
Data security refers to managing and protecting sensitive digital information throughout its lifecycle using a combination of governance, layered technical and administrative controls, and continuous risk-informed processes across different environments.
Table of Contents
Data security in modern computing
In a world of distributed computing, enterprise operations span on-premises systems, multiple cloud environments, and services delivered “as a service.” Data security must therefore address protecting sensitive data across the full spectrum of environments. Risk-informed organizations recognize that protecting data is not simply a matter of firewalls, but of unified policy, oversight, and measurable controls.
The National Institute of Standards and Technology (NIST) defines the information life cycle as stages including creation, processing, use, storage and disposition, a model that underpins modern data-security strategies (NIST, 2016). The same research shows that knowing how data flows and where controls apply is foundational to effective protection.
Governments estimate the economic impact of malicious cyber activity at between US $57 billion and US $109 billion in a single year, underscoring how critical it is for business leaders to view data-security as an enterprise risk, not just an IT issue (White House, 2018).
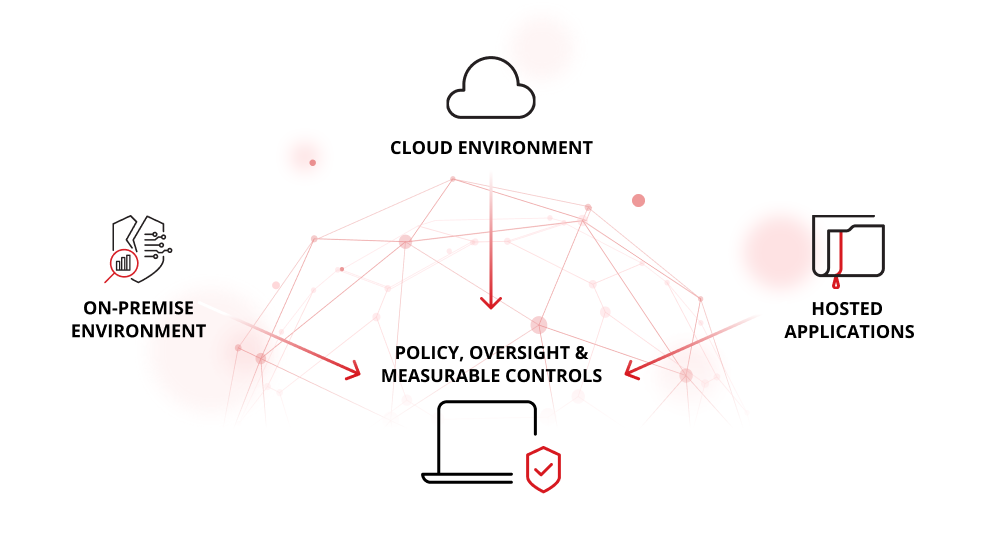
Data security policies, standards and best practices
Robust data security starts with policy: clear definitions of data types, classification schemes, and lifecycle responsibilities. Standards such as NIST SP 800-64 and other lifecycle-oriented frameworks articulate how organizations should balance protection of assets with efficient operations (NIST, 2008).
From that foundation, organizations build layered controls: encryption and key-management at rest and in transit, identity and access management on every platform, logging and audit trails for activity, and egress monitoring for environments that include SaaS and cloud.
Best practices dictate that policies are aligned with the enterprise’s risk strategy, are applied across the hybrid infrastructure (on-premises, hybrid, cloud) and are updated continuously. Standardization across platforms offers regulatory alignment, operational resilience, and a base for automation and measurement.
Implementing data security best practices in the cloud
Cloud adoption and service models change the calculus of data security. Data may reside in multiple regions, move between SaaS applications, and be accessed via mobile or remote devices, increasing both scale and exposure. Enterprises often have many copies and silos of data across hybrid infrastructure, complicating governance and controls.
Modern frameworks emphasize lifecycle control of data, requiring unified discovery, classification, access controls, and monitoring across all storage and service platforms. The NIST Research Data Framework (RDaF) version 2.0 outlines six lifecycle stages and supports strategies to manage data throughout enterprise and hybrid environments (NIST, 2024).
