Cyber-Kriminalität
Trend Micro and INTERPOL Join Forces Again for Operation Synergia
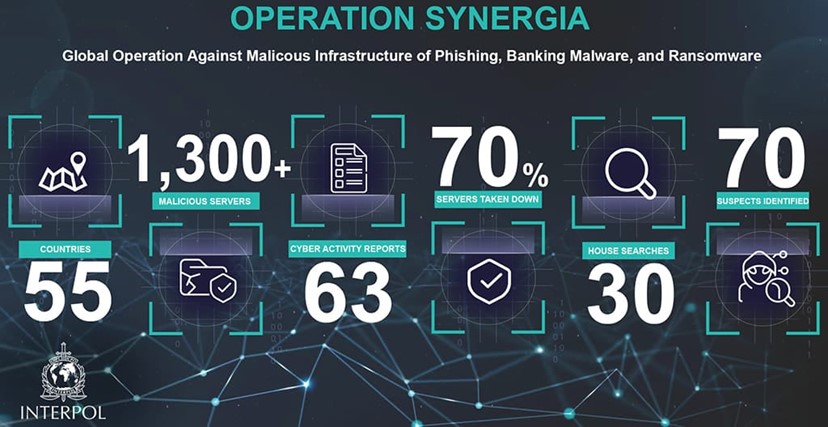
Trend and other private entities recently contributed to INTERPOL’s Operation Synergia, a global operation that successfully took down over 1,000 C&C servers and identified suspects related to phishing, banking malware, and ransomware activity.
Trend Micro has an extensive track record of working with law enforcement by providing threat intelligence. Recently, Trend and other private entities contributed to INTERPOL’s Operation Synergia, an operation that focuses on three threat types (ransomware, banking trojans, and phishing) and took down 1,300 command-and-control (C&C) servers ranging from various botnet and malware connections, phishing servers, and ransomware attacks. In this global operation, 55 member countries participated which resulted in the takedown of 70% of the identified servers.
