Ransomware
Brute Force RDP Attacks Plant CRYSIS Ransomware
In 2016, we noticed that operators of the CRYSIS ransomware family were targeting Australia and New Zealand businesses via RDP brute force attacks. Since then, brute force RDP attacks against SMEs and large enterprises across the globe were seen.
In September 2016, we noticed that operators of the updated CRYSIS ransomware family (detected as RANSOM_CRYSIS) were targeting Australia and New Zealand businesses via remote desktop (RDP) brute force attacks. Since then, brute force RDP attacks are still ongoing, affecting both SMEs and large enterprises across the globe. In fact, the volume of these attacks doubled in January 2017 from a comparable period in late 2016. While a wide variety of sectors have been affected, the most consistent target has been the healthcare sector in the United States.
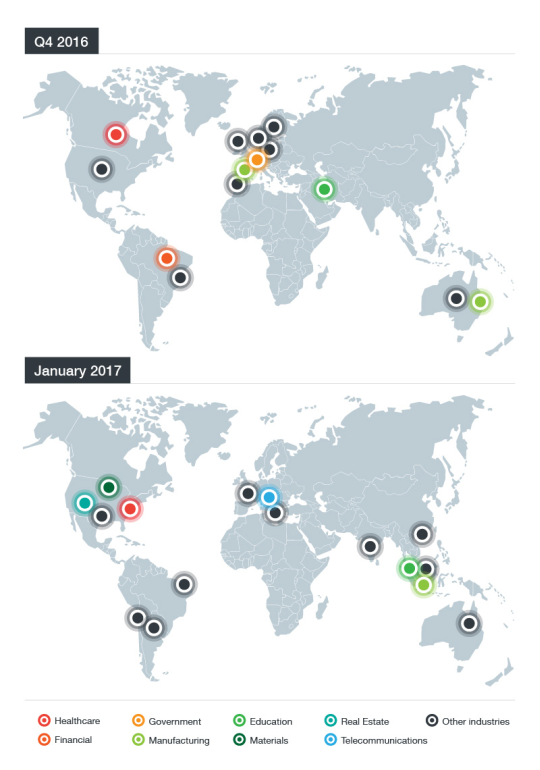
Figure 1. Distribution of victims
We believe that the same group of attackers is behind the earlier attacks and the current campaign. The file names being used are consistent within each region. Other parts of this attack—such as where the malicious files are dropped onto the compromised machine—are also consistent.
As we originally observed, during the RDP session a folder shared on the remote PC was used to transfer malware from the attacker machine:

Figure 2. Setting for shared folder to be used in RDP session
In some cases, the clipboard was also used to transfer files:
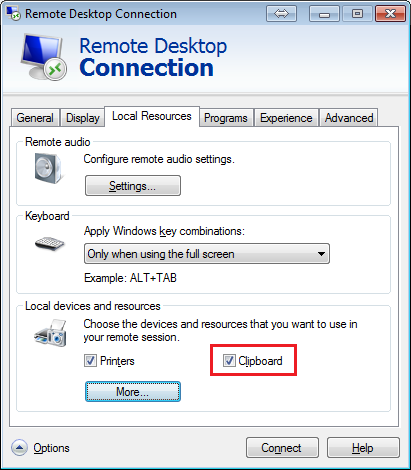
Figure 3. Setting for clipboard to be used in RDP session
Both methods expose the local resources of the attacker to the remote machine, and vice-versa. By default, there are no applied restrictions to these RDP features on an endpoint that is exposed to the internet and it is up to the administrator to apply controls.
The attacker tries to log in using various commonly-used usernames and passwords. Once the attacker has determined the correct username and password combination, he (or she) usually comes back multiple times within a short period to try and infect the endpoint. These repeated attempts are usually successful within a matter of minutes.
In one particular case, we saw CRYSIS deployed six times (packed different ways) on an endpoint within a span of 10 minutes. When we went over the files that were copied, they were created at various times during a 30-day period starting from the time of the first compromise attempt. The attackers had multiple files at their disposal, and they were experimenting with various payloads until they found something that worked well.
What to do when you suspect that this method has been used against your organization
If you find yourself in this situation, our original discussion in September event provided some key steps to consider.
- Limit the potential risk to your network by applying proper security settings in Remote Desktop Services. Disabling access to shared drives and the clipboard would limit the ability to copy files via RDP. Restricting other security settings may be useful as well. Note that limiting such functionality may impact usability
- Try to identify any offending IP addresses. With newer versions of Windows, the OS logs Remote Desktop connection details in the Windows Event Viewer with the Event ID 1149. The logged information includes the user account that was used (i.e., the compromised account), as well as the IP address of the attacker.
Trend Micro customers may also take advantage of some of the product features, namely:
- Check the product configuration for a product like Trend Micro OfficeScan. Specifically, check for an option like “Scan network drive” and make sure it is activated. This feature is usually disabled, but in some cases (like this one) it may be useful. It may even allow for the cleanup of the attacker's host: the shared network drive (located under \\tsclient) has full read/write access by default. Activating the “Scan network drive” option cleans the contents of this shared drive.
- Advanced network detection tools like Trend Micro Deep Discoverycan monitor brute-force attacks. Multiple “Unsuccessful logon to Kerberos” and “Logon attempt – RDP” events could be signs of an ongoing brute-force attack, and allow the IT administrator to know if the attack was successful. This should be monitored at all times for hosts that are exposed to the internet via RDP.
Trend Micro Ransomware Solutions

