In an era dominated by the Internet of Things (IoT), envision a thriving manufacturing plant adorned with countless interconnected devices. These devices, operating on a private 5G network, create an intricate web of connectivity. Safeguarded within a private IP subnet, these IoT devices remain impervious to external threats thanks to their isolation. With the 5G core and backend servers securely nestled in the cloud, these devices have limited or no internet access.
Yet, a crucial question arises: How can attackers breach this seemingly impenetrable fortress? Amidst a world rife with security challenges, a vulnerability emerges in the form of packet reflection, jeopardizing the sanctity of these private 5G networks.
The Vulnerability
The vulnerability at hand resides within the GPRS Tunneling Protocol User Plane (GTP-U), which connects base stations to the user plane function (UPF) of the 5G core. Surprisingly, this critical link lacks encryption and authentication mechanisms, disregarding the GSM Association (GSMA) recommendations to implement Internet Protocol Security (IPSec) encryption on GTP tunnels. Concerns regarding latency and throughput primarily drive this omission.
Consequently, Trend Micro Research and its partners have discovered a concerning packet reflection vulnerability in 5G core UPFs, exploiting the absence of IP cross-checking between the control and data planes in packet cores. While firewalls and access control lists (ACL) can provide some level of protection, constant manual reconfiguration is necessary.
This vulnerability has been reported to the Zero Day Initiative (ZDI) and has obtained a high Common Vulnerability Scoring System (CVSS) score of 8.3, underscoring its severity.
Enterprise 5G Topologies
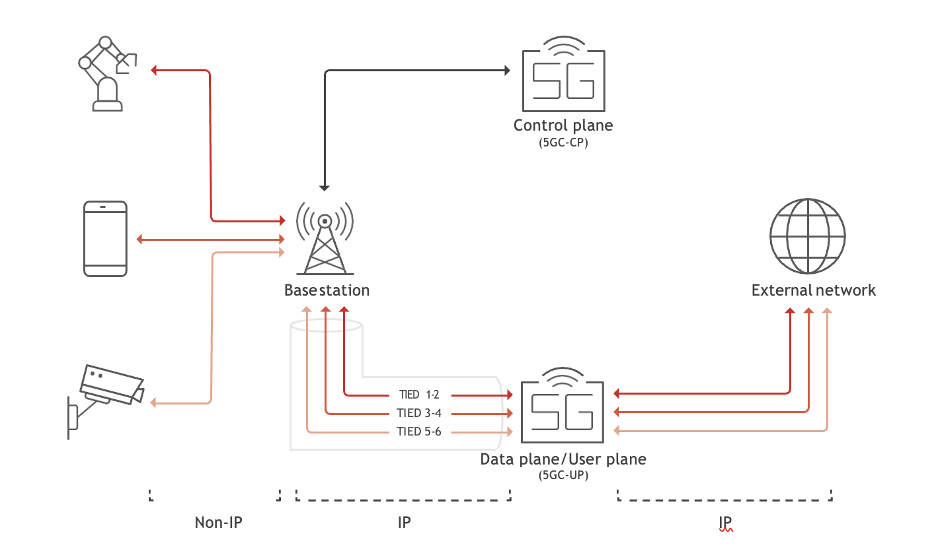
Private enterprise 5G networks can be deployed in various configurations, often incorporating a local breakout (LBO) at the edge or on-premises, keeping local traffic within the corporate network. These configurations include:
- 5G core in a public cloud with LBO at the edge.
- 5G core located at the operator's premises with on-premises LBO.
- 5G core in a private cloud or multi-access edge computing (MEC) with co-located LBO.
Data traffic from 5G user devices (UE) travels through GTP tunnels between a base station and the 5G core.
The crux of the matter lies in the 5G core User Plane interface (N3), which is often exposed to the cloud, serving as a gateway for potential attackers. This exposure enables attackers to create GTP packets, encapsulating attack packets with private addresses and sending them to the UPF IP.
Attacks can be initiated in both the downlink and uplink directions. In the downlink scenario, the attacker crafts a packet with the UE IP as the destination and an internet IP ( it could be the attacker’s own IP, which paves the way for 2-way connection) as the source. This packet is then encapsulated within a GTP packet and sent to the UPF. The UPF forwards the packet to the base station, which decapsulates the inner packet and delivers it to the UE. This establishes a two-way connection between the attacker and the UE.