Trend was able to share malicious IP addresses in these three categories. The threat intelligence provided by Trend contributed to 63 INTERPOL Cyber Activity Reports (Figure 1) and, over the course of operation, led to 30 house searches and the identification of 70 suspects facilitating the phishing, malware, or ransomware activity.
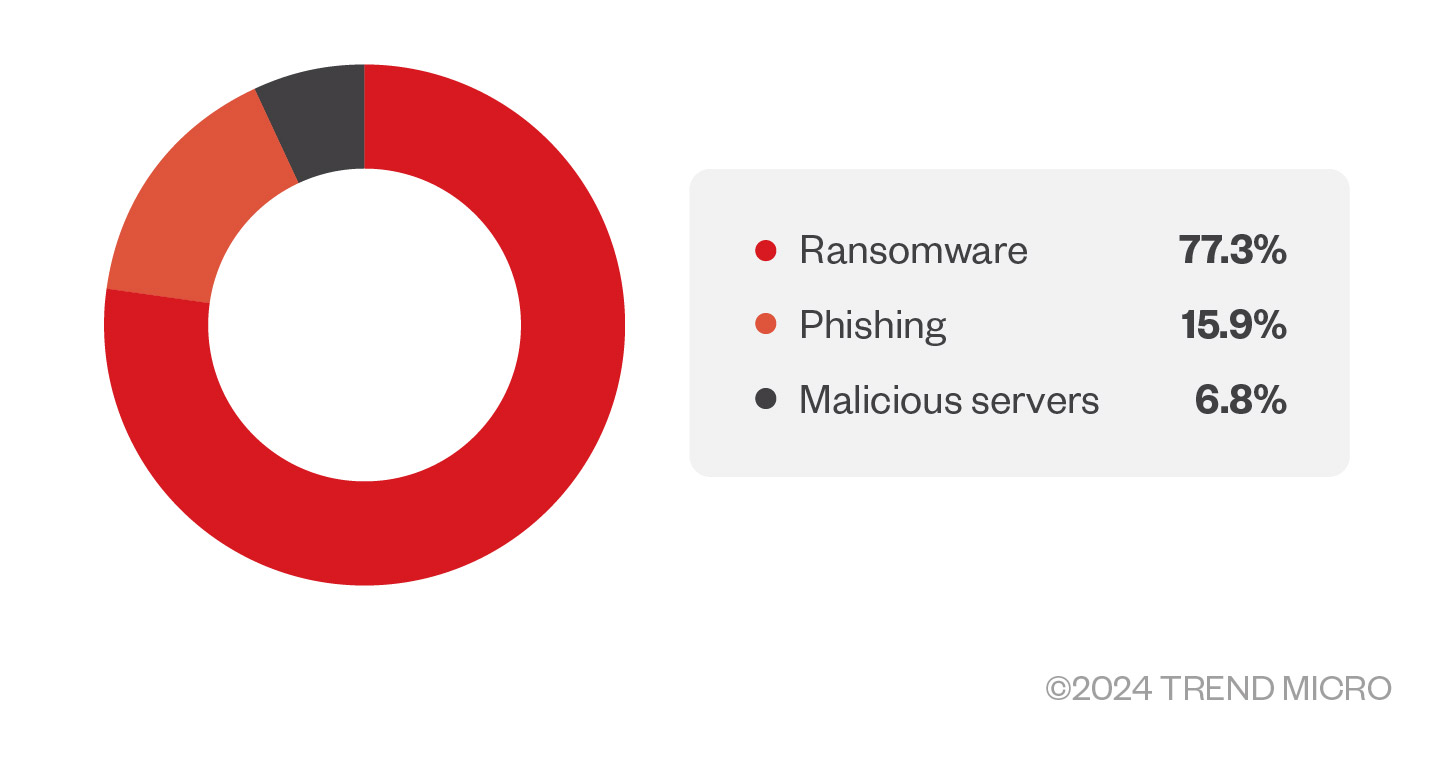
In the first half of 2023, most of malicious IP addresses detected from the Trend Micro™ Smart Protection Network™ were related to ransomware at 77.3% (Figure 2). Detecting these malicious IP addresses and providing it to law enforcement agencies (LEAs) like INTERPOL is a significant contribution in combatting notorious crimes like ransomware attacks, which have been evolving into a stronger and worse cyberthreat.
Malware varieties
As part of its cooperation with this Interpol-led operation, Trend assisted in identifying the varieties of malware connecting to unique C&C servers. Many of these pieces of malware acted as ransomware enablers or as a means of initial access, making it crucial to intercept them to prevent ransomware infections. The malware types most used to connect with the servers include stealers, trojan stealers, remote access trojans (RATs), downloaders, and botnets (Figure 3).
