Cyber Threats
Tackling the Growing and Evolving Digital Attack Surface: 2022 Midyear Cybersecurity Report
This blog entry highlights the threats that dominated the first six months of the year, which we discussed in detail in our midyear cybersecurity roundup report, “Defending the Expanding Attack Surface.”
Organizations had to contend with scattered work pools and a widened digital attack surface in the first half of 2022 — a situation that cybercriminals were quick to take advantage of by launching sophisticated attacks both old and new. In fact, Trend Micro detected and thwarted over 63 billion overall threats in the first half of 2022. We discuss the threats that dominated the first six months of the year in our midyear cybersecurity roundup report, “Defending the Expanding Attack Surface.”
The continued growth of MaaS and RaaS schemes
The first half of 2022 saw a rise in malware-as-a-service (MaaS), as evidenced by the resurgence of the Emotet botnet. Although Emotet’s infrastructure was dismantled in 2021, malicious actors continued to use it as part of their MaaS schemes to deploy Conti and other ransomware families to Emotet-compromised systems.
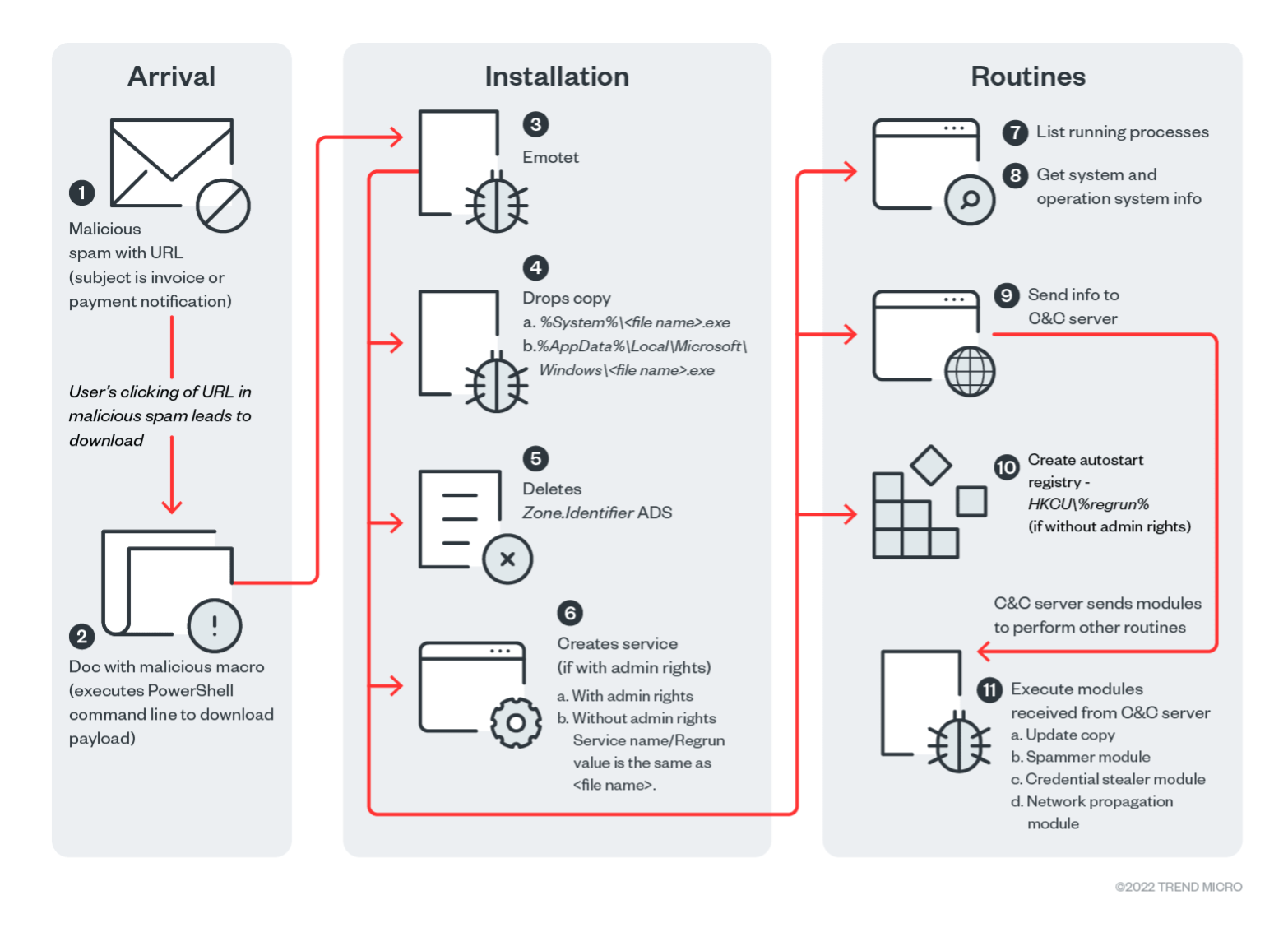
According to our Trend Micro Smart Protection Network (SPN) platform, Emotet detections soared in the first six months of 2022 with 148,701 detections compared to the 13,811 detections in the first half of the previous year. Based on our telemetry, Japan was the country with the highest number of detections.