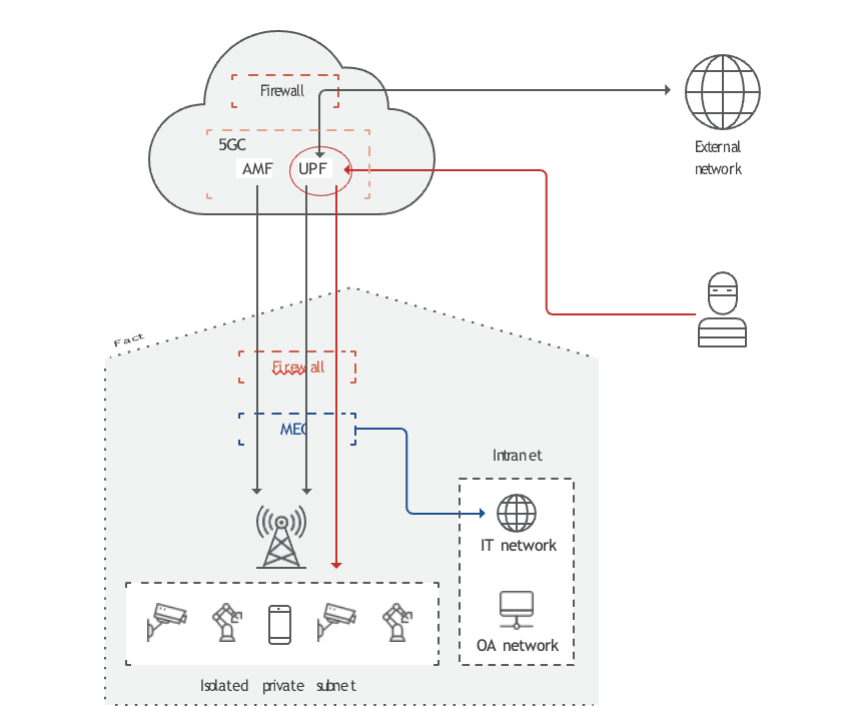
In the uplink scenario, the attacker initiates an attack by sending a packet with the UE's IP address as the source and an internet IP address as the destination. This packet is then encapsulated within a GTP packet and sent to the User Plane Function (UPF). The UPF forwards the packet to the internet server, and the response is delivered back to the UE through the 5G network.
To carry out these attacks, the attacker requires a valid Tunnel Endpoint Identifier (TEID) associated with the target IP. TEIDs are 32 bits in length and can be discovered through a brute-force method. The attacker sends a ping flood with various TEIDs until a matching one is found.
The Root Cause
The 3rd Generation Partnership Project (3GPP) standards do not enforce peer verification for user plane packets (but are mandatory for the control plane), creating a significant security gap. This vulnerability allows potential attackers to exploit the network's integrity and confidentiality. Recent tests on 5G cores from various vendors have revealed multiple vulnerabilities that worsen the situation. One proposed solution to enhance security is the implementation of IPsec, although its adoption is limited due to cost and scalability challenges.
In response to these vulnerabilities, the Zero Day Initiative (ZDI) has reported vulnerable devices to the respective vendors. Recommendations have been made to implement additional security measures such as firewalls and demilitarized zones (DMZs). However, it is crucial to recognize that this vulnerability is not simply a patchable problem; it requires a comprehensive approach to address it.
The packet reflection vulnerability in private 5G networks poses a critical security risk, enabling attackers to infiltrate and compromise internal IoT devices. This vulnerability is particularly concerning for manufacturers and businesses operating in isolated environments, as they face severe risks, including ransomware attacks, data breaches, disruptions to critical operations, and degradation in service quality. Organizations must prioritize the implementation of robust security protocols and measures to mitigate these risks and safeguard their networks and assets.
Mitigating the Eisks
The recently discovered vulnerability presents an undeniable reality that cannot be ignored: attackers from anywhere on the internet could effortlessly breach a private network. This raises significant concerns as it grants access to internal networks and private subnets. Such access provides attackers with a dangerous foothold into devices within cellular networks, which is an extremely troubling prospect.
It is crucial to perceive this vulnerability as more than a mere security risk. Instead, it should be recognized as a gateway for attackers to infiltrate internal networks, exploiting any vulnerabilities within connected devices. This is particularly worrisome for manufacturers and businesses operating within isolated and private networks, where regular security patch updates may not be common practice. For those moving from wifi to private cellular networks, it might come as a shock that private subnets can be reached from the Internet.
The implications of this vulnerability are vast and should not be underestimated. They range from potential ransomware attacks to the exfiltration of susceptible data, prolonged disruptions from denial-of-service (DoS) attacks, and even the infiltration of stealthy agents compromising product quality.
Given the severity of these potential risks, organizations must take immediate action. Proactive measures, including comprehensive security protocols, regular patch updates, and robust intrusion detection systems, must be implemented to address this vulnerability. Failure to do so could significantly damage the network infrastructure and the affected entities' reputation.
Strengthening Enterprise Defenses
To shield against this looming threat, enterprises can adopt specific security practices that enhance their security posture:
Implement IPsec and secure tunneling mechanisms
Consider using IPsec or other secure tunneling mechanisms to thwart most man-on-the-side (MoTS) attacks. While encryption comes with various costs, evaluating its acceptability for your organization is crucial for strengthening your network security.
External security devices
Given the absence of built-in IP cross-checking mechanisms in 5G cores from most vendors, consider employing external security devices with this capability. These devices can effectively reduce the attack surface without compromising performance.
Leverage CTOne for enhanced security
Enterprises seeking comprehensive solutions to fortify their cybersecurity posture can turn to CTOne, a global leader in communication technology. CTOne, a subsidiary of Trend Micro, is dedicated to enabling digital transformation and bolstering the resilience of communication technology.
Multilayered Security Solutions with Trend Vision One™
In the face of ever-evolving threats, the importance of implementing multilayered security solutions becomes evident. Trend Micro's cybersecurity platform, Trend Vision One™, offers businesses a comprehensive perspective of their attack surface.
This platform simplifies the process of detecting and responding to threats, seamlessly adapting to industrial control systems (ICS) and 5G environments. By assessing risk exposure and automatically deploying controls to mitigate such risks, Trend Vision One™ reduces alert volume, enabling security teams to focus on strategically crucial tasks.
Safeguard your future by staying one step ahead in the realm of cybersecurity. Download the full study from Trend Micro Research to explore a comprehensive analysis of this critical security vulnerability and the strategies to counter it