Integrating data-loss prevention, policy-based monitoring, encryption in transit and at rest, and identity-driven access across computing platforms allows organizations to regain control of data even as workloads shift and evolve. The key is to treat data as the guarded asset, not just the environment.
Data security vs. traditional perimeter protection
Traditional perimeter security focuses on network boundaries, keeping threats out of the “castle.” In contrast, modern data security assumes threats can originate anywhere: endpoint, cloud service, supply chain. It protects the data itself regardless of location.
This shift aligns with zero-trust architecture: trust nothing by default, verify every connection, and protect every object. Data-centric security means focusing on how data is accessed, used, moved, and disposed of across the IT infrastrcture, not just within network boundaries.
Organizations must move from asking “Where is our boundary?” to “How is our data managed, accessed, and protected across the entire environment and services?” The critical question becomes not location, but control, visibility and accountability.
Aspect
Data Security
Traditional Perimeter Protection
Security Scope
Applies to data at rest, in transit, and in use across systems and platforms.
Focuses on securing the perimeter of a network (e.g., firewalls, routers).
Approach
Applies to data at rest, in transit, and in use across systems and platforms.
Broad, location-based, and relies on blocking unauthorized access.
Threat Detection
Uses data-centric monitoring, anomaly detection, and Data Loss Prevention (DLP).
Uses intrusion detection/prevention systems (IDS/IPS) at network edges.
Compliance & Governance
Aligns with data protection regulations (e.g., GDPR, HIPAA).
May not fully address data-specific compliance requirements.
Technology Examples
Encryption, tokenization, DLP, Zero Trust, IAM (Identity & Access Management).
Firewalls, VPNs, IDS/IPS, DMZs (Demilitarized Zones).
Data security vs. compliance-only approaches
Compliance frameworks are valuable. They set minimum thresholds for protection, drive audit evidence, and support regulatory alignment. But compliance alone is not sufficient. A compliance-only mindset can leave operational gaps, technological blind spots and resilience shortfalls.
Data security must be embedded in strategy, not just a certification checkbox. When organizations align data-security controls with business risk, measure outcomes, and update policy/process/technology dynamically, they achieve performance and protection. Over time, policies evolve into best practices, and systems become measurable and accountable.
Aspect
Data Security
Compliance-Only Approach
Primary Goal
Protect data from breaches and unauthorized access
Meet regulatory requirements and avoid penalties
Focus
Risk reduction and proactive defense
Documentation and audit readiness
Key Activities
Encryption, access control, threat monitoring, patching
Policies, procedures, reporting, certifications
Outcome
Strong resilience against cyberattacks
Legal compliance but potential security gaps
Risk
Lower risk of breaches
Higher risk if compliance is treated as the end goal
Data security governance and continuous improvement
Governance ensures that policies, controls and systems remain aligned with business strategy, technology change, and threat evolution. Frameworks such as NIST SP 800-37 (Risk Management Framework) guide organizations through preparation, assessment, monitoring and continuous improvement (NIST, 2019).
Key metrics provide visibility: percentage of data classified, encryption coverage, key-rotation compliance, mean time to restore, time to detect abnormal access or exfiltration. These become how executives and boards understand risk and progress.
By embedding data-security ownership into enterprise risk management, organizations position data-security not as a cost center but as a strategic enabler. Unified oversight across platforms, consistent policy enforcement and measurable outcomes build trust and continuity.
