Global Threat Research
Leading cybersecurity with second-to-none attack intelligence
Security powered by industry-leading threat research
Spearheading the fight against cybercrime, we work tirelessly to gather intelligence across adversary, attack, and threat landscapes to help you face present and future threats. Guided by these insights and AI models, we protect over 500,000 companies worldwide from hundreds of millions of threats daily.
Elite threat intel
Unprecedented insights into vulnerabilities and exploits as the only leading security vendor with its own agnostic bug bounty program, the Trend Micro™ Zero Day Initiative™ (ZDI).
Dedicated team
A dedicated team of researchers and data scientists operating 24/7/365.

Real-time insights
Real-time insights from multiple native sensors covering cloud, gateway, email, web, network, server, endpoint, mobile, and IoT/IIoT/OT.

Research and innovation
Relentless focus on research and innovation for over 30 years leading to 700+ patents.


Intelligence is power
Decades of human intelligence, bolstered by nearly 20 years of using artificial intelligence in the cybersecurity industry, mean unprecedented insights into who, what, and how adversaries target. Trend has the foresight to better understand today’s attacks and deliver the best cyber risk and cybersecurity platform in the world.
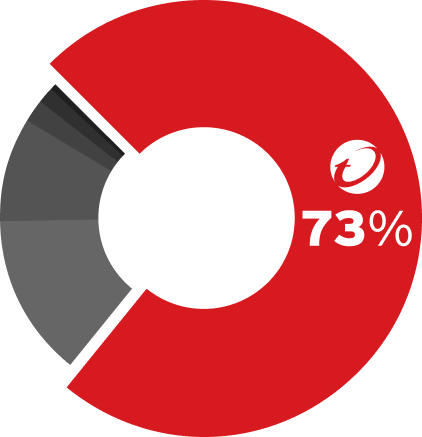
We Are THE Leader in Vulnerability Research
See how 450+ dedicated threat researchers across 14 global threat research centers unite for powerful frontline defense.

Addressing the challenges of today’s cybersecurity landscape
Cyber threats
Built on over 30 years of cybersecurity leadership, hundreds of global threat researchers, and insights across in cloud, web, email, network, server, endpoint, mobile, and IoT/IIoT/OT environments, our solutions offer the broadest attack and threat coverage.
Vulnerability
Trend Micro™ Zero Day Initiative™ (ZDI), the world’s largest agnostic bug bounty program, delivers the best vulnerability research worldwide. Researchers identify bugs spanning OS, applications, SCADA, OT, and EVs, giving us first access to pre-disclosure vulnerabilities. Customers get 3 months of virtual patches before vendor patches are available for instant protection across all environments.
Targeted attacks
Our researchers are constantly analyzing targeted attacks to better understand how adversaries’ tactics, techniques and procedures (TTPs) evolve. Based on years of adversarial and campaign intelligence, our AI models track their next steps to help customers withstand them.
AI and machine learning
Advanced attack methods require advanced detection approaches. We enhance your defenses, efficiency, and detection of zero-hour threats using over 19 years of experience building AI/GenAI and ML into our solutions. Our tailored AI ensures optimal protection in every scenario.
The internet of things (IoT), industrial IoT (IIoT), and operational technology (OT)
Cyber criminals target critical infrastructure using IoT/IIoT/OT as common avenues of attack. Trend and ZDI have collected extensive threat intelligence from customers using these platforms, giving us deeper insights into attack surface threats.
Cloud infrastructure
Trend understands the attacks and threats targeting this infrastructure better than most. The cloud research team takes an attack-driven approach that begins with threat modeling to inform potential attack scenarios, with defenses then built into existing and future products.
Cybercriminal undergrounds
Our researchers have invaluable insights into cybercriminal undergrounds. Decades-long partnerships with Interpol, Europol, the United Nations, the FBI, and the US Department of Homeland Security have given us early insights into cybercriminal operations while helping us make the world safer.
Future threats
Our forward-looking threat research team continually assesses the evolving cybersecurity landscape to predict potential threats while mapping out viable security strategies.
Elite threat defense
Imagine being protected from cyber threats months before they strike. At Trend, our industry-leading threat intelligence makes this a reality.
OUR IMPACT
The proof is in the numbers
+161B
Threats blocked in 2023 alone
+6.6T
Threat queries in 2023 alone
+250M
Worldwide sensors
