Cyber Threats
MBR Wiper Attacks Strike Korean Power Plant
In recent weeks, a major Korean electric utility has been affected by destructive malware, which was designed to wipe the master boot records (MBRs) of affected systems. It is believed that this MBR wiper arrived at the target systems in part via a vulnerability in the Hangul Word Processor (HWP), a commonly used application in South Korea.
Update as of 11:29 P.M. PST, December 23, 2014 Upon further analysis, we confirmed that TROJ_WHAIM.A checks if the current date and time is Dec 10, 2014 11:00 AM or later. If it meets this condition, it sets the registry, HKEY_LOCAL_MACHINE\SOFTWARE\PcaSvcc\finish to 1, thus triggering the MBR infection. Otherwise, it sleeps for a minute and checks the system time again. Aside from the MBR infection capabilities and overwriting certain strings, another similarity of this attack to the March 2013 incident is its ‘time bomb’ routine. A certain action is set in motion once the indicated date/time by the attackers is reached by the infected system.
In recent weeks, a major Korean electric utility has been affected by destructive malware, which was designed to wipe the master boot records (MBRs) of affected systems. It is believed that this MBR wiper arrived at the target systems in part via a vulnerability in the Hangul Word Processor (HWP), a commonly used application in South Korea. A variety of social engineering lures were used to get would-be victims to open these files. Below is a quick overview of the attack with the infection chain starting from a spearphishing email sent to the employees' inboxes.
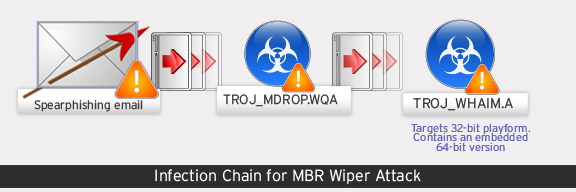
Malware Behavior
We detect the malware as TROJ_WHAIM.A, which is a fairly straightforward MBR wiper. In addition to the MBR, it also overwrites files that are of specific types on the affected system. It installs itself as a service on affected machines to ensure that it will run whenever the system is restarted. Rather cleverly, it uses file names, service names, and descriptions of actual legitimate Windows services. This ensures that a cursory examination of a system's services may not find anything malicious, helping this threat evade detection.
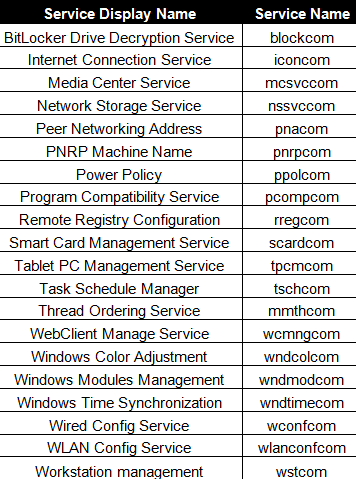
Figure 1. List of legitimate service names used by TROJ_WHAIM.A
Similarities to Previous MBR Attacks?
This particular MBR-wiping behavior, while uncommon, has been seen before. We observed these routines in March 2013 when several attacks hit various South Korean government agencies resulting in major disruptions to their operations. The malware involved in this attack overwrote the MBR with a series of the words PRINCPES, HASTATI, or PR!NCPES. The recent attack on Sony Pictures also exhibited a similar MBR-wiping capability. There are also similarities to the previous MBR wiper attacks as well. All three attacks mentioned earlier overwrite the MBR with certain repeated strings. This attack uses the repeating "Who Am I?" string, while the Sony attack used a repeating 0xAAAAAAAA pattern.

Figure 2. Screenshot of 'Who Am I' message seen upon bootup of infected systems
Destructive Malware and Demands
It has been claimed that the attack on Sony Pictures was because of that studio's production of the film The Interview. While we cannot independently verify the veracity of these claims, something similar has happened with this incident. We've noticed a particular Twitter user tweeting his demands toward the affected company, and if not met, would subsequently release various KHNP documents. Among these demands are the shutdown of nuclear power plants in Korea (nuclear provides for 29% of South Korean electricity requirements).
No Definitive Attribution
While there are definite similarities in the behavior of all these attacks, this is not enough to conclude that the parties behind the attacks are also related. All three attacks have been well documented, and it is possible that the parties behind each attack were "inspired" by the others without necessarily being tied. Without sufficient evidence, we cannot make claims either way. These attacks highlight our findings about the destructive, MBR-wiping malware that appear to have become a part of the arsenal of several threat actors. This is a threat that system administrators will have to deal with, and not all targeted attack countermeasures will be effective. Techniques to mitigate the damage that these attacks cause should be considered as a part of defense-in-depth networks.