Why data security matters for today’s enterprises
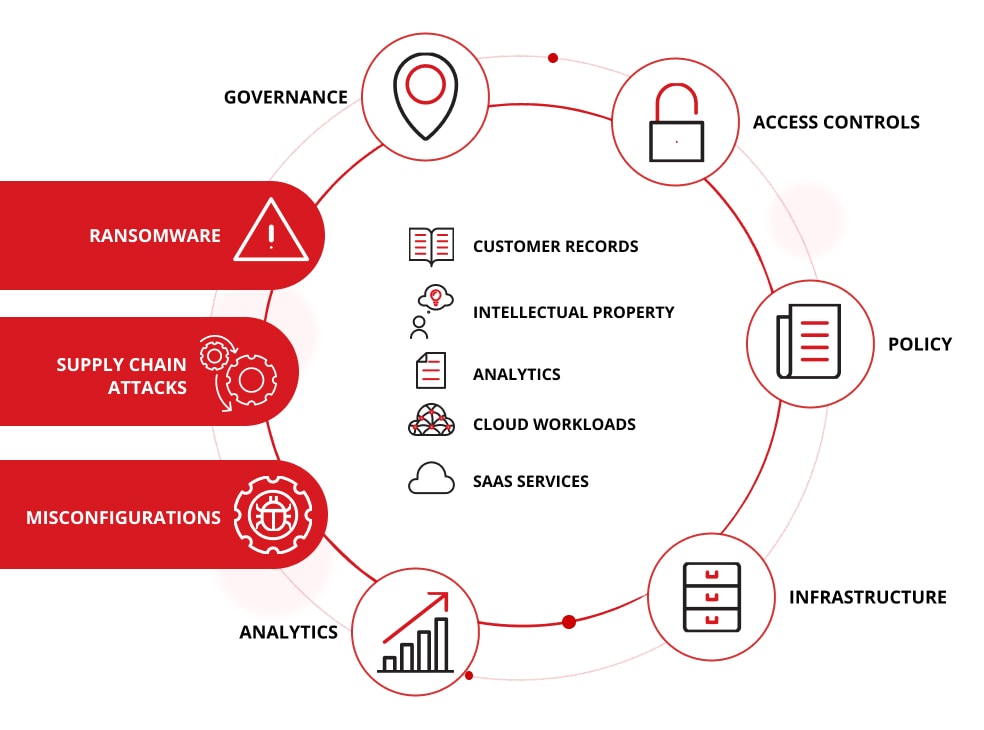
Data is the lifeblood of modern business: customer records, intellectual property, analytics, cloud workloads and SaaS services drive value. Yet data is also the target of modern adversaries like ransomware, supply-chain attacks, and exploitation of cloud misconfigurations. Organizations with fragmented data oversight, unsupported infrastrcture, or legacy controls are exposed.
By taking a holistic approach to data security that connects policy, infrastructure, access, controls, analytics, and governance, enterprises reduce risk, enable innovation, and build resilience. They meet regulatory obligations and build stakeholder trust. They also turn data into a strategic asset rather than a liability.
Where can I get help with data security?
The data landscape requires more than compliance checklists; it demands a proactive, risk-informed approach to protecting sensitive information across every environment. Trend Vision One™ delivers this capability through an AI-powered enterprise cybersecurity platform designed to safeguard data wherever it resides.
By unifying visibility across cloud, endpoint, email and network layers, Trend Vision One centralizes data protection, privacy enforcement and compliance reporting. Its native AI engine, Trend Cybertron™, analyzes global telemetry to identify emerging risks and recommend preventive measures before exposure occurs. Discover how Trend Vision One can enhance your data security posture today.
Scott Sargeant, Vice President of Product Management, is a seasoned technology leader with over 25 years of experience in delivering enterprise-class solutions across the cybersecurity and IT landscape.
Frequently Asked Questions (FAQs)
How is data stored?
Data lives on physical drives, cloud servers, or network systems, organized in databases for retrieval and analysis.
Is all data stored forever?
No. Ethical storage follows retention limits, so data is deleted or anonymized once no longer needed or legally required.
What are the basics of data security?
Protecting information through access control, encryption, and monitoring to prevent unauthorized use, loss, or corruption.
What is data security in simple words?
Keeping digital information safe from theft, damage, or misuse using technology, policies, and responsible human behavior.
What are the 5 components of data security?
Confidentiality, integrity, availability, authentication, and accountability; together ensuring that data remains accurate, accessible, and trusted.
What are the three principles of data security?
Confidentiality, integrity, and availability—known as the CIA triad—form the foundation of every secure system.
What are some examples of data security?
Encryption, data masking, threat detection, and exposure management all protect sensitive digital assets.
What does GDPR stand for?
General Data Protection Regulation is the European Union’s privacy law that gives individuals control over how organizations collect and use their data.
What are the 7 GDPR requirements?
They are: lawfulness, fairness, and transparency; purpose limitation; data minimization; accuracy; storage limitation; integrity and confidentiality; and accountability.
What are the four major data threats?
Malware, phishing, credentialmisuse, and physical loss of devices compromise confidentiality and system reliability.