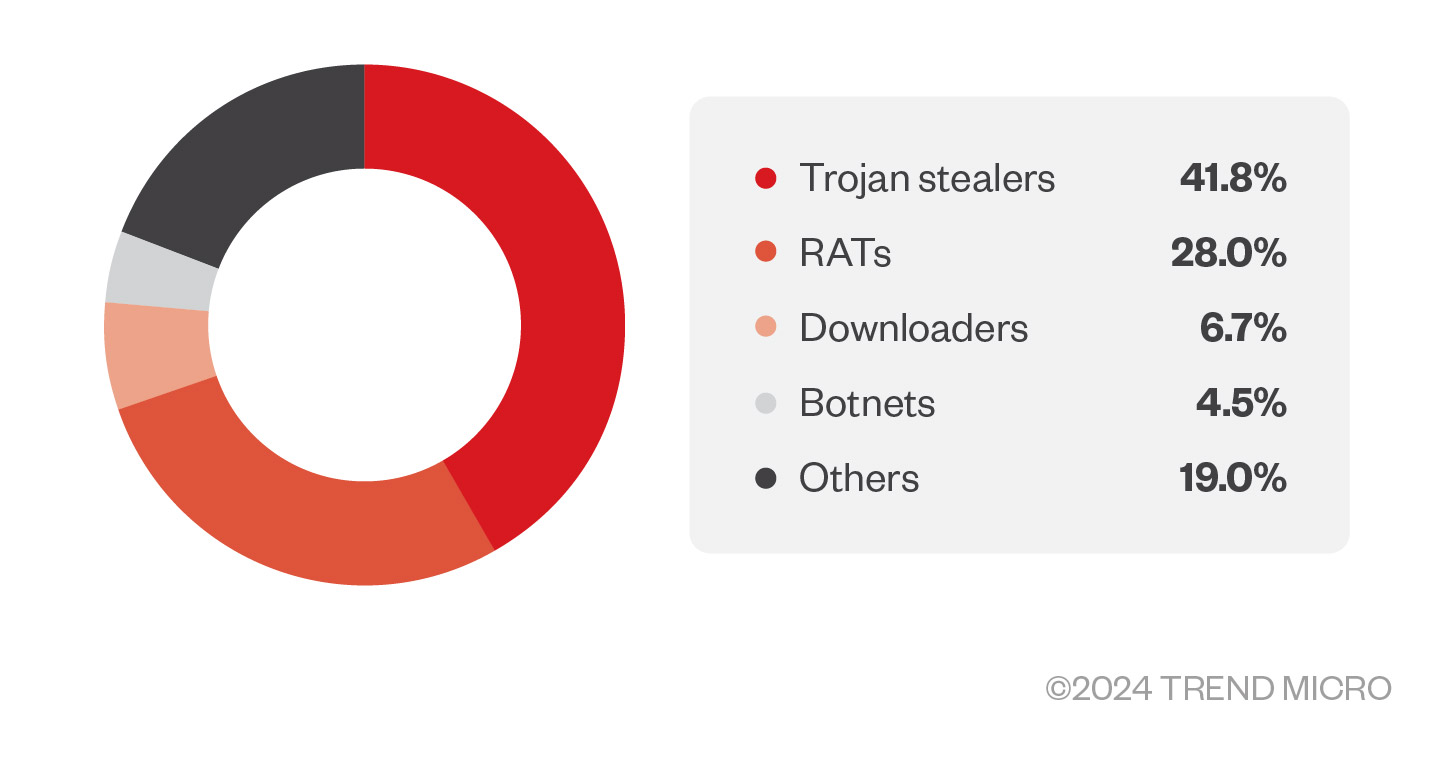
Some of the most common RATs used by the threat actors targeted in Operation Synergia include DCRat, Cobalt Strike, Remcos, and AsyncRAT. Additionally, among the commonly used stealers were ArkeiStealer, Azorult, Raccoon, and Stealc.
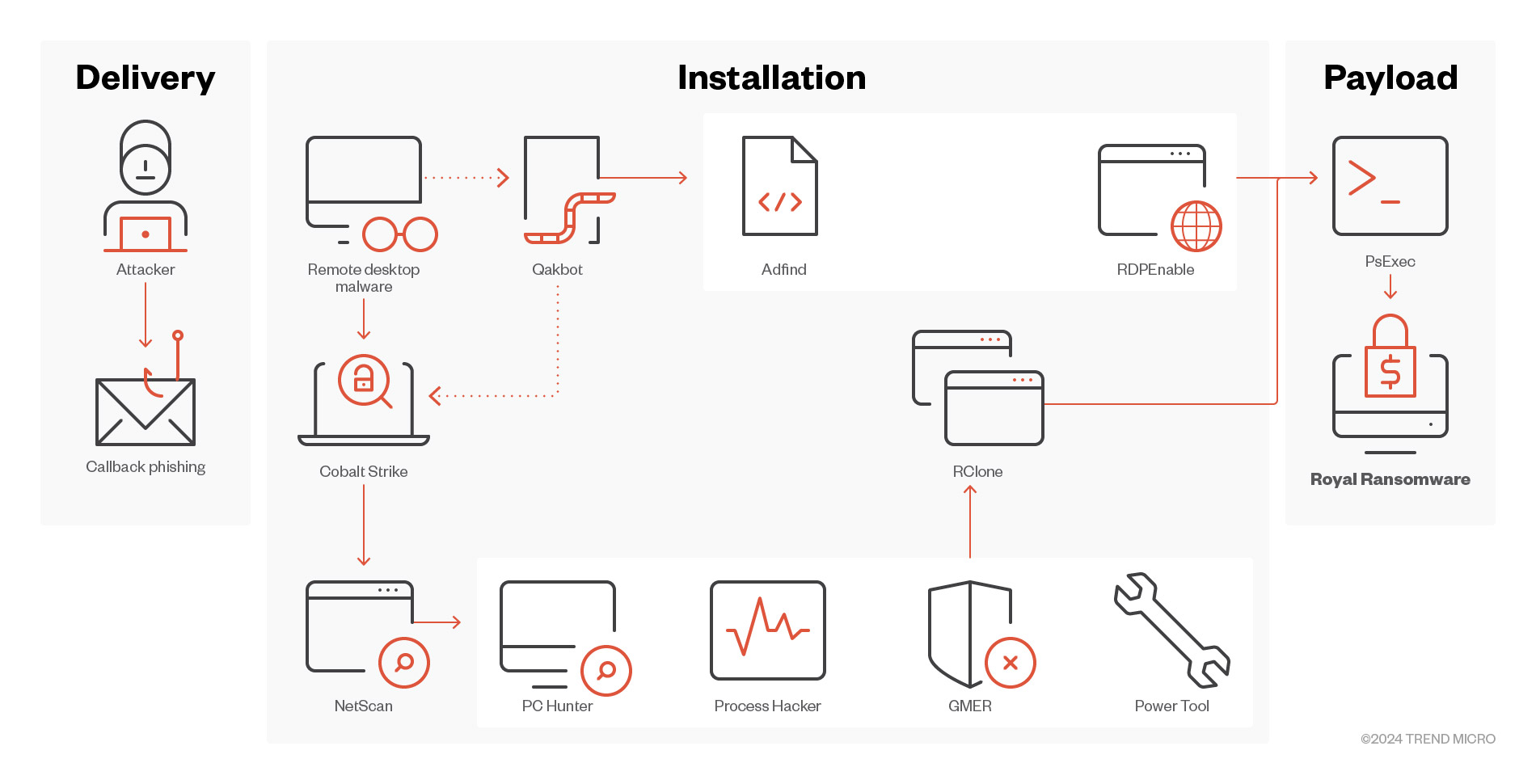
Cobalt Strike
The infamous Cobalt Strike was one of the notable malware instances observed in the infrastructures related to the banking trojans, ransomware, and phishing activity that Trend shared with INTERPOL for Operation Synergia. While Cobalt Strike is primarily utilized by cybersecurity professionals and red teams for legitimate security testing purposes, it has been exploited by cybercriminals for lateral movement between machines and for C&C communication. Cobalt Strike has been employed by several notorious ransomware families, including Black Basta, BlackCat, Royal, and Rhysida (Figure 4).
