The SCADA That Cried Wolf: Who Is Really Attacking Your ICS Devices Part 2 [blog]
The concern on ICS/SCADA security gained prominence due to high-profile attacks targeting these devices, most notably Flame and Stuxnet. However, we noted recent findings, which prove that the interest in ICS/SCADA devices as attack platforms is far from waning.
We’ve all read about how insecure ICS/SCADA devices are and how certain threat actors are targeting these systems. As proof, we noted numerous attempts aimed at the dummy ICS and SCADA devices we created during our initial research. The insights gathered from this were the basis of my talk during the Blackhat Europe 2013 last March, which later became the paper Who’s Really Attacking Your ICS Equipment?.
More importantly, this study gave us a look at the possible consequences that may occur once these devices are attacked successfully.
This time around, my latest research The SCADA That Cried Wolf: Who’s Really Attacking Your ICS Devices takes the issue of ICS/SCADA attacks further. While in my first paper we saw several threat actors attempt attacks on these fake ICS systems, this time we are now seeing several noteworthy trends. One of these is the increase in “targeted” attacks – i.e., attacks that appear to be looking into ICS devices more closely prior to executing the attack. During the study, we found malware targeting very specific applications, which can be considered more “targeted” as threat actors are now Trojanizing valid applications traditionally seen as “proprietary”.
Continuing in the same vein, we saw several attacks listed below that are interesting. The following graph shows the the origins of attack against our ICS honeypots.
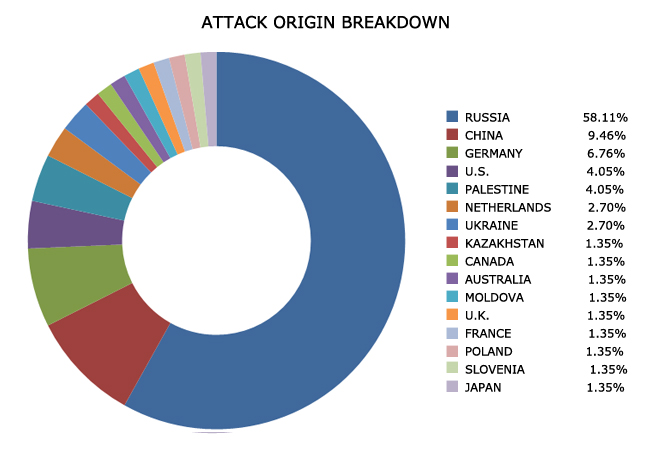
Figure 1: Percentage of attacks per country
This new research also includes new details and architecture into the virtualized installments worldwide; to eight different countries and 12 different cities. I also cover the in-depth usage of Browser Exploitation Framework (BeEF) for use in attribution of attackers.
We expect that attack trends will continue to increase in the ICS arena, with increased motivation and aim. In addition, we expect that possible ransomware may start to affect the ICS arena, possibly holding devices hostage in return for payment (or ransom). With continued diligence and utilizing secure computing techniques, your ability to deflect and defend these attacks will help secure your organization. To know more about how to defend these devices, you may refer to my previous posting Protecting Your ICS/SCADA Environment.
The findings on this research provide great insight into the world of ICS/SCADA attacks. You may read the full report here.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One