Why choose Trend Vision One™ Cloud Security?
Eliminate security gaps with our full CNAPP solution that enables visibility and control across multi-cloud environments. Gain real-time risk assessments, exposure management, and predicted attack paths through our centralized dashboard.

Comprehensive visibility and control
You can’t protect what you can’t see. Take advantage of real-time risk assessment and monitoring with detailed insight into potential attack paths, all from a single dashboard.
Continuous assessment and prioritization
Stay ahead of the evolving threat landscape with continuous monitoring to identify and mitigate threats before they impact your cloud environment. Proactively identify attack paths, assess vulnerabilities, and remediate before threats have a chance.
Simplified compliance and cost management
Streamline security, compliance, and incident response. Gain a unified view of your cloud environment with detailed reporting to quickly identify and prioritize areas that require immediate attention. With flexible licensing and reduced tool sprawl, you alleviate complexity and save money.
See what others miss. Stop risks first.
Industry-leading Trend Vision One Cloud IPS seamlessly integrates with AWS Network Firewall supported by Trend Zero Day Initiative™ (Trend ZDI). Enable comprehensive protection with a single click while managed cloud IPS rules proactively block malware and vulnerabilities before reaching your business applications.
Centralized overview of your cloud projects
Project View transforms cloud security with a unified lens into your cloud projects, interactive widgets, detailed tables, and real-time updates for effective risk management.


Manage cloud risks with confidence
Gain continuous discovery and real-time risk assessment of attack surfaces across workloads, containers, APIs, and cloud assets with Cloud Risk Management. Achieve unified visibility, ongoing vulnerability evaluations, predictive risk analytics, compliance monitoring, and seamless integration with existing security tools.