AsyncRAT
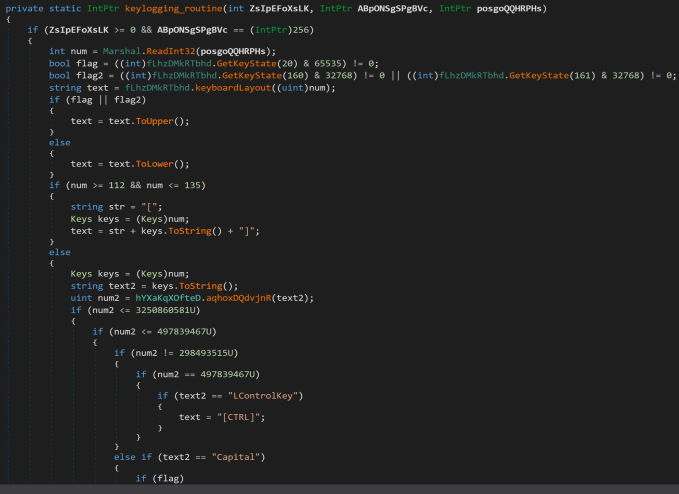
In addition to loaders, a RAT known as AsyncRAT was identified in relation to the infrastructures. AsyncRAT enables attackers to remotely access and control compromised systems, facilitating various malicious activities including data theft, surveillance, and the execution of additional malware. In December 2023, researchers from Trend’s Managed XDR team shared their findings on various cases involving AsyncRAT. Based on their findings, the backdoor commands of AsyncRAT’s binary are mainly dependent on its embedded configuration; one example is logging keystrokes, as shown in Figure 5.
RedLine
2023 proved to be a busy year for the RedLine stealer, another noteworthy malware instance Trend observed during its participation in Operation Synergia. The RedLine stealer was observed deploying various techniques throughout 2023: These techniques included spear-phishing campaigns, the abuse of extended validation (EV) code signing certificates to deploy ransomware payloads, and the exploitation of the increasing popularity of artificial intelligence (AI) to distribute the RedLine stealer (Figure 6).
C&C server locations
Trend has also consistently supported INTERPOL’s Cyber Fusion Centre (CFC) by identifying additional C&C servers across multiple country locations (Figure 7), contributing to a more comprehensive understanding of threat information. Trend’s partnership with this LEA in dismantling extensive botnet servers, leading to the widespread disruption of cybercriminal activities and the apprehension of several threat actors, is a testament to the success of this global collaboration, akin to that of Trend’s previous involvement in the INTERPOL-led Africa Cyber Surge I and II operations in the focus region of Africa.