| Comparison of Emotet detections | |
|---|---|
| Year | Count |
| 1H 2021 | 13,811 |
| 1H 2022 | 148,701 |
Source: Trend Micro Smart Protection Network
| Top five countries with Emotet detections | |
|---|---|
| Country | 1H 2022 |
| Japan | 107,669 |
| US | 4,837 |
| India | 3,729 |
| Italy | 3,442 |
| Brazil | 3,006 |
Source: Trend Micro Smart Protection Network
Ransomware-as-a-service (RaaS) schemes were also prevalent during this period. This model allows developers’ affiliates — even ones without significant technical knowledge — to purchase or rent ransomware tools and infrastructures to make attacks even more sophisticated. Based on available data for the first half of 2022, there were 67 active RaaS and extortion groups with over 1,200 victim organizations.
| Active RaaS and extortion groups | Victim organizations |
| 57 | 1,205 |
The numbers of active RaaS and extortion groups and the number of victim organizations of successful ransomware attacks in the first half of 202
Source: RaaS and extortion groups’ leak sites
Our SPN data also shows that LockBit, Conti, and BlackCat were the three ransomware families that stood out in the RaaS arena in terms of detections.
| Ransomware family | 1H 2021 | 1H 2022 |
| LockBit | 341 | 1,843 |
| Conti | 622 | 1,090 |
| BlackCat | 2 | 1,397 |
Source: Trend Micro Smart Protection Network
The pervasiveness of cloud misconfiguration and cryptocurrency-mining attacks
Cloud-based containers have been integral to the digital transformation strategies of organizations worldwide. Unfortunately, because of containers’ ubiquity and tendency to be misconfigured, malicious actors continue to target them in varied and evolutionary attacks.
A survey conducted by Red Hat in May 2022 further proves just how substantial the misconfiguration problem in organizations is. 300 DevOps, engineering, and security professionals comprised the respondents, 53% of whom shared that they detected a misconfiguration in their containers and/or Kubernetes deployments.
In May 2022, we investigated Kubernetes clusters that were publicly exposed via port 10250 and saw over 243,000 exposed cluster nodes via Shodan. It should be noted that almost 600 nodes returned the “200 – OK” notification, which attackers could exploit by installing and running malicious programs on the kubelet API.
Aside from abusing publicly exposed Kubernetes clusters, cybercriminals also continued to steal cryptocurrency-mining capabilities from victims’ resources in the first half of the year. We determined the five most prominent actor groups in the cryptocurrency-mining space based on research we conducted last year and published earlier this year: Outlaw targets internet-of-things (IoT) devices and Linux cloud servers by exploiting known vulnerabilities or performing brute-force Secure Shell Protocol (SSH) attacks, while TeamTNT is one of the most technically proficient threat actors focused on cryptocurrency mining. Kinsing is known for quickly abusing new exploits (including the Log4Shell vulnerability) in a short period, while 8220 is known for exploiting Oracle WebLogic vulnerabilities. Finally, Kek Security is a relatively new group that uses sophisticated techniques and integrates new exploits in its attacks.
Protecting organizations from sophisticated and complex threats amid an expanding attack surface
Two years ![]() after the onset of a global health crisis, many organizations around the world have started to return to their offices, while the rest have opted for a hybrid or a permanent remote work setup. To keep interconnected working environments and new tools and technologies secure, cybersecurity teams require a strong and unified cybersecurity strategy that can cover the burgeoning digital attack surface. Read our midyear cybersecurity report, “Defending the Expanding Attack Surface,” to learn more about the threat landscape in the first half of 2022 and gain critical insights on security protocols and best practices.
after the onset of a global health crisis, many organizations around the world have started to return to their offices, while the rest have opted for a hybrid or a permanent remote work setup. To keep interconnected working environments and new tools and technologies secure, cybersecurity teams require a strong and unified cybersecurity strategy that can cover the burgeoning digital attack surface. Read our midyear cybersecurity report, “Defending the Expanding Attack Surface,” to learn more about the threat landscape in the first half of 2022 and gain critical insights on security protocols and best practices.

