TrickBot continues to evolve as it adds more features to steal users’ credentials, the most recent development we published being the pwgrab32 module. Because of TrickBot’s modular capability, we found a newly added POS malware feature that makes this banking trojan more dangerous. The new module scans for indicators if an infected computer is connected to a network that supports POS services and machines.
We’re currently investigating how the malware authors could leverage this information, given that they have successfully infiltrated the network with POS-related services installed but stop short of getting specific data such as credit card, ATM or other banking-related information. It’s possible that the cyber actors are gathering information at this stage in preparation for future intrusions.
Analyzing module psfin32
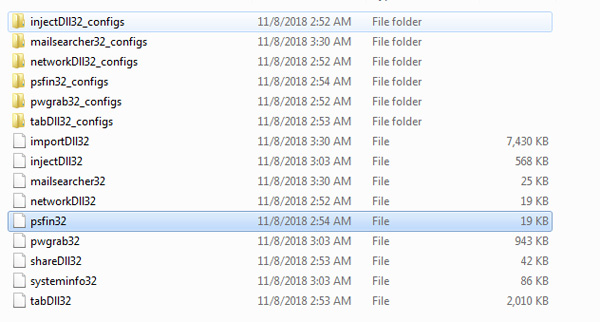
Figure 1. TrickBot’s new module, psfin32
The new POS extraction module, psfin32, is similar to its predecessor network domain harvesting module, but modified solely to identify POS-related terms located in the domain of interest. Identifying the POS services in a network from domain controllers and basic accounts, this module still uses LDAP queries to access Active Directory Services (ADS), which is responsible for storing information about objects on the network. This LDAP query searches for machines in the Global Catalog for dnsHostName containing the following substrings:
| *POS* | *LANE* | *BOH* | *TERM* |
| *REG* | *STORE* | *ALOHA* | |
| *CASH* | *RETAIL* | *MICROS* |
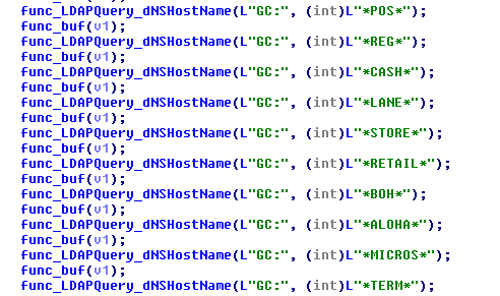
Figure 2. LDAP query substrings search

Figure 3. LDAP query machine search
If the query does not resolve any of the requested information, it also performs other queries for different accounts or objects in the network based on the following:
- sAMAccountName: This is used to support legacy Windows OS versions such as Windows NT 4.0, Windows 95, Windows 98, and LAN Manager

Figure 4. sAMAccountName user query

Figure 5. sAMAccountName group query
- Site Name

Figure 6. Site name query
- Organizational Unit (OU)

Figure 7. OU query
In addition to domain controllers, it also sends queries to computers with basic accounts or users in the network with UserAccountControl (UAC) 8192.
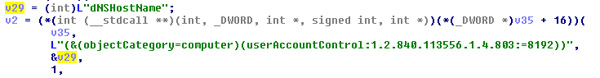
Figure 8. Non-domain controller query
Once TrickBot has extracted the information, it stores the information to its pre-configured “Log” file to send to its C&C server Dpost server via POST connection. If the C&C server is not accessible, it would prompt “Dpost servers unavailable,” otherwise the prompt shows “Report successfully sent.”
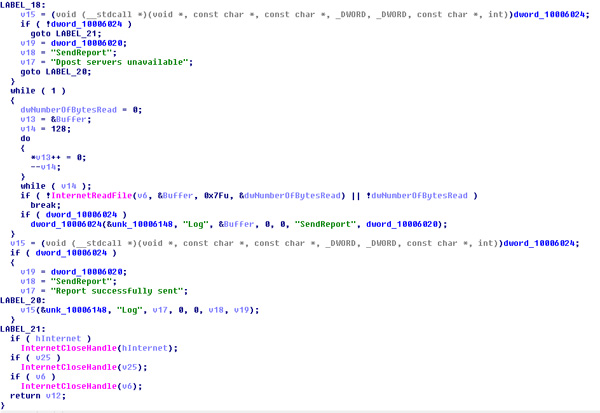
Figure 9. C&C communication
Considering the module’s timing for deployment, the threat actors may be leveraging the holidays to gather information and distribution, especially after a similar entry by Brad Duncan published in ISC talked about a malspam campaign involving TrickBot macros targeting the United States. While the analyzed sample size of documents and URLs have since been inaccessible, users and businesses are cautioned against opening suspicious emails, files and attachments.
Defending against this threat: Trend Micro solutions
Given its modular feature, we can expect more changes from TrickBot to make it more challenging to detect and defend against. Users and businesses can defend themselves from banking trojans like TrickBot by using a multi-layered approach, especially given this busy season.
Trend Micro protects customers from all threats related to TrickBot. To protect enterprises and users from this malware, it is best to employ endpoint application control that reduces attack and infiltration exposure by ensuring only files, documents and updates associated with whitelisted applications and sites can be installed, downloaded, and viewed. Endpoint solutions such as Trend Micro™ Security, Trend Micro™ Smart Protection Suites, and Trend Micro Worry-Free™ Business Security can detect these malicious files to protect users' systems.
Indicator of Compromise
SHA256
a9b00d12f7fa52209a8ead91bb595522effc0ab5e4dcfa02e0d145ae7ea1cb19 - TrojanSpy.Win32.TRICKBOT.AL