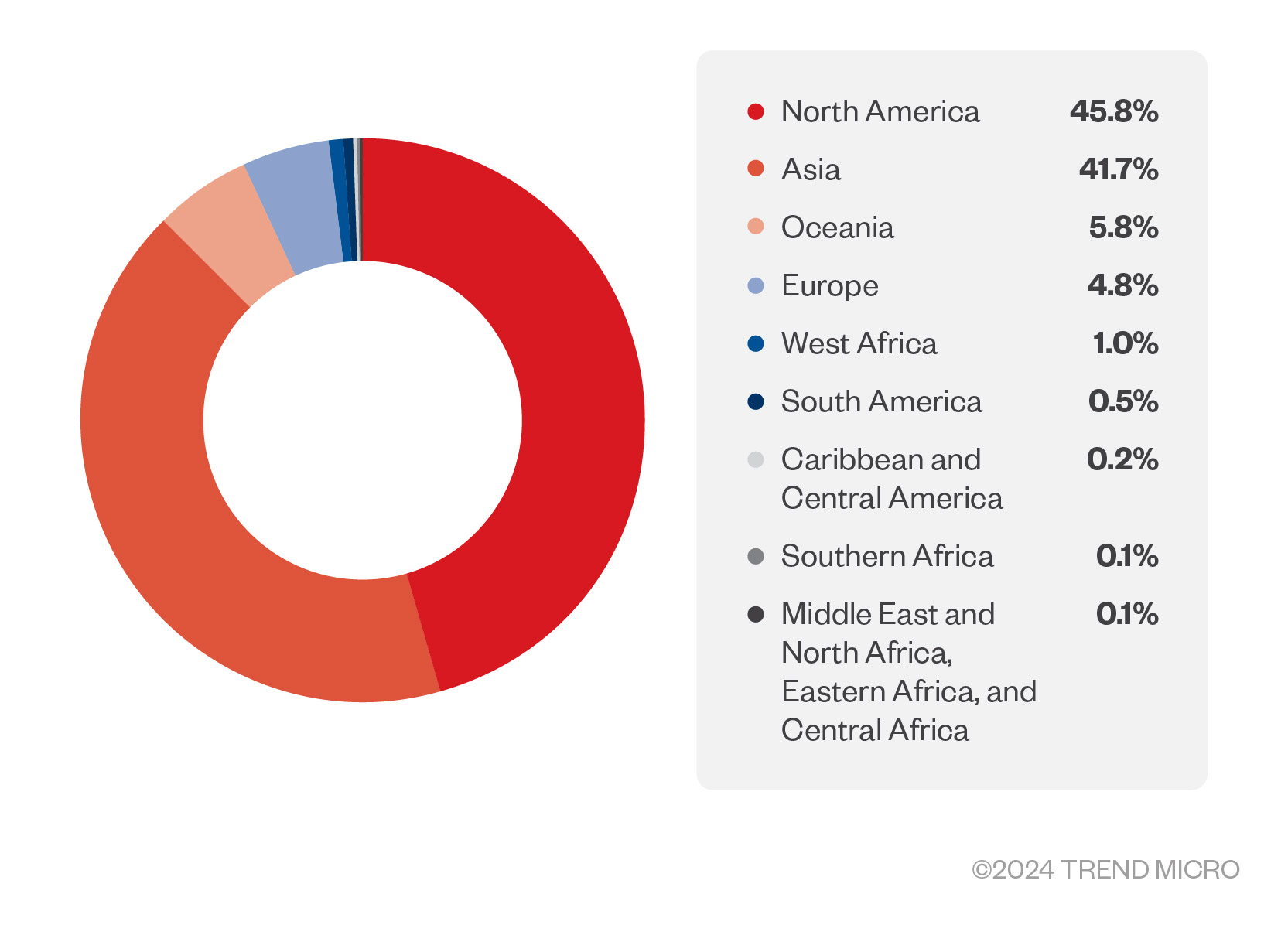
Additionally, Trend provided the location of various C&C servers in Kuwait, Hong Kong, Singapore, Bolivia, and several other sites in Europe. Although some of these servers did not go through the operation (the inclusion of such is dependent on the participating member countries involved in Operation Synergia), sharing this telemetry from Trend empowers LEAs to coordinate with member countries and seek their help in combating cybercrime.
Partnership with INTERPOL
Trend has a long and successful history of cooperation with law enforcement agencies across the globe. Operations that involve law enforcement and private sector cooperation allow security organizations and industry experts to provide their skills, resources, and years of experience to aid in the investigation and apprehension of malicious actors. As cybercrime operations are evolving and expanding — especially the relentless deployment of spam run campaigns — LEA operations are adjusting as well. They strategize and embrace what we call "smart operation," as it casts wider net for the infrastructure of cybercriminals and turns it into actionable intelligence with execution of operation in a short span of time, truly a remarkable one.
Trend’s partnership with INTERPOL has led to many successful takedowns over the years, like the dismantling of the 16shop phishing kit and the disruption of African cybercrime networks under Africa Cyber Surge I and II last year, the arrests of business email compromise (BEC) actors under Operation Killer Bee in 2022, and the arrests of REvil and Cl0p members for Operation Cyclone in 2021. This partnership continues as we at Trend carry on our mission to secure today’s connected world.

