Fake Norton Security Notification Leads to a Phishing Website
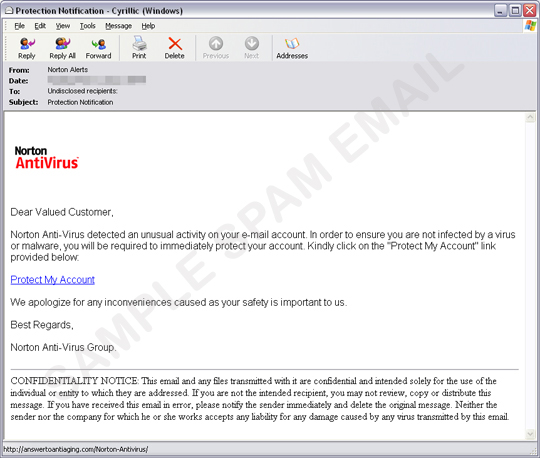
An email message that pretends to be an account security notification from Norton tells its victim of a supposed unusual account activity. The email message urges the recipient to update account details via the link provided in the message. Clicking on the link redirects the recipient to a compromised website believed to be hacked into by a hacker group known as Underground Security Crew:
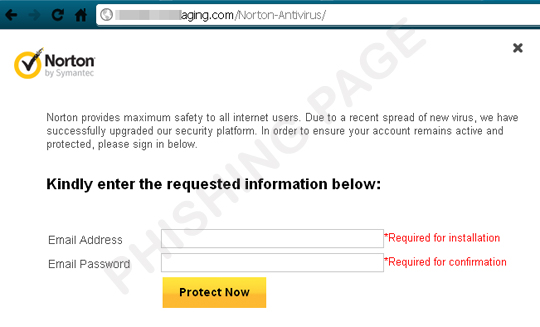
After completing and submitting the form on the compromised website, the user is redirected to the original index page of Norton.
Upon further investigation, Trend Micro engineers found a server-side script on the phishing form hosted in the compromised website:
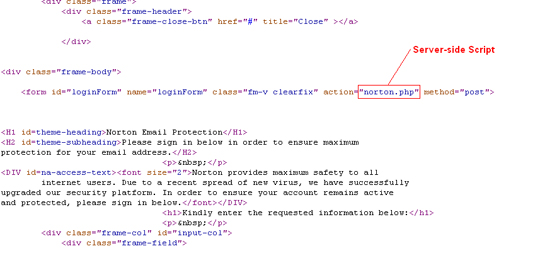
The identified server-side script is used to capture the email address and password provided on the phishing form. Because it hosted on a server, the code of the script cannot be viewed easily. Destination of the stolen data is also difficult to track. The cybercriminals used the security feature of the server-side scripting to hide the compromise to steal information.
It is of utmost important to check account details by going direct to merchant's or product's website.
- ENGINE:
- PATTERN:8908
