New Black Hole Exploit Technique
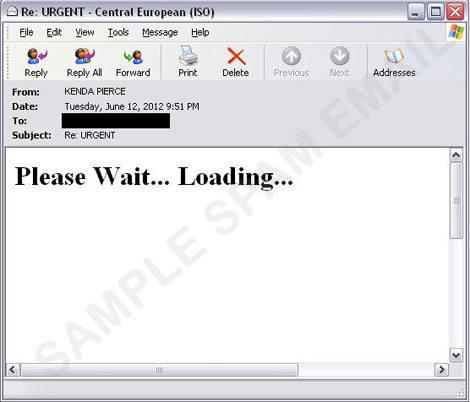
Trend Micro researchers are continuously monitoring spammed messages that lead to black hole exploits. Typically, these spammed messages have links that, when clicked by the users, end with the download of a malware, usually a ZBOT variant. However, this time around, a script embedded in the spammed message automatically connects to a compromised site. Users see a general loading text displayed but are also redirected to another website that starts the infection by downloading a malware in its landing page.
The gathered spammed messages contain different compromised URLs and the downloaded file Set.jar. The said embedded script is in HTML format and runs on email clients that support HTML. Users are advised to be wary in opening email messages even if these came from seemingly known sources. Note that black hole exploit campaigns leverage known organizations and websites to lure users into clicking the malicious URL that lands users to the exploit page.
- ENGINE:7.0
- PATTERN:8968
