The IT teams of medium and large businesses are expected to protect their networks from high-risk enterprise threats. At the same time, they are also expected to concentrate on their main role, which is managing the day-to-day IT operations of their companies. To help IT teams decide where their points of focus should be to create an effective security strategy, we took a look at data based on the Trend Micro™ Smart Protection Network™ infrastructure in North America in the first quarter of 2018. We determined the trends in the threat landscape and paint a picture of the main types of threats that both individuals and organizations face today. From there, we were able to summarize the trends into three main points:
- Information stealers remained to be among the most prevalent malware today.
- Despite its decline, ransomware was still among our top detections.
- Cryptocurrency miners continued to gain traction in line with the hype around cryptocurrency.
The information we’ve gathered points to the importance of implementing a proactive incident response strategy, including threat detection and incident response capabilities when possible and expert assistance where necessary.
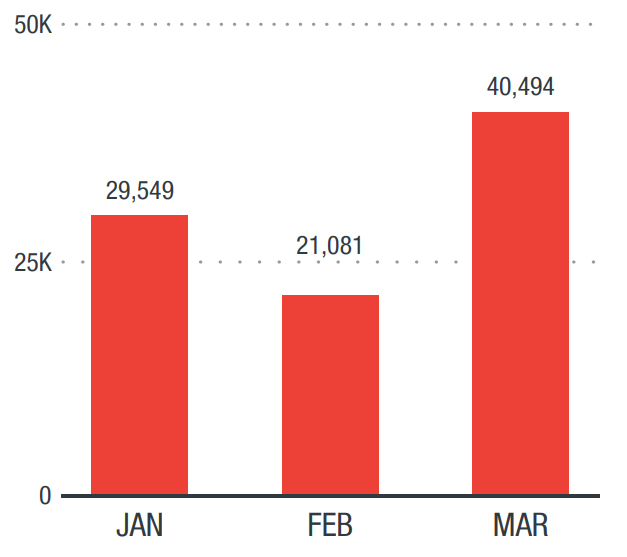
Total malware detections in North America in Q1 2018
Malware families such as EMOTET, DRIDEX, and QAKBOT were neither new nor especially noteworthy. Yet they were still among those that had high detections. They are extensively used by cybercriminals looking to steal information because of their effectivity, wide array of capabilities (such as email spamming and lateral movement), and fast propagation techniques (including spreading via botnets). Given the large number of security technologies that are designed to combat them, it would make sense to think that IT teams would have little difficulty detecting and containing these threats. However, our high detection numbers indicate that they still pose a significant problem for organizations. Considering that there are even more challenging threats in the wild, we start to get an idea of what IT teams are dealing with when it comes to security.
While our data showed declining numbers, make no mistake about it: Ransomware still had high detection counts. These included two notable ransomware variants, WCRY and LOCKY. WCRY, perhaps the most noteworthy malware of 2017, struck anew with attacks on an aerospace corporation. LOCKY, while perhaps not as notable as WCRY in terms of making media headlines, still accounted for the majority of malicious email traffic.
Ransomware can be devastating for organizations, as essential data or even the actual operations can be compromised. For example, a computer containing health records can be infected and its data encrypted, preventing access to important patient information. In a worse scenario, large numbers of an enterprise’s endpoints can be crippled, resulting in the inability to run the business properly. With these in mind, IT teams have a strong reason to ensure that their networks are as safe as possible from a full-blown attack.
Unsurprisingly, the hype surrounding cryptocurrencies seems to have a direct correlation to the rise of cryptocurrency miners, the malicious sort of which uses the resources of victimized systems to surreptitiously harvest cryptocurrencies on behalf of the attackers. Cryptocurrency miners emerged as the second most detected type of malware in North America in Q1 2018, with miners such as COINHIVE, COINMINER, MALXMR, and CRYPTONIGHT among the most notable variants. IT teams may have trouble detecting cryptocurrency mining malware in their networks, since malicious miners are designed to be difficult to detect and to remain in the victimized systems as long as possible. This means that an attacker can infect an endpoint and earn cryptocurrencies with little effort and without the user noticing anything amiss except for decreased system performance, which can be attributed to other factors. While damaging enough to individual users, cryptocurrency mining malware in an enterprise environment can be even worse as compromised system performance can affect an organization’s bottom line.
| Month | Information Theft Malware | Ransomware | Cryptocurrency-Mining Malware |
| January | 10,688 | 4,756 | 7,344 |
| February | 8,181 | 4,054 | 1,563 |
| March | 9,577 | 3,794 | 7,665 |
| Total | 28,446 | 12,604 | 16,572 |
Comparison of information theft malware, ransomware, and cryptocurrency-mining malware detections
With regard to infection vectors, email- and web-based techniques emerged as the primary approaches. Delivering threats via email, in particular, has proved to be a widely used technique among cybercriminals owing to its effectiveness and simplicity — all it often takes is social engineering, a decoy document, and the exploitation of a known flaw to do the job.
Taking a proactive security stance
While the threats varied widely in terms of characteristics and capabilities, many of them were also challenging to address from a security standpoint. Given the persistence of the threats we detected, simple, perimeter-based security may not be adequate enough to stop the threats before they can inflict damage. Thus, there is a need for IT professionals in an organization to take a more proactive approach when it comes to security, as it will allow for quicker detection and response to threats. While the use of multilayered security technology can certainly help, even relatively simple but effective techniques such as proactive network monitoring, log analysis, and network segmentation can prevent, or at least minimize, potential damage in the event of a malware infection.
However, there can also be limitations to this approach. While large organizations may have the luxury of having and maintaining full-time security teams, smaller organizations have to rely on their in-house security teams, which are likely to already have their hands full performing the day-to-day task of handling the technology side of the business. Furthermore, while security researchers and professionals working in the industry are able to detect and address most kinds of malware, regular IT staff may not have the skills or experience required to handle the more advanced threats.
Even ransomware, one of the most common types of malware in the wild, often has telltale signs within the first few minutes of infection that can be detected by proper network monitoring (or even by knowing the proper file extensions used by ransomware). But these can fall through the cracks as IT staff may not know what to look out for. Stopping the infection as soon as possible can make a world of difference; even a brief time in which the ransomware runs rampant can allow it to encrypt even more files or cause more damage.
Cryptocurrency-mining malware can be difficult to detect as it often runs in the background. However, the longer it stays within a system, the more CPU cycles it consumes and the more cryptocurrencies the cybercriminals are able to mine.
Information theft malware is especially harmful, as leaked data can cause widespread damage — not only to an organization’s business but also to its clients and reputation.
The role of managed detection and response (MDR)
For organizations that want to maximize their security strategies but cannot afford full-time security teams, managed detection and response (MDR) may be a viable option. Essentially, MDR can be considered as a “crack team” of security professionals who will handle a specialized role for an organization, typically proactive threat detection and analysis, including vulnerability assessment, patching, firmware upgrades, and intrusion detection and prevention systems (IDS/IPS) monitoring.
One of the main advantages of MDR is that it is able to place an incident into context and correlate logs with events. The MDR team consists of security analysts and incident response analysts who can look into an organization’s logs to check whether any noteworthy events are happening. If any suspicious activities or notable incidents are seen, they will reach out to the organization and do further examination. MDR is then responsible for both threat research and dealing with incidents. A delivery mechanism for the solution — such as a customer notification, threat intelligence, or pattern file — is decided upon, which is then provided to the organization.
Learn more about how a proactive incident response strategy and MDR can be used to handle modern threats in our research brief, The Need for Proactive Incident Response: Q1 2018 Trends in the North American Threat Landscape.