Key capabilities include CSPM, ASM, EASM, CIEM, AI-SPM, DSPM, IaC/template scanning, agentless vulnerability and malware scanning, attack path analysis, and API risk visibility.
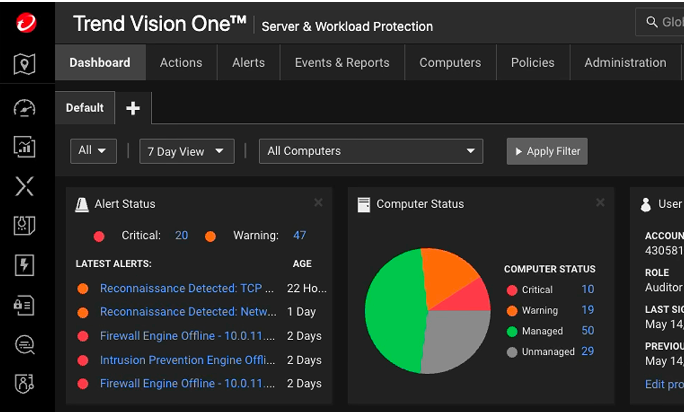
Robust server and cloud workload security
With Trend Vision One™ Server and Workload Security (SWP), your organization will gain protection for servers and workloads across hybrid and multi-cloud environments. Real-time threat detection, advanced encryption, automated vulnerability management, compliance enforcement, and comprehensive visibility and control ensure the ever-evolving threats are no match for your organization.
Unified protection, accelerated builds
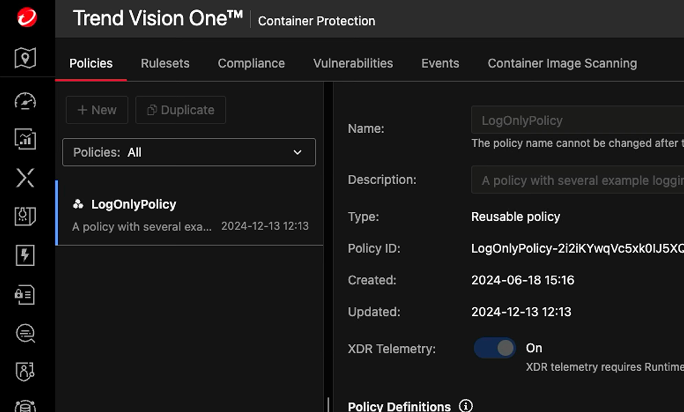
Trend Vision One™ Container Security equips your team with comprehensive protection for pre-runtime and runtime environments, including container image scanning for vulnerabilities, malware, and secrets.
Gain Kubernetes Security Posture Management (KSPM), continuous runtime scanning, policy enforcement, and malware protection. Ensure security with access control, intelligent network segmentation, and automated compliance checks for your containerized infrastructure.
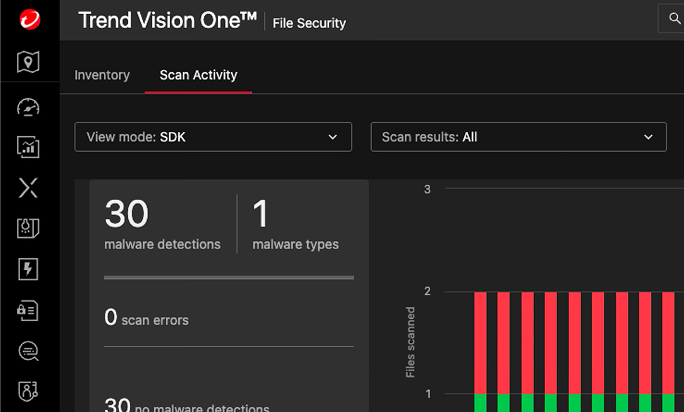
Comprehensive and effortless file security
Trend Vision One™ File Security provides flexibility, scalability, and comprehensive protection with an Software Development Kit, virtual appliance, cloud storage integration, and a containerized scanner. Secure your Amazon S3 buckets with machine learning for compliance. Maintain robust security by scanning for malware, quarantining threats, enhancing detection, and scaling as needed.
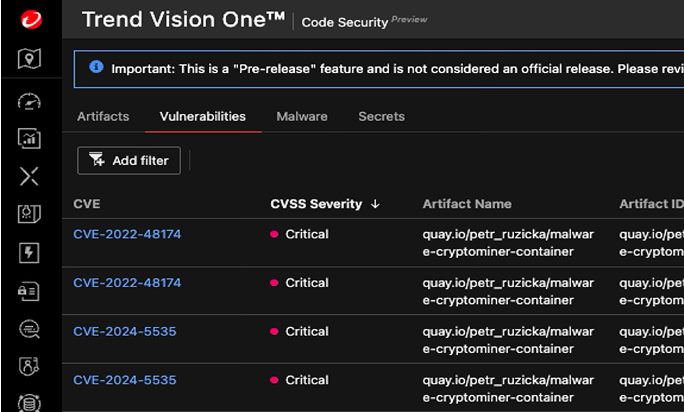
Secure code from development to deployment
Trend Vision One™ Code Security takes a proactive approach by integrating security early in development, detecting and preventing vulnerabilities, malware, and secrets before runtime. Enjoy continuous visibility from code creation to cloud deployment, automated CI/CD security testing, and enforced secure coding practices.
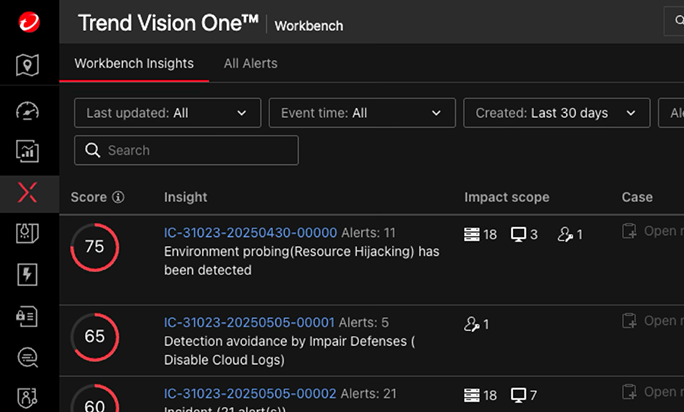
Unmatched threat detection and response
Trend Vision One™ XDR for Cloud leverages 700+ detection models and global threat intelligence to enhance detection and response. Integrated with AWS CloudTrail, it pre-empts threats like privilege escalation and S3 data exfiltration. Automated playbooks deliver cross-platform visibility, advanced correlation, and rapid response. With capabilities like XDR, CDR, and AI-DR, turn cloud noise into clarity with for secure, scalable operations.
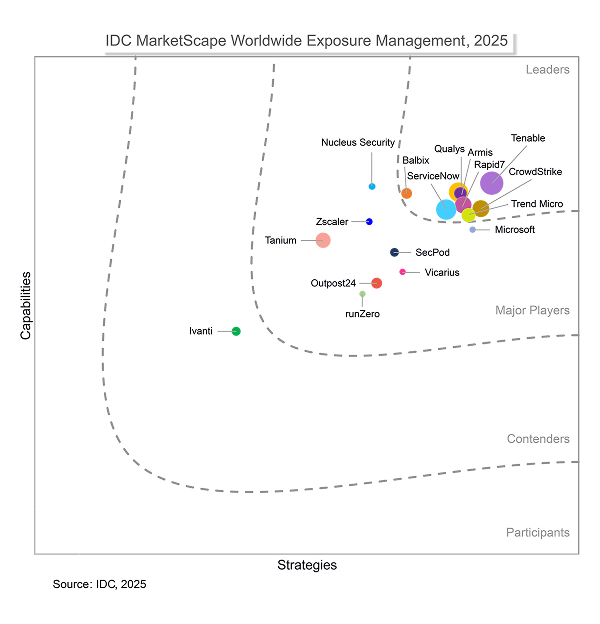
Trend Vision One Ranked #1 out of 59 Enterprise Solutions
The extended detection and response platform customers are raving about.




See Cloud Security in action
Discover how you can unlock end-to-end cloud asset protection and visibility for all your cloud assets across multiple cloud environments.
DEFENDING AGAINST
- Known & Unknown Threats
- Third-Party Packages
- Suspicious Drift
- Network Threats
- Misconfigurations
THIRD-PARTY INTEGRATIONS
20+ More






CLOUD SERVICE PROVIDERS
125+ Cloud Services



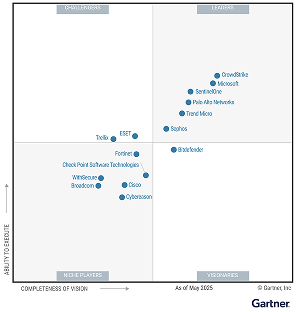
Trusted by industry experts