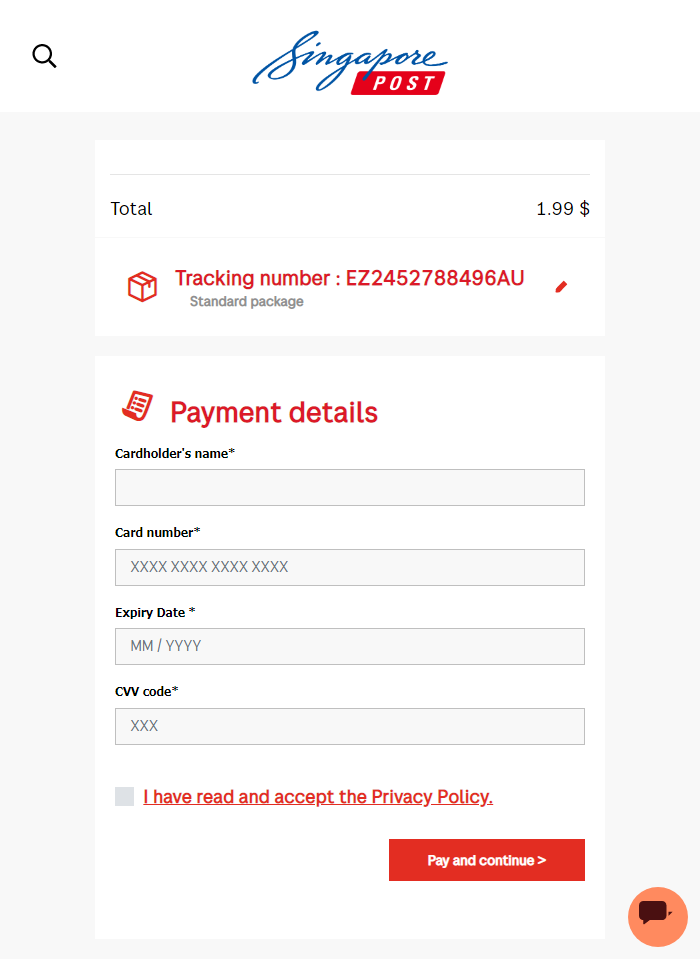
Figure 17. A fake Singapore Post payment page
Once a victim enters credit or debit card information, the fake payment page will lead to an infinitely loading verification page — an indicator that the pending order is inauthentic.
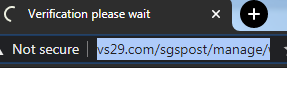
Figure 18. An infinitely loading verification page
More phishing schemes to come
Covid-19 has proven that with or without a pandemic, cybercriminals will continue to prey on victims for ill gain. In fact, cybercriminals have become even more predatory during the pandemic. For example, as more people in different countries favor online shopping in order to stay at home, a whopping 350% increase in phishing websites was seen in the first quarter of 2020.
In the campaigns that we highlighted in this article, the malicious actors included fake online payment forms in order to effortlessly take financial information from victims — a trend that might become the new norm for phishing websites even beyond the pandemic period. Stealing email and password credentials are common for phishing authors, but this mode of operation can also prove fruitless, especially since many popular online brands now support two-factor and multifactor authentication, not to mention even third-party authenticators in order to avoid unwanted account logins to their websites. For phishing authors, it is easier to steal credit and debit information instead. Indeed, ATMs do not require a physical banking card as long as cardless withdrawals are supported. Additionally, while they do require a PIN number before any transaction can be made, this is still an easier problem to fix for phishing authors via brute-force techniques.
Best practices against phishing scams
In order to remain protected from phishing threats, it is recommended that users follow a few best practices:
- Inspect the name of the website. Usually, scam and phishing domains will come in the form of random words that are unrelated to the service that it is posing as (for example, ckconsulting[.]com or vs29[.]com).
- Inspect the content of the website. If you unknowingly click on a website, check its brand name or the name of the service. Phishing websites are a bit tricky since they often copy a legitimate brand’s content. This is why it’s helpful to explore external links such as the “Terms of Service,” “Help,” and “Privacy Policy” pages, if available.
- Double-check all information. If you receive an email indicating that you are the recipient of a delivery order, make sure that it is legitimate by manually checking your account on the official website of the postal or delivery service.
Trend Micro solutions
The Trend Micro™ Cloud App Security solution enhances the security of Microsoft 365 and other cloud services by taking advantage of sandbox malware analysis for ransomware, business email compromise (BEC), and other advanced threats. It also protects cloud file sharing from threats and data loss by controlling sensitive data usage and protecting file sharing from malware.
Trend Micro™ Deep Discovery™ Email Inspector defends users against phishing and ransomware attacks through real-time scanning and advanced analysis techniques for known and unknown attacks.
Trend Micro™ Security, which includes Antivirus+ Security,Antivirus for Mac®, Internet Security, Maximum Security, and Premium Security Suite, protects users from web threats, scams, and phishing attempts. It also blocks malicious websites that aim to steal personal data.
The Trend Micro™ Home Network Security protects home networks by effectively blocking intrusions, hacking attempts, and web threats.
The Trend Micro™ Mobile Security for Android and Trend Micro Mobile Security for iOS thwart threats, block malicious apps and websites, improve device performance, and shield users against unsafe Wi-Fi networks.
Trend Micro™ Fraud Buster is a free online service that utilizes advanced machine learning systems and Trend Micro’s extensive database to inform users if a suspicious email or chat message poses a threat or otherwise through a rating system.
Trend Micro Check, a browser extension for Google Chrome and a chatbot for Facebook Messenger and WhatsApp, helps protect users by actively checking suspicious websites and sales scams. It also integrates with NewsGuard, allowing users to verify the credibility of online news items and stories.
The Trend Micro Site Safety Center is a free online service that allows users to check if a URL is safe to access. It provides users scores that are based on several factors, including historical locations, changes, and indications of suspicious activities.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